2016-06-20 - EK DATA DUMP (NEUTRINO EK, RIG EK, SUNDOWN EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-20-EK-data-dump-8-pcaps.zip 3.9 MB (3,881,337 bytes)
- 2016-06-20-Afraidgate-Neutrino-EK_sends-CryptXXX-ransomware.pcap (580,968 bytes)
- 2016-06-20-EITest-Neutrino-EK-sends-CryptXXX-ransomware.pcap (619,361 bytes)
- 2016-06-20-Rig-EK-after-chipdating_link.pcap (87,185 bytes)
- 2016-06-20-Rig-EK-after-monavocatparis_fr.pcap (245,813 bytes)
- 2016-06-20-Sundown-EK-traffic.pcap (383,350 bytes)
- 2016-06-20-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-contaratosbeach_gr.pcap (627,304 bytes)
- 2016-06-20-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-salentoeasy_it.pcap (624,267 bytes)
- 2016-06-20-pseudoDarkleech-using-hopto_org-Neutrino-EK-sends-CryptXXX-ransomware.pcap (1,198,039 bytes)
- 2016-06-20-EK-data-dump-malware-and-artifacts.zip 1.6 MB (1,616,365 bytes)
- 2016-06-20-Afraidgate-Neutrino-EK-flash-exploit.swf (81,565 bytes)
- 2016-06-20-Afraidgate-Neutrino-EK-landing-page.txt (927 bytes)
- 2016-06-20-Afraidgate-Neutrino-EK-payload-CryptXXX-ransomware.dll (452,608 bytes)
- 2016-06-20-EITest-Neutrino-EK-flash-exploit.swf (81,565 bytes)
- 2016-06-20-EITest-Neutrino-EK-landing-page.txt (817 bytes)
- 2016-06-20-EITest-Neutrino-EK-payload-CryptXXX-ransomware.dll (476,160 bytes)
- 2016-06-20-EITest-flash-file-from-mionne_tk.swf (15,832 bytes)
- 2016-06-20-Rig-EK-flash-exploit.swf (21,798 bytes)
- 2016-06-20-Rig-EK-landing-page-after-chipdating_link.txt (5,264 bytes)
- 2016-06-20-Rig-EK-landing-page-after-monavocatparis_fr.txt (5,304 bytes)
- 2016-06-20-Rig-EK-payload-after-chipdating_link.exe (43,008 bytes)
- 2016-06-20-Rig-EK-payload-after-monavocatparis_fr.exe (196,608 bytes)
- 2016-06-20-Sundown-EK-flash-exploit.swf (38,603 bytes)
- 2016-06-20-Sundown-EK-landing-page-1-of-2-second-run-with-IE8.txt (31,176 bytes)
- 2016-06-20-Sundown-EK-landing-page-2-of-2-second-run-with-IE8.txt (45,836 bytes)
- 2016-06-20-Sundown-EK-landing-page-first-run-with-IE11.txt (66,220 bytes)
- 2016-06-20-Sundown-EK-payload.exe (172,032 bytes)
- 2016-06-20-Sundown-EK-silverlight-exploit.zip (20,412 bytes)
- 2016-06-20-decrypt-instructions-for-all-CryptXXX-ransomware-samples.bmp (3,686,454 bytes)
- 2016-06-20-decrypt-instructions-for-all-CryptXXX-ransomware-samples.html (36,201 bytes)
- 2016-06-20-decrypt-instructions-for-all-CryptXXX-ransomware-samples.txt (1,755 bytes)
- 2016-06-20-page-from-contaratosbeach.gr-with-injected-pseudoDarkleech-script.txt (145,733 bytes)
- 2016-06-20-page-from-salentoeasy.it-with-injected-pseudoDarkleech-script.txt (16,546 bytes)
- 2016-06-20-pseudoDarkleech-Neutrino-EK-flash-exploit-after-contaratosbeach_gr.swf (82,983 bytes)
- 2016-06-20-pseudoDarkleech-Neutrino-EK-flash-exploit-after-salentoeasy_it.swf (82,941 bytes)
- 2016-06-20-pseudoDarkleech-Neutrino-EK-landing-page-after-contaratosbeach_gr.txt (801 bytes)
- 2016-06-20-pseudoDarkleech-Neutrino-EK-landing-page-after-salentoeasy_it.txt (819 bytes)
- 2016-06-20-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (443,904 bytes)
NOTES:
- A list of Proofpoint's blog posts about CryptXXX ransomware can be found here.
- Background on the Afraidgate campaign is here.
- Background on the EITest campaign is here.
- Background on the pseudoDarkleech campaign is here.
- A blog about campaigns switching from Angler EK to Neutrino EK is here.
- Compromised websites for today's first two pseudoDarkleech infections were found on malwaredomainlist[.]com (2025 note: This site is no longer online).
- The chipdating[.]link URL used in malvertising, still active and causing Rig EK, was tweeted by @malekal_morte (link).
- The referer for the other Rig EK pcap was found on Broadanalysis[.]com (2025 note: This site is no longer online).
- Of note, the CryptXXX ransomware sample from today's last pcap of Neutrino EK sending CryptXXX ransomware (using the hopto[.]org redirect) makes me think CryptXXX ransomware was updated.
TRAFFIC
ASSOCIATED DOMAINS:
- 93.114.65[.]96 port 80 - ac84[.]ro - Redirect/Gate to Rig EK
- 46.30.47[.]121 port 80 - et.pictureyourselfhome[.]com - Rig EK
- 62.210.192[.]114 port 80 - chipdating[.]link - Malvertising-related gate to Rig EK
- 46.30.46[.]27 port 80 - biomasspelletplant6[.]xyz - Malvertising-related gate to Rig EK
- 46.30.46[.]27 port 80 - artisticplaces[.]net - Malvertising-related gate to Rig EK
- 46.30.47[.]121 port 80 - ds.prideontheseas[.]com - Rig EK
- 115.28.36[.224 port 80 - www.doswf[.]com - GET /copyright/files/c.c - Post-infection traffic
- 185.93.185[.]230 port 80 - sgrhsgeroihgrseishdkigasdj[.]xyz - Sundown EK
- 185.93.185[.]230 port 80 - serouihorshgouirsgdkiga[.]xyz - Sundown EK (sending payload)
- 46.185.173[.]25 port 80 - galop.serviciosgeologicos[.]com[.]ar - Afraidgate redirect
- 5.135.252[.]99 port 80 - montbelv.morgansltd[.]com - Neutrino EK (Afraidgate)
- 85.93.0[.]43 port 80 - mionne[.]tk - EITest gate
- 74.208.173[.]38 port 80 - neopyralidarumuncacheable.morgansdecorators[.]com - Neutrino EK (EITest & pseudoDarkleech)
- 188.0.236[.]7 port 443 - CryptXXX ransomware callback (attempted TCP connections, no response)
- 85.25.194[.]116 port 443 - CryptXXX ransomware callback (attempted TCP connections, no response)
- 83.217.27[.]178 port 80 - lklhmmtev.hopto[.]org - GET /wordpress/?ARX8 - hopto[.]org gate with pseudoDarkleech script
- 74.208.155[.]61 port 80 - inknee.morgansruthin[.]co[.]uk - Neutrino EK
- 185.49.68[.]215 port 443 - CryptXXX ransomware callback traffic (custom encoded)
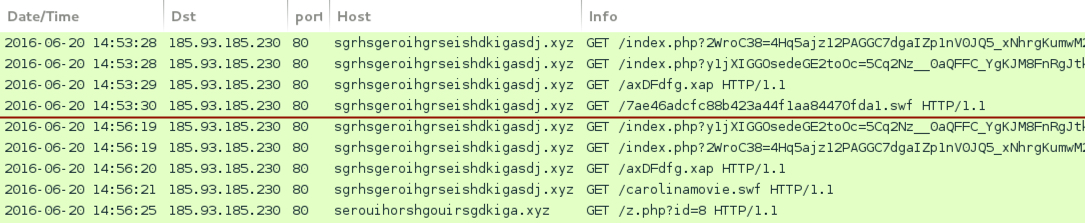
Shown above: Sundown EK. Two tries. No infection the first time using an IE11 setup. Got it later using IE8.
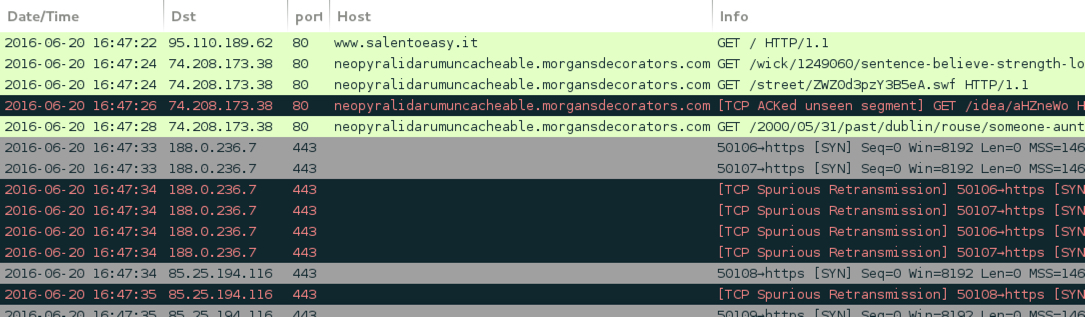
Shown above: pseudoDarkleech Neutrino EK sends CryptXXX ransomware, example 1.
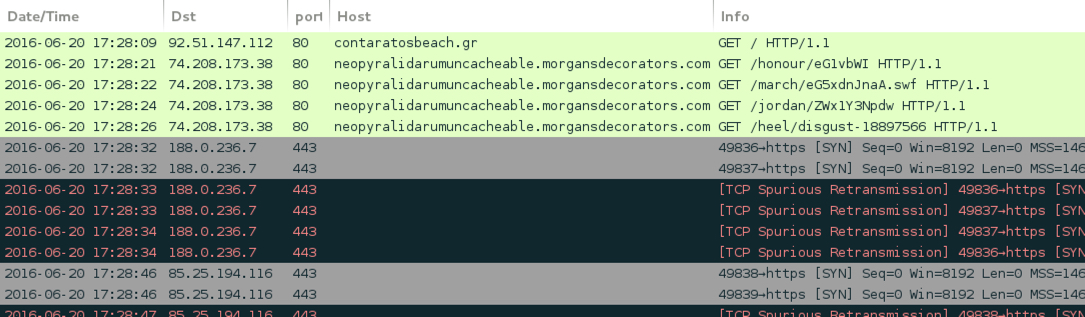
Shown above: pseudoDarkleech Neutrino EK sends CryptXXX ransomware, example 2.
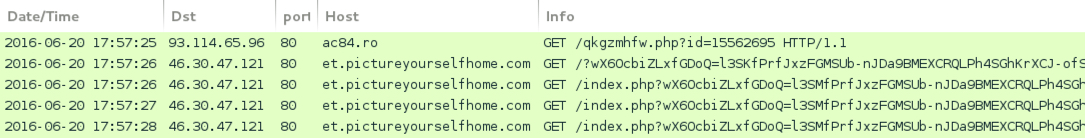
Shown above: Rig EK infection chain after veiwing monavocatparis[.]fr.
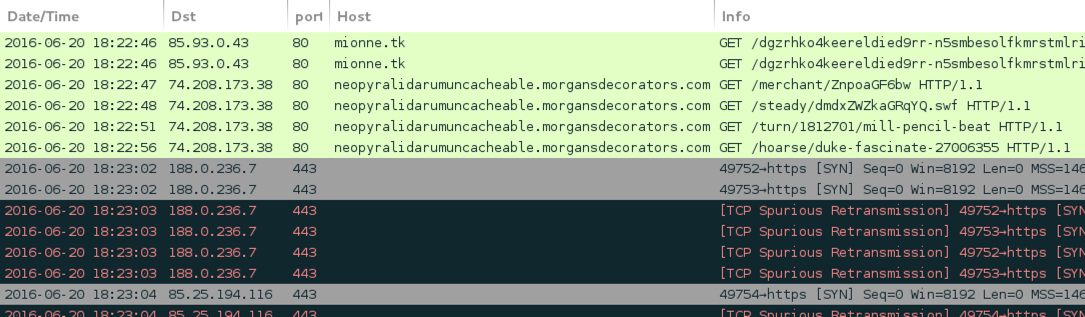
Shown above: EITest Neutrino EK sends CryptXXX ransomware.
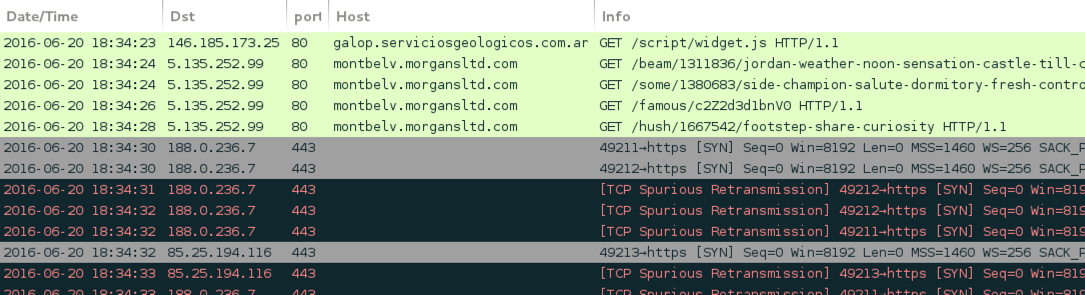
Shown above: Afraidgate Neutrino EK sends CryptXXX ransomware.
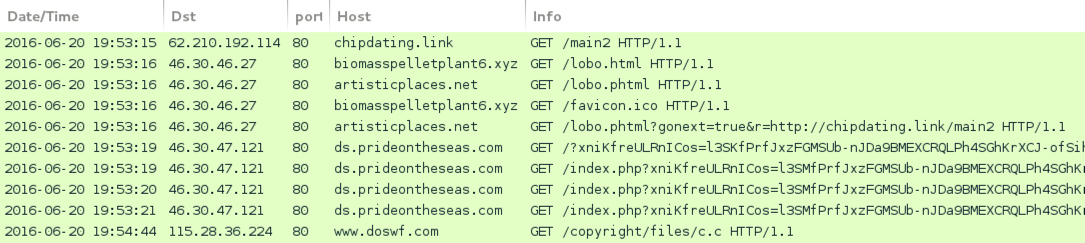
Shown above: Rig EK infection chain after veiwing chipdating[.]link URL.
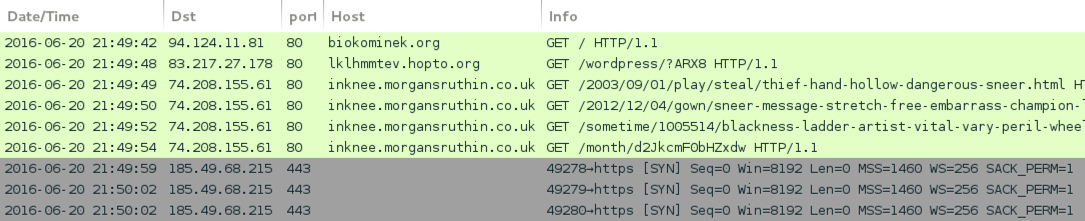
Shown above: pseudoDarkleech Neutrino EK with hopto[.]org gate sends CryptXXX ransomware.
Click here to return to the main page.
