2016-06-21 - DATA DUMP - NEUTRINO EK SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-21-Neutrino-EK-4-pcaps.zip 3.0 MB (3,035,401 bytes)
- 2016-06-21-Afraidgate-Neutrino-EK-sends-CryptXXX-ransomware.pcap (1,166,861 bytes)
- 2016-06-21-EITest-Neutrino-EK-sends-CryptXXX-ransomware.pcap (1,184,332 bytes)
- 2016-06-21-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-fsm-europe_eu.pcap (447,648 bytes)
- 2016-06-21-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-xenon_com_au.pcap (446,789 bytes)
- 2016-06-21-Neutrino-EK-malware-and-artifacts.zip 1.1 MB (1,136,136 bytes)
- 2016-06-21-Afraidgate-CryptXXX-ransomware-decrypt-instructions.bmp (8,294,454 bytes)
- 2016-06-21-Afraidgate-CryptXXX-ransomware-decrypt-instructions.html (36,201 bytes)
- 2016-06-21-Afraidgate-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-06-21-Afraidgate-Neutrino-EK-flash-exploit.swf (82,631 bytes)
- 2016-06-21-Afraidgate-Neutrino-EK-landing-page.txt (817 bytes)
- 2016-06-21-Afraidgate-Neutrino-EK-payload-CryptXXX-ransomware.dll (303,104 bytes)
- 2016-06-21-Afraidgate-galop.serviciosgeologicos_com_ar-script-widget.js.txt (231 bytes)
- 2016-06-21-EITest-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-06-21-EITest-CryptXXX-ransomware-decrypt-instructions.html (36,201 bytes)
- 2016-06-21-EITest-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-06-21-EITest-Neutrino-EK-flash-exploit.swf (82,632 bytes)
- 2016-06-21-EITest-Neutrino-EK-landing-page.txt (817 bytes)
- 2016-06-21-EITest-Neutrino-EK-payload-CryptXXX-ransomware.dll (303,104 bytes)
- 2016-06-21-EITest-flash-redirect-from-dertyt_ml.swf (15,832 bytes)
- 2016-06-21-page-from-fsm-europe_eu-with-injected-pseudoDarkleech-script.txt (82,298 bytes)
- 2016-06-21-page-from-jkanime_net-with-injected-Afraidgate-script.txt (122,934 bytes)
- 2016-06-21-page-from-ladepresion_org-with-injected-EITest-script.txt (41,907 bytes)
- 2016-06-21-page-from-xenon_com_au-with-injected-pseudoDarkleech-script.txt (56,463 bytes)
- 2016-06-21-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.bmp (8,294,454 bytes)
- 2016-06-21-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.html (36,201 bytes)
- 2016-06-21-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-06-21-pseudoDarkleech-Neutrino-EK-flash-exploit-after-fsm-europe_eu.swf (82,626 bytes)
- 2016-06-21-pseudoDarkleech-Neutrino-EK-flash-exploit-after-xenon_com_au.swf (82,629 bytes)
- 2016-06-21-pseudoDarkleech-Neutrino-EK-landing-page-after-fsm-europe_eu.txt (803 bytes)
- 2016-06-21-pseudoDarkleech-Neutrino-EK-landing-page-after-xenon_com_au.txt (893 bytes)
- 2016-06-21-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (303,104 bytes)
NOTES:
- A list of Proofpoint's blog posts about CryptXXX ransomware can be found here.
- Background on the Afraidgate campaign is here.
- Background on the EITest campaign is here.
- Background on the pseudoDarkleech campaign is here.
- A blog about campaigns switching from Angler EK to Neutrino EK is here.
- Compromised websites for today's two pseudoDarkleech infections were found on malwaredomainlist[.]com (2025 note: this site is no longer online).
- The compromised website for today's Afraidgate traffic was found in a report published by Forcepoint (2025 note: this page is no longer available).
- The compromised website for today's EITest traffic was found on Broadanalysis[.]com (2025 note: this site is no longer online).
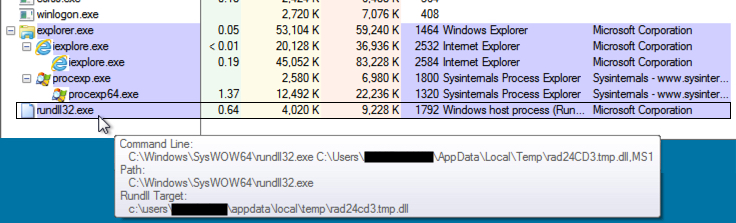
- CryptXXX ransomware infections from Neutrino EK are no longer copying rundll32.exe to the same folder as the CryptXXX ransomware .dll file and renaming it.
- In today's infections, C:\Windows\SysWOW64\rundll32.exe loaded the CryptXXX ransomware .dll file.
Shown above: An example of rundll32.exe and the CryptXXX ransomware .dll file in Process Explorer.
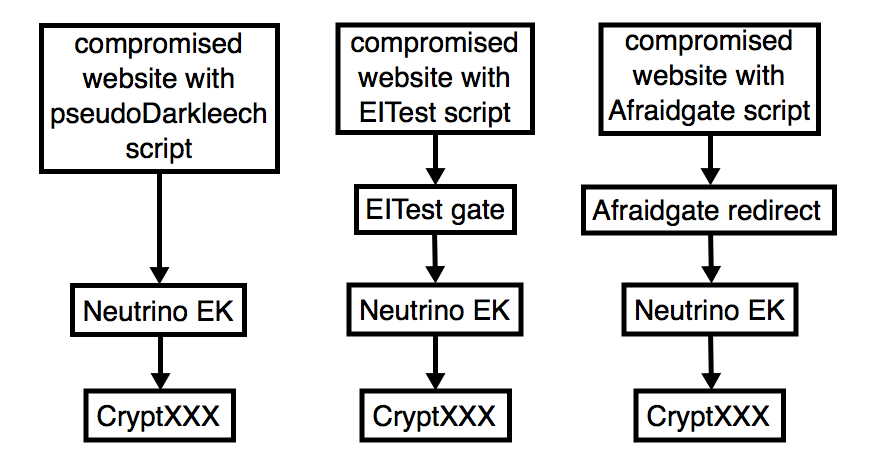
Shown above: Flow charts for these Neutrino EK --> CryptXXX ransomware infections.
TRAFFIC
ASSOCIATED DOMAINS:
- 146.185.173[.]25 port 80 - galop.serviciosgeologicos[.]com-.]ar - GET /script/widget.js - Afraidgate redirect
- 85.93.0[.]43 port 80 - dertyt[.]ml - EITest gate
- 74.208.77[.]101 port 80 - contentview.rtbb[.]co[.]uk - Neutrino EK from the pseudoDarkleech pcaps
- 74.208.166[.]84 port 80 - faro0prokaryo.rubymcguire[.]co[.]uk - Neutrino EK from the Afraidgate pcap
- 74.208.161[.]216 port 80 - miserons-burchten.scillcharity[.]co[.]uk - Neutrino EK from the EITest pcap
- 185.49.68[.]215 port 443 - CryptXXX ransomware callback traffic from all the pcaps
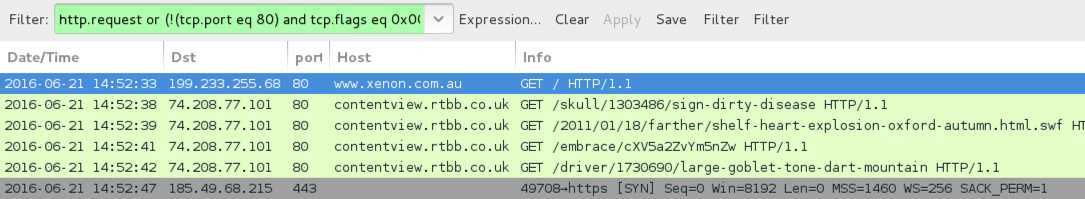
Shown above: pseudoDarkleech --> Neutrino EK --> CryptXXX ransomware infection after viewing xenon[.]com[.]au.
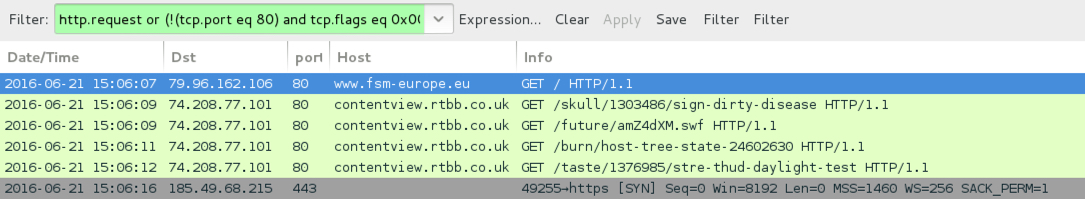
Shown above: pseudoDarkleech --> Neutrino EK --> CryptXXX ransomware infection after viewing fsm-europe[.]eu.
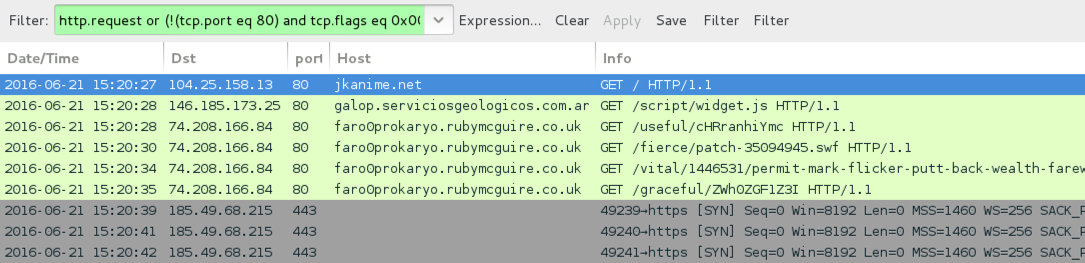
Shown above: Afraidgate --> Neutrino EK --> CryptXXX ransomware infection after jkanime.net.
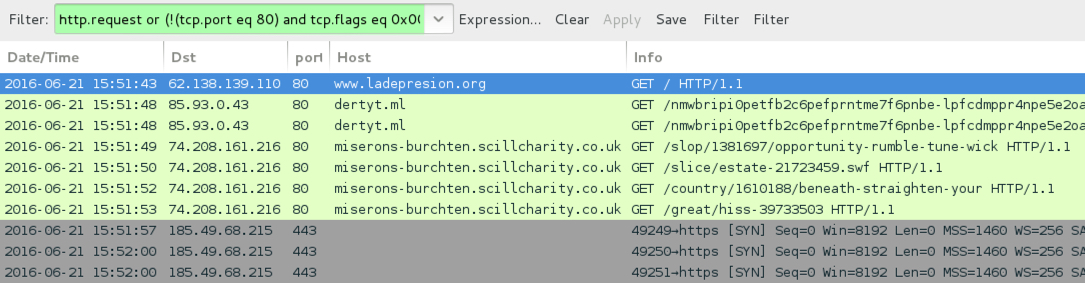
Shown above: EITest --> Neutrino EK --> CryptXXX ransomware infection after ladepresion.org.
IMAGES
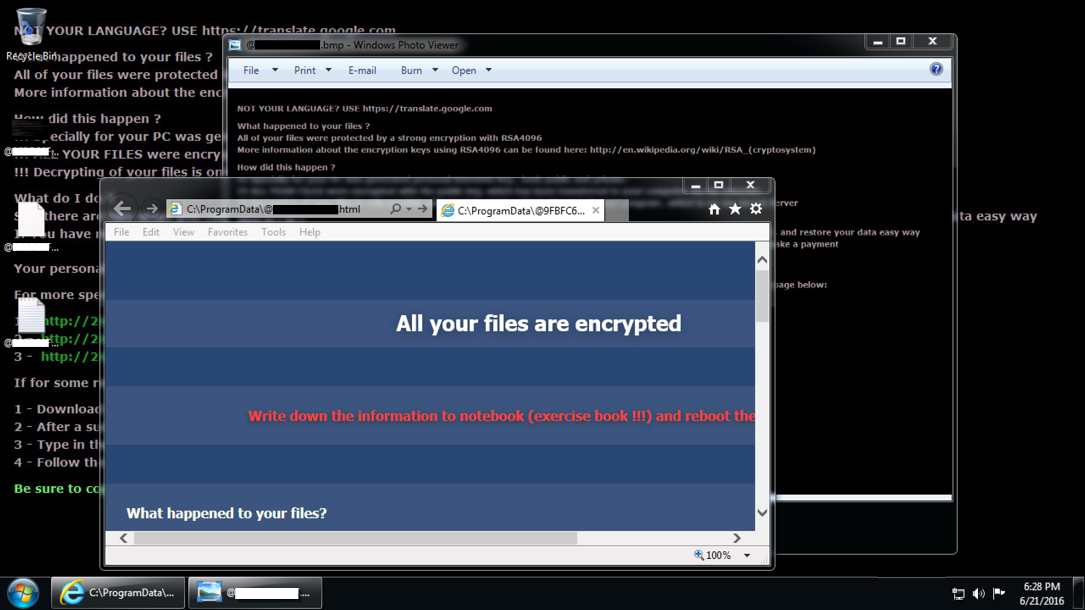
Shown above: An example of an infected Windows desktop, rebooted after one of today's Neutrino EK --> CryptXXX ransomware infections.
Click here to return to the main page.