2016-07-01 - NEUTRINO EK AND "REALSTATISTICS" GATE CHANGE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- Since yesterday (2016-06-30), the "realstatistics" gate leading to Neutrino EK has changed from realstatistics.info to realstatistics.pro. See below for details.
- Background on the pseudoDarkleech campaign is available here.
- Of note, there is some significant packet loss in the first pseudoDarkleech pcap for today's blog.
ASSOCIATED FILES:
- 2016-07-01-Neutrino-EK-sends-CryptXXX-ransomware-3-pcaps.zip 1.7 MB (1,698,410 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-gennaroespositomilano_it.pcap (715,824 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-second-example.pcap (1,136,508 bytes)
- 2016-07-01-realstatistics-gate-traffic-after-tne_mx.pcap (6,655 bytes)
- 2016-07-01-page-from-gennaroespositomilano_it-with-injected-pseudoDarkleech-script.txt (15,990 bytes)
- 2016-07-01-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-07-01-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.html (36,201 bytes)
- 2016-07-01-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-flash-exploit-after-gennaroespositomilano_it.swf (86,405 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-flash-exploit-second-example.swf (85,196 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-landing-page-after-gennaroespositomilano_it.txt (1,025 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-landing-page-second-example.txt (1,105 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-after-gennaroespositomilano_it.dll (458,752 bytes)
- 2016-07-01-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-second-example.dll (368,640 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
- tne[.]mx - compromised site with injected script pointing to a "realstatistics" gate
- 5.199.130[.]155 port 80 - realstatistics[.]pro - GET /js/analytics.php?id=123 - "realstatistics" gate
- www.gennaroespositomilano[.]it - compromised site with injected script from the pseudoDarkleech campaign
- 69.162.100[.]198 port 80 - koushuu.lumenmaster[.]co[.]uk - Neutrino EK
- 185.49.68[.]215 port 443 - CryptXXX ransomware callback traffic
- [information removed] - another compromised site with injected script from the pseudoDarkleech campaign
- 85.25.160[.]174 port 80 - personssastucieuses.maharajatandoori[.]net - Neutrino EK
- 185.49.68[.]215 port 443 - CryptXXX ransomware callback traffic
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 8417423f6519a42ca114d974d86d30f5262c26eb4ecee76b424e05c6418c1b73
File name: 2016-07-01-pseudoDarkleech-Neutrino-EK-flash-exploit-after-gennaroespositomilano_it.swf
- SHA256 hash: 711298374c87bfbf19d3cbefcd24415978fbc914dba411a80911438831374eca
File name: 2016-07-01-pseudoDarkleech-Neutrino-EK-flash-exploit-second-example.swf
MALWARE PAYLOADS:
- SHA256 hash: cbe0262667f1bc96489641bd96c2fd704085555f90aab44132d8c0dfe54da8ca
File name: 2016-07-01-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-after-gennaroespositomilano_it.dll
- SHA256 hash: 39ed07e5b0e326bd49402ed12b702756640477b43f76da6b21e6c2a314c086f8
File name: 2016-07-01-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-second-example.dll
IMAGES
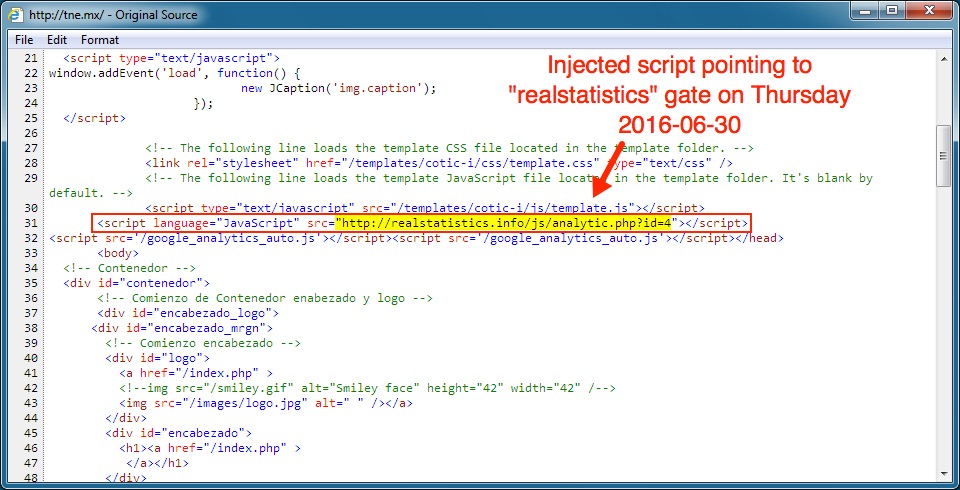
Shown above: Injected script pointing to the "realstatistics" gate from a compromised website yesterday.
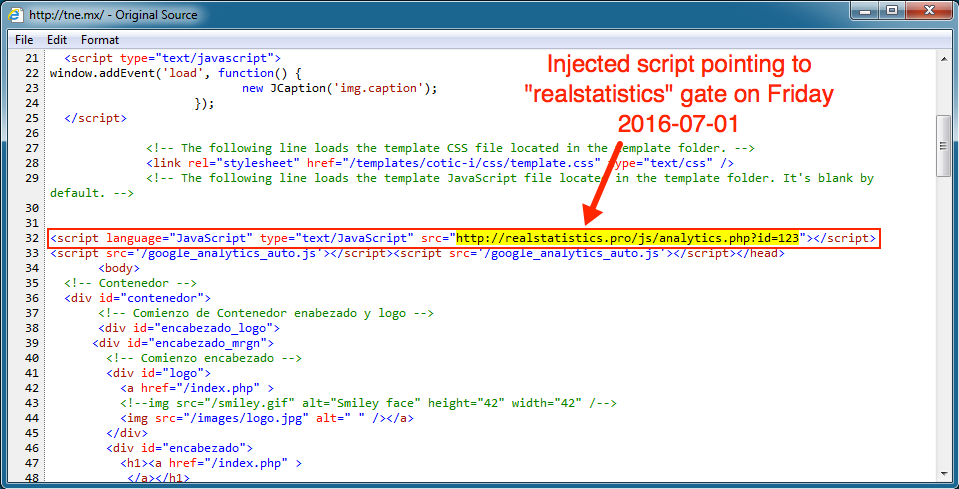
Shown above: Injected script from the same site pointing to a different "realstatistics" gate today.
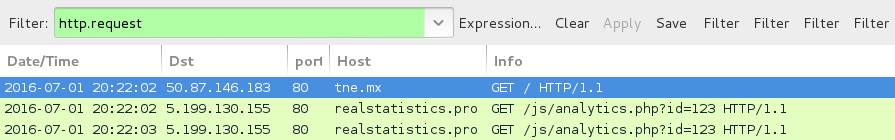
Shown above: As you can see, the new "realstatistics" domain is using a different IP address and a slightly different URL.
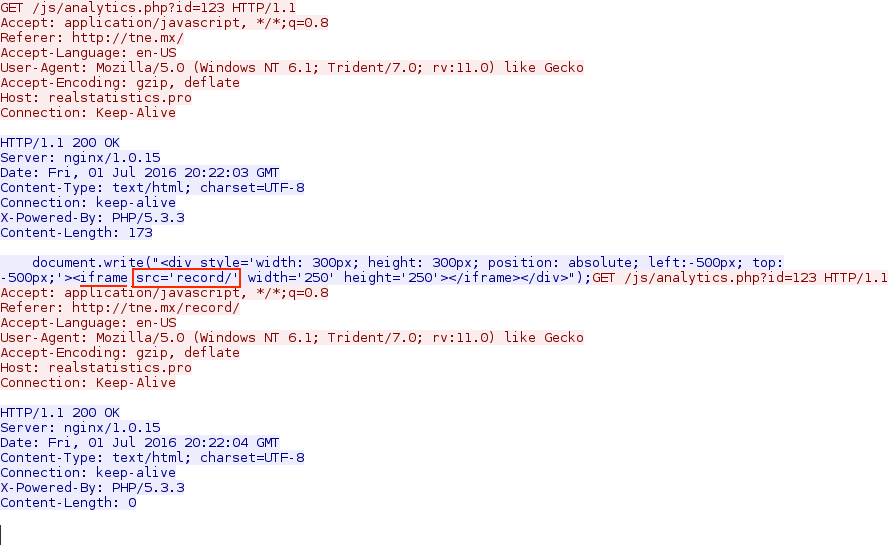
Shown above: Unfortunately, I haven't been able to get past this new gate. The iframe looks like it's using a placeholder.
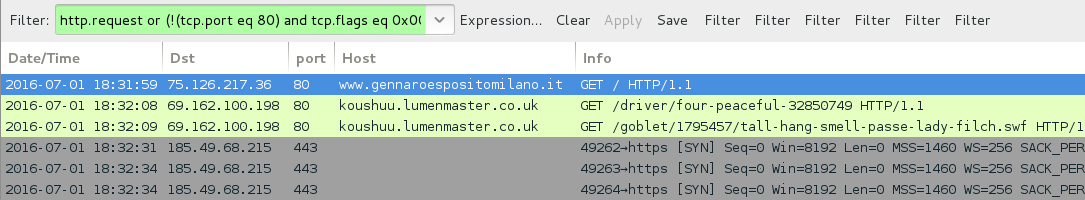
Shown above: Neutrino EK and CryptXXX ransomware traffic kicked off by viewing gennaroespositomilano[.]it.
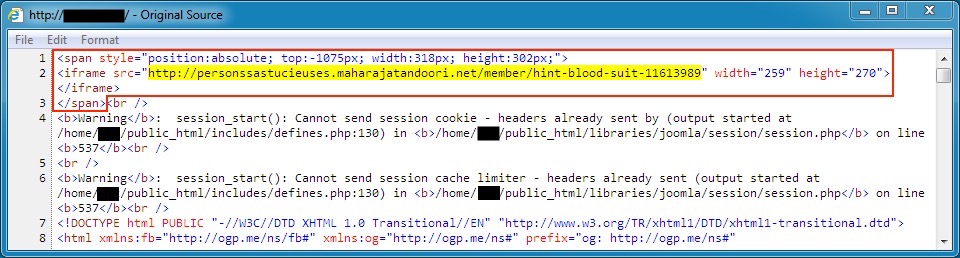
Shown above: Injected pseudoDarkleech script in a page from a second compromised site.
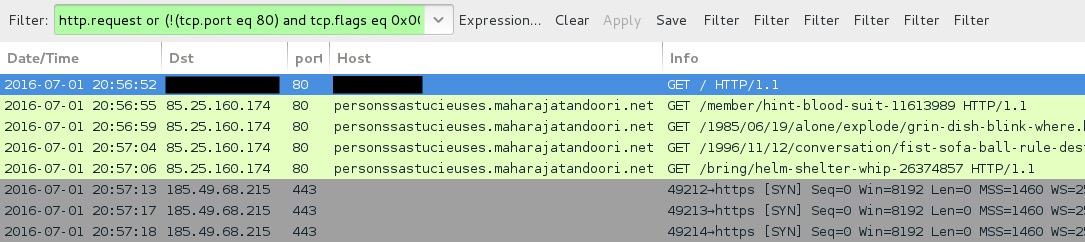
Shown above: Neutrino EK and CryptXXX ransomware traffic kicked off by viewing the second compromised site.
Click here to return to the main page.
