2016-07-05 - MAGNITUDE EK FROM 62.138.5[.]199 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-05-Magnitude-EK-sends-Cerber-ransomware.pcap.zip 723.1 kB (723,054 bytes)
- 2016-07-05-Magnitude-EK-sends-Cerber-ransomware.pcap (1,542,877 bytes)
- 2016-07-05-Magnitude-EK-and-Cerber-ransomware-files.zip 1.4 MB (1,422,737 bytes)
- 2016-07-05-Cerber-ransomware-decryption-instructions.bmp (2,647,454 bytes)
- 2016-07-05-Cerber-ransomware-decryption-instructions.html (12,127 bytes)
- 2016-07-05-Cerber-ransomware-decryption-instructions.txt (10,373 bytes)
- 2016-07-05-Magnitude-EK-flash-exploit.swf (22,013 bytes)
- 2016-07-05-Magnitude-EK-flash-redirect.swf (717 bytes)
- 2016-07-05-Magnitude-EK-payload-Cerber-ransomware.exe (377,078 bytes)
NOTES:
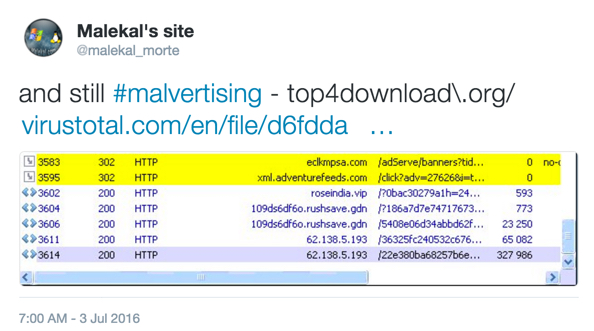
- Thanks to @malekal_morte for the Twitter post that helped me get today's traffic.
Shown above: Tweet from @malekal_morte on 2016-07-03.
TRAFFIC
ASSOCIATED DOMAINS:
- 91.134.161[.]42 port 80 - top4download[.]org - First gate
- 91.134.161[.]60 port 80 - roseindia[.]vip - Second gate
- 62.138.5[.]199 port 80 - 18a43zad864bo96.armlay[.]gdn - Magnitude EK
- 62.138.5[.]199 port 80 - 62.138.5[.]199 - Magnitude EK
- 216.189.148[.]182 port 80 - 27lelchgcvs2wpm7.asd3r3[.]top - Decrypt instructions site
- 31.184.232[.]0 to 31.184.239[.]255 (31.184.232[.]0/21) - traffic over UDP port 6892 caused by Cerber ransomware
OTHER DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- 216.189.148[.]182 - 27lelchgcvs2wpm7.azwsxe[.]top
- 216.189.148[.]182 - 27lelchgcvs2wpm7.fgkr56[.]top
- 216.189.148[.]182 - 27lelchgcvs2wpm7.adevf4[.]top
- 217.197.83[.]19 - 27lelchgcvs2wpm7.onion[.]to
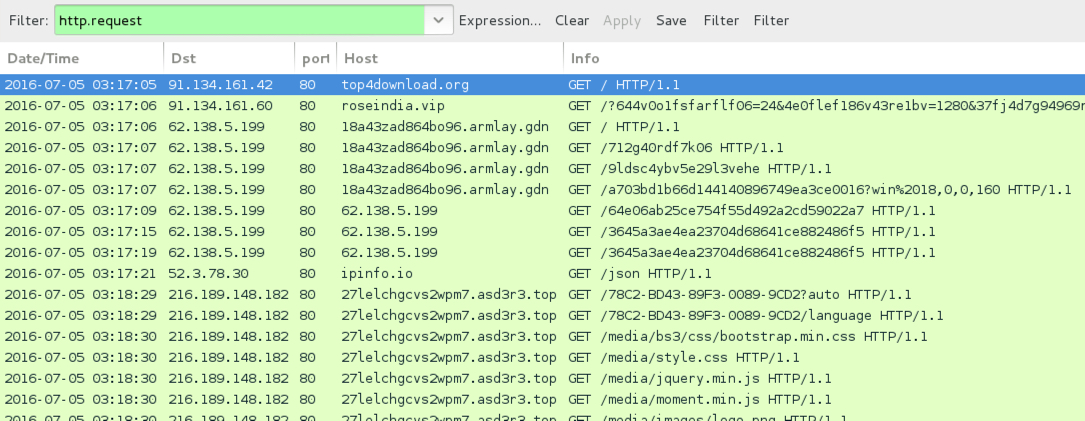
Shown above: Traffic from today's infection filtered in Wireshark.
FILE HASHES
FLASH REDIRECT AND EXPLOIT:
- SHA256 hash: c31720ad18a49b0f59cc31cb20a50ac14a21f7a602ebf960d6fc29ab0af8b01c
File name: 2016-07-05-Magnitude-EK-flash-redirect.swf
- SHA256 hash: 1885dff2158ba50e8d32b0363b583ed627d8518f3d904c95106edb7fd5deed21
File name: 2016-07-05-Magnitude-EK-flash-exploit.swf
MALWARE PAYLOAD:
- SHA256 hash: 8564b5286ae6282be441dacad9de9215f4498fca94def27b30c1291f1326cf32
File name: 2016-07-05-Magnitude-EK-payload-Cerber-ransomware.exe
Click here to return to the main page.