2016-07-11 - EK DATA DUMP (MAGNITUDE EK, NEUTRINO EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-11-EK-data-dump-3-pcaps.zip 2.1 MB (20,879,38 bytes)
- 2016-07-11-Afraidgate-Neutrino-EK-sends-CryptXXX-ransomware.pcap (1,104,777 bytes)
- 2016-07-11-Magnitude-EK-sends-Cerber-ransomware.pcap (991,030 bytes)
- 2016-07-11-Neutrino-EK-sends-Gootkit-malware.pcap (426,467 bytes)
- 2016-07-11-EK-data-dump-malware-and-artifacts.zip 910.6 kB (910,631 bytes)
- 2016-07-11-Afraidgate-CryptXXX-ransomware-decrypt-instructions.BMP (3,686,454 bytes)
- 2016-07-11-Afraidgate-CryptXXX-ransomware-decrypt-instructions.HTML (18,215 bytes)
- 2016-07-11-Afraidgate-Neutrino-EK-flash-exploit.swf (82,369 bytes)
- 2016-07-11-Afraidgate-Neutrino-EK-landing-page.txt (2,076 bytes)
- 2016-07-11-Afraidgate-Neutrino-EK-payload-CryptXXX-ransomware.dll (483,328 bytes)
- 2016-07-11-Cerber-ransomware-decryption-instructions.html (12,414 bytes)
- 2016-07-11-Cerber-ransomware-decryption-instructions.txt (10,522 bytes)
- 2016-07-11-Cerber-ransomware-decryption-instructions.vbs (234 bytes)
- 2016-07-11-Magnitude-EK-flash-exploit.swf (58,686 bytes)
- 2016-07-11-Magnitude-EK-flash-redirect.swf (720 bytes)
- 2016-07-11-Magnitude-EK-landing-page.txt (706 bytes)
- 2016-07-11-Magnitude-EK-more-html.txt (22,901 bytes)
- 2016-07-11-Magnitude-EK-payload-Cerber-ransomware.exe (293,656 bytes)
- 2016-07-11-other-Neutrino-EK-flash-exploit.swf (84,243 bytes)
- 2016-07-11-other-Neutrino-EK-landing-page.txt (2,100 bytes)
- 2016-07-11-other-Neutrino-EK-payload-Gootkit.exe (198,144 bytes)
NOTES:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated
- 2016-07-07 - Bleeping Computer: New CryptXXX changes name to Microsoft Decryptor
- 2016-07-08 - Malware-traffic-analysis.net: CryptXXX updated again, now looking more like it did before previous change, also changes back to "UltraDeCrypter".
- Tipped off on today's Magnitude EK activity by a tweet from @malekal_morte which can be found here.
- Other Neutrino EK activity also found due to a tweet from @malekal_morte available here.
- Background on the Afraidgate campaign (now using Neutrino EK instead of Angler) is available here.
TRAFFIC
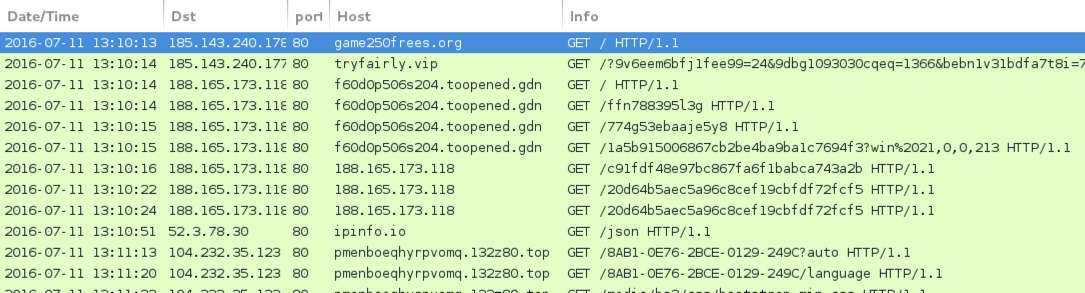
Shown above: Traffic from the first pcap filtered in Wireshark (Magnitude EK sends Cerber ransomware).
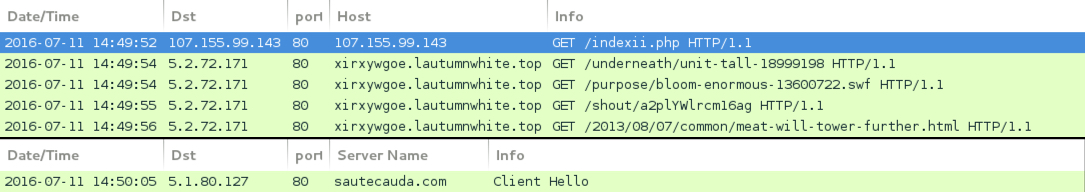
Shown above: Traffic from the second pcap filtered in Wireshark (other Neutrino EK sends Gootkit).
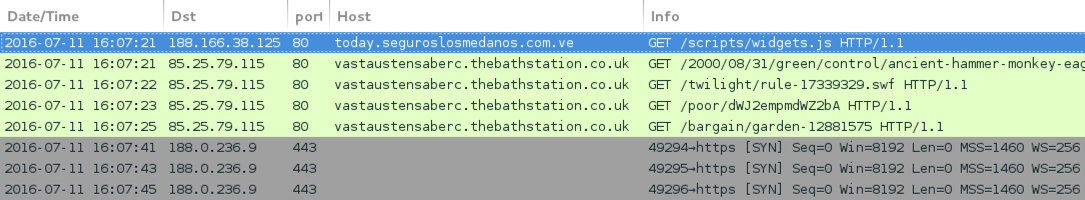
Shown above: Traffic from the third pcap filtered in Wireshark (Afraidgate Neutrino EK sends CryptXXX ransomware).
ASSOCIATED DOMAINS:
- 185.143.240[.]178 port 80 - game250frees[.]org - Compromised domain
- 185.143.240[.]177 port 80 - tryfairly[.]vip - profiling gate
- 188.165.173[.]118 port 80 - f60d0p506s204.toopened[.]gdn - Magnitude EK
- 188.165.173[.]118 port 80 - 188.165.173[.]118 - Magnitude EK
- ipinfo[.]io - IP address check by Cerber ransomware
- 38.141.234[.]0 through 38.141.235[.]255 (38.141.234[.]0/23) - traffic over UDP port 6892 caused by Cerber ransomware
- 107.155.99[.]143 port 80 - 107.155.99[.]143 - GET /indexii.php - Gate to Neutrino EK
- 5.2.72[.]171 port 80 - xirxywgoe.lautumnwhite[.]top - Neutrino EK
- 5.1.80[.]127 port 80 - sautecauda[.]com - SSL traffic over port 80 (Gootkit callback)
- 188.166.38[.]125 port 80 - today.seguroslosmedanos[.]com[.]ve - GET /scripts/widgets.js - Gate to Neutrino EK
- 85.25.79[.]115 port 80 - vastaustensaberc.thebathstation[.]co[.]uk - Neutrino EK
- 188.0.236[.]9 port 443 - CryptXXX ransomware post-infection traffic (custom encoded, not SSL)
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- pmenboeqhyrpvomq.132z80[.]top - domain from today's Cerber ransomware sample
- pmenboeqhyrpvomq.bigfooters[.]loan - domain from today's Cerber ransomware sample
- pmenboeqhyrpvomq.marksgain[.]kim - domain from today's Cerber ransomware sample
- pmenboeqhyrpvomq.swissprogramms[.]bid - domain from today's Cerber ransomware sample
- pmenboeqhyrpvomq[.]onion[.]to - domain from today's Cerber ransomware sample
- wxaga5ybn5wjcn3x[.]onion[.]to - domain from today's Afraidgate CryptXXX ransomware sample
- wxaga5ybn5wjcn3x[.]onion[.]cab - domain from today's Afraidgate CryptXXX ransomware sample
- wxaga5ybn5wjcn3x[.]onion[.]city - domain from today's Afraidgate CryptXXX ransomware sample
FILE HASHES
FLASH REDIRECTS/EXPLOITS:
- SHA256 hash: 9ecd17a4c0f55aeae2e5cad9bf22fb860327ded04cb025132ce566748604c07d
File name: 2016-07-11-Magnitude-EK-flash-redirect.swf
- SHA256 hash: f16b6835cab9b2157e950bd38075359c0083e57627aa5af67523801137443de8
File name: 2016-07-11-Magnitude-EK-flash-exploit.swf
- SHA256 hash: af82f425c7337a87c6a6d08b05b1f45a7e6e660aa74f83fbca9a04977d5ee269
File name: 2016-07-11-other-Neutrino-EK-flash-exploit.swf
- SHA256 hash: 40d2db7d522c5822107b450e633baab5608b143bc69e9a38a87773b51ae95c24
File name: 2016-07-11-Afraidgate-Neutrino-EK-flash-exploit.swf
PAYLOADS:
- SHA256 hash: 649f06c85b1b9a6ed1d257c21a103e6aa09480706719d86bfb10436654a0b517
File name: 2016-07-11-Magnitude-EK-payload-Cerber-ransomware.exe
- SHA256 hash: d8e05ac76e4723a859a2834372c23714c030d4ce3e39a47511db7fdb7f8b79d4
File name: 2016-07-11-other-Neutrino-EK-payload-Gootkit-malware.exe
- SHA256 hash: d3b1de1efb431e7c7b31f11e1809be97da471054e3b275aaadb6df118b42cab5
File name: 2016-07-11-Afraidgate-Neutrino-EK-payload-CryptXXX-ransomware.dll
Click here to return to the main page.
