2016-07-18 - NEUTRINO EK FROM 185.141.25[.]59 SENDS BANDARCHOR RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-18-Neutrino-EK-sends-Bandarchor-ransomware.pcap.zip 208.7 kB (208,674 bytes)
- 2016-07-18-Neutrino-EK-sends-Bandarchor-ransomware.pcap (231,890 bytes)
- 2016-07-18-Neutrino-EK-and-Bandarchor-ransomware-files.zip 180.4 kB (180,363 bytes)
- 2016-07-18-Bandarchor-ransomware-decryption-instructions.txt (1,216 bytes)
- 2016-07-18-Neutrino-EK-flash-exploit.swf (87,115 bytes)
- 2016-07-18-Neutrino-EK-landing-page.txt (3,779 bytes)
- 2016-07-18-Neutrino-EK-payload-Bandarchor-ransomware.exe (110,714 bytes)
NOTES:
- More information on Bandarchor ransomware can be found here and here.
- Today's Bandarchor ransomware sample uses the same email addresses in the decrypt instructions as the last time I saw it on 2016-07-14.
Shown above: My tipper for this traffic at Malwaredomainlist (2025 note: this site is no longer online).
TRAFFIC
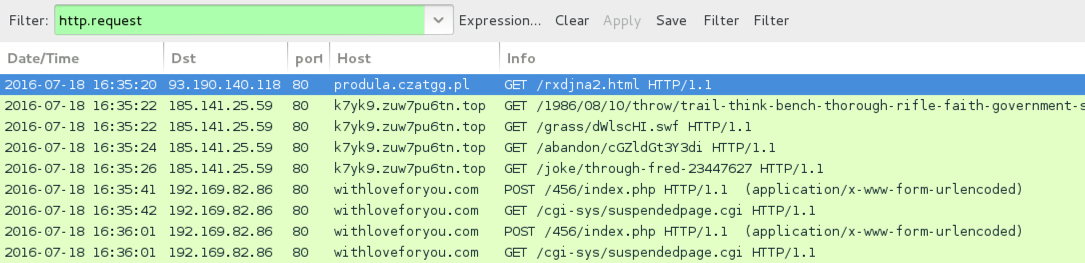
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 93.190.140[.]118 port 80 - produla.czatgg[.]pl - Redirect/gate pointing to Neutrino EK
- 185.141.25[.]59 port 80 - k7yk9.zuw7pu6tn[.]top - Neutrino EK
- 192.169.82[.]86 port 80 - withloveforyou[.]com - Post-infection traffic
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- Primary email: sos@juicylemon[.]biz
- Secondary email: juicylemon@protonmail[.]com
- Bitmessage: BM-NBRCUPTenKgYbLVCAfeVUHVsHFK6Ue2F
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 0c76e232c2e1adf5b8f948a9e9e3db2f16f9a30dfd5cb6b2c4579a6bb7dba72d
File name: 2016-07-18-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 9d33bedd2e837e467b65eca3dfca05e1a4502dd2e032b6f2201a201e675a5eb4
File name: 2016-07-18-Neutrino-EK-payload-Bandarchor-ransomware.exe
Click here to return to the main page.
