2016-07-21 - NEUTRINO EK SENDS BANDARCHOR RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-21-Neutrino-EK-sends-Bandarchor-ransomware-2-pcaps.zip 519.1 kB (519,081 bytes)
- 2016-07-21-Neutrino-EK-sends-Bandarchor-ransomware-first-run.pcap (272,143 bytes)
- 2016-07-21-Neutrino-EK-sends-Bandarchor-ransomware-second-run.pcap (287,868 bytes)
- 22016-07-21-Neutrino-EK-and-Bandarchor-ransomware-files.zip 287.4 kB (287,410 bytes)
- 2016-07-21-Neutrino-EK-flash-exploit-first-run.swf (86,242 bytes)
- 2016-07-21-Neutrino-EK-flash-exploit-second-run.swf (86,242 bytes)
- 2016-07-21-Neutrino-EK-landing-page-first-run.txt (3,793 bytes)
- 2016-07-21-Neutrino-EK-landing-page-second-run.txt (3,911 bytes)
- 2016-07-21-Neutrino-EK-payload-Bandarchor-ransomware-first-and-second-run.exe (163,840 bytes)
NOTES:
- More information on Bandarchor ransomware can be found here and here.
- Like yesterday, today's Bandarchor ransomware sample didn't leave any decryption instructions.
- It just listed the same email addresses as yesterday in the names of the encrypted files (see below).
- Also saw the same post-infection traffic as yesterday.
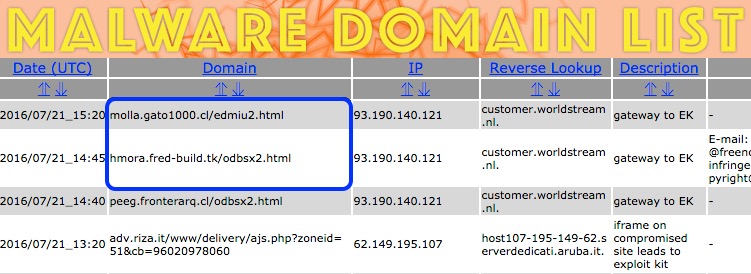
Shown above: My tipper for this traffic at Malwaredomainlist (no longer online).
TRAFFIC
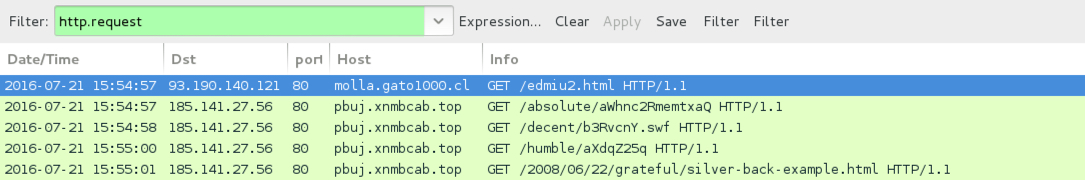
Shown above: Traffic from the first pcap filtered in Wireshark.
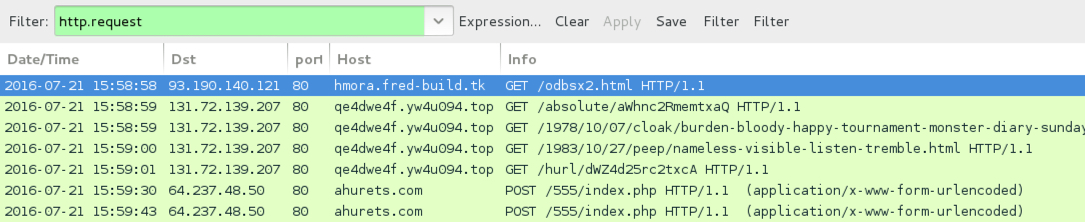
Shown above: Traffic from the second pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 93.190.140[.]121 port 80 - molla.gato1000[.]cl - GET /edmiu2.html - Redirect pointing to Neutrino EK
- 185.141.27[.]56 port 80 - pbuj.xnmbcab[.]top - Neutrino EK
- 93.190.140[.]121 port 80 - hmora.fred-build[.]tk - GET /odbsx2.html - Redirect pointing to Neutrino EK
- 131.72.139[.]207 port 80 - qe4dwe4f.yw4u094[.]top - Neutrino EK
- 64.237.48[.]50 port 80 - ahurets[.]com - POST /555/index.php - Post-infection traffic caused by the Bandarchor ransomware
EMAILS TO GET THE DECRYPT INSTRUCTIONS:
- aes256decoder@protonmail[.]com - First email address generated by the Bandachor ransomware
- decrypt@aesencryption[.]info - Second email address generated by the Bandachor ransomware
FILE HASHES
FLASH FILES:
- SHA256 hash: 166f16f0445bd6320e508a10db73b3b86303b70344d948449979b55307f9af9b
File name: 2016-07-21-Neutrino-EK-flash-exploit-first-run.swf
- SHA256 hash: d2fc8e87bbad08db2bf391e3c56c874d1300dbea123607e0a2dcc083a404dfba
File name: 2016-07-21-Neutrino-EK-flash-exploit-second-run.swf
PAYLOAD:
- SHA256 hash: f3115be9877ef36cafae26f18002528ea63377e5441c3870c02b4a737b9e127b
File name: 2016-07-21-Neutrino-EK-payload-Bandarchor-ransomware-first-and-second-run.exe
IMAGES
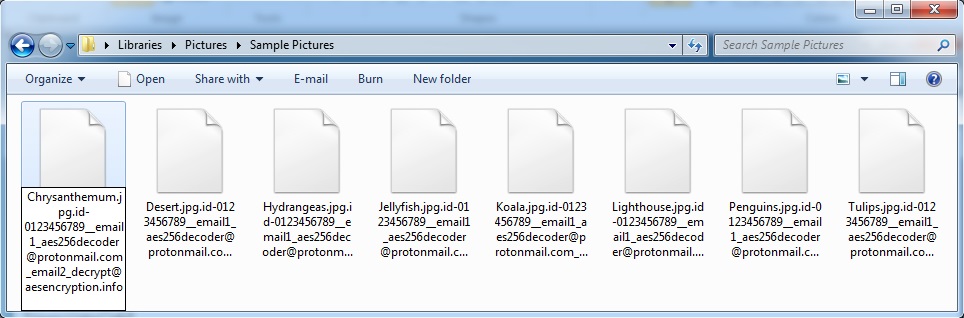
Shown above: Example of the encrypted file names from an infected host.
Shown above: Domain for the second email address was registered on 2016-07-19 through Namecheap.
Click here to return to the main page.
