2016-10-17 - SUNDOWN EK FROM 37.139.47[.]53 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Z2016-10-17-Sundown-EK-sends-Locky-ransomware.pcap.zip 262.0 kB (261,952 bytes)
- 2016-10-17-Sundown-EK-sends-Locky-ransomware.pcap (399,867 bytes)
- 2016-10-17-Sundown-EK-and-Locky-ransomware-files.zip 278.4 kB (278,398 bytes)
- 2016-10-17-Locky-ransomware_HOWDO_text.bmp (149,158 bytes)
- 2016-10-17-Locky-ransomware_HOWDO_text.html (9,899 bytes)
- 2016-10-17-Sundown-EK-flash-exploit.swf (71,545 bytes)
- 2016-10-17-Sundown-EK-landing-page.txt (21,005 bytes)
- 2016-10-17-Sundown-EK-payload-Locky-ransomware.exe (250,880 bytes)
NOTES:
- Thanks to Baber, who tipped me off to this infection chain.
- Aside from the signature hits I got from the ETPRO ruleset indicating this is Sundown EK, I couldn't find anything else related this traffic.
BACKGROUND ON SUNDOWN EK:
- 2015-06-08 - Malware Don't Need Coffee: Fast look at Sundown EK.
- 2015-06-18 - Virus Bulletin: Beta exploit pack: one more piece of crimeware for the infection road!
- 2015-06-25 - ProofPoint Blog: Sundown EK Spreads LuminosityLink RAT: Light After Dark.
- 2016-09-02 - SpiderLabs Blog: Sundown EK - Stealing Its Way to the Top.
- 2016-10-17 - MalwareBytes Blog: New-looking Sundown EK drops Smoke Loader, Kronos banker.
TRAFFIC
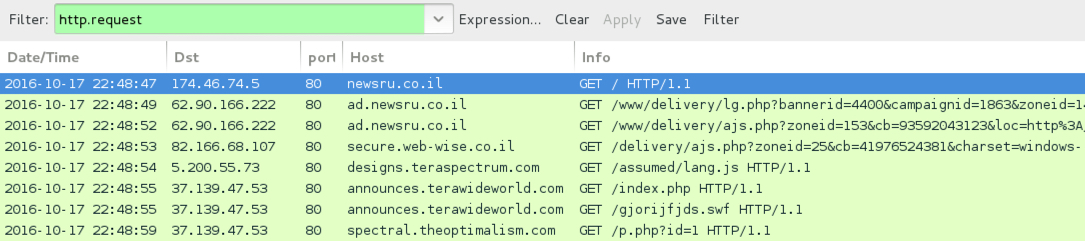
Shown above: Infection traffic filtered in Wireshark.
INITIAL WEBSITE AND AD TRAFFIC CHAIN:
- newsru[.]co[.]il
- ad.newsru[.]co[.]il
- secure.web-wise[.]co[.]il
GATE:
- 5.200.55[.]73 port 80 - designs.teraspectrum[.]com - GET /assumed/lang.js
SUNDOWN EK:
- 37.139.47[.]53 port 80 - announces.terawideworld[.]com - GET /index.php - landing page
- 37.139.47[.]53 port 80 - announces.terawideworld[.]com - GET /gjorijfjds.swf - Flash exploit
- 37.139.47[.]53 port 80 - spectral.theoptimalism[.]com - GET /p.php?id=1 - payload (Locky)
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: f1016d736929c2cbd9265b2d975a4bf8593aafa6c1af5318bef8329b3f869bf6
File name: 016-10-17-Sundown-EK-flash-exploit.swf (71,545 bytes)
PAYLOAD (LOCKY RANSOMWARE):
- SHA256 hash: 04e3cce4775868fcfb497de27979ea077623d0bc9707f86efd86ab0136227d3a
File name: 2016-10-17-Sundown-EK-payload-Locky-ransomware.exe (250,880 bytes)
IMAGES
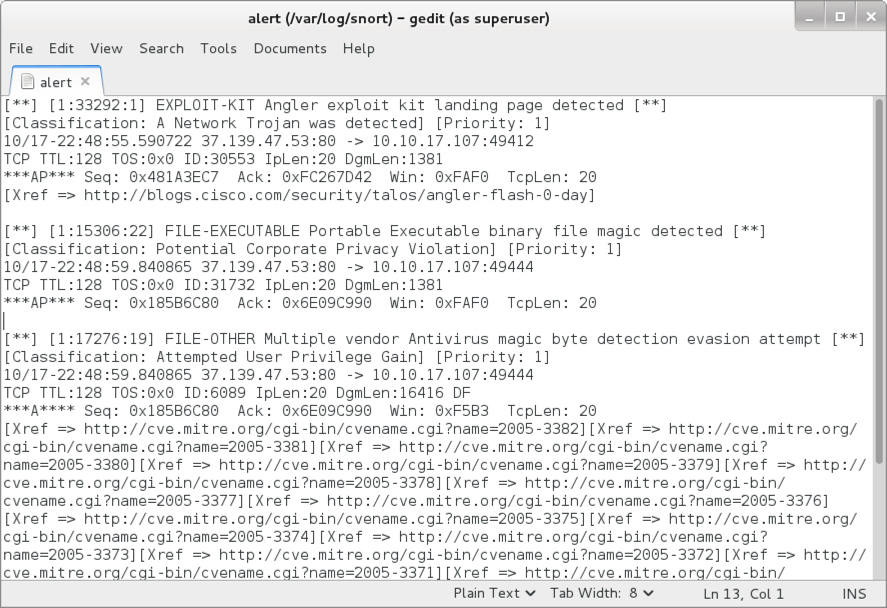
Shown above: Notable alerts on the traffic in Snort using the Snort subscriber ruleset.
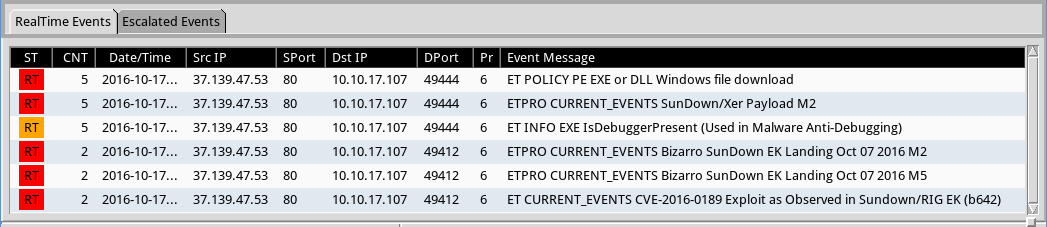
Shown above: Notable alerts on the infection traffic in Security Onion using Suricata and the EmergingThreats Pro ruleset.
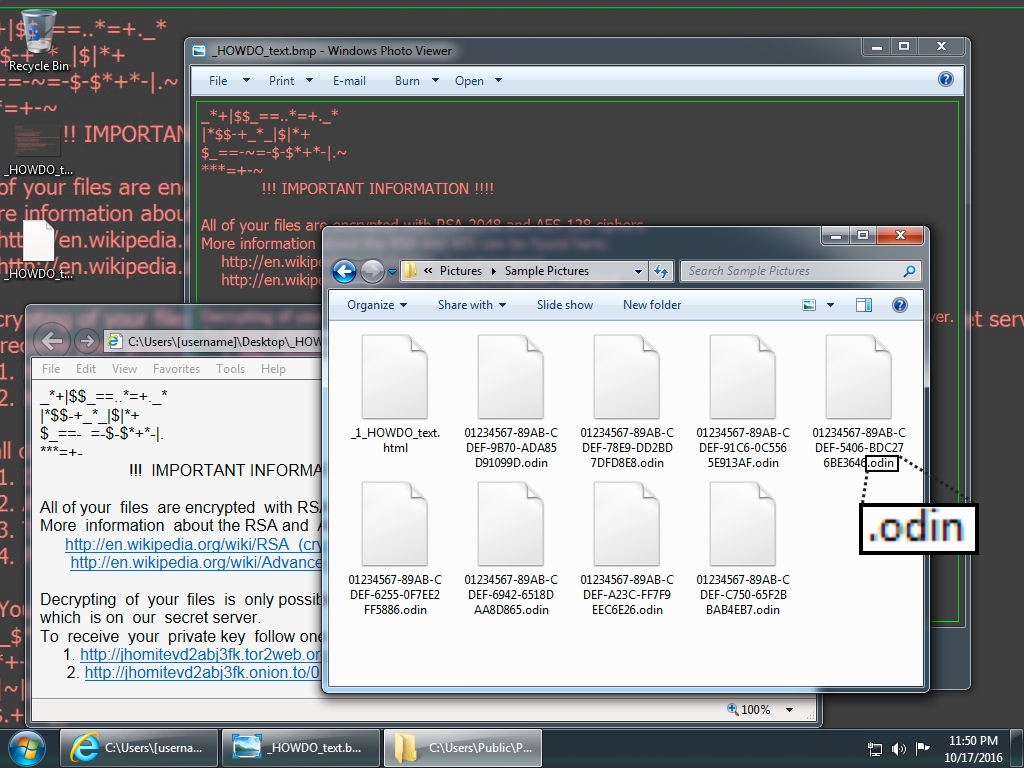
Shown above: Desktop of an infected Windows host after rebooting.
Click here to return to the main page.
