2016-10-26 - JRAT (ADWIND) INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-26-jRAT-infection-traffic.pcap.zip 519.9 kB (519,892 bytes)
- 2016-10-26-jRAT-infection-traffic.pcap (601,883 bytes)
- 2016-10-26-files-from-jRAT-infection.zip 245.9 kB (245,914 bytes)
- 2016-10-26-email-0753-UTC.eml (28,061 bytes)
- FAX NO_278_scan_001_pdf.jar (232,864 bytes)
NOTES:
- Documenting a malicious email I received with a link to jRAT (Adwind) malware.
- This .jar file has the same callback domain as the one I documented on 2016-10-23.
- Today's email also has some of the same header lines as last time.
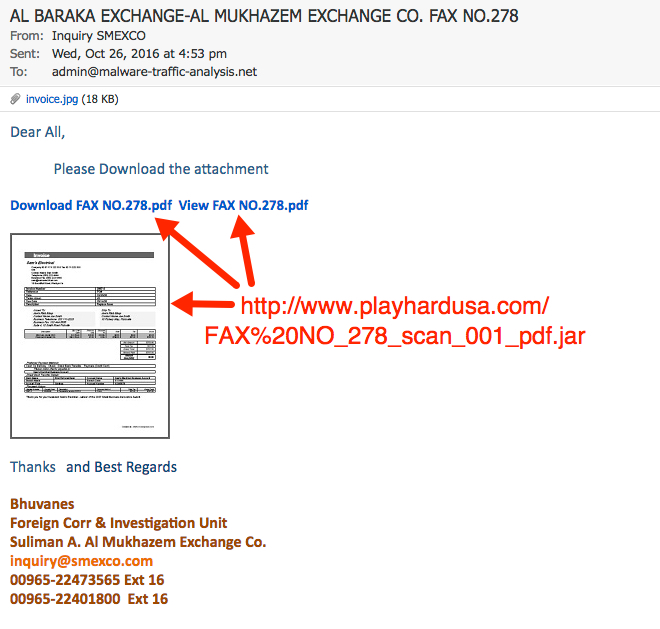
Shown above: Screenshot of the email.
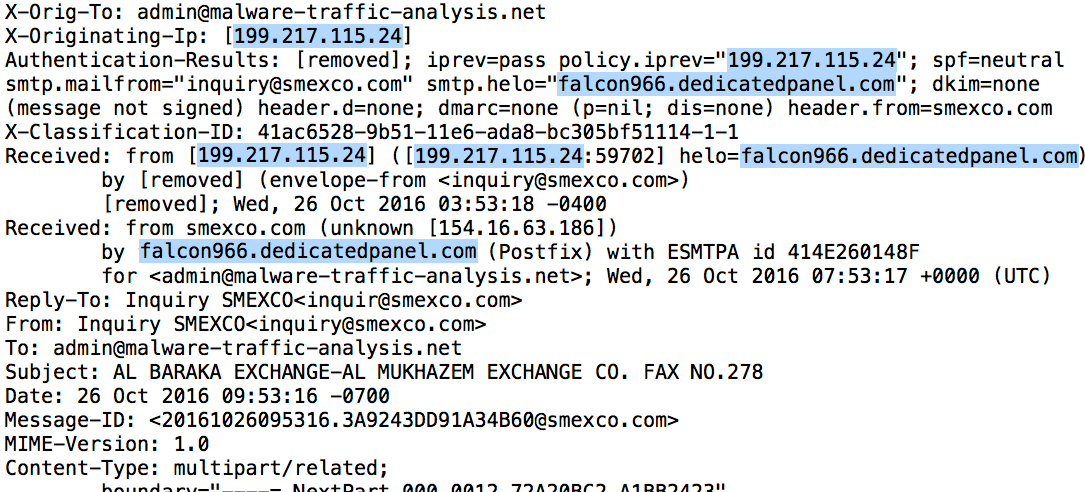
Shown above: Messages headers.
MESSAGE HEADERS:
- Mail server: 199.217.115[.]24 - falcon966.dedicatedpanel[.]com
- Message-ID header: <20161026095316.3A9243DD91A34B60@smexco[.]com>
- Date/time: Wednesday, 2016-10-26 16:53 UTC
- From: <inquir@smexco[.]com>
- To: <admin@malware-traffic-analysis[.]net>
- Subject: AL BARAKA EXCHANGE-AL MUKHAZEM EXCHANGE CO. FAX NO.278
MESSAGE TEXT:
Dear All,
Please Download the attachment
Download FAX NO.278.pdf View FAX NO.278.pdf
Thanks and Best Regards
Bhuvanes
Foreign Corr & Investigation Unit
Suliman A. Al Mukhazem Exchange Co.
inquiry@smexco[.]com
00965-22473565 Ext 16
00965-22401800 Ext 16
TRAFFIC
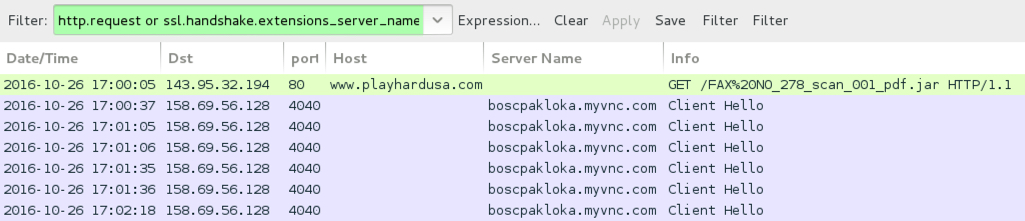
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 143.95.32[.]194 port 80 - www.playhardusa[.]com - GET /FAX%20NO_278_scan_001_pdf.jar - Download link from malspam
- 158.69.56[.]128 port 4040 - boscpakloka.myvnc[.]com - Adwind (jRAT) callback (assylias.Inc SSL cert)
FILE HASHES
DOWNLOADED .JAR FILE:
- SHA256 hash: 51d0f63e2d215ab1e4240468b8a518412472dc90ed24fffb8e5cf1e7aa75ede2
File name: FAX NO_278_scan_001_pdf.jar (232,864 bytes)
Shown above: The malicious .jar file.
Click here to return to the main page.