2016-11-03 - "THOR" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- ZIP archive of all the information: 2016-11-03-Locky-ransomware-data.zip 707.8 kB MB (707,756 bytes)
- 2016-11-03-Locky-ransomware-email-tracker.csv (3,965 bytes)
- 2016-11-03-Locky-ransomware-infection-traffic.pcap (322,362 bytes)
- files-from-infected-hosts / 2016-11-03-Locky-ransomware-Decryptor-style.css (3,422 bytes)
- files-from-infected-hosts / 2016-11-03-Locky-ransomware-Decryptor.html (6,460 bytes)
- files-from-infected-hosts / 2016-11-03-Locky-ransomware-artifact_WHAT_is.bmp (3,864,030 bytes)
- files-from-infected-hosts / 2016-11-03-Locky-ransomware-artifact_WHAT_is.html (9,378 bytes)
- files-from-infected-hosts / 2016-11-03-Locky-ransomware-binary-example-1.dll (303,104 bytes)
- files-from-infected-hosts / 2016-11-03-Locky-ransomware-binary-example-2.dll (315,392 bytes)
- attachments / GiWOXG212070.zip (1,247 bytes)
- attachments / JZTv73287697.zip (1,256 bytes)
- attachments / LSTFpHM0833911.zip (1,252 bytes)
- attachments / Lx86173440.zip (1,262 bytes)
- attachments / MABBkWp04211954.zip (1,250 bytes)
- attachments / QonH3370533.zip (1,261 bytes)
- attachments / Rdk4132815.zip (1,266 bytes)
- attachments / TXymLf24605687.zip (1,271 bytes)
- attachments / VGh48444.zip (1,253 bytes)
- attachments / WuFanr053440.zip (1,257 bytes)
- attachments / bgvTUO496306.zip (1,254 bytes)
- attachments / eZSw8623066.zip (1,256 bytes)
- attachments / gUfWy71659761.zip (1,253 bytes)
- attachments / lpM3531751.zip (1,269 bytes)
- attachments / nsexNZ504951.zip (1,243 bytes)
- attachments / pJJ780426.zip (1,246 bytes)
- attachments / qDnDRhj713487.zip (1,249 bytes)
- attachments / qZQCWp4811495.zip (1,261 bytes)
- attachments / qdRIae34444.zip (1,245 bytes)
- attachments / qwzDqH0761367.zip (1,246 bytes)
- emails / 2016-11-03-malspam-1315-UTC.eml (2,514 bytes)
- emails / 2016-11-03-malspam-1323-UTC.eml (2,516 bytes)
- emails / 2016-11-03-malspam-1407-UTC.eml (2,501 bytes)
- emails / 2016-11-03-malspam-1445-UTC.eml (2,498 bytes)
- emails / 2016-11-03-malspam-1447-UTC.eml (2,500 bytes)
- emails / 2016-11-03-malspam-1451-UTC.eml (2,507 bytes)
- emails / 2016-11-03-malspam-1452-UTC.eml (2,457 bytes)
- emails / 2016-11-03-malspam-1454-UTC.eml (2,487 bytes)
- emails / 2016-11-03-malspam-1456-UTC.eml (2,462 bytes)
- emails / 2016-11-03-malspam-1458-UTC.eml (2,488 bytes)
- emails / 2016-11-03-malspam-1501-UTC.eml (2,495 bytes)
- emails / 2016-11-03-malspam-1513-UTC.eml (2,475 bytes)
- emails / 2016-11-03-malspam-1515-UTC.eml (2,507 bytes)
- emails / 2016-11-03-malspam-1522-UTC.eml (2,472 bytes)
- emails / 2016-11-03-malspam-1536-UTC.eml (2,487 bytes)
- emails / 2016-11-03-malspam-1622-UTC.eml (2,500 bytes)
- emails / 2016-11-03-malspam-1732-UTC.eml (2,499 bytes)
- emails / 2016-11-03-malspam-1759-UTC.eml (2,516 bytes)
- emails / 2016-11-03-malspam-1803-UTC.eml (2,500 bytes)
- emails / 2016-11-03-malspam-1921-UTC.eml (2,465 bytes)
- extracted-files / BwNptv3681-38112.vbs (36,24 bytes)
- extracted-files / CYeqQL7541-29104.vbs (3,549 bytes)
- extracted-files / IQVuw6029-1166.vbs (3,741 bytes)
- extracted-files / JGhAff4039-0371.vbs (3,521 bytes)
- extracted-files / KDdqS9707-1848.vbs (3,633 bytes)
- extracted-files / MChhG3267-3359.vbs (3,583 bytes)
- extracted-files / TXwYT7031-1420.vbs (3,582 bytes)
- extracted-files / TYFGYV7920-0998.vbs (3,518 bytes)
- extracted-files / TmUPy382-1682.vbs (3,614 bytes)
- extracted-files / UKJLe3894-3543.vbs (3,524 bytes)
- extracted-files / bIsoLw7513-3750.vbs (3,471 bytes)
- extracted-files / cWGarA9995-1067.vbs (3,489 bytes)
- extracted-files / fIFNTp632-2603.vbs (3,583 bytes)
- extracted-files / iRXsj7393-1513.vbs (3,615 bytes)
- extracted-files / nOXOk9764-24111.vbs (3,526 bytes)
- extracted-files / qIJuq8169-2320.vbs (3,758 bytes)
- extracted-files / rdjkEj4834-3748.vbs (3,705 bytes)
- extracted-files / whGUM1098-3139.vbs (3,733 bytes)
- extracted-files / xMzCU4574-23107.vbs (3,685 bytes)
- extracted-files / zMXDJX5248-1503.vbs (3,693 bytes)
NOTES:
- Since 2016-10-25, Locky ransomware has been using .thor as a file extension for the files it encrypts ( link ).
Shown above: October 25th 2016, a day that will live in infamy.
EMAILS
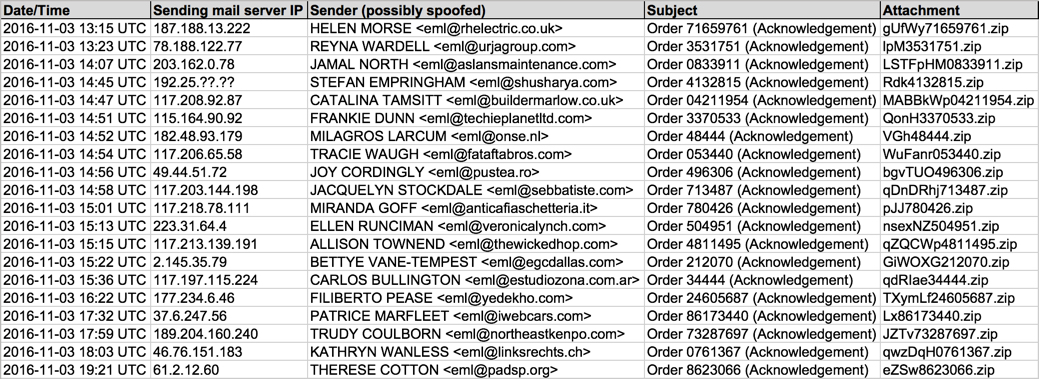
Shown above: Data from 6 emails pushing Locky ransomware (part 1 of 2).
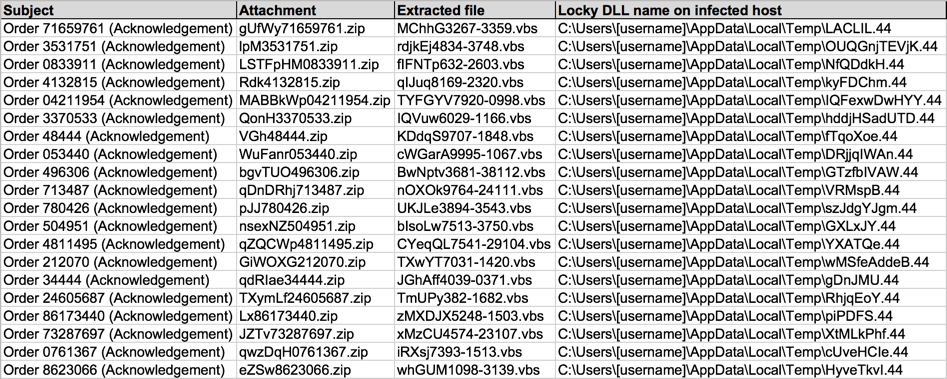
Shown above: Data from 6 emails pushing Locky ransomware (part 2 of 2).
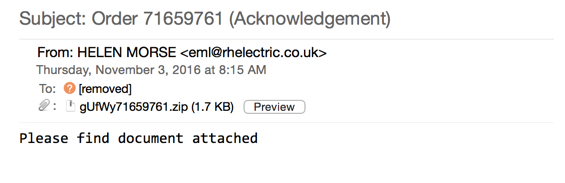
Shown above: An example from one of these emails.
TRAFFIC
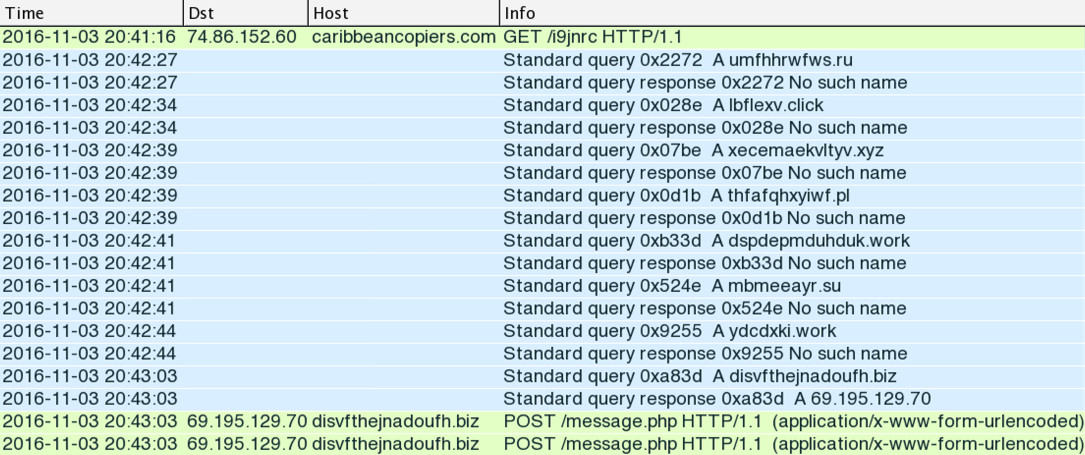
Shown above: An example of infection traffic from one of the emails.
ALL 75 URLS FROM THE 20 EXTRACTED .JS SCRIPTS:
- 113.10.206[.]34 - 0551gx[.]cn - GET /i9jnrc
- 160.153.128[.]35 - 1kupon[.]com - GET /i9jnrc
- 160.153.128[.]35 - www.1kupon[.]com - GET /i9jnrc
- 78.140.191[.]36 - 3-50-90[.]ru - GET /i9jnrc
- 185.12.94[.]59 - abgr[.]ru - GET /i9jnrc
- 94.126.173[.]51 - adj3[.]pt - GET /i9jnrc
- 128.140.220[.]131 - aertsbonarius[.]nl - GET /i9jnrc
- 89.42.220[.]193 - agorarestaurant[.]ro - GET /i9jnrc
- 122.200.219[.]36 - aifgroup[.]jp - GET /i9jnrc
- 192.186.246[.]98 - albakrawe-uae[.]com - GET /i9jnrc
- 5.149.249[.]138 - allebanken[.]net - GET /i9jnrc
- 91.203.4[.]62 - almaks-mr[.]ru - GET /i9jnrc
- 160.153.16[.]58 - anime-one[.]com - GET /i9jnrc
- 185.23.21[.]11 - arbeiten[.]pl - GET /i9jnrc
- 149.255.62[.]42 - archmod[.]com - GET /i9jnrc
- 203.146.170[.]111 - atdi[.]in[.]th - GET /i9jnrc
- 90.153.255[.]233 - awaelschool[.]com - GET /i9jnrc
- 86.57.246[.]177 - ayurvedic[.]by - GET /i9jnrc
- 104.219.248[.]93 - baseballtivy[.]com - GET /i9jnrc
- 198.54.116[.]205 - basketballninja[.]com - GET /i9jnrc
- 45.56.74[.]109 - bassguitartips[.]com - GET /i9jnrc
- 66.23.231[.]107 - bdvdo[.]net - GET /i9jnrc
- 171.25.229[.]105 - beamit[.]be - GET /i9jnrc
- 203.98.95[.]2 - beautyexpress[.]com[.]au - GET /i9jnrc
- 94.231.109[.]70 - bechsautomobiler[.]dk - GET /i9jnrc
- 107.180.41[.]153 - berrysbarber[.]com - GET /i9jnrc
- 68.65.122[.]42 - bestprservices[.]com - GET /i9jnrc
- 85.248.29[.]37 - bha-group[.]eu - GET /i9jnrc
- 66.228.41[.]116 - bipmwebs[.]com - GET /i9jnrc
- 103.28.37[.]210 - birthdaystoday[.]net - GET /i9jnrc
- 103.28.37[.]210 - www.birthdaystoday[.]net - GET /i9jnrc
- 50.22.54[.]171 - bradandmel[.]com - GET /i9jnrc
- 195.114.0[.]64 - britneyspears.website[.]pl - GET /i9jnrc
- 213.190.55[.]15 - bvn[.]lt - GET /i9jnrc
- 66.7.216[.]232 - caballerobustamante[.]com[.]pe - GET /i9jnrc
- 143.95.77[.]231 - cafedelrey[.]es - GET /i9jnrc
- 89.46.6[.]187 - carbonfiber[.]ro - GET /i9jnrc
- 74.86.152[.]60 - caribbeancopiers[.]com - GET /i9jnrc
- 69.163.163[.]94 - casadalocacao[.]com - GET /i9jnrc
- 69.163.163[.]94 - www.casadalocacao[.]com - GET /i9jnrc
- 211.149.234[.]125 - cgrs168[.]com - GET /i9jnrc
- 61.47.60[.]187 - chandrphen[.]com - GET /i9jnrc
- 103.233.192[.]226 - ck[.]co[.]th - GET /i9jnrc
- 65.39.156[.]131 - clubchasseetpechedesamis[.]com - GET /i9jnrc
- 176.223.123[.]53 - contserv[.]ro - GET /i9jnrc
- 76.74.242[.]200 - corinnenewton[.]ca - GET /i9jnrc
- 85.17.223[.]149 - cosywall[.]pl - GET /i9jnrc
- 198.54.116[.]40 - crecrec[.]com - GET /i9jnrc
- 212.175.247[.]30 - cyprushealthservices[.]com - GET /i9jnrc
- 91.224.60[.]21 - debki-klara[.]pl - GET /i9jnrc
- 108.163.209[.]27 - decactus[.]cl - GET /i9jnrc
- 122.114.89[.]67 - diandiandx[.]com - GET /i9jnrc
- 67.228.30[.]108 - distributorsite[.]com - GET /i9jnrc
- 198.54.114[.]213 - drkitchen[.]ca - GET /i9jnrc
- 31.186.169[.]157 - dutchcotton[.]nl - GET /i9jnrc
- 162.213.255[.]40 - dwcell[.]com - GET /i9jnrc
- 210.229.234[.]170 - e-ws[.]net - GET /i9jnrc
- 109.237.214[.]122 - edcentre[.]nl - GET /i9jnrc
- 143.95.247[.]142 - edu-net[.]ro - GET /i9jnrc
- 157.157.17[.]3 - eldamennska[.]is - GET /i9jnrc
- 89.108.118[.]14 - electron-trade[.]ru - GET /i9jnrc
- 109.168.103[.]128 - elektronstore[.]it - GET /i9jnrc
- 113.10.202[.]114 - erdssw[.]net - GET /i9jnrc
- 113.10.202[.]114 - erdssw[.]net - GET /i9jnrc
- 195.66.93[.]10 - eurotrading[.]com[.]ua - GET /i9jnrc
- 166.62.28[.]119 - evirtualteam[.]com - GET /i9jnrc
- 192.110.214[.]51 - faiz-e-mushtaq[.]com - GET /i9jnrc
- 85.214.22[.]254 - familieheigl[.]de - GET /i9jnrc
- 91.225.28[.]24 - farko[.]eu - GET /i9jnrc
- 192.254.79[.]89 - fastbitcoin[.]net - GET /i9jnrc
- 184.107.232[.]146 - fibrotek[.]com - GET /i9jnrc
- 192.186.238[.]229 - pastelesallegro[.]mx - GET /i9jnrc
- 62.84.69[.]75 - schuhdowdy[.]net - GET /i9jnrc
- 62.84.69[.]75 - teriisawa[.]com - GET /i9jnrc
- 113.10.206[.]161 - tgtsserver[.]com - GET /i9jnrc
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLE:
- 69.295.129[.]70 port 80 - disvfthejnadoufh[.]biz - POST /message.php
OTHER DNS QUERIES DURING POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLE:
- umfhhrwfws[.]ru (DNS reply: No such name)
- lbflexv[.]click (DNS reply: No such name)
- xecemaekvltyv[.]xyz (DNS reply: No such name)
- thfafqhxyiwf[.]pl (DNS reply: No such name)
- dspdepmduhduk[.]work (DNS reply: No such name)
- mbmeeayr[.]su (DNS reply: No such name)
- ydcdxki[.]work (DNS reply: No such name)
DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- mwddgguaa5rj7b54.tor2web[.]org
- mwddgguaa5rj7b54[.]onion[.]to
FILE HASHES
LOCKY RANSOMWARE DLL SAMPLES:
- SHA256 hash: 0e969221c2e8d9c76a5ad863a80be2486a867ad8358bffd3a56158fcf7e3997e
File name: C:\Users\[username]\AppData\Local\Temp\[random characters].44 (303,104 bytes)
- SHA256 hash: 9bbc3f494be9c4507ca0059f54f3aff12503a1bcad89071136d43dc8ed949299
File name: C:\Users\[username]\AppData\Local\Temp\[random characters].44 (315,392 bytes)
IMAGES
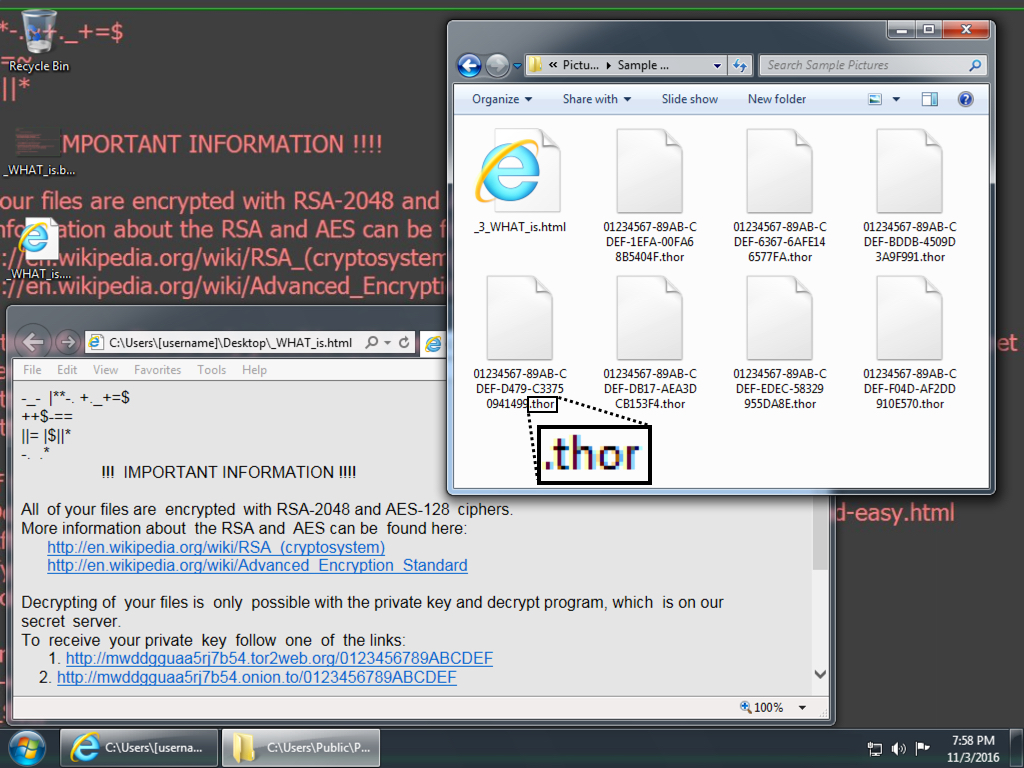
Shown above: Screen shot from an infected Windows desktop. Note the .thor file extension.
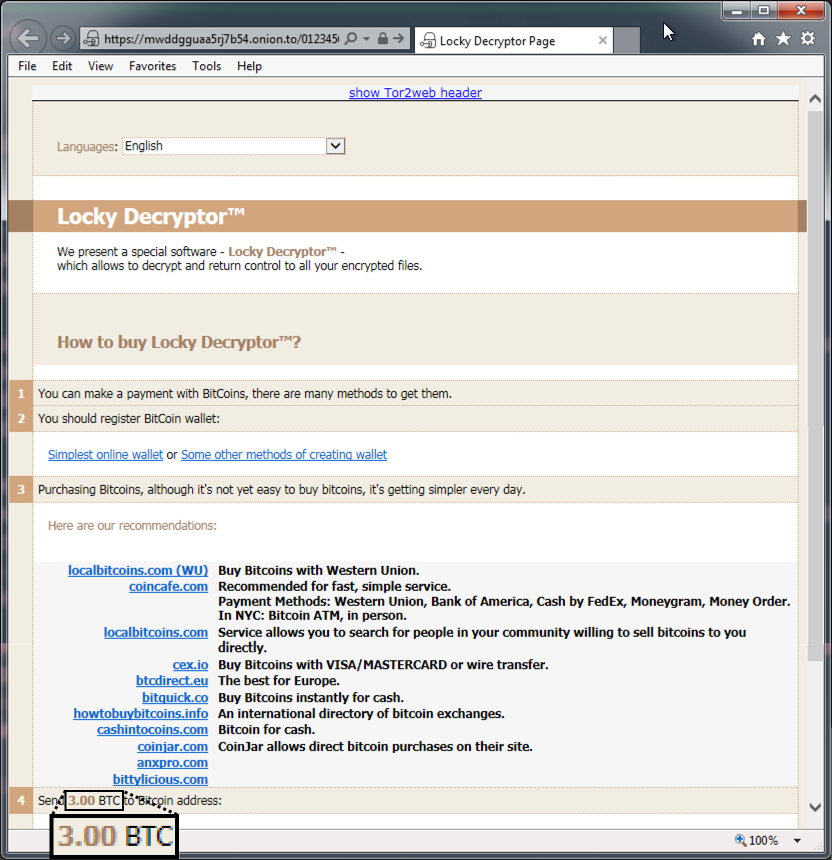
Shown above: Ransom payment was 3.0 bitcoin for the infections I generated.
Click here to return to the main page.

