2016-11-04 - MALWARE INFECTION FROM LINK IN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-04-infection-traffic-from-link-in-email.pcap.zip 7.1 MB (7,082,612 bytes)
- 2016-11-04-infection-traffic-from-link-in-email.pcap (7,508,637 bytes)
- 2016-11-04-files-from-an-infection.zip 4.1 MB (4,055,018 bytes)
- 2016-11-04-email-spoofing-Facebook-1230-UTC.eml (10,865 bytes)
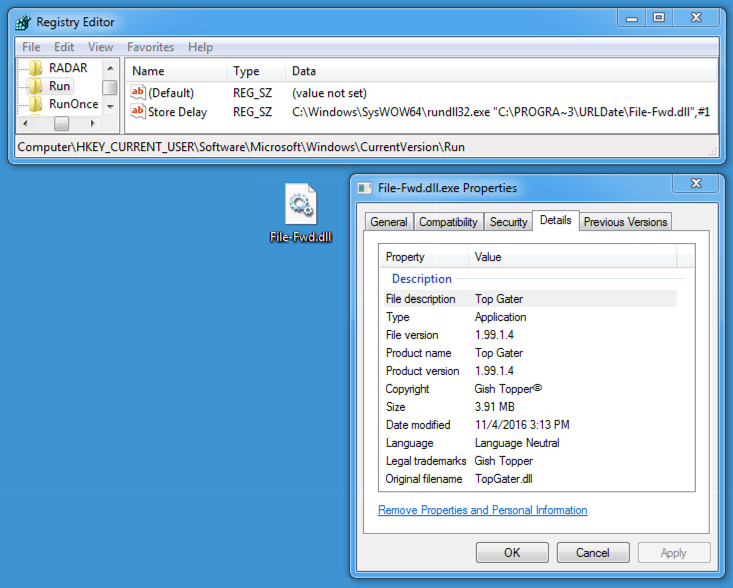
- File-Fwd.dll (4,108,800 bytes)
- IMG_68794206_0521890.js (9,587 bytes)
- IMG_68794206_0521890.zip (3,238 bytes)
NOTES:
- I documented a similar email last week on 2016-10-31 (link ).
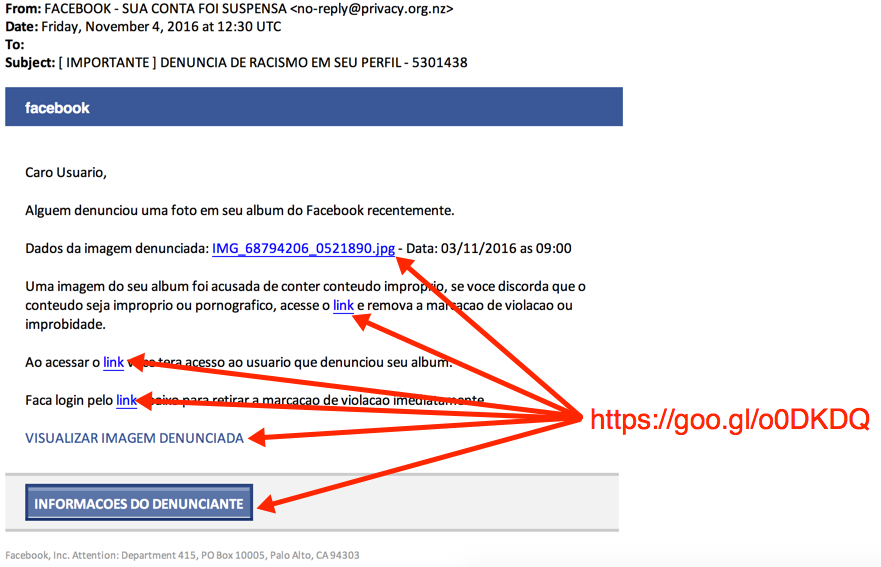
Shown above: Screenshot of the email.
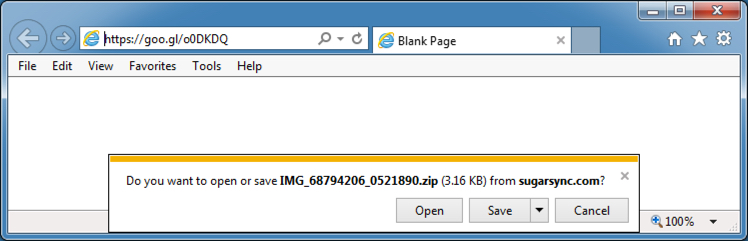
Shown above: Clicking on one of the links in the email (it's a goo[.]gl URL).
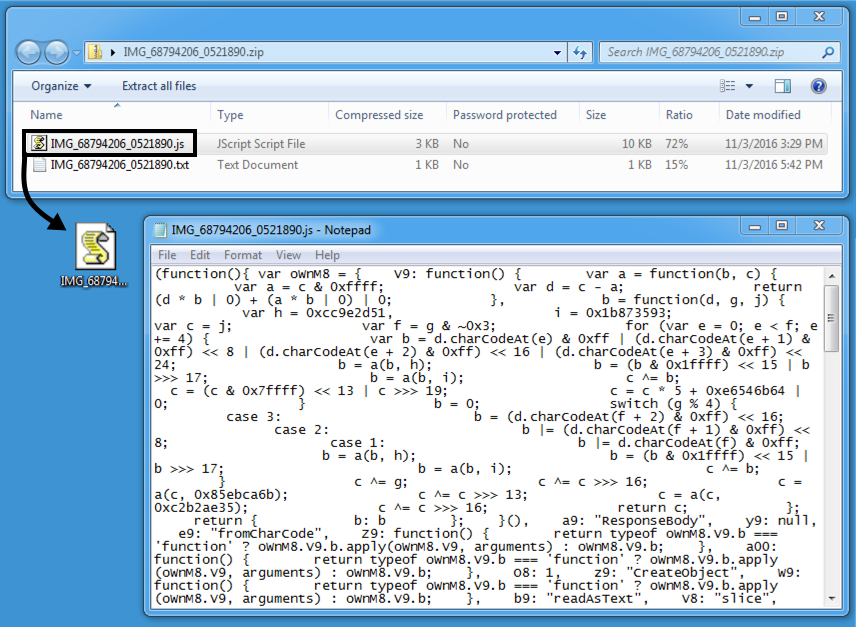
Shown above: File downloaded from the goo[.]gl link in the malspam.
TRAFFIC
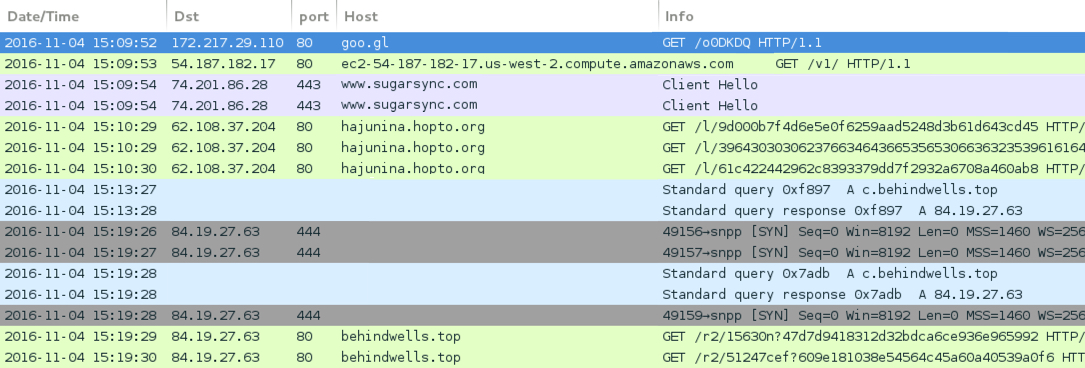
Shown above: Traffic from the infection filtered in Wireshark.
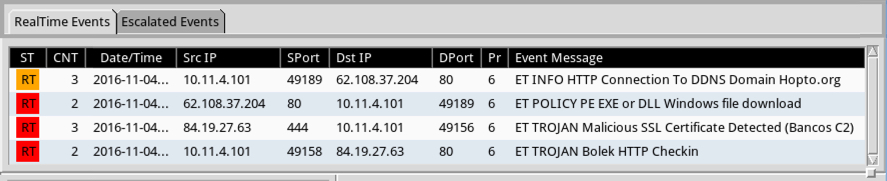
Shown above: Alerts using tcpreplay on the first pcap with the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion.
ASSOCIATED DOMAINS:
- goo[.]gl - GET /o0DKDQ (Link from the email)
- ec2-54-187-182-17.us-west-2.compute.amazonaws[.]com - GET /v1/ (redirect from the goo[.]gl link)
- www.sugarsync[.]com - /pf/D3235179_820_128649329?directDownload=true (HTTPS download of the zip file)
- 62.108.37[.]204 port 80 - hajunina.hopto[.]org - HTTP post-infection traffic
- 84.19.27[.]63 port 444 - c.behindwells[.]top - HTTPS/TLS/SSL post-infection traffic
- 84.19.27[.]63 port 80 - behindwells[.]top - HTTP post-infection traffic
FILE HASHES
Zip archive downloaded from any of the goo[.]gl links in the email:
- SHA256 hash: 2ddc4e2f93135561bd9de7429d28c38b45e8fc2ae27f0d73c855f0960fc25f7e
File name: IMG_68794206_0521890.zip (3,238 bytes)
.js file extracted from the zip archive:
- SHA256 hash: 510d9815b6f267a1bbf13da0b4a7005be21698a24dcfc6895b56f8515c0e557f
File name: IMG_68794206_0521890.js (9,587 bytes)
DLL file dropped on the infected Windows host:
- SHA256 hash: 64f01cb3eccaab99ca212a24a32720970e78b30baff2d34ab39a6e9cb4ef2acd
File name: C:\ProgramData\URLDate\File-Fwd.dll (4,108,800 bytes)
Shown above: Artifacts from the infected host.
Click here to return to the main page.