2016-11-09 - RIG EK/RIG-V DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-09-Rig-EK-and-RIGv-data-dump-all-4-pcaps.zip 1.2 MB (1,216,735 bytes)
- 2016-11-09-1st-run-EITest-Rig-EK-sends-CryptFile2-ransomwware.pcap (226,241 bytes)
- 2016-11-09-2nd-run-EITest-Rig-EK.pcap (588,833 bytes)
- 2016-11-09-3rd-run-pseudoDarkleech-RIGv-sends-Cerber-ransomwware.pcap (550,482 bytes)
- 2016-11-09-4th-run-EITest-Rig-EK-sends-Gootkit.pcap (387,405 bytes)
- 2016-11-09-Rig-EK-and-RIGv-data-dump-malware-and-artifacts.zip 1.0 MB (1,033,657 bytes)
- 2016-11-09-1st-run-page-from-showbizgeek_com-with-injected-script.txt (101,025 bytes)
- 2016-11-09-1st-run-EITest-Rig-EK-landing-page.txt (3,176 bytes)
- 2016-11-09-1st-run-EITest-Rig-EK-flash-exploit.swf (51,964 bytes)
- 2016-11-09-1st-run-EITest-Rig-EK-payload-CryptFile2-ransomwware.exe (87,552 bytes)
- 2016-11-09-2nd-run-page-from-bienvivir_org-with-injected-script.txt (24,167 bytes)
- 2016-11-09-2nd-run-EITest-Rig-EK-landing-page.txt (3,315 bytes)
- 2016-11-09-2nd-run-EITest-Rig-EK-flash-exploit.swf (52,582 bytes)
- 2016-11-09-2nd-run-EITest-Rig-EK-payload.exe (555,520 bytes)
- 2016-11-09-3rd-run-page-from-joellipman_com-with-injected-script.txt (68,435 bytes)
- 2016-11-09-3rd-run-pseudoDarkleech-RIGv-landing-page.txt (5,188 bytes)
- 2016-11-09-3rd-run-pseudoDarkleech-RIGv-flash-exploit.swf (51,783 bytes)
- 2016-11-09-3rd-run-pseudoDarkleech-RIGv-payload-Cerber-ransomwware.exe (265,471 bytes)
- 2016-11-09-4th-run-page-from-tedscafe_com-with-injected-script.txt (10,836 bytes)
- 2016-11-09-4th-run-EITest-Rig-EK-landing-page.txt (3,295 bytes)
- 2016-11-09-4th-run-EITest-Rig-EK-flash-exploit.swf (52,582 bytes)
- 2016-11-09-4th-run-EITest-Rig-EK-payload-Gootkit.exe (151,040 bytes)
TRAFFIC
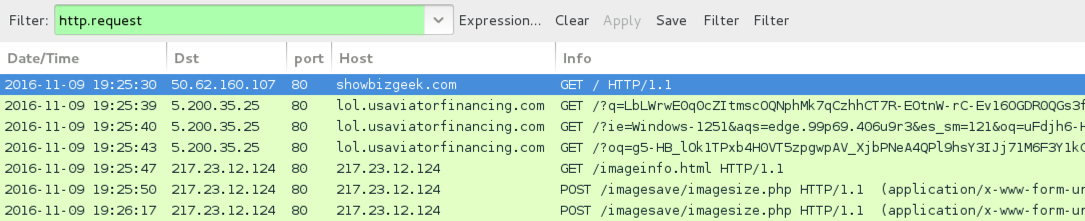
Shown above: Traffic from the 1st pcap filtered in Wireshark.
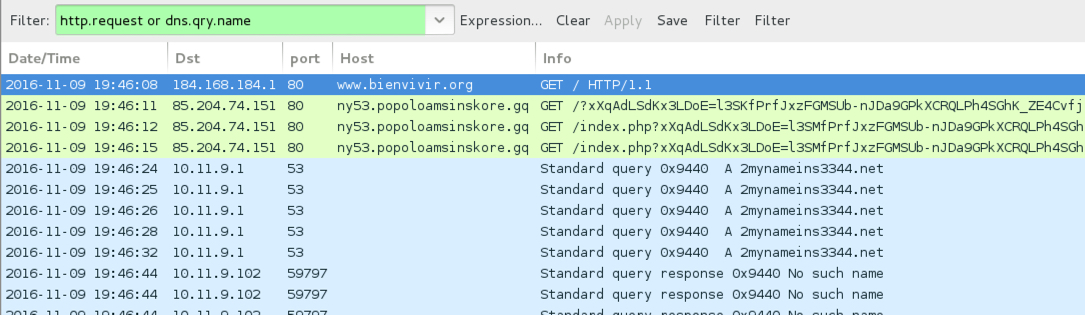
Shown above: Traffic from the 2nd pcap filtered in Wireshark.
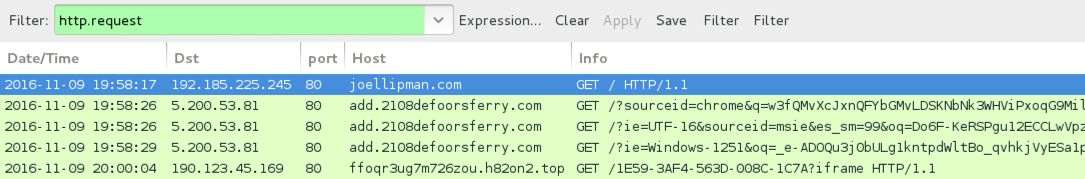
Shown above: Traffic from the 3rd pcap filtered in Wireshark.
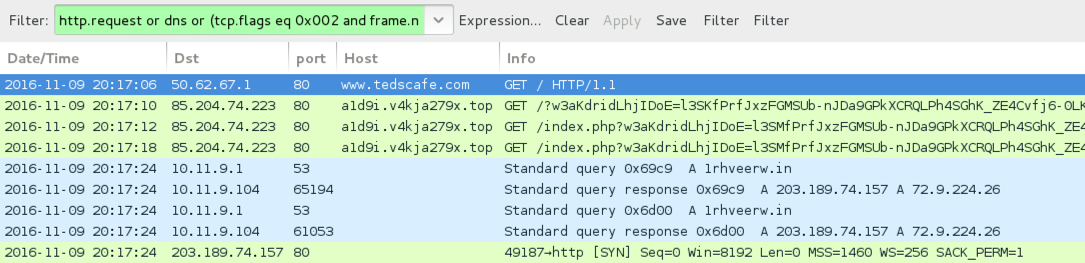
Shown above: Traffic from the 4th pcap filtered in Wireshark.
1ST RUN:
- showbizgeek[.]com - Compromised site
- 5.200.35[.]25 port 80 - lol.usaviatorfinancing[.]com - Rig EK (with RIG-v URLs)
- 217.23.12[.]124 port 80 - 217.23.12[.]124 - Post-infection traffic caused by CryptFile2 ransomware
2ND RUN:
- www.bienvivir[.]org - Compromised site
- 85.204.74[.]151 port 80 - ny53.popoloamsinskore[.]gq - Rig EK
- Several DNS queries for - 2mynameins3344[.]net - Server response: No such name (Could this be another sample of Chthonic?)
3RD RUN:
- joellipman[.]com - Compromised site
- 5.200.53[.]81 port 80 - add.2108defoorsferry[.]com - RIG-v
- 65.55.50[.]0 - 65.55.50[.]31 (65.55.50[.]0/27) port 6892 - UDP traffic caused by Cerber ransomware
- 192.42.118[.]0 - 192.42.118[.]31 (192.42.118[.]0/27)port 6892 - UDP traffic caused by Cerber ransomware
- 194.165.16[.]0 - 194.165.19[.]255 (194.165.16[.]0/22) port 6892 - UDP traffic caused by Cerber ransomware
- 190.123.45[.]169 port 80 - ffoqr3ug7m726zou.h82on2[.]top - HTTP traffic caused by Cerber ransomware
4TH RUN:
- www.tedscafe[.]com - Compromised site
- 85.204.74[.]223 port 80 - a1d9i.v4kja279x[.]top - Rig EK
- 203.189.74[.]157 port 80 - 1rhveerw[.]in - Post-infection HTTPS/SSL/TLS traffic caused by (I assume) Gootkit malware
FILE HASHES
FLASH EXPLOITS (SHA256 HASH - FILE NAME):
- c733ab81ed78a00a2f7beacfc82f6227936477dab33f05a0e4a3ba2340385dbe - 2016-11-09-1st-run-EITest-Rig-EK-flash-exploit.swf
- 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1 - 2016-11-09-2nd-run-EITest-Rig-EK-flash-exploit.swf
- 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1 - 2016-11-09-4th-run-EITest-Rig-EK-flash-exploit.swf
- bc168c0c453f3d35846a9b4f8912f82e300e2ddd3bfa69fa6d4f539c2983b48e - 2016-11-09-3rd-run-pseudoDarkleech-RIGv-flash-exploit.swf
PAYLOAD (SHA256 HASH - FILE NAME):
- 9b7a93df69ec9521ca5e169e865bfb9905625cadf056f2d10d48014a22cb253c - 2016-11-09-1st-run-EITest-Rig-EK-payload-CryptFile2-ransomware.exe
- a49b886847c53f64cb2da3801c22d88159c9ca5b564d59c72caee12c4661c12f - 2016-11-09-2nd-run-EITest-Rig-EK-payload.exe
- d025b663f0fafccbadad16ffc74888e404c846285cca35aaa73e94c090406b12 - 2016-11-09-3rd-run-pseudoDarkleech-RIGv-payload-Cerber-ransomware.exe
- 5cb6028535a11bbdd17cd603cf0b086875b20b1e8f0be13c75dd302abd93ac53 - 2016-11-09-4th-run-EITest-Rig-EK-payload-Gootkit.exe
Click here to return to the main page.
