2016-11-22 - RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-22-Rig-EK-data-dump-all-4-pcaps.zip 1.4 MB (1,401,198 bytes)
- 2016-11-22-1st-run-EITest-Rig-E-traffic.pcap (662,419 bytes)
- 2016-11-22-2nd-run-EITest-Rig-standard-sends-CryptFile2-ransomware.pcap (173,971 bytes)
- 2016-11-22-3rd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (601,911 bytes)
- 2016-11-22-4th-run-Afraidgate-Rig-V-causes-Locky-ransomware-infection.pcap (358,995 bytes)
- 2016-11-22-Rig-EK-data-dump-malware-and-artifacts.zip 882.4 kB (882,351 bytes)
- 2016-11-22-1st-run-EITest-Rig-E-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-11-22-1st-run-EITest-Rig-E-flash-exploit.swf (40,141 bytes)
- 2016-11-22-1st-run-EITest-Rig-E-landing-page.txt (85,260 bytes)
- 2016-11-22-1st-run-EITest-Rig-E-payload-radAA63F.tmp.exe (261,632 bytes)
- 2016-11-22-1st-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,804 bytes)
- 2016-11-22-2nd-run-EITest-Rig-standard-flash-exploit.swf (39,147 bytes)
- 2016-11-22-2nd-run-EITest-Rig-standard-landing-page.txt (3,138 bytes)
- 2016-11-22-2nd-run-EITest-Rig-standard-payload-CryptFile2-ransomware-3274.tmp (85,504 bytes)
- 2016-11-22-2nd-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,812 bytes)
- 2016-11-22-3rd-run-page-from-wordtemplates_org-with-injected-script.txt (54,474 bytes)
- 2016-11-22-3rd-run-pseudoDarkleech-Rig-V-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-11-22-3rd-run-pseudoDarkleech-Rig-V-flash-exploit.swf (37,559 bytes)
- 2016-11-22-3rd-run-pseudoDarkleech-Rig-V-landing-page.txt (5,,192 bytes)
- 2016-11-22-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radCC957.tmp.exe (260,298 bytes)
- 2016-11-22-4th-run-Afraidgate-Rig-V-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-11-22-4th-run-Afraidgate-Rig-V-flash-exploit.swf (3,7559 bytes)
- 2016-11-22-4th-run-Afraidgate-Rig-V-landing-page.txt (5,192 bytes)
- 2016-11-22-4th-run-Afraidgate-Rig-V-payload-radCD4C2.tmp.exe (78,848 bytes)
- 2016-11-22-4th-run-Afraidgate-redirect-openair.mirceasandu_ro-shortcuts.js.txt (415 bytes)
- 2016-11-22-4th-run-page-from-ardenne_org-with-injected-script.txt (18,666 bytes)
- 2016-11-22-4th-run-post-infection-download-Locky-ransomware-jtqaLMMFNErRMgrba8hW2Al3B.exe (211,456 bytes)
BACKGROUND:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: uses new URL patterns introduced by Rig-V, but old obfuscation (ASCII string to XOR the payload binary) The EITest campaign uses Rig standard to send CryptFile2 ransomware.
TRAFFIC
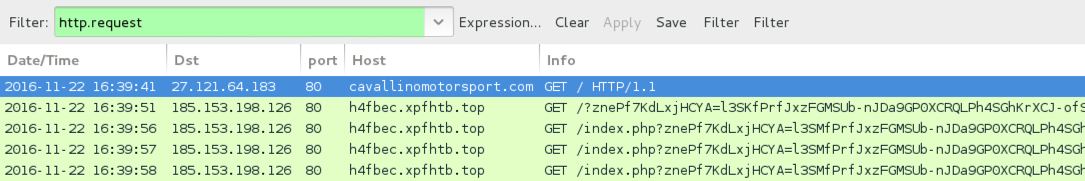
Shown above: Traffic from the 1st infection filtered in Wireshark.
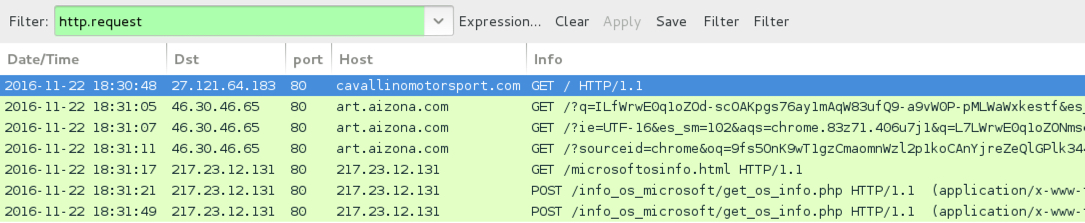
Shown above: Traffic from the 2nd infection filtered in Wireshark.
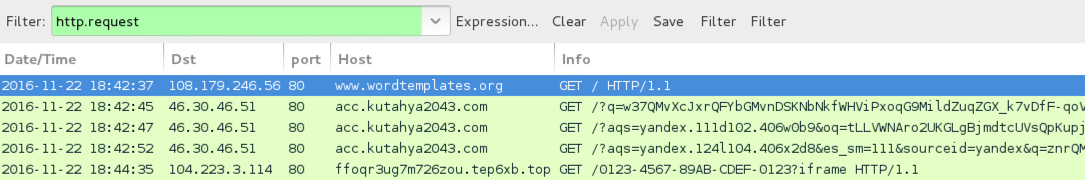
Shown above: Traffic from the 3rdd infection filtered in Wireshark.
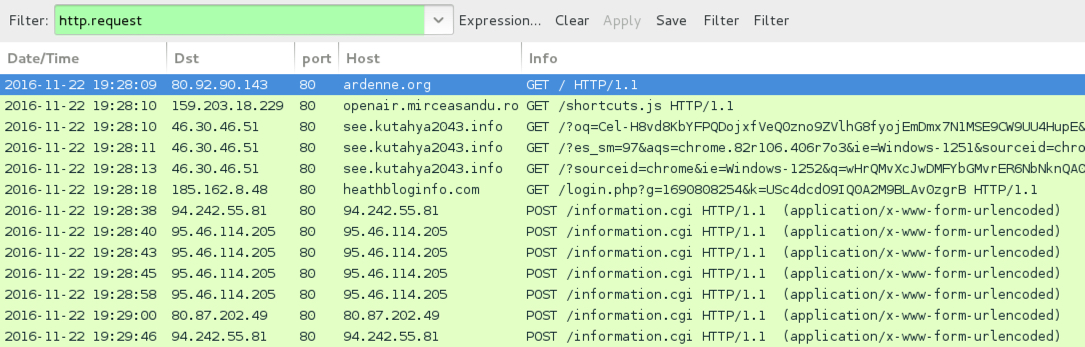
Shown above: Traffic from the bonus infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- cavallinomotorsport[.]com - Compromised site that led to EITest Rig-E (1st run) and EITest Rig standard (2nd run)
- www.wordtemplates[.]org - Compromised site that led to pseudoDarkleech Rig-V (3rd run)
- ardenne[.]org - Compromised site that led to Afraidgate Rig-V (4th run)
- 185.153.198[.]126 port 80 - h4fbec.xpfhtb[.]top - Rig-E (1st run)
- 46.30.46[.]65 port 80 - art.aizona[.]com - Rig standard (2nd run)
- 46.30.46[.]51 port 80 - acc.kutahya2043[.]com - Rig-V (3rd run)
- 46.30.46[.]51 port 80 - see.kutahya2043[.]info - Rig-V (4th run)
- 217.23.12[.]131 port 80 - 217.23.12[.]131 - CryptFile2 ransomware post-infection traffic (2nd run)
- 65.55.50[.]0 - 65.55.50[.]31 (65.55.50[.]0/27) port 6892 - UDP traffic caused by Cerber ransomware (3rd run)
- 192.42.118[.]0 - 192.42.118[.]31 (192.42.118[.]0/27)port 6892 - UDP traffic caused by Cerber ransomware (3rd run)
- 194.165.16[.]0 - 194.165.19[.]255 (194.165.16[.]0/22) port 6892 - UDP traffic caused by Cerber ransomware (3rd run)
- 104.223.3.114 port 80 - ffoqr3ug7m726zou.tep6xb[.]top - HTTP traffic caused by Cerber ransomware (3rd run)
- 159.203.18[.]229 port 80 - openair.mirceasandu[.]ro - Afraidgate redirect (4th run)
- 185.162.8[.]48 port 80 - heathbloginfo[.]com - Domain contacted to download Locky ransomware (4th run)
- 94.242.55[.]81 port 80 - 94.242.55[.]81 - Locky ransomware post-infection traffic (4th run)
- 95.46.114[.]205 port 80 - 95.46.114[.]205 - Locky ransomware post-infection traffic (4th run)
- 80.87.202[.]49 port 80 - 80.87.202[.]49 - Locky ransomware post-infection traffic (4th run)
FILE HASHES
FLASH EXPLOITS (SHA256 HASH - FILE NAME):
- b73dd34e63a001b3be1e809c889df4a075162891034404e4d344d7cfafb1bc0e - 2016-11-22-1st-run-EITest-Rig-E-flash-exploit.swf
- 8794626ca0160b5be2965240fdfd05d0c4818d6f72a4ddffbc7a6f48c0460094 - 2016-11-22-2nd-run-EITest-Rig-standard-flash-exploit.swf
- 3faf0f278306eaca73f7b6d6f20ea64522e03e56192df6aee561e9359f1d2948 - 2016-11-22-3rd-run-pseudoDarkleech-Rig-V-flash-exploit.swf
- 3faf0f278306eaca73f7b6d6f20ea64522e03e56192df6aee561e9359f1d2948 - 2016-11-22-4th-run-Afraidgate-Rig-V-flash-exploit.swf
MALWARE (SHA256 HASH - FILE NAME):
- 45a1a265bb27ee8f05b0835db2efa89bd88d0ec3aecfb1b3a922f26602535654 - 2016-11-22-1st-run-EITest-Rig-E-payload-radAA63F.tmp.exe
- d26d94b3f2148b818969a692efa8fccab2f8476d06b7119e2996108aefc47981 - 2016-11-22-2nd-run-EITest-Rig-standard-payload-CryptFile2-ransomware-3274.tmp
- 30ed67ed6e182b925a5f891abf0bc0c68e8712bc9eea33561d30a18efd33db62 - 2016-11-22-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radCC957.tmp.exe
- cf0ddff94b84954900457f39b209c5aab6e5c46d723d5afdf310032a6e650cc3 - 2016-11-22-4th-run-Afraidgate-Rig-V-payload-radCD4C2.tmp.exe
- d319d46e713f1ec1f1f1bb7473af606eff38912dc0e84ddce9063fa60f95a900 - 2016-11-22-4th-run-post-infection-download-Locky-ransomware-jtqaLMMFNErRMgrba8hW2Al3B.exe
Click here to return to the main page.
