2016-12-07 - RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-07-Rig-EK-data-dump-5-pcaps.zip 1.7 MB (1,712,786 bytes)
- 2016-12-07-1st-run-EITest-Rig-E-sends-Gootkit.pcap (511,118 bytes)
- 2016-12-07-2nd-run-EITest-Rig-E-sends-Smoke-Loader.pcap (167,116 bytes)
- 2016-12-07-3rd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (637,182 bytes)
- 2016-12-07-4th-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (651,266 bytes)
- 2016-12-07-5th-run-EITest-Rig-E-sends-Smoke-Loader.pcap (147,121 bytes)
- 2016-12-07-Rig-EK-data-dump-malware-and-artifacts.zip 1.2 MB (1,224,494 bytes)
- 2016-12-07-1st-run-EITest-Rig-E-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-07-1st-run-EITest-Rig-E-flash-exploit.swf (17,657 bytes)
- 2016-12-07-1st-run-EITest-Rig-E-landing-page.txt (85,199 bytes)
- 2016-12-07-1st-run-EITest-Rig-E-payload-Gootkit-rad0BCCB.tmp.exe (237,568 bytes)
- 2016-12-07-1st-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,838 bytes)
- 2016-12-07-1st-run-post-infection-follow-up-malware.exe (397,824 bytes)
- 2016-12-07-2nd-run-EITest-Rig-E-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-07-2nd-run-EITest-Rig-E-flash-exploit.swf (17,657 bytes)
- 2016-12-07-2nd-run-EITest-Rig-E-landing-page.txt (85,251 bytes)
- 2016-12-07-2nd-run-EITest-Rig-E-payload-Smoke-Loader-rad79415.tmp.exe (43,520 bytes)
- 2016-12-07-2nd-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,844 bytes)
- 2016-12-07-3rd-run-page-from-joellipman_com-with-injected-script.txt (68,908 bytes)
- 2016-12-07-3rd-run-pseudoDarkleech-Rig-V-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-07-3rd-run-pseudoDarkleech-Rig-V-flash-exploit.swf (17,618 bytes)
- 2016-12-07-3rd-run-pseudoDarkleech-Rig-V-landing-page.txt (5,375 bytes)
- 2016-12-07-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad30C82.tmp.exe (264,228 bytes)
- 2016-12-07-4th-run-pseudoDarkleech-Rig-V-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-07-4th-run-pseudoDarkleech-Rig-V-flash-exploit.swf (17,618 bytes)
- 2016-12-07-4th-run-pseudoDarkleech-Rig-V-landing-page.txt (5,380 bytes)
- 2016-12-07-4th-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad6EB28.tmp.exe (264,228 bytes)
- 2016-12-07-4th-run-wordtemplates_org-with-injected-script.txt (54,484 bytes)
- 2016-12-07-5th-run-EITest-Rig-E-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-07-5th-run-EITest-Rig-E-flash-exploit.swf (17,657 bytes)
- 2016-12-07-5th-run-EITest-Rig-E-landing-page.txt (85,229 bytes)
- 2016-12-07-5th-run-EITest-Rig-E-payload-Smoke-Loader-radE32E0.tmp.exe (43,520 bytes)
- 2016-12-07-5th-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,841 bytes)
TRAFFIC
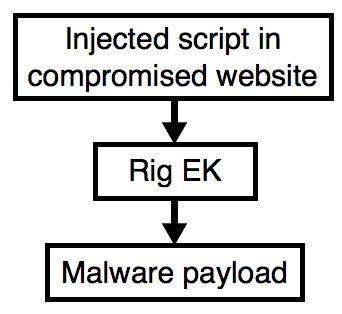
Shown above: Flow chart for today's infection traffic.
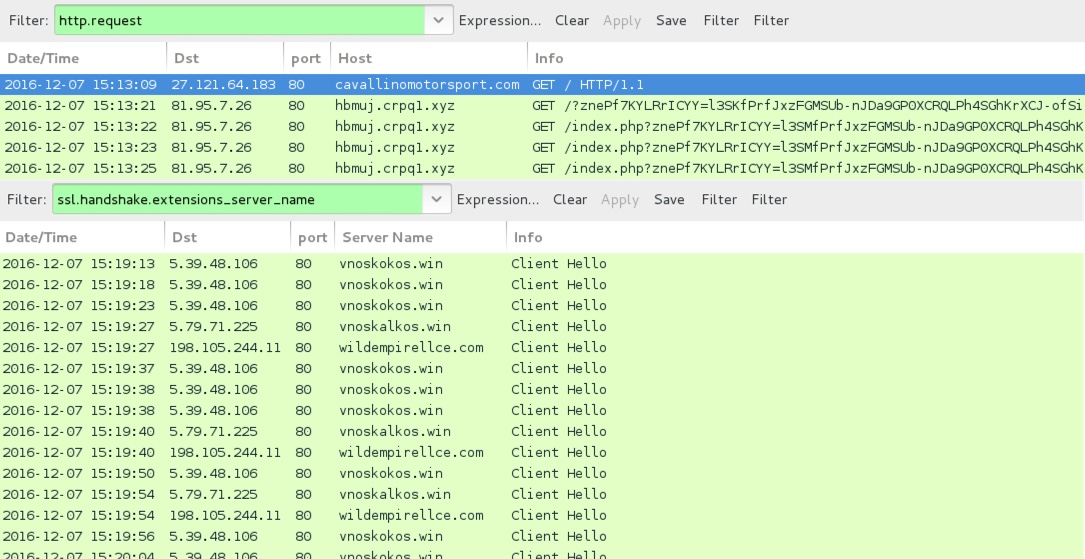
Shown above: Traffic from the 1st infection filtered in Wireshark.
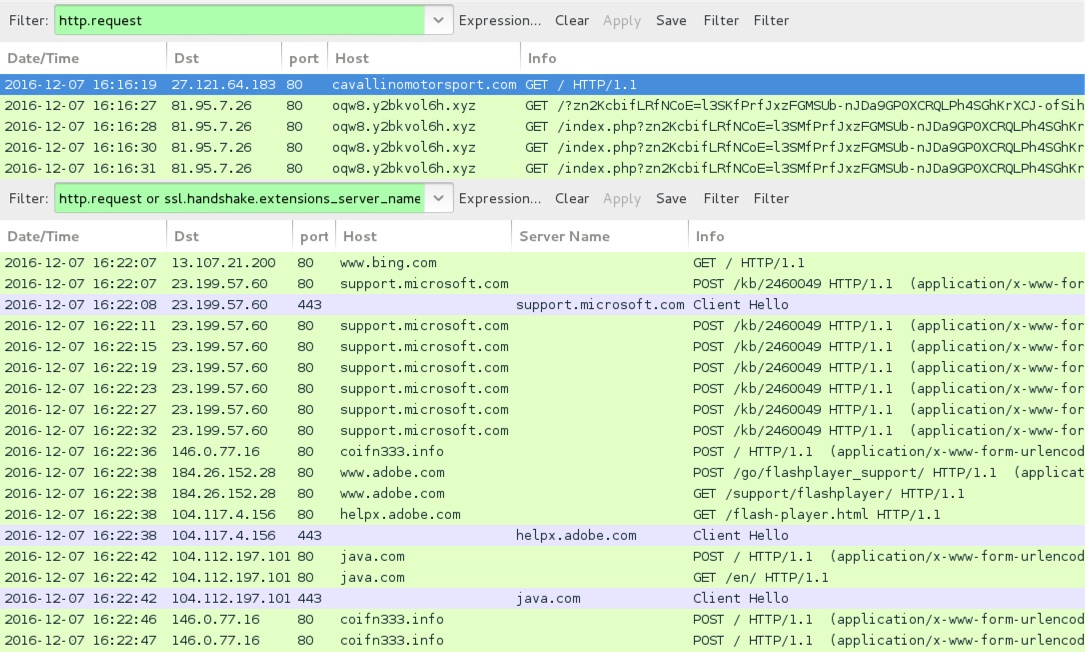
Shown above: Traffic from the 2nd infection filtered in Wireshark.
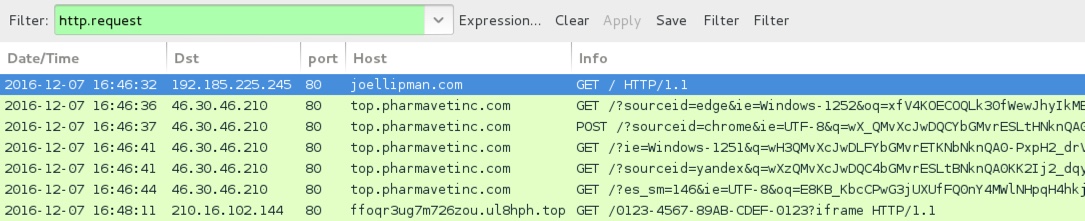
Shown above: Traffic from the 3rd infection filtered in Wireshark.
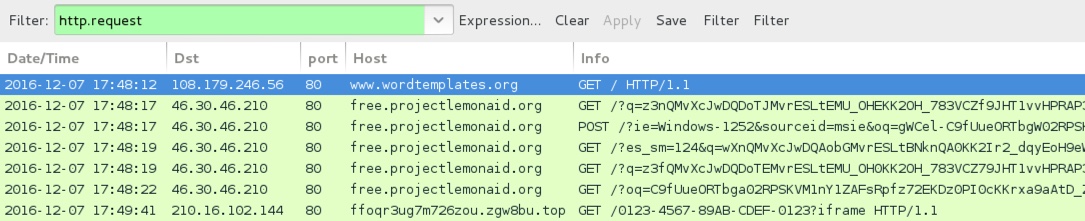
Shown above: Traffic from the 4th infection filtered in Wireshark.
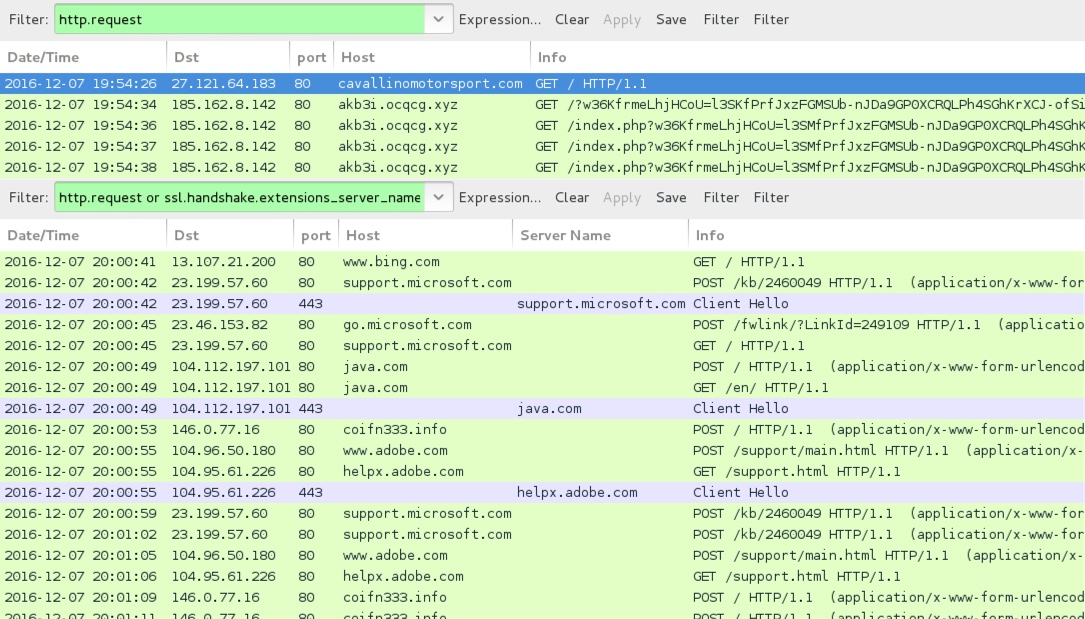
Shown above: Traffic from the 5th infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- cavallinomotorsport[.]com - Compromised site
- 81.95.7[.]26 port 80 - hbmuj.crpq1[.]xyz - Rig-E
- 5.39.48[.]106 port 80 - vnoskokos[.]win - Gootkit post-infection HTTPS/SSL/TLS traffic
- 5.79.71[.]225 port 80 - vnoskalkos[.]win - Gootkit post-infection HTTPS/SSL/TLS traffic
- 198.105.244[.]11 port 80 - wildempirellce[.]com - Gootkit post-infection HTTPS/SSL/TLS traffic
- cavallinomotorsport[.]com - Compromised site
- 81.95.7[.]26 port 80 - oqw8.y2bkvol6h[.]xyz - Rig-E
- 146.0.77[.]16 port 80 - coifn333[.]info - Smoke Loader post-infection HTTP traffic
- joellipman[.]com - Compromised site
- 46.30.46[.]210 port 80 - top.pharmavetinc[.]com - Rig-V
- 15.49.2[.]0 to 15.49.2[.]31 (15.49.2[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 122.1.13[.]0 to 122.1[.]31 (122.1.13[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 194.165.16[.]0 to 194.165.17[.]255 (194.165.16[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 210.16.102[.]144 port 80 - ffoqr3ug7m726zou.ul8hph[.]top - Cerber ransomware post-infection HTTP traffic
- www.wordtemplates[.]org - Compromised site
- 46.30.46[.]210 port 80 - free.projectlemonaid[.]org - Rig-V
- 15.49.2[.]0 to 15.49.2[.]31 (15.49.2[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 122.1.13[.]0 to 122.1[.]31 (122.1.13[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 194.165.16[.]0 to 194.165.17[.]255 (194.165.16[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 210.16.102[.]144 port 80 - ffoqr3ug7m726zou.zgw8bu[.]top - Cerber ransomware post-infection HTTP traffic
- cavallinomotorsport[.]com - Compromised site
- 185.162.8[.]142 port 80 - akb3i.ocqcg[.]xyz - Rig-E
- 146.0.77[.]16 port 80 - coifn333[.]info - Smoke Loader post-infection HTTP traffic
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 732f898c4ec1847aac57f019698c1328608bb0852ecee147fc498373283a9821 (17,657 bytes)
File description: 2016-12-07 EITest Rig-E Flash-exploit
- SHA256 hash: 0dc0e76091e65b422ff0dd45b0b07de605047e8c4564cd4097dafca7ee229028 (17,618 bytes)
File description: 2016-12-07 EITest Rig-V Flash-exploit
PAYLOADS (READ: SHA256 HASH - FILE NAME - FILE SIZE):
- 893a38969233228c4f73b2d152797c71b9d6c8076390ada74cb655e83c61cb36 - 2016-12-07-1st-run-EITest-Rig-E-payload-Gootkit.exe - 237,568 bytes
- da718292a1e40c15f512155cbda7ef807a421d0d0cb56666a639b95a1bfa0fe1 - 2016-12-07-1st-run-post-infection-follow-up-malware.exe - 397,824 bytes
- 772fcfe20f0bb14861a611901a7354759515cbd7d1b4762436e9c1f4c2c290df - 2016-12-07-2nd-run-EITest-Rig-E-payload-Smoke-Loader.exe - 43,520 bytes
- 4715f450ff14a6487a8d1876d05878b1fff3d6dd1c5d1d93d4f8aadd327af9ce - 2016-12-07-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware.exe - 264,228 bytes
- 5998d2fc69cbab14ba4b5459bbd2ab01dda67581573900079445176782bd2e4d - 2016-12-07-4th-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware.exe - 264,228 bytes
- 0c7a0fb9a1271f4a19868a24dfdd6faa0bfb1d35331cfbf315632e7370ddf012 - 2016-12-07-5th-run-EITest-Rig-E-payload-Smoke-Loader.exe - 43,520 bytes
Click here to return to the main page.
