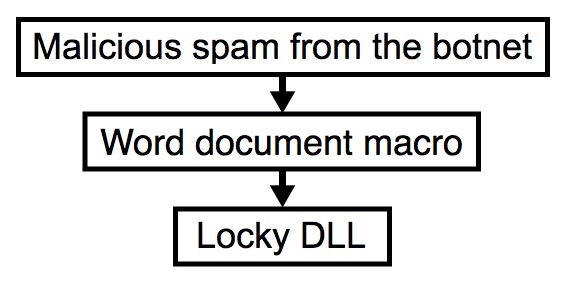
2016-12-16 - "OSIRIS" VARIANT LOCKY RANSOMWARE FROM WORD DOCUMENTS WITH MACROS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-16-Locky-ransowmare-email-tracker.csv.zip 3.1 kB (3,055 bytes)
- 2016-12-16-Locky-ransomware-infection-traffic.pcap.zip 236.8 kB (236,813 bytes)
- 2016-12-16-Locky-ransomware-emails-20-examples.zip 667.5 kB (667,509 bytes)
- 2016-12-16-email-attachments-for-Locky-ransomware.zip 627.0 kB (626,961 bytes)
- 2016-12-16-Locky-ransomware-files-from-infected-host.zip 214.3 kB (214,349 bytes)
NOTES:
- The entry point for today's Locky ransomware DLL is sample input in case anyone wants to run it with rundll32.exe in a controlled environment.
Shown above: Chain of events for an infection from this malspam.
THE EMAILS
IP ADDRESSES OF BOTNET HOSTS SENDING THE EMAILS:
- 1.54.122[.]63 : Vietnam - FPT Telecom Company
- 5.220.181[.]87 : Iran - Telecommunication company of West Azarbaijan
- 39.35.229[.]182 : Pakistan - Pakistan Telecommuication Company Limited
- 42.118.78[.]249 : Vietnam - FPT Telecom Company
- 46.143.248[.]48 : Iran - Ferdowsi University of Mashhad
- 79.149.50[.]118 : Spain - 118.red-79-149-50.dynamicip.rima-tde[.]net
- 93.46.181[.]26 : Italy - 93-46-181-26.ip108.fastwebnet[.]it
- 95.0.137[.]236 : Turkey - 95.0.137[.]236.dynamic.ttnet[.]com[.]tr
- 103.255.4[.]6 : Pakistan - For Karachi IGW (CMPak Limited)
- 103.255.5[.]249 : Pakistan - For Karachi IGW (CMPak Limited)
- 112.215.172[.]111 : Indonesia - PT Excelcomindo Pratama
- 117.239.31[.]186 : India - static.ill.117.239.31[.]186/24.bsnl[.]in
- 118.107.133[.]88 : Pakistan - SCO Dialup and ADSL, ADSL2+ Network (SNET)
- 120.188.66[.]120 : Indonesia - PT Indosat
- 131.0.192[.]165 : Brazil - 65-192-0-131.clicknetguarai[.]com[.]br
- 175.100.49[.]229 : Cambodia - Viettel (cambodia) PTE., LTD.
- 177.23.89[.]197 : Brazil - Bruno Nascimento Santos Moreira
- 179.219.186[.]91 : Brazil - b3dbba5b.virtua[.]com[.]br
- 189.216.199[.]54 : Mexico - Cablevision S.A. De C.V.
- 191.179.102[.]105 : Brazil - bfb36669.virtua[.]com[.]br
SUBJECT LINES:
- Bill-3046
- Bill-5050
- Bill-5439
- Bill-0600
- Bill-6211
- Bill-6453
- Bill-7855
- Bill-06153
- Bill-21335
- Bill-110199
- Bill-213563
- Bill-583903
- Bill-722121
- Bill-899082
- Bill-0363222
- Bill-0496867
- Bill-2206097
- Bill-2586897
- Bill-8183509
- Bill-9302668
SPOOFED SENDING ADDRESSES:
- blair farquharson <blair.farquharson@[recipient's email domain]>
- brain deacon <brain.deacon@[recipient's email domain]>
- dena webber <dena.webber@[recipient's email domain]>
- donald armitage <donald.armitage@[recipient's email domain]>
- erin morse <erin.morse@[recipient's email domain]>
- giovanni hepworth <giovanni.hepworth@[recipient's email domain]>
- katy bridges <katy.bridges@[recipient's email domain]>
- kay greenhill <kay.greenhill@[recipient's email domain]>
- lesa shaddock <lesa.shaddock@[recipient's email domain]>
- marquita drynan <marquita.drynan@[recipient's email domain]>
- mattie wilde <mattie.wilde@[recipient's email domain]>
- pedro mba <pedro.mba@[recipient's email domain]>
- quentin handsacre <quentin.handsacre@[recipient's email domain]>
- robbie cardow <robbie.cardow@[recipient's email domain]>
- rosalind stockill <rosalind.stockill@[recipient's email domain]>
- sandy innes <sandy.innes@[recipient's email domain]>
- summer ketcham <summer.ketcham@[recipient's email domain]>
- susanna lafferty <susanna.lafferty@[recipient's email domain]>
- valeria hendrickson <valeria.hendrickson@[recipient's email domain]>
- vicente yare <vicente.yare@[recipient's email domain]>
RECIPIENT:
- resort@doggiespalace[.]com
- NOTE: This was the recipient in the To: line for all the malspam. The actual recipients were likely BCC-ed.

Shown above: Data from 20 emails pushing Locky ransomware (part 1 of 2).
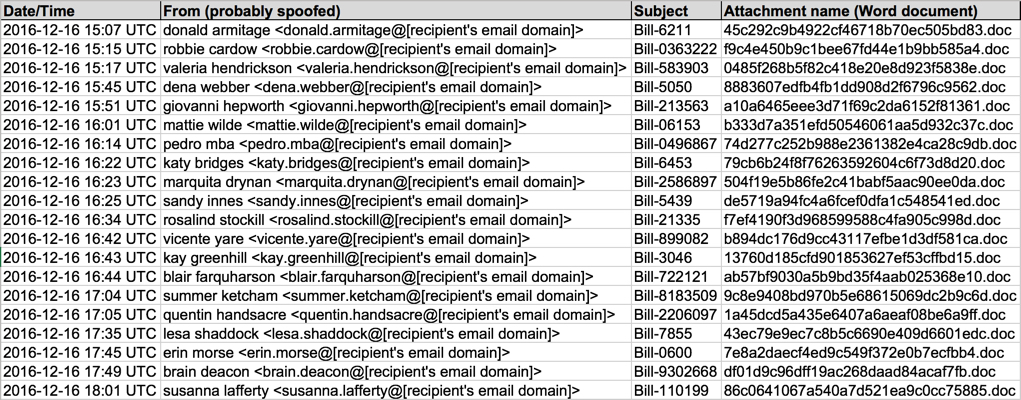
Shown above: Data from 20 emails pushing Locky ransomware (part 2 of 2).
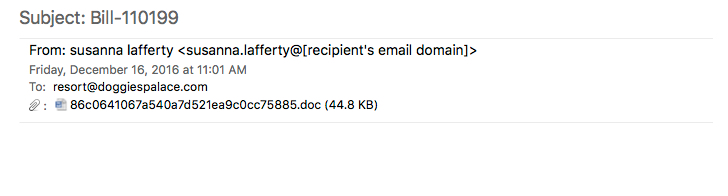
Shown above: An example of these emails.
Shown above: An example of these attachments--Word documents with malicious macros.
TRAFFIC
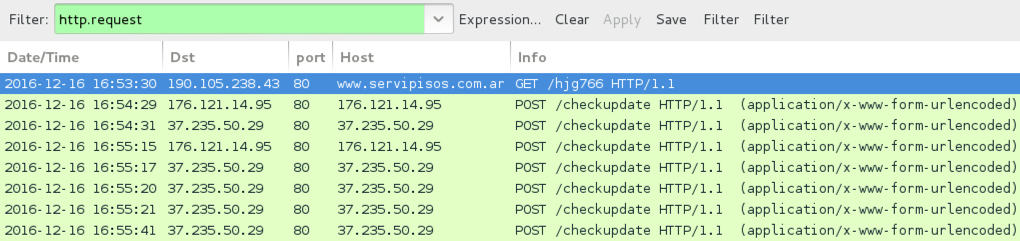
Shown above: An example of infection traffic by the Word macro from one of the emails.
TRAFFIC GENERATED BY THE WORD DOCUMENT MACROS RETRIEVING THE LOCKY RANSOMWARE BINARY:
- 5.135.219[.]3 - gallery.mohammadtarighi[.]ir - GET /hjg766
- 50.62.116[.]1 - mgascca[.]com - GET /hjg766
- 65.39.193[.]50 - theexcelconsultant[.]com - GET /hjg766
- 69.161.143[.]24 - fiddlefire[.]net - GET /hjg766
- 103.9.170[.]249 - pcflame[.]com[.]au - GET /hjg766
- 107.180.54[.]172 - dicksmacker[.]com - GET /hjg766
- 112.140.42[.]29 - kurou.bokunenjin[.]com - GET /hjg766
- 184.168.207[.]1 - nortra-cables[.]com - GET /hjg766
- 190.105.238[.]43 - www.servipisos[.]com[.]ar - GET /hjg766
- 198.105.221[.]209 - amaniinitiative[.]org - GET /hjg766
- 199.116.78[.]152 - mbdvacations[.]com - GET /hjg766
- 216.114.192[.]21 - masonlodgestpeter[.]org - GET /hjg766
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLE:
- 37.235.50[.]29 port 80 - 37.235.50[.]29 - POST /checkupdate
- 176.121.14[.]95 port 80 - 176.121.14[.]95 - POST /checkupdate
TOR DOMAIN FROM THE DECRYPTION INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
LOCKY RANSOMWARE DLL FILE:
- SHA256 hash: 5ec1798e890792c5f8e63fe255561d7cd173bedc1abc41faa2a7be11bb2bd947 (282,624 bytes)
- File name: C:\Users\[username]\AppData\Local\Temp\loppsa2.aww
- DLL entry point: input
WORD DOCUMENT ATTACHMENTS FROM THE EMAILS (READ: SHA256 HASH - FILE NAME):
- 02f01ae140e7e659aec7825012bb4739157d0a02c967035601155031db23c1c3 - f9c4e450b9c1bee67fd44e1b9bb585a4.doc
- 02f01ae140e7e659aec7825012bb4739157d0a02c967035601155031db23c1c3 - 0485f268b5f82c418e20e8d923f5838e.doc
- 22135e6e8ed919cd652d90c0b23f365d851bea05146774194c04f6177f41dc77 - df01d9c96dff19ac268daad84acaf7fb.doc
- 22135e6e8ed919cd652d90c0b23f365d851bea05146774194c04f6177f41dc77 - 86c0641067a540a7d521ea9c0cc75885.doc
- 42f2b6c8fd27400f45d44366e8acfd24b9f13cbcd4eb45a85b319deed55c320e - 13760d185cfd901853627ef53cffbd15.doc
- 42f2b6c8fd27400f45d44366e8acfd24b9f13cbcd4eb45a85b319deed55c320e - ab57bf9030a5b9bd35f4aab025368e10.doc
- 4cd922f1a3071cf93c75604fa4a866922b73c4eb7f495d9cbf8bf4af5d55dced - b333d7a351efd50546061aa5d932c37c.doc
- 78c5af40d37789eacb4bdcc100a2ed16ab33b8762ab51796338c32c416eadab9 - b894dc176d9cc43117efbe1d3df581ca.doc
- 8032edec46d7c4188e9c7f8f57bbbd0552f00a95943d96278d842a3a527fac64 - 9c8e9408bd970b5e68615069dc2b9c6d.doc
- 8032edec46d7c4188e9c7f8f57bbbd0552f00a95943d96278d842a3a527fac64 - 1a45dcd5a435e6407a6aeaf08be6a9ff.doc
- 94e042d3b39b7332152647849ab1b291d25782abf56369e5fc12dc0315a91e6d - 79cb6b24f8f76263592604c6f73d8d20.doc
- 94e042d3b39b7332152647849ab1b291d25782abf56369e5fc12dc0315a91e6d - 504f19e5b86fe2c41babf5aac90ee0da.doc
- 9e5c8d9112889e681a40384aab3f45964b53fe168a6a178ae0abae4adf70d708 - f7ef4190f3d968599588c4fa905c998d.doc
- b9e985e06eaec1a747872a050622faab6c2e8a05b48d27aafaf8162421a8828a - a10a6465eee3d71f69c2da6152f81361.doc
- ca846a081466facaa10e746f083028a45527335d7176c5238d5562f76664745f - 43ec79e9ec7c8b5c6690e409d6601edc.doc
- d48aced8ba2beddb014c70f8405a8c4256f8709efbfa90390cd7cd1b36562d17 - 8883607edfb4fb1dd908d2f6796c9562.doc
- e68e263b2cb2179f68db06744627777aec11f0a9569fc66bd7e539dcef8532cd - 7e8a2daecf4ed9c549f372e0b7ecfbb4.doc
- ef26bbbabaff4a92b0293e6b2857d362d66941e76ec1053db6143cb019058095 - 45c292c9b4922cf46718b70ec505bd83.doc
- fdb6f561e8f49d074904ddaee6900a88d1bf493fa2d1a8c1db1dfe4c8e82786b - de5719a94fc4a6fcef0dfa1c548541ed.doc
- ff6ec87b2e66ae25394b97f3886b0537e536ed92694453196e3c3ea8468bc973 - 74d277c252b988e2361382e4ca28c9db.doc
IMAGES
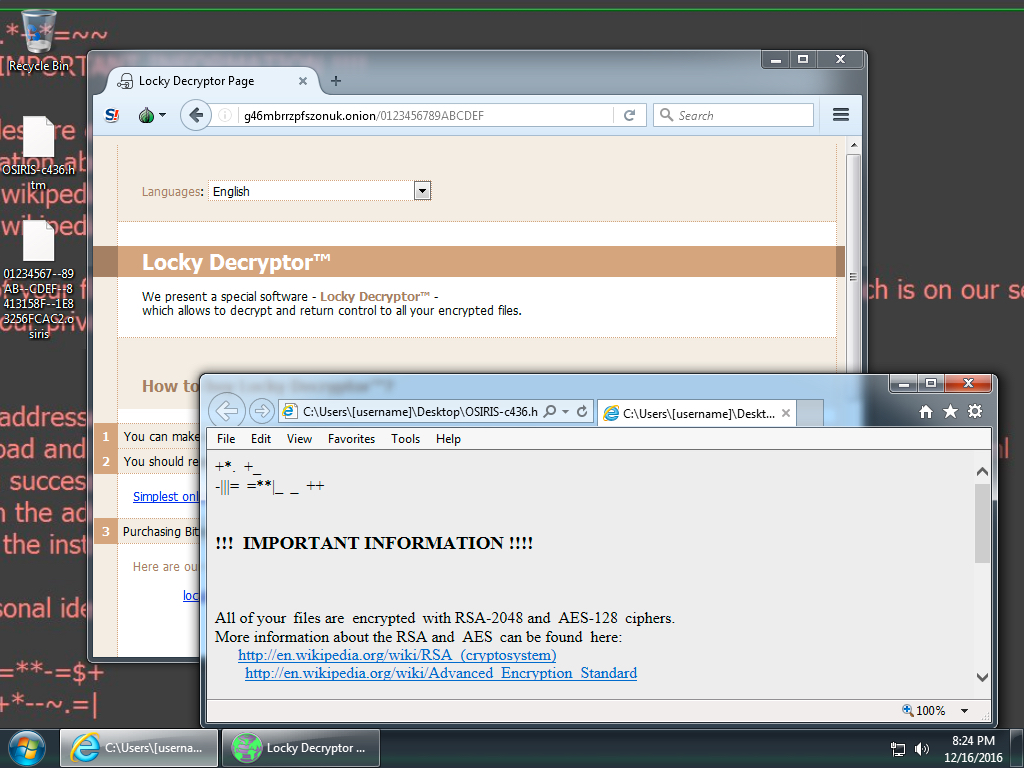
Shown above: Screen shot from an infected Windows desktop. Note the .osiris file extension.
Click here to return to the main page.