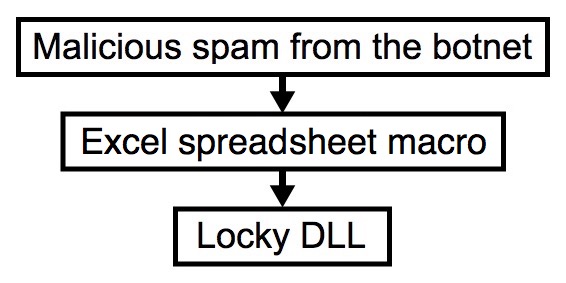
2016-12-20 - "OSIRIS" VARIANT LOCKY RANSOMWARE FROM EXCEL FILES WITH MACROS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-20-Locky-ransomware-infection-traffic.pcap.zip 222.7 kB (222,748 bytes)
- 2016-12-20-Locky-ransomware-files-from-an-infected-host.zip 207.5 kB (207,487 bytes)
- 2016-12-20-email-tracker-for-Locky-ransomware.csv.zip 1.9 kB (1,857 bytes)
- 2016-12-20-emails-for-Locky-ransomware.zip 316.8 kB (316,825 bytes)
- 2016-12-20-email-attachments-for-Locky-ransomware.zip 292.5 kB (292,505 bytes)
NOTES:
- The entry point for today's Locky ransomware DLL sample is vape in case anyone wants to run it with rundll32.exe in a controlled environment.
I know the ransomware authors were thinking of "Loki" when they named it "Locky". But this current pairing of Egyptian and Norse mythology seems like a weird fit.
Shown above: Chain of events for an infection from this email.
THE EMAILS
IP ADDRESSES OF BOTNET HOSTS SENDING THE MALSPAM:
- 39.37.181[.]130 : Pakistan - Pakistan Telecommuication Company Limited
- 43.229.90[.]217 : India - Kottayam Cable Channel Distributors Pvt LTD
- 88.250.146[.]207 : Turkey - 88.250.146[.]207.dynamic.ttnet[.]com[.]tr
- 115.98.166[.]224 : India - Hathway IP Over Cable Internet Access Service
- 116.203.73[.]65 : India - PDSNnew3 Mumbai PDSN
- 160.120.33[.]182 : Ivory Coast (Cote) - Cote D'ivoire Telecom
- 188.211.62[.]237 : Iran - Telecommunication Company Of Tehran
- 190.181.34[.]58 : Bolivia - static-190-181-34-58.acelerate[.]net
- 197.231.48[.]141 : Lesotho - Vodacom-Lesotho Wiman 3G clients
- 213.207.48[.]34 : Albania - VIVO Communications Sh p k
SUBJECT LINE:
- for printing
SPOOFED SENDING ADDRESSES:
- KRIS GARSIDE <kris.garside@murobonito[.]com>
- VIRGINIA DAVIS? <virginia.davis?@evansgeorgiachiropractors[.]com>
- ELBA SCHOPPLE <elba.schopple@actbijverslaving[.]nl>
- JOANN MONTGOMERY <joann.montgomery@gspta[.]com>
- SABRINA KNEEN <sabrina.kneen@fourwheeldriveworld[.]com>
- CAREY SEARLE <carey.searle@platinum[.]com[.]br>
- LAURA HIGGIN <laura.higgin@worldtrade-freightagencies[.]com>
- RACHEL LIGHTNER <rachel.lightner@nathaliasiqueira[.]com[.]br>
- CHRYSTAL STAPLETON <chrystal.stapleton@yorker[.]com[.]ar>
- STACI KEMP <staci.kemp@andromea[.]org>>
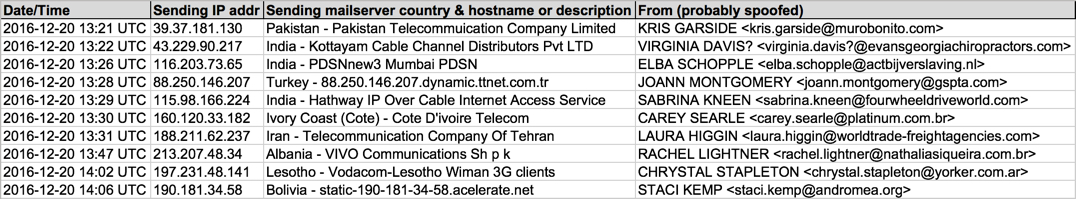
Shown above: Data from 20 email examples pushing Locky ransomware (part 1 of 2).
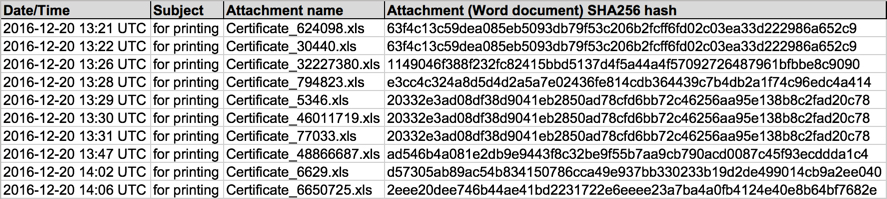
Shown above: Data from 20 email examples pushing Locky ransomware (part 2 of 2).
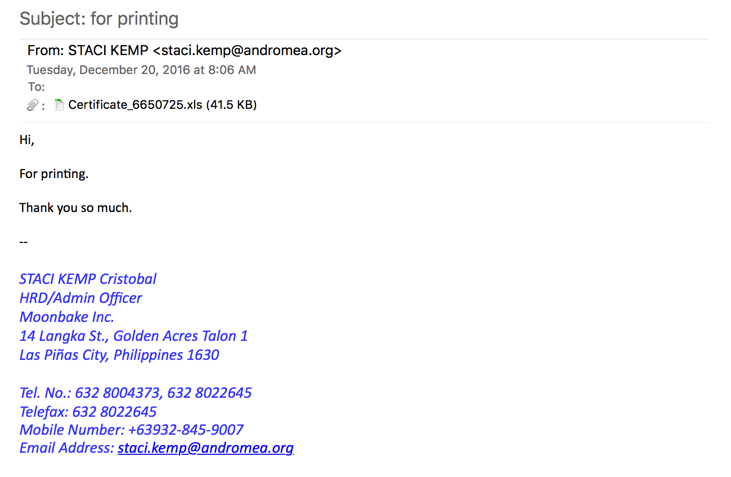
Shown above: An example of these emails.
Shown above: An example of these attachments--Excel spreadsheets with malicious macros.
TRAFFIC
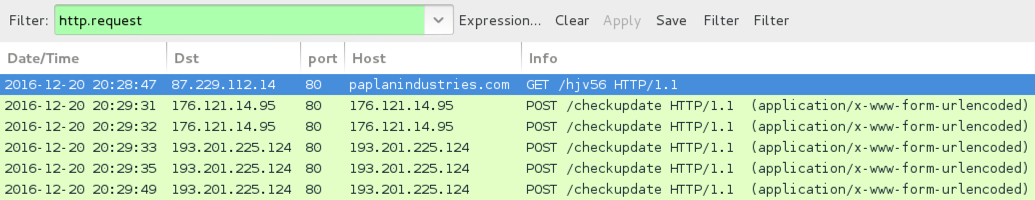
Shown above: An example of infection traffic by the Excel macro from one of the emails.
TRAFFIC GENERATED BY THE EXCEL SPREADSHEET MACROS RETRIEVING THE LOCKY RANSOMWARE BINARY:
- 47.90.76[.]65 port 80 - ashpeptide[.]com - GET /hjv56
- 50.63.202[.]53 port 80 - guide4health[.]info - GET /hjv56
- 69.172.201[.]253 port 80 - no1archeryandsports[.]ca - GET /hjv56
- 82.165.156[.]24 port 80 - friedensschlag[.]de - GET /hjv56
- 87.229.112[.]14 port 80 - paplanindustries[.]com - GET /hjv56
- 162.144.2[.]204 port 80 - www.azrodandclassic[.]com - GET /hjv56
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLE:
- 176.121.14[.]95 port 80 - 176.121.14[.]95 - POST /checkupdate
- 193.201.225[.]124 port 80 - 193.201.225[.]124 - POST /checkupdate
TOR DOMAIN FROM THE DECRYPTION INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
LOCKY RANSOMWARE DLL FILE:
- SHA256 hash: 53a9fedfab0d20d64916f1a03620e2be255c5d8ec334370999f0dd03ca7a7624 (266,240 bytes)
- File name: C:\Users\[username]\AppData\Local\Temp\momerk2.vip
- DLL entry point: vape
EXCEL SPREADSHEET ATTACHMENTS FROM THE EMAILS (SHA256 HASH - FILE NAME):
- 1149046f388f232fc82415bbd5137d4f5a44a4f57092726487961bfbbe8c9090 - Certificate_32227380.xls
- 20332e3ad08df38d9041eb2850ad78cfd6bb72c46256aa95e138b8c2fad20c78 - Certificate_5346.xls
- 20332e3ad08df38d9041eb2850ad78cfd6bb72c46256aa95e138b8c2fad20c78 - Certificate_77033.xls
- 20332e3ad08df38d9041eb2850ad78cfd6bb72c46256aa95e138b8c2fad20c78 - Certificate_46011719.xls
- 2eee20dee746b44ae41bd2231722e6eeee23a7ba4a0fb4124e40e8b64bf7682e - Certificate_6650725.xls
- 63f4c13c59dea085eb5093db79f53c206b2fcff6fd02c03ea33d222986a652c9 - Certificate_30440.xls
- 63f4c13c59dea085eb5093db79f53c206b2fcff6fd02c03ea33d222986a652c9 - Certificate_624098.xls
- ad546b4a081e2db9e9443f8c32be9f55b7aa9cb790acd0087c45f93ecddda1c4 - Certificate_48866687.xls
- d57305ab89ac54b834150786cca49e937bb330233b19d2de499014cb9a2ee040 - Certificate_6629.xls
- e3cc4c324a8d5d4d2a5a7e02436fe814cdb364439c7b4db2a1f74c96edc4a414 - Certificate_794823.xls
IMAGES
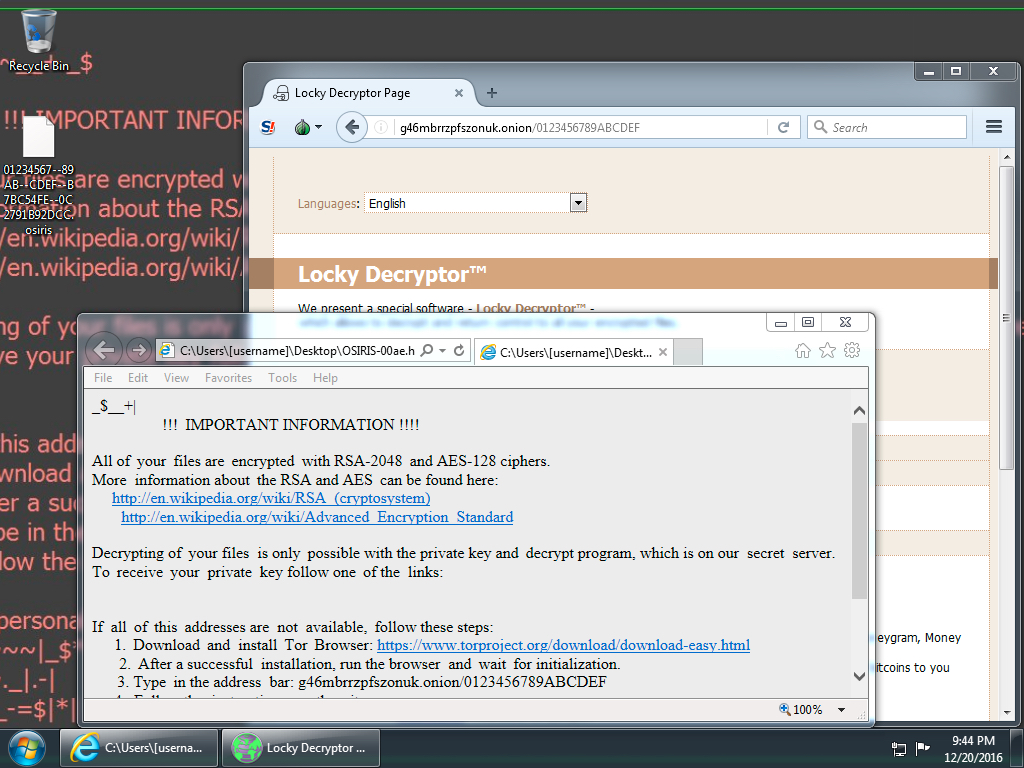
Shown above: Screen shot from an infected Windows desktop. Note the .osiris file extension.
Click here to return to the main page.