2017-01-04 - "BLANK SLATE" CAMPAIGN SENDS CERBER RANSOMWARE
ASSOCIATED FILES:
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
- 2017-01-04-Cerber-ransomware-infection-traffic.pcap.zip 208.3 kB (208,323 bytes)
- 2017-01-04-Cerber-ransomware-infection-traffic.pcap (304,487 bytes)
- 2017-01-04-Blank-Slate-email-and-Cerber-ransomware.zip 541.7 kB (541,663 bytes)
- 15010386517237.zip (25,491 bytes)
- 19206.doc (62,464 bytes)
- 2017-01-04-Blank-Slate-malspam-0724-UTC.eml (34,863 bytes)
- 2017-01-04-Cerber-ransomware-decryption-instructions_7A7N_README_.hta (67,448 bytes)
- 2017-01-04-Cerber-ransomware-decryption-instructions_7A7N_README_.jpg (226,029 bytes)
- Roaming.exE (229,661 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
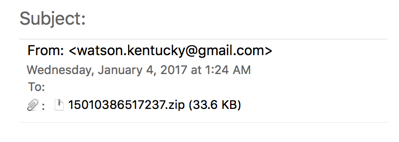
Shown above: Screenshot of the email.
NOTE: The sender's address was spoofed--the message did not come from a gmail account.
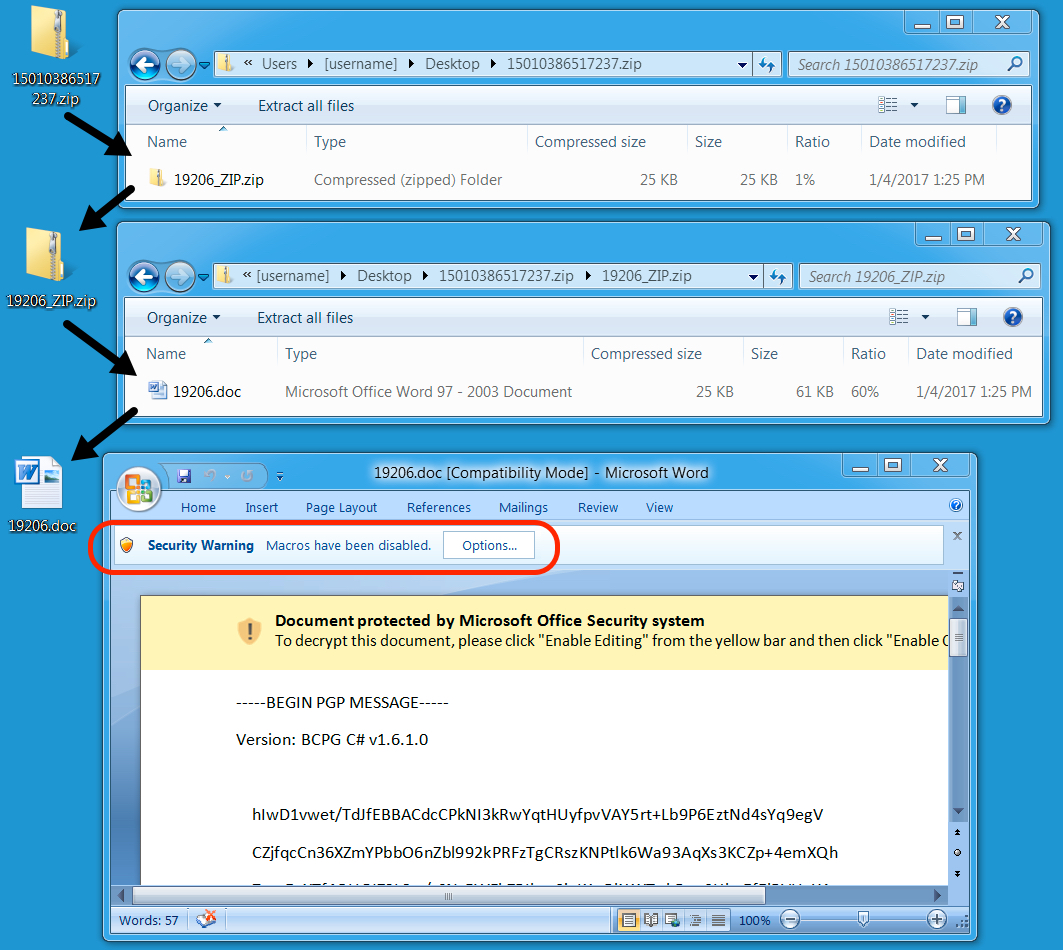
Shown above: Malicious word document extracted from the email attachment.
NOTE: Enabling macros on that Word document will download and run Cerber ransomware.
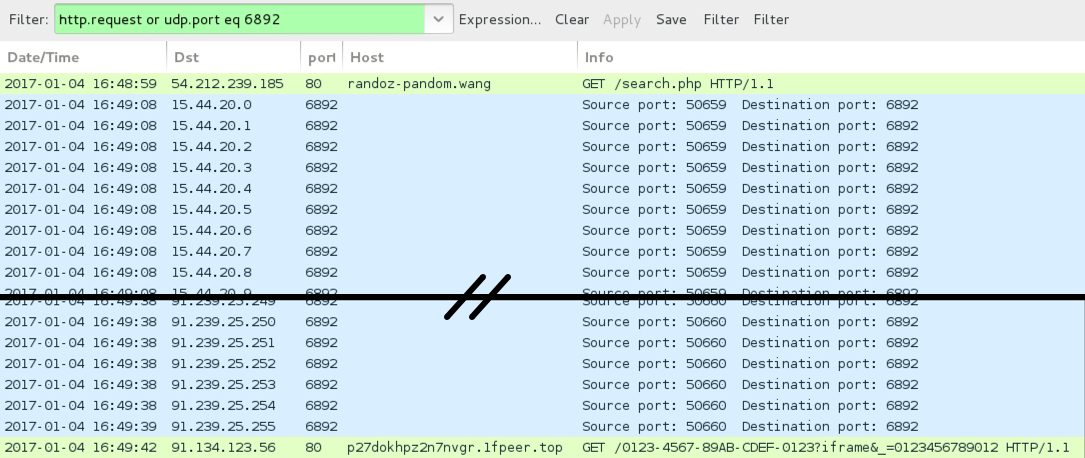
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- 54.212.239[.]185 port 80 - randoz-pandom[.]wang - GET /search.php - Word macro downloading the Cerber ransomware
- 15.44.20[.]0 to 15.44.20[.]31 (15.44.20[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 16.43.12[.]0 to 16.43.12[.]31 (16.43.12[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.134.123[.]56 port 80 - p27dokhpz2n7nvgr.1fpeer[.]top - Cerber ransomware post-infection HTTP traffic
FILE HASHES
ATTACHMENT AND EXTRACTED WORD DOCUMENT:
- SHA256 hash: 4fb39a97721f066af6a551274550461874138683977bf5e52acd937ea19bfc0c (25,491 bytes)
File name: 15010386517237.zip
- SHA256 hash: b8658a91138b7be842293612c1c1d9dad873ed4638f84262cb58fcee60eab8a4 (62,464 bytes)
File name: 19206.doc
- NOTE: The document was double-zipped. It was a zip archive containing a zip archive of the Word document.
DOWNLOADED MALWARE (CERBER RANSOMWARE):
- SHA256 hash: 03aa2410d07ea49dd6f05f2e0b0815ad400a83725ac88281b5f85ee7a7314bc7 (229,661 bytes)
File path: C:\Users\[username]\Roaming\Roaming.exE
Shown above: A copy of the malware before it deleted itself.
Click here to return to the main page.