2017-01-05 - BRAZIL TARGETED MALWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This is the same campaign I documented on 2016-09-21, 2016-08-30, and 2016-08-26.
- The campaign has continued since then, but I haven't documented a recent example until now.
- See the 2016-08-26 blog post for a list of my previous posts covering this threat actor.
ASSOCIATED FILES:
- 2017-01-05-Brazil-targeted-malware-infection.pcap.zip 1.3 MB (1,309,387 bytes)
- 2017-01-05-Brazil-targeted-malware-infection.pcap (1,728,547 bytes)
- 2017-01-05-Brazil-malspam-20-examples.zip 37.2 kB (37,168 bytes)
- 2017-01-04-Brazil-malspam-1412-UTC.eml (3,075 bytes)
- 2017-01-04-Brazil-malspam-1656-UTC.eml (3,077 bytes)
- 2017-01-04-Brazil-malspam-2111-UTC.eml (3,075 bytes)
- 2017-01-04-Brazil-malspam-2154-UTC.eml (3,075 bytes)
- 2017-01-04-Brazil-malspam-2316-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0250-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0313-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0331-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0342-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0644-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0759-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0852-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-0956-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-1049-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-1201-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-1210-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-1218-UTC.eml (3,074 bytes)
- 2017-01-05-Brazil-malspam-1358-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-1438-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-malspam-1627-UTC.eml (3,075 bytes)
- 2017-01-05-Brazil-targeted-malware-and-artifacts.zip 1.4 MB (1,400,812 bytes)
- 05012017HLiMHwQ9RfYE4G5KrDQR19Z6O4lHh828377.vbe (548 bytes)
- Ionic.Zip.Reduced.dll (253,440 bytes)
- JUNGLE-PC.aes (16 bytes)
- JUNGLE-PC.zip (1,087,252 bytes)
- JUNGLE-PCx.ocx (440 bytes)
- SYSJUNGLEPC37.txt (3,242 bytes)
- dll.dll.exe (396,480 bytes)
- tmpB04B.tmp (11,548 bytes)
- wimgwdfh.yim.vbs (53,223 bytes)
EMAILS
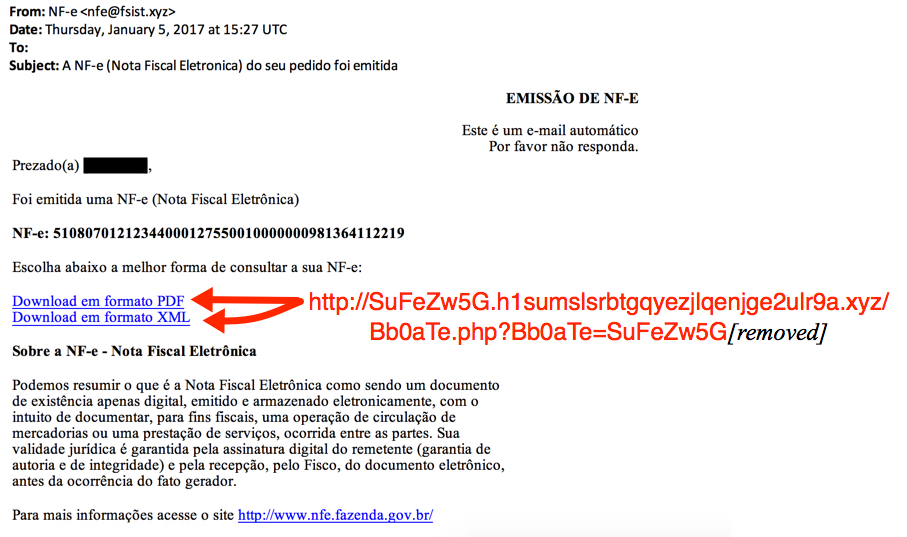
Shown above: Screen shot of the email.
EMAIL HEADERS:
- From: NF-e <nfe@fsist[.]xyz>
- Subject: A NF-e (Nota Fiscal Eletronica) do seu pedido foi emitida
TRAFFIC
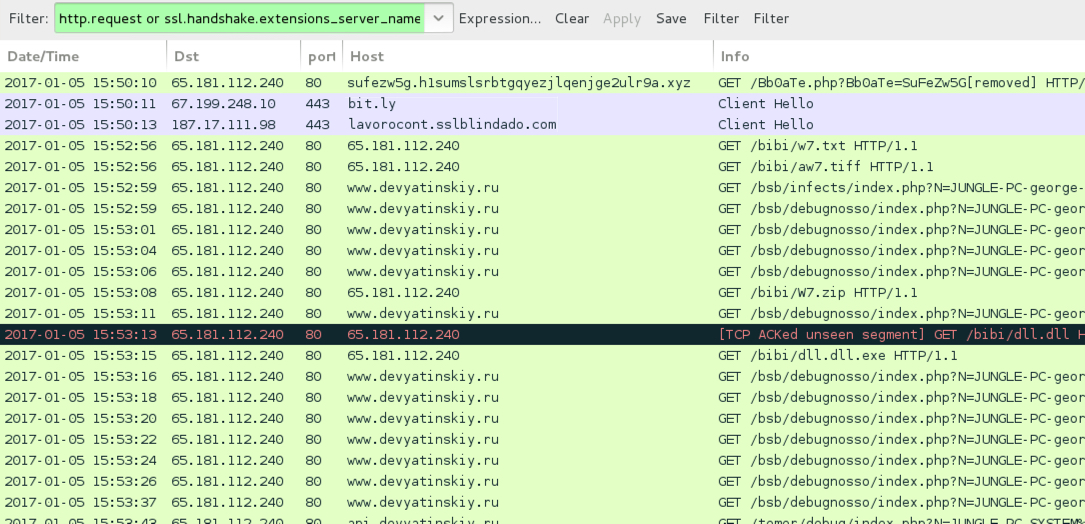
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- bit[.]ly - GET /2iLZYgQ - redirect from the link in the email (HTTPS)
- 187.17.111.98 port 443 - lavorocont.sslblindado[.]com - GET /sys/ [returns the malicious .vbs file]
- 65.181.112[.]240 port 80 - 65.181.112[.]240 - GET /bibi/w7.txt
- 65.181.112[.]240 port 80 - 65.181.112[.]240 - GET /bibi/aw7.tiff
- 65.181.112[.]240 port 80 - 65.181.112[.]240 - GET /bibi/W7.zip
- 65.181.112[.]240 port 80 - 65.181.112[.]240 - GET /bibi/dll.dll
- 65.181.112[.]240 port 80 - 65.181.112[.]240 - GET /bibi/dll.dll.exe
- 65.181.112[.]240 port 80 - www.devyatinskiy[.]ru - HTTP post-infection traffic
- 65.181.112[.]240 port 80 - api.devyatinskiy[.]ru - HTTP post-infection traffic
- 65.181.113[.]204 port 443 - ssl.houselannister[.]top - IRC traffic (botnet command and control)
- DNS query for: imestre.houselannister[.]top - response: 127.0.0.1
MALWARE
ARTIFACTS FOUND ON THE INFECTED HOST:
- Downloaded from the email link: 05012017HLiMHwQ9RfYE4G5KrDQR19Z6O4lHh828377.vbe
- C:\Users\george-of-the-jungle\AppData\Local\Temp\Java\dll.dll.exe
- C:\Users\george-of-the-jungle\AppData\Local\Temp\Java\Ionic.Zip.Reduced.dll
- C:\Users\george-of-the-jungle\AppData\Local\Temp\Java\JUNGLE-PC.aes
- C:\Users\george-of-the-jungle\AppData\Local\Temp\Java\JUNGLE-PC.zip
- C:\Users\george-of-the-jungle\AppData\Local\Temp\tmpB04B.tmp
- C:\Windows\System32\Java\Ionic.Zip.Reduced.dll
- C:\Windows\System32\Java\JUNGLE-PC.aes
- C:\Windows\System32\Java\JUNGLE-PC.zip
- C:\Windows\System32\Java\wimgwdfh.yim.vbs
- C:\Windows\System32\JUNGLE-PCx.ocx
- C:\Windows\System32\Tasks\SYSJUNGLEPC37
SHA256 HASHES FOR THE ARTIFACTS:
- d1faae74de1d15de0fc9ff900071b2c93e8829c16cf83d3c5b8d54f0c7f362ab - 05012017HLiMHwQ9RfYE4G5KrDQR19Z6O4lHh828377.vbe
- a4009288982e4c30d22b544167f72db882e34f0fda7d4061b2c02c84688c0ed1 - Ionic.Zip.Reduced.dll
- 910dc2d1dd279269bbc44b0cade6309fe2134f6fd9d27a7dbb001d5becbac1dc - JUNGLE-PC.aes
- e68121b88cbb2ee953ecb9d71dbdbf3948f40564a31babb7825405a0af581a54 - JUNGLE-PC.zip
- 9e74abc443e40f22ff46f7897ff5bf600948128d9e04acd4a47ef972b75e3297 - JUNGLE-PCx.ocx
- 7198608af1fb82d3fbe17bbd58e93b97ab615245d467deba926e90a830799fa4 - SYSJUNGLEPC37.txt
- 3b08535b4add194f5661e1131c8e81af373ca322cf669674cf1272095e5cab95 - dll.dll.exe
- 4de58ed6c0f43356af5f5f957b2adee3eb2f690c89e4201742499ca57b9b9482 - tmpB04B.tmp
- 372d9dc21f9c11c09c1aaee140e27af2d71e45ba326ac7ecfb635dbba2f5e765 - wimgwdfh.yim.vbs
ADDITIONAL INFO
Here are the links I saw from the emails:
- 1mACnzZm.h1sumslsrbtgqyezjlqenjge2ulr9a[.]xyz - GET/1Sunfe.php?1Sunfe=1mACnzZm[removed]
- DEma2Ar3.h1sumslsrbtgqyezjlqenjge2ulr9a[.]xyz - GET/5oWcpq.php?5oWcpq=DEma2Ar3[removed]
- KUQv28sr.h1sumslsrbtgqyezjlqenjge2ulr9a[.]xyz - GET/R1D6xA.php?R1D6xA=KUQv28sr[removed]
- Spm6K04J.h1sumslsrbtgqyezjlqenjge2ulr9a[.]xyz - GET/dh9VeW.php?dh9VeW=Spm6K04J[removed]
- SuFeZw5G.h1sumslsrbtgqyezjlqenjge2ulr9a[.]xyz - GET/Bb0aTe.php?Bb0aTe=SuFeZw5G[removed]
- X0Y6BwRr.h1sumslsrbtgqyezjlqenjge2ulr9a[.]xyz - GET/vX7jiO.php?vX7jiO=X0Y6BwRr[removed]
- 2uG3I3WM.iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz - GET/VAPNI2.php?VAPNI2=2uG3I3WM[removed]
- 3H6pQOGu.iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz - GET/5OslGe.php?5OslGe=3H6pQOGu[removed]
- 8aEbOeYF.iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz - GET/wFF35I.php?wFF35I=8aEbOeYF[removed]
- FLFqnm8c.iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz - GET/sjv2wV.php?sjv2wV=FLFqnm8c[removed]
- Fz8gXEaI.iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz - GET/RgcO7I.php?RgcO7I=Fz8gXEaI[removed]
- qjiuRU9d.iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz - GET/aV8vOF.php?aV8vOF=qjiuRU9d[removed]
- uJP003pF.iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz - GET/CVYj0t.php?CVYj0t=uJP003pF[removed]
- ruIAi0Qv.p4d4rjooop9njubdzanx0modrrewdn[.]xyz - GET/3hIwng.php?3hIwng=ruIAi0Qv[removed]
- UEpC0dzI.p4d4rjooop9njubdzanx0modrrewdn[.]xyz - GET/er9Dfp.php?er9Dfp=UEpC0dzI[removed]
- wWrkhgu5.p4d4rjooop9njubdzanx0modrrewdn[.]xyz - GET/4xu6rB.php?4xu6rB=wWrkhgu5[removed]
- af7LQRRd.x00mnmwvua7mi11z5ckhyqfn7qsf9t[.]xyz - GET/dKstM2.php?dKstM2=af7LQRRd[removed]
- qx1dTCLN.x00mnmwvua7mi11z5ckhyqfn7qsf9t[.]xyz - GET/XV1GAf.php?XV1GAf=qx1dTCLN[removed]
- L35n3BTe.x00mnmwvua7mi11z5ckhyqfn7qsf9t[.]xyz - GET/6sA4hF.php?6sA4hF=L35n3BTe[removed]
- 8ntrM8N7.x00mnmwvua7mi11z5ckhyqfn7qsf9t[.]xyz - GET/akj3Wu.php?akj3Wu=8ntrM8N7[removed]
Here are the base domains from the above URLs:
- h1sumslsrbtgqyezjlqenjge2ulr9a[.]xyz
- iy7jkiidp5xqcesvhhyeuoobwhbotu[.]xyz
- p4d4rjooop9njubdzanx0modrrewdn[.]xyz
- x00mnmwvua7mi11z5ckhyqfn7qsf9t[.]xyz
Those four domains were registered on 2017-01-02 with the following info:
- Sponsoring Registrar: PDR Ltd. d/b/a PublicDomainRegistry[.]com
- Registrant name: Soren Laderoute
- Registrant state/province: Kiev
- Registrant country: Ukraine
- Registrant email: sorenladeroute@protonmail[.]com
Note: fsist[.]xyz and jioapnllybzbexyxyyodecgbvuit16[.]xyz are also registered to Soren Laderoute with the same contact data.
When I pinged them today, all the above domains appeared to be hosted on 65.181.112[.]240.
- IP Address: 65.181.112[.]240
- IP Location: US - Solar VPS
- ASN: AS25653 FORTRESSITX - FortressITX, US
- Abuse email: abuse@solarvps[.]com
Click here to return to the main page.
