2017-01-06 - SUNDOWN EK FROM 188.165.163[.]226 AND 93.190.143[.]201
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-06-Sundown-EK-sends-Zloader.pcap.zip 763.1 kB (763,089 bytes)
- 2017-01-06-Sundown-EK-sends-Zloader.pcap (978,479 bytes)
- 2017-01-06-Sundown-EK-artifacts-and-ZLoader.zip 321.4 kB (321,410 bytes)
- 2017-01-06-Sundown-EK-fash-exploit-78493521.swf (45,026 bytes)
- 2017-01-06-Sundown-EK-fash-exploit-9643522803.swf (14,088 bytes)
- 2017-01-06-Sundown-EK-landing-page.txt (73,418 bytes)
- 2017-01-06-Sundown-EK-payload-Zloader.exe (244,224 bytes)
- 2017-01-06-run-Sundown-EK-other-exploit-JHgfjhc.png (52,591 bytes)
BACKGROUND ON SUNDOWN EXPLOIT KIT:
- Nick Biasini from Cisco's Talos threat intelligence team, wrote about Sundown EK in this October 2016 article: Sundown EK: You Better Take Care.
OTHER NOTES:
- The URL patterns for Sundown EK changed starting 2017-01-05 to what I'm showing for today.
TRAFFIC
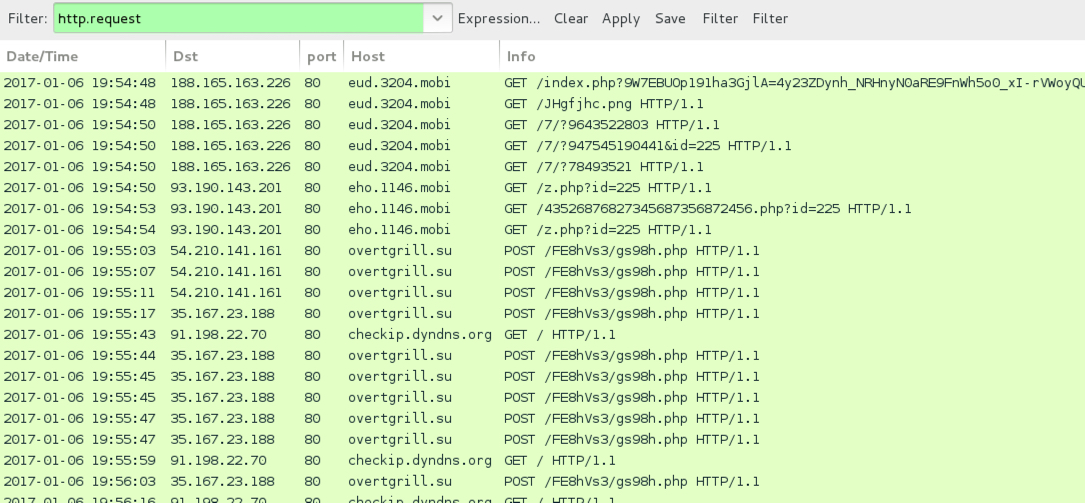
Shown above: Pcap from the infection traffic filtered in Wireshark
SUNDOWN EK:
- 188.165.163[.]226 port 80 - eud.3204[.]mobi - GET /index.php?9W7EBUOp191ha3GjlA=4y23ZDynh_NRHnyN0aRE9FnWh5o0_xI-rVWoyQUxcwvxksnowbciR2Mb
- 188.165.163[.]226 port 80 - eud.3204[.]mobi - GET /JHgfjhc.png
- 188.165.163[.]226 port 80 - eud.3204[.]mobi - GET /7/?9643522803
- 188.165.163[.]226 port 80 - eud.3204[.]mobi - GET /7/?947545190441&id=225
- 188.165.163[.]226 port 80 - eud.3204[.]mobi - GET /7/?78493521
- 93.190.143[.]201 port 80 - eho.1146[.]mobi - GET /z.php?id=225
- 93.190.143[.]201 port 80 - eho.1146[.]mobi - GET /43526876827345687356872456.php?id=225
- 93.190.143[.]201 port 80 - eho.1146[.]mobi - GET /z.php?id=225
POST INFECTION TRAFFIC:
- 54.210.141[.]161 port 80 - overtgrill[.]su - POST /FE8hVs3/gs98h.php
- 35.167.23[.]188 port 80 - overtgrill[.]su - POST /FE8hVs3/gs98h.php
- checkip.dyndns[.]org - GET /
FILE HASHES
EXPLOITS:
- SHA256 hash: 0744ba67c5f8210fcdcf4acb328df68780e96d10f2c68b8eddbb9a355bca213e
File description: Sundown EK Flash exploit returned after GET /7/?9643522803
File size: 14,088 bytes
- SHA256 hash: 67d598c6acbd6545ab24bbd44cedcb825657746923f47473dc40d0d1f122abb6
File description: Sundown EK Flash exploit returned after GET /7/?78493521
File size: 45,026 bytes
- SHA256 hash: 49cb62e64ce93a825e5fb9b20dc2407a0d943d5c49fa06a464b76c0f04efcc94
File description: Sundown EK exploit returned after GET /JHgfjhc.png
File size: 52,591 bytes
PAYLOADS AND FOLLOW-UP MALWARE:
- SHA256 hash: 05b96b412347a1383d7add644b2bc29142ec79df581655ffca4731dbde742d40
File description: Zloader (Terdot.A) sent as Sundown EK payload
File size: 244,224 bytes
File path: C:\Users\[username]\AppData\Local\Temp\rad0B36A.tmp.exe
File path: C:\Users\[username]\AppData\Local\Temp\rad5EFE3.tmp.exe
File path: C:\Users\[username]\AppData\Local\Temp\radB325B.tmp.exe
File path: C:\Users\[username]\AppData\Local\Temp\rgh.exe
File path: C:\Users\[username]\AppData\Local\Temp\sf.exe
File path: C:\Users\[username]\AppData\Local\Temp\yrre.exe
File path: C:\Users\[username]\AppData\Local\Temp\z.tmp
IMAGES
NOTE: For the folders and most of the files shown below, the names are randomized, so if you infected a Windows host with the same malware sample, you won't have the same folder or file names (except for php.exe and php5ts.dll).
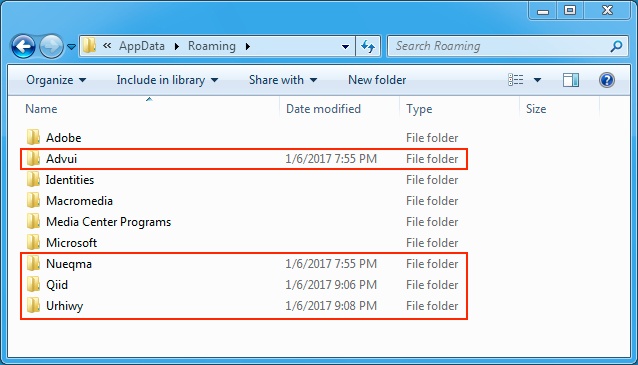
Shown above: Some of the folders created on the infected Windows host.
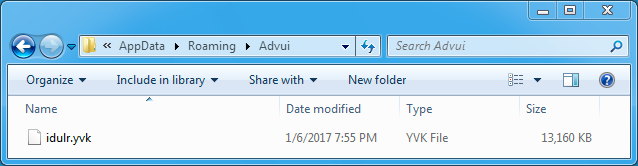
Shown above: Contents of C:\Users\[username]\AppData\Roaming\Advui
Shown above: Contents of C:\Users\[username]\AppData\Roaming\Nueqma
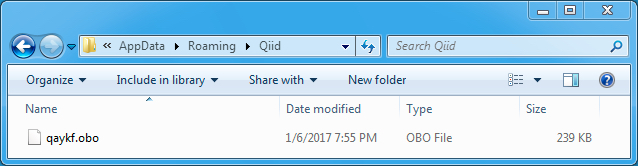
Shown above: Contents of C:\Users\[username]\AppData\Roaming\Qiid
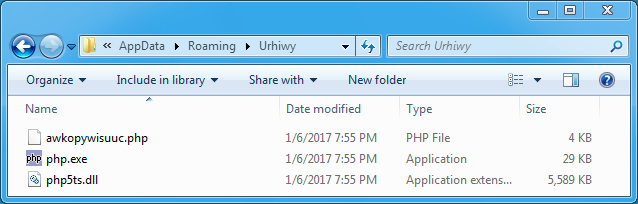
Shown above: Contents of C:\Users\[username]\AppData\Roaming\Urhiwy
Click here to return to the main page.
