2017-01-09 - "BLANK SLATE" CAMPAIGN SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-09-Cerber-ransomware-infection-traffic.pcap.zip 209.1 kB (209,112 bytes)
- 2017-01-09-Cerber-ransomware-infection-traffic.pcap (303,525 bytes)
- 2017-01-09-Blank-Slate-malspam-tracker.csv.zip 0.7 kB (731 bytes)
- 2017-01-09-Blank-Slate-maslpam-tracker.csv (857 bytes)
- 2017-01-09-Blank-Slate-emails-and-Cerber-ransomware.zip 3.6 MB (3,574,054 bytes)
- emails / 2017-01-06-Blank-Slate-malspam-2127-UTC.eml (43,717 bytes)
- emails / 2017-01-07-Blank-Slate-malspam-1319-UTC.eml (44,224 bytes)
- emails / 2017-01-07-Blank-Slate-malspam-1519-UTC.eml (35,996 bytes)
- emails / 2017-01-07-Blank-Slate-malspam-1829-UTC.eml (43,448 bytes)
- emails / 2017-01-07-Blank-Slate-malspam-2136-UTC.eml (45,077 bytes)
- emails / 2017-01-08-Blank-Slate-malspam-2133-UTC.eml (58,928 bytes)
- emails / 2017-01-08-Blank-Slate-malspam-2238-UTC.eml (59,681 bytes)
- emails / 2017-01-09-Blank-Slate-malspam-0112-UTC.eml (51,706 bytes)
- emails / 2017-01-09-Blank-Slate-malspam-0119-UTC.eml (49,647 bytes)
- emails / 2017-01-09-Blank-Slate-malspam-0154-UTC.eml (57,251 bytes)
- emails / 2017-01-09-Blank-Slate-malspam-1047-UTC.eml (37,889 bytes)
- emails / 2017-01-09-Blank-Slate-malspam-1106-UTC.eml (38,115 bytes)
- emails / 2017-01-09-Blank-Slate-malspam-1624-UTC.eml (36,090 bytes)
- attachments / 17463.zip (27,902 bytes)
- attachments / 3564149445.zip (31,847 bytes)
- attachments / 4820876899.zip (33,055 bytes)
- attachments / 04398408565.zip (32,439 bytes)
- attachments / 1125380733161.zip (26,337 bytes)
- attachments / 11932415970879.zip (27,738 bytes)
- attachments / 35957656855277.zip (32,061 bytes)
- attachments / 850474845283453.zip (26,415 bytes)
- attachments / INFO_602960_[removed].zip (36,444 bytes)
- attachments / INFO_694972_[removed].zip (42,077 bytes)
- attachments / INFO_619608933_[removed].zip (43,865 bytes)
- attachments / INFO_949273973_[removed].zip (43,310 bytes)
- attachments / INFO_956010938_[removed].zip (37,962 bytes)
- extracted-Word-docs / 2241.doc (91,648 bytes)
- extracted-Word-docs / 3423.doc (107,520 bytes)
- extracted-Word-docs / 6743.doc (64,000 bytes)
- extracted-Word-docs / 13729.doc (103,424 bytes)
- extracted-Word-docs / 17807.doc (78,336 bytes)
- extracted-Word-docs / 18493.doc (75,264 bytes)
- extracted-Word-docs / 19221.doc (77,312 bytes)
- extracted-Word-docs / 21458.doc (75,776 bytes)
- extracted-Word-docs / 22551.doc (72,704 bytes)
- extracted-Word-docs / 22980.doc (94,720 bytes)
- extracted-Word-docs / 22987.doc (78,848 bytes)
- extracted-Word-docs / 23861.doc (106,496 bytes)
- extracted-Word-docs / 26211.doc (75,776 bytes)
- Cerber-ransomware-files / 2017-01-07-Cerber-ransomware-example-1-of-3.exe (240,191 bytes)
- Cerber-ransomware-files / 2017-01-07-Cerber-ransomware-example-2-of-3.exe (240,191 bytes)
- Cerber-ransomware-files / 2017-01-07-Cerber-ransomware-example-3-of-3.exe (240,191 bytes)
- Cerber-ransomware-files / 2017-01-08-Cerber-ransomware-example.exe (245,422 bytes)
- Cerber-ransomware-files / 2017-01-09-Cerber-ransomware-example-1-of-5.exe (307,575 bytes)
- Cerber-ransomware-files / 2017-01-09-Cerber-ransomware-example-2-of-5.exe (307,575 bytes)
- Cerber-ransomware-files / 2017-01-09-Cerber-ransomware-example-3-of-5.exe (263,616 bytes)
- Cerber-ransomware-files / 2017-01-09-Cerber-ransomware-example-4-of-5.exe (261,423 bytes)
- Cerber-ransomware-files / 2017-01-09-Cerber-ransomware-example-5-of-5.exe (261,423 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
TRAFFIC
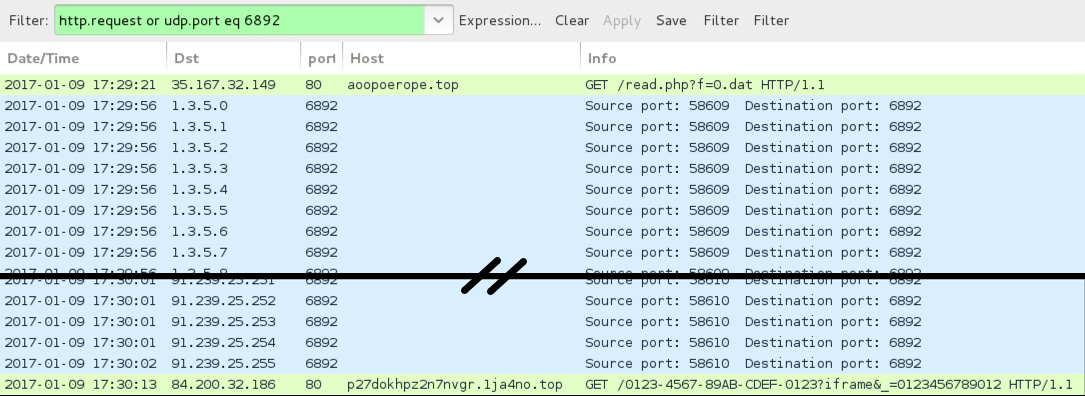
Shown above: Pcap from an example of infection traffic filtered in Wireshark
DOMAINS FROM THE TRAFFIC EXAMPLE ON 2017-01-09:
- 1.3.5[.]0 to 1.3.5[.]31 (1.3.5[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 2.4.6[.]0 to 2.4.6[.]31 (2.4.6[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 84.200.32[.]186 port 80 - p27dokhpz2n7nvgr.1ja4no[.]top - Cerber ransomware post-infection HTTP traffic
URLS FROM THE VARIOUS WORD MACROS TO RETRIEVE CERBER RANSOMWARE:
- trendsnonstop[.]top - GET /search.php
- lolotocoporo[.]wang - GET /search.php
- bogidoggy[.]top - GET /search.php
- poooperfath[.]top - GET /read.php?f=0.dat
- aoopoerope[.]top - GET /read.php?f=0.dat
- NOTE: These domains were hosted on Amazon Web Services (AWS) and their IP addresses were not static.
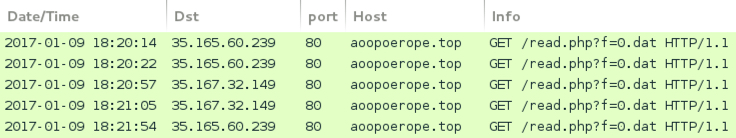
Shown above: Example of different AWS IP addresses for the same malicious domain.
FILE HASHES
EMAIL ATTACHMENTS:
- 91661280c76f8c73915e920a630036fea3d4f63e7611c813387d145f2b32e37e - 17463.zip
- 37cfa71a868f9be3de6b4ff03ccddd62a420b925868f0b8d327940e3600c6e22 - 3564149445.zip
- 2c61152194d4638e0be7a43b4ab666cf1f5400763ee28f7f59efb9b8cb994bc0 - 4820876899.zip
- 81b6c7e43e848be6cd91a19bf1375c507c6df33c368493e9169c30d3b0b5b6d7 - 04398408565.zip
- d289dde3206139a53d6f0588cc69778a00ca1c11f515166c7425befe0564c5ac - 1125380733161.zip
- a44125530bbe7180076ef4f6696f2aaf24a9ed944a8e1ed6bf9741394b2a9129 - 11932415970879.zip
- 60ff7ac17a2fbd42125589df504d35741d3eff591a8ea8058def625c77fada08 - 35957656855277.zip
- 905f1d3cf0d39968b1641cd51d74afe91c5beb12d0fb227eaf66330c5689e2b1 - 850474845283453.zip
- 23f3e2c7057325559bcdff5e67c7f1b92c94a7e2bf4d3bf36f4ed534bf2610df - INFO_602960_[removed].zip
- 9effccd1967c6176db0422a515e4d6c220e6a386ee948d4137fdfa94eabc62cd - INFO_694972_[removed].zip
- c9d9833ff051fae97dad891fcd5aa9080d7bf56da3a501d369205d4857f2d8f3 - INFO_619608933_[removed].zip
- 5e6bcac64b33366bae7b5f247f460844b4913b426f7a4da4eba92b4d75086e03 - INFO_949273973_[removed].zip
- ca3caed716c14014f63ea069763a5ee7192c4d6c7b1c8f782199982442a3e658 - INFO_956010938_[removed].zip
EXTRACTED WORD DOCUMENTS:
- a71ee83eeab559bb3008da514eff45af8a4273a6ff818b617e6faca0964bd846 - 2241.doc
- cbc5a0644a7c91f1adbc3ce65c4464f4f692c105cd2890228e98fc7748a554c8 - 3423.doc
- c9f7fc72a9eb7b9497edcc992c9c7853bad18fd6798e1a478ae8f6858dc70123 - 6743.doc
- 3a0b32f83cd6e7bd4a4e1b4b0cd1e11e17b1354fd38bd36cee7a2db54cdb12de - 13729.doc
- 423c4340b8b3749337b2e9f0fcce2f66146bf359116a3177abf4f94b17eea17d - 17807.doc
- b67b8a437cef8eb4cd370a48d7bf6ffe05aa7a75f44ba7be0639c3f10f612106 - 18493.doc
- 356c39cbed3733cd7178c8067a8725bc299a029443bc0b7c0f37b5d7e5392f88 - 19221.doc
- 13f144ceea5864daaae7638d8fda4c1655231952b4a4f75bef039edcb25a068b - 21458.doc
- fc5c3292ad93d7b4d5cd0e409307fff0f1500a0d56383715c74163d3e0edbc70 - 22551.doc
- c5cb617e4b5645919804213d7c9c4e414a986cd60cb9397dd969845f4e7a7f5e - 22980.doc
- b3f208b06b59c8c99569dfcfcde78fb05fac4cce49730999967ebb6b035a3385 - 22987.doc
- 2d139b59f3c7c1b5ad47043544a97f308db3622f6f4b995770de778071ccd8c8 - 23861.doc
- 550f4164d9b78f0ce964434179071dd49b27ad8e4763c2c52289afce20370171 - 26211.doc
CERBER RANSOMWARE SAMPLES RETRIEVED FROM THE WORD MACROS:
- f1d97e4d3c105851cf2a4d98ef6f0f075f9645e112ddd2665a81498bdaa005a8 - 2017-01-07 Cerber ransomware example 1 of 3
- 04c2cdb0ec22f94caa7fd1f951e572e1e4138638737df495aa82302d109e6002 - 2017-01-07 Cerber ransomware example 2 of 3
- 7a55b387489053938cb9ee1b1d735751501a092e36c249d411496f9217b4cfec - 2017-01-07 Cerber ransomware example 3 of 3
- a5822e6798d322670d7295d812b393d3d791935293e2dd64b78c72ca33dce822 - 2017-01-08 Cerber ransomware example
- 927458c5a75272a94a3660d0d1eacf9a11106bf1cd607e07dbd5785ec3d8757e - 2017-01-09 Cerber ransomware example 1 of 5
- ca77acd34581015164a25d59d3a6219668e3631b0214afb81fbad980dd5ec834 - 2017-01-09 Cerber ransomware example 2 of 5
- 767ba30905b5f9cec9134871a50ab2e856124b2b1d9aa8beefaed4af3b57d226 - 2017-01-09 Cerber ransomware example 3 of 5
- 57234802cd13f297024cf2f7a62aa37b959e343ebbff6310d0481b42c409e8cb - 2017-01-09 Cerber ransomware example 4 of 5
- 8ecf2e9381cea169c16bb68a5e0532ba04f3e6de0d6b6a1d4aab92c445d308c5 - 2017-01-09 Cerber ransomware example 5 of 5
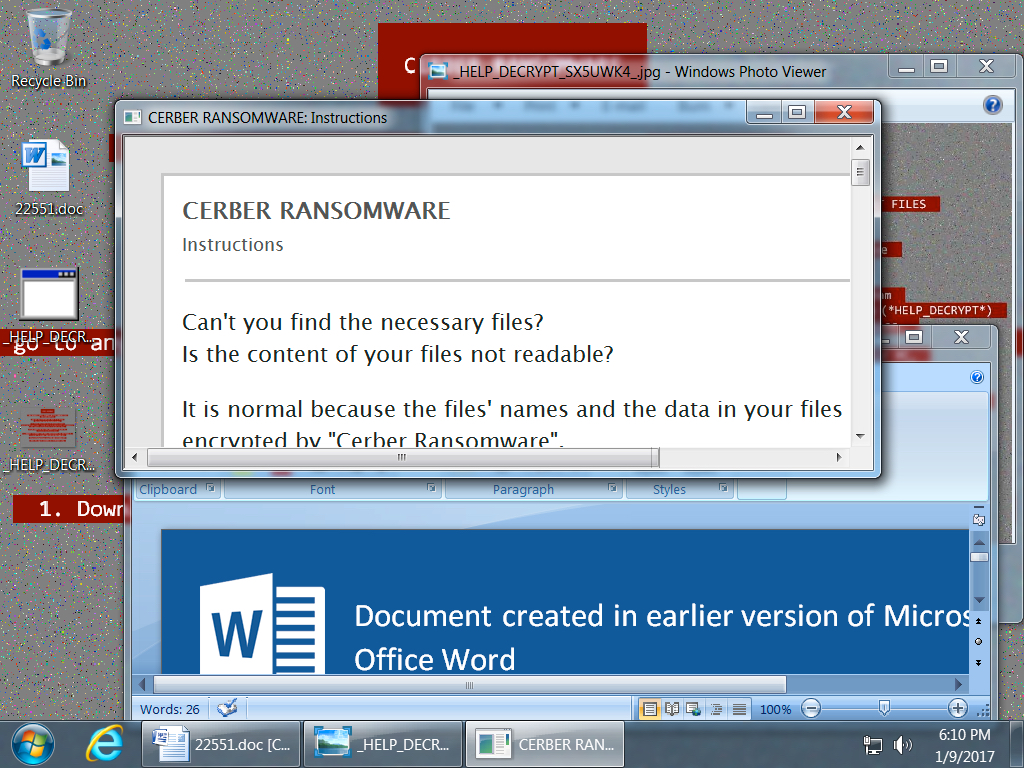
Shown above: Desktop of an infected Windows host.
Click here to return to the main page.
