2017-01-09 - ZEUS PANDA BANKER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-09-Zeus-Panda-Banker-infection-traffic.pcap.zip 138.4 kB (138,390 bytes)
- 2017-01-09-Zeus-Panda-Banker-infection-traffic.pcap (163,756 bytes)
- 2017-01-09-Zeus-Panda-Banker-email-and-malware.zip 440.1 kB (440,080 bytes)
- 2017-01-09-DHL-malspam-1337-UTC.eml (196,707 bytes)
- CVS Commercial form 20170109.cvs.exe (240,170 bytes)
- CVS Commercial form 20170109.zip (144,449 bytes)
THE EMAIL
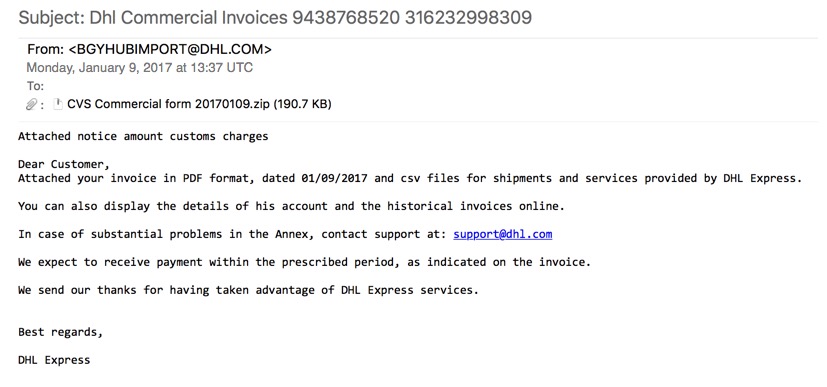
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Received from: public-gprs394884.centertel[.]pl (37.47.173[.]197)
- Date/Time: 2017-01-09 13:37 UTC
- Subject: Dhl Commercial Invoices 9438768520 316232998309
- From: <BGYHUBIMPORT@DHL[.]COM>
- Attachment name: CVS Commercial form 20170109.zip
MESSAGE TEXT:
Attached notice amount customs charges
Dear Customer,
Attached your invoice in PDF format, dated 01/09/2017 and csv files for shipments and services provided by DHL Express.
You can also display the details of his account and the historical invoices online.
In case of substantial problems in the Annex, contact support at: support@dhl.com
We expect to receive payment within the prescribed period, as indicated on the invoice.
We send our thanks for having taken advantage of DHL Express services.
Best regards,
DHL Express
TRAFFIC
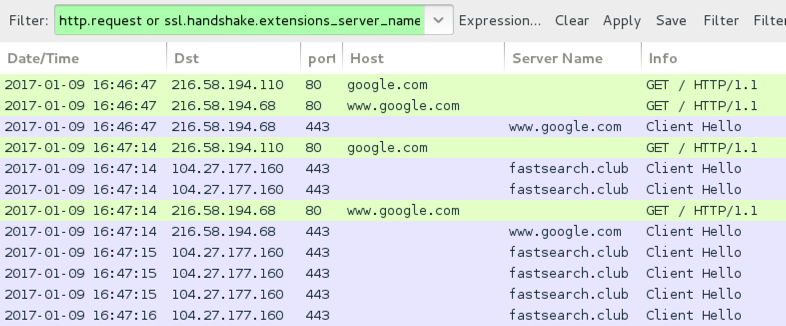
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- google[.]com - GET / check for connectivity (or possibly location)
- 104.27.177[.]160 port 443 - fastsearch[.]club - HTTPS/SSL/TLS Zeus Panda Banker C2 traffic
FILE HASHES
ATTACHED ZIP ARCHIVE:
- SHA256 hash: 63ecfe3dd8bf5040b1a8bd034d5e4ec861ba8870e98c3aa3de2057d8d21ba440 (144,449 bytes)
File name: CVS Commercial form 20170109.zip
EXTRACTED MALWARE:
- SHA256 hash: ef6c9eb9475c3e392db7fe9872d6ab2d5d8642d5764ce2b3360e609ede8e9459 (240,170 bytes)
File name: CVS Commercial form 20170109.cvs[.]exe
IMAGES
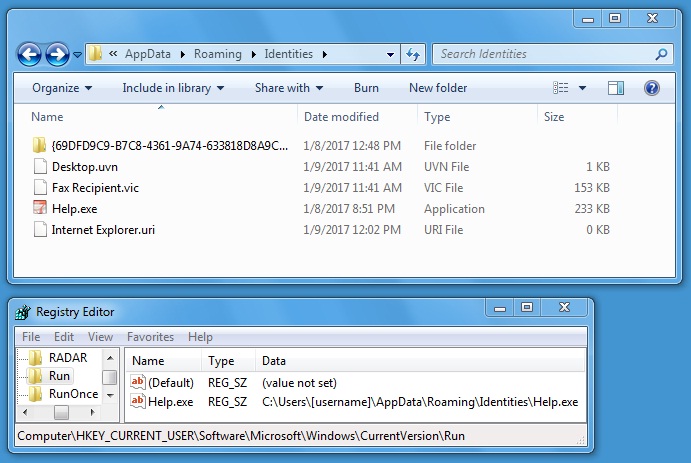
Shown above: Artifacts and registry update for this malware infection on a physical host.
FINAL NOTES
Click here to return to the main page.
