2017-01-11 - RIG-V FROM 109.234.38[.]150
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-11-Rig-V-activity-5-pcaps.zip 1.7 MB (1,696,258 bytes)
- 2017-01-11-EITest-Rig-V-sends-CryptoMix-ransomware-1st-run.pcap (265,815 bytes)
- 2017-01-11-EITest-Rig-V-sends-CryptoMix-ransomware-2nd-run.pcap (318,367 bytes)
- 2017-01-11-pseudoDarkleech-Rig-V-sends-Cerber-ransomware-1st-run.pcap (513,487 bytes)
- 2017-01-11-pseudoDarkleech-Rig-V-sends-Cerber-ransomware-2nd-run.pcap (415,050 bytes)
- 2017-01-11-pseudoDarkleech-Rig-V-sends-Cerber-ransomware-3rd-run.pcap (689,751 bytes)
- 2017-01-11-Rig-V-artifacts-and-associated-malware.zip 1.3 MB (1,265,898 bytes)
- 2017-01-11-Cerber-ransomware_HELP_DECRYPT_P0M4FLVC_.hta (67,682 bytes)
- 2017-01-11-Cerber-ransomware_HELP_DECRYPT_P0M4FLVC_.jpg (237,109 bytes)
- 2017-01-11-CryptoMix-ransomwawre-decryption-instructions.txt (1,480 bytes)
- 2017-01-11-EITest-Rig-V-1st-run-payload-CryptoMix-ransomware-rad9F7AB.tmp.exe (99,328 bytes)
- 2017-01-11-EITest-Rig-V-2nd-run-payload-CryptoMix-ransomware-radEC302.tmp.exe (98,816 bytes)
- 2017-01-11-Rig-V-artifact-QTTYUADAF.txt (1,137 bytes)
- 2017-01-11-Rig-V-flash-exploit.swf (16,946 bytes)
- 2017-01-11-Rig-V-landing-page-pseudoDarkleech-1st-run.txt (5,184 bytes)
- 2017-01-11-Rig-V-landing-page-pseudoDarkleech-2nd-run.txt (5,187 bytes)
- 2017-01-11-Rig-V-run-landing-page-EITest-1st-run.txt (5,187 bytes)
- 2017-01-11-Rig-V-run-landing-page-EITest-2nd-run.txt (5,189 bytes)
- 2017-01-11-Rig-V-run-landing-page-EITest-3rd-run.txt (5,192 bytes)
- 2017-01-11-page-from-activaclinics_com-with-injected-EITest-script.txt (59,303 bytes)
- 2017-01-11-page-from-alleghenyhomehealth_com-with-injected-pseudoDarkleech-script.txt (23,818 bytes)
- 2017-01-11-page-from-gardencityhall_com-with-injected-pseudoDarkleech-script.txt (27,801 bytes)
- 2017-01-11-page-from-grillo-designs_com-with-injected-EITest-script.txt (97,506 bytes)
- 2017-01-11-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (66,791 bytes)
- 2017-01-11-pseudoDarkleech-Rig-V-1st-run-payload-Cerber-ransomware-radE9100.tmp.exe (325,350 bytes)
- 2017-01-11-pseudoDarkleech-Rig-V-2nd-run-payload-Cerber-ransomware-rad21C56.tmp.exe (310,858 bytes)
- 2017-01-11-pseudoDarkleech-Rig-V-3rd-run-payload-Cerber-ransomware-rad8077D.tmp.exe (300,772 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I usually run across 2 versions of Rig EK: Rig-V (Rig 4.0) and Rig-E (Empire Pack).
- Rig-V is what security researchers called Rig EK version 4 when it was only accessible by "VIP" customers, while the old version (Rig 3) was still in use (reference).
- I currently call it "Rig-V" out of habit.
- The proper name for Rig-E is "Empire Pack". Empire Pack a variant of Rig EK as described by Kafeine here.
- I haven't seen Empire Pack traffic in 2017 yet, but I often see it from the EITest campaign (when EITest is distributing something other than CryptoMix/CryptFile2 or Cerber).
Shown above: Login panels for each exploit kit. Images from malware.dontneedcoffee.com (link).
OTHER NOTES:
- My thanks to everyone who continues to inform me about compromised websites. Without your help, I wouldn't be able to generate most of this traffic.
- Rig EK continues to use .news as a top level domain (TLD). That's always pun-worthy.
Shown above: I will never get tired of ".news" puns.
TRAFFIC
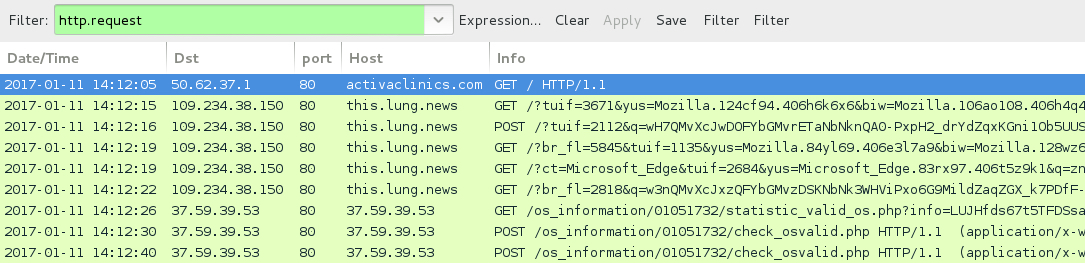
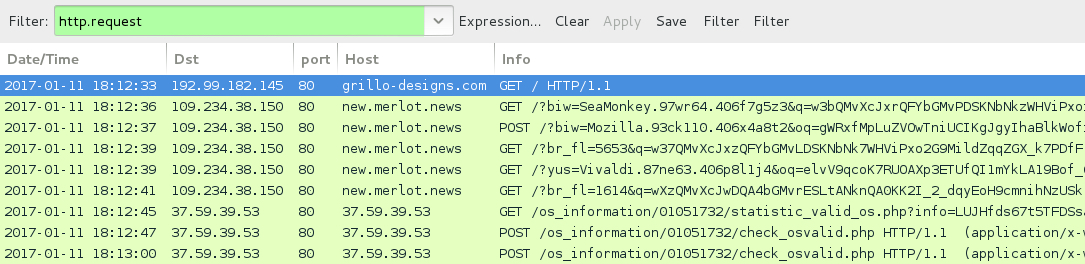
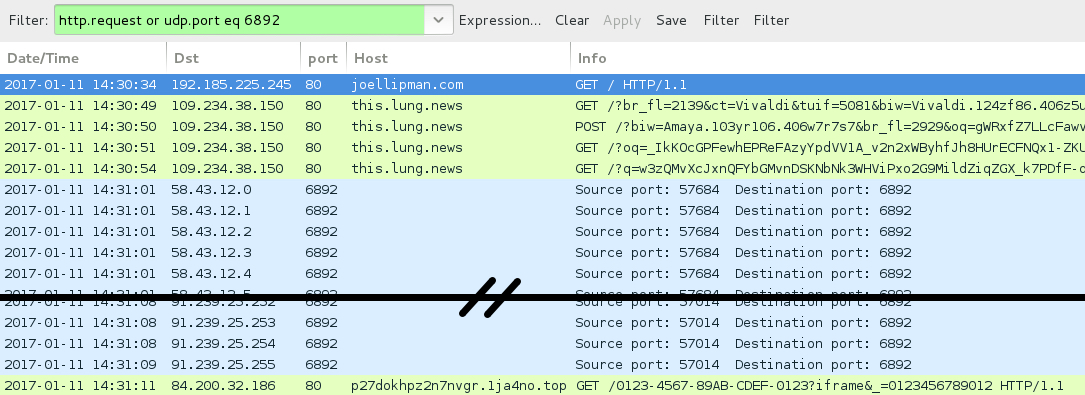
ASSOCIATED DOMAINS:
- activaclinics[.]com - Compromised site used for EITest campaign (1st run)
- grillo-designs[.]com - Compromised site used for EITest campaign (2nd run)
- joellipman[.]com - Compromised site used for pseudoDarkleech campaign (1st run)
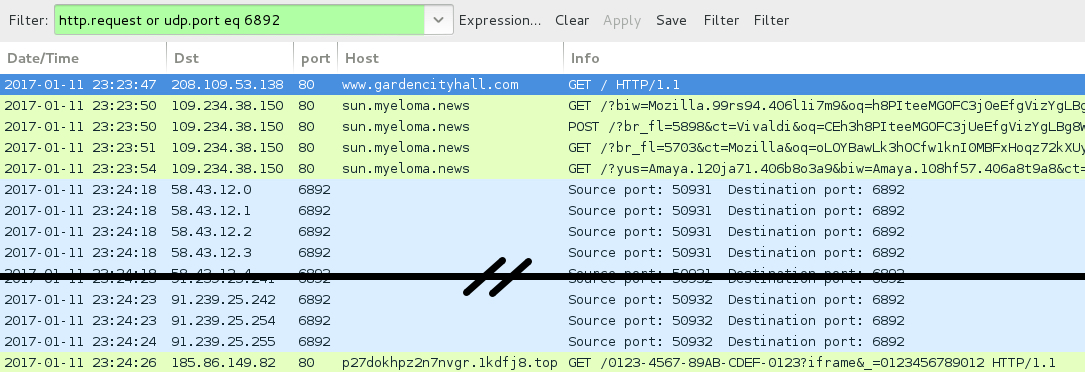
- www.gardencityhall[.]com - Compromised site used for pseudoDarkleech campaign (2nd run)
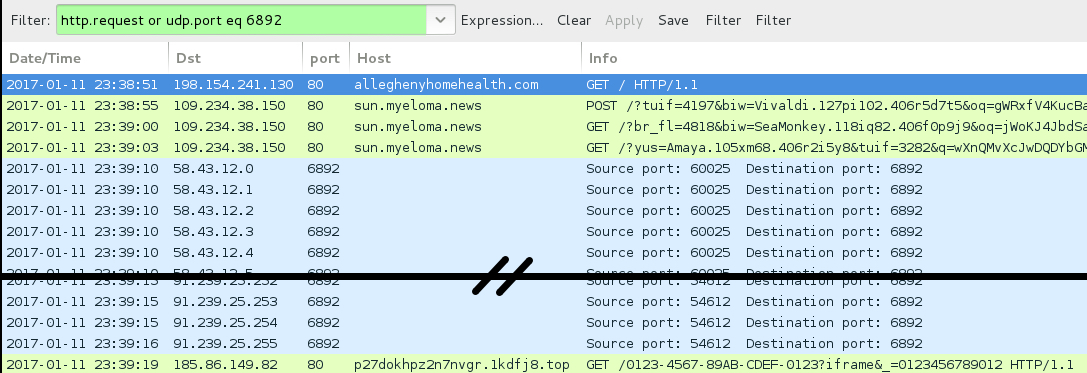
- alleghenyhomehealth[.]com - Compromised site used for pseudoDarkleech campaign (3rd run)
- 109.234.38[.]150 port 80 - this.lung[.]news Rig-V (EITest 1st run and psuedoDarkleech 1st run)
- 109.234.38[.]150 port 80 - new.merlot[.]news Rig-V (EITest 2nd run)
- 109.234.38[.]150 port 80 - sun.myeloma[.]news Rig-V (pseudoDarkleech 2nd and 3rd runs)
- 37.59.39[.]53 port 80 - 37.59.39[.]53 - CryptoMix (CryptFile2) ransomware callback traffic
- 58.43.12[.]0 to 58.43.12[.]31 (58.43.12[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.1.48[.]0 to 91.1.48[.]31 (91.1.48[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 84.200.32[.]186 port 80 - p27dokhpz2n7nvgr.1ja4no[.]top - Cerber ransomwarepost-infection HTTP traffic
- 185.86.149[.]82 port 80 - p27dokhpz2n7nvgr.1kdfj8[.]top - Cerber ransomwarepost-infection HTTP traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 HASH: 16c22d0e03433b80c00cebe4b2b37198eec7f005fd7fba3d4b2f9b822a47dc93 (16,946 bytes)
- File description: Rig-V Flash exploit seen on 2017-01-11
PAYLOADS:
- SHA256 HASH: e7a98896fa15d359c7fbd9254711f34210fe01286c4c2775086814ff0a4f2dfb (99,328 bytes)
- File description: EITest Rig-V payload - CryptoMix/CryptFile2 ransomware, .lesli variant (1st run)
- SHA256 HASH: 72bf7a5160606c1ae566fe45e96262f34af0b8204f8bdb79fede2b183c4c9e9f (99,328 bytes)
- File description: EITest Rig-V payload - CryptoMix/CryptFile2 ransomware, .lesli variant (2nd run)
- SHA256 HASH: 1d92a6c2b5c847353042dc2e57721fa7623b60b432d146e08b1f305ec320eb96 (325,350 bytes)
- File description: pseudoDarkleech Rig-V payload - Cerber ransomware (1st run)
- SHA256 HASH: 2e785f9b988b5f670706b29a2c7f3f081c9d0e0c2924fbf25fcd51fa8a75f10b (310,858 bytes)
- File description: pseudoDarkleech Rig-V payload - Cerber ransomware (2nd run)
- SHA256 HASH: 9a9f4e6c5e139d8362c57081f90cc4de5c7ba26392313ffc785f5fac4b9cb8f1 (300,772 bytes)
- File description: pseudoDarkleech Rig-V payload - Cerber ransomware (3rd run)
Click here to return to the main page.