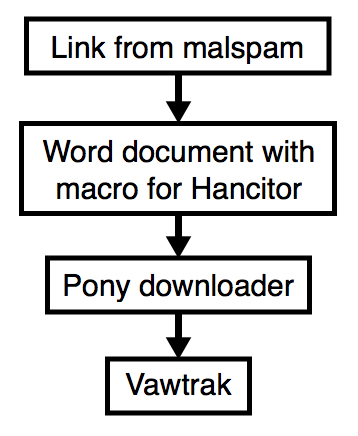
2017-01-12 - HANCITOR INFECTION WITH PONY AND VAWTRAK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-12-Hancitor-infection-with-Pony-and-Vawtrak.pcap.zip 1.1 MB (1,139,660 bytes)
- 2017-01-12-Hancitor-infection-with-Pony-and-Vawtrak.pcap (1,398,569 bytes)
- 2017-01-12-Hancitor-malspam-1652-UTC.eml.zip 0.9 kB (864 bytes)
- 2017-01-12-Hancitor-malspam-1652-UTC.eml (1,049 bytes)
- 2017-01-12-malware-from-Hancitor-infection.zip 440 kB (440,127 bytes)
- 2017-01-12-Hancitor-example.doc (190,464 bytes)
- 2017-01-12-Pony-example-pm1.dll (71,680 bytes)
- 2017-01-12-Vawtrak-example.exe (489,984 bytes)
NOTES:
- More malspam as described in an ISC diary I wrote covering Hancitor/Pony/Vawtrak activty from Tuesday 2017-01-10 (link).
- Today it's a fake iphone order.
Shown above: Flowchart for this infection traffic.
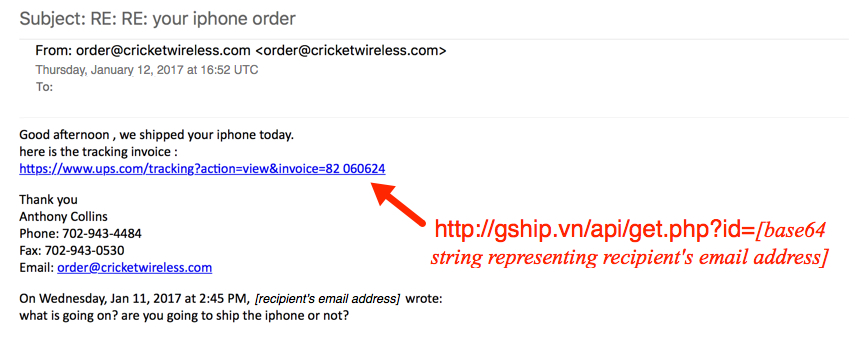
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Date: Thursday 2017-01-12 at 16:52 UTC
- From: order@cricketwireless[.]com <order@cricketwireless[.]com>
- Subject: RE: RE: your iphone order
- Message-ID: <7A60F44D.E796C0E6@cricketwireless[.]com>
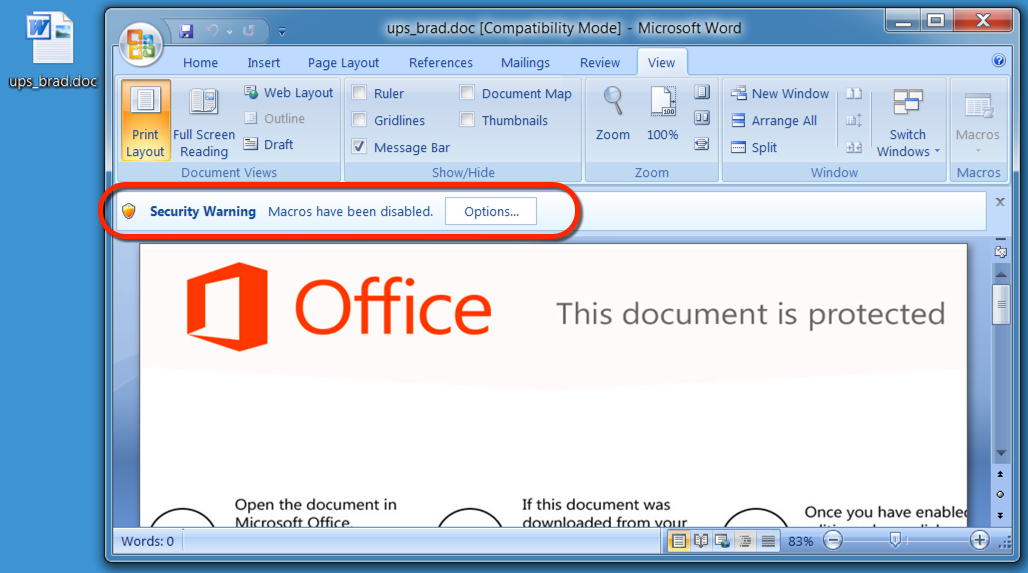
Shown above: Word document downloaded from link in the email.
TRAFFIC
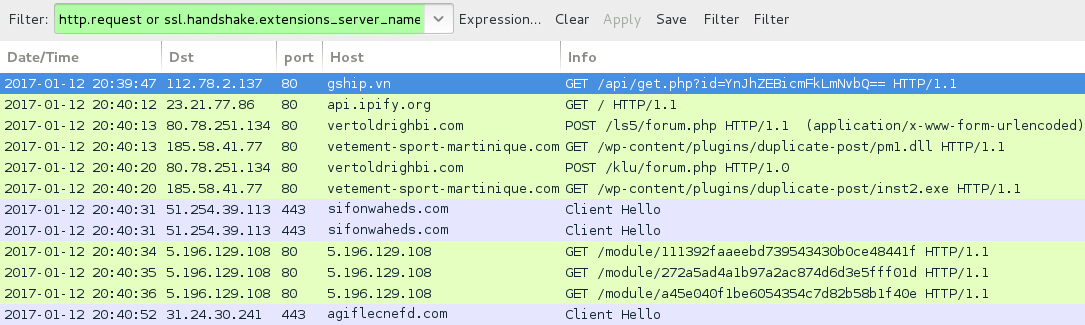
Shown above: Word document downloaded from link in the email.
ASSOCIATED DOMAINS:
- 112.78.2[.]137 port 80 - gship[.]vn - GET /api/get.php?id=[base64 characters representing recipient's email address]
- api.ipify[.]org - GET / [IP address check by the infected host]
- 80.78.251[.]134 port 80 - vertoldrighbi[.]com - POST /ls5/forum.php [Hancitor check-in]
- 185.58.41[.]77 port 80 - vetement-sport-martinique[.]com - GET /wp-content/plugins/duplicate-post/pm1.dll [Download Pony DLL]
- 80.78.251[.]134 port 80 - vertoldrighbi[.]com - POST /klu/forum.php [Hancitor check-in]
- 185.58.41[.]77 port 80 - vetement-sport-martinique[.]com - GET /wp-content/plugins/duplicate-post/inst2.exe [Vawtrak download]
- 51.254.39[.]113 port 443 - sifonwaheds[.]com - HTTPS/SSL/TLS traffic caused by Vawtrak
- 5.196.129[.]108 port 80 - 5.196.129[.]108 - GET /module/111392faaeebd739543430b0ce48441f [Vawtrak post-infection HTTP traffic]
- 5.196.129[.]108 port 80 - 5.196.129[.]108 - GET /module/272a5ad4a1b97a2ac874d6d3e5fff01d [Vawtrak post-infection HTTP traffic]
- 5.196.129[.]108 port 80 - 5.196.129[.]108 - GET /module/a45e040f1be6054354c7d82b58b1f40e [Vawtrak post-infection HTTP traffic]
- DNS query for efficiencyhg[.]ru - blank response from name server
- DNS query for monotonousfd[.]ru - blank response from name server
- 31.24.30[.]241 port 443 - agiflecnefd[.]com - HTTPS/SSL/TLS traffic caused by Vawtrak
FILE HASHES
WORD DOCUMENT:
- SHA256 hash: 74a649097b294bbf0ea63a521acdf37ee586ef42c56cb343680dc3b4c4fb074d (190,464 bytes)
File description: Hancitor maldoc (Word document) on 2017-01-12
PONY DLL:
- SHA256 hash: 4f64b253fa41acaedbf705a494de97cdcce293383e5cebef5a72dc264205f924 (71,680 bytes)
File description: Pony downloader (DLL file) on 2017-01-12
VAWTRAK MALWARE:
- SHA256 hash: 4c6a0d18ab824c3c497a2b3a76a2672d7f288414ae2e132b28840fb5b7e901fd (489,984 bytes)
File description: Vawtrak malware (EXE file) on 2017-01-12
Click here to return to the main page.