2017-01-13 - "BLANK SLATE" CAMPAIGN SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-13-Cerber-ransomware-infection-traffic.pcap.zip 856.3 kB (856,274 bytes)
- 2017-01-13-Cerber-ransomware-infection-traffic.pcap (1,040,210 bytes)
- 2017-01-13-Blank-Slate-emails-and-Cerber-ransomware.zip 1.9 MB (1,903,475 bytes)
- 2017-01-13-Blank-Slate-malspam-0007-UTC.eml (60,258 bytes)
- 2017-01-13-Blank-Slate-malspam-0837-UTC.eml (52,969 bytes)
- 2017-01-13-Blank-Slate-malspam-1049-UTC.eml (62,599 bytes)
- 2017-01-13-Blank-Slate-malspam-1428-UTC.eml (39,344 bytes)
- 2017-01-13-Blank-Slate-malspam-1607-UTC.eml (60,538 bytes)
- 2017-01-13-Blank-Slate-malspam-1715-UTC.eml (45,145 bytes)
- 2017-01-13-Blank-Slate-malspam-1854-UTC.eml (66,499 bytes)
- 2017-01-13-Blank-Slate-malspam-tracker.csv (1,543 bytes)
- 332101.zip (33,128 bytes)
- 62274826.zip (48,923 bytes)
- 793186269136.zip (44,507 bytes)
- 6225549306381.zip (28,811 bytes)
- 09488786419-[recipient].zip (38,860 bytes)
- INFO_60191_[recipient].zip (46,026 bytes)
- $MONEY-86635301206-[recipient].zip (44,293 bytes)
- 2589.doc (102,912 bytes)
- 5274.doc (79,360 bytes)
- 6254.doc (86,016 bytes)
- 10803.doc (116,224 bytes)
- 21457.doc (115,200 bytes)
- 23183.doc (123,392 bytes)
- 29546.doc (118,784 bytes)
- 2017-01-13-Cerber-ransomware-1st-example.exe (275,484 bytes)
- 2017-01-13-Cerber-ransomware-2nd-example.exe (275,484 bytes)
- 2017-01-13-Cerber-ransomware-3rd-example.exe (271,954 bytes)
- 2017-01-13-Cerber-ransomware-4th-example.exe (275,484 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- The Cerber ransomware is downloaded from IP addresses belonging to Amazon Web Services (AWS).
- Several of these Word documents had an error in the macro that prevented them from working.
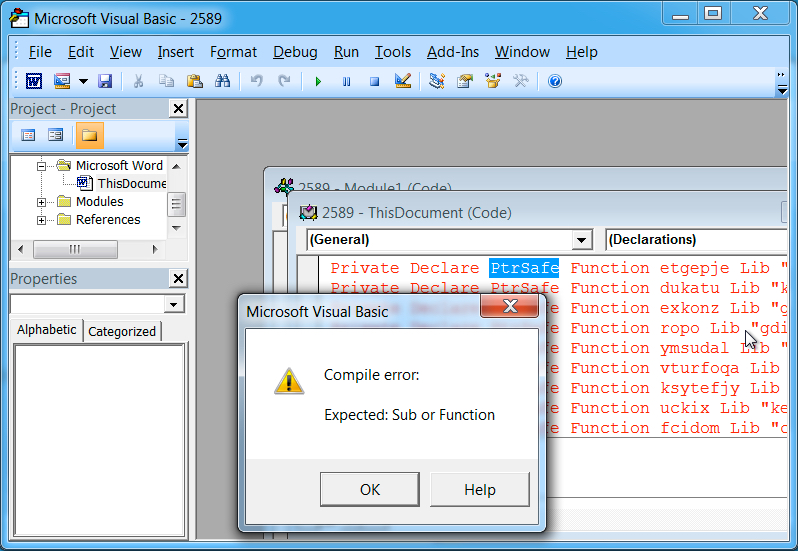
Shown above: Error seen when enabling macros on some of these Word documents.
EMAILS
Read: date/time -- received from mailserver at -- sender (spoofed) -- subject -- zip attachment name -- extracted doc
- 2017-01-13 00:07 UTC -- 186.117.249[.]226 -- <atie121609@gmail[.]com> -- (none) -- $MONEY-86635301206-[recipient].zip -- 21457.doc
- 2017-01-13 08:37 UTC -- 111.194.131[.]109 -- <[recipient's name]@pearlresearch[.]com> -- 35571 [recipient's name from email address] -- 09488786419-[recipient].zip -- 2589.doc
- 2017-01-13 10:49 UTC -- telebucaramanga[.]net[.]co -- <carol@mirror[.]co[.]uk> -- (none) -- INFO_60191_[recipient's name from email address].zip -- 29546.doc
- 2017-01-13 14:28 UTC -- 117.255.233[.]191 -- <mathias.heinrich@web[.]de> -- (none) -- 6225549306381.zip -- 5274.doc
- 2017-01-13 16:07 UTC -- 94.51.8[.]224 -- <marycris-paccia@libero[.]it> -- (none) -- 793186269136.zip -- 10803.doc
- 2017-01-13 17:15 UTC -- rdtc[.]ru -- <eforney@elon[.]edu> -- (none) -- 332101.zip -- 6254.doc
- 2017-01-13 18:54 UTC -- hinet[.]net -- <andreas.nilsson@norstat[.]se> -- (none) -- 62274826.zip -- 23183.doc
TRAFFIC
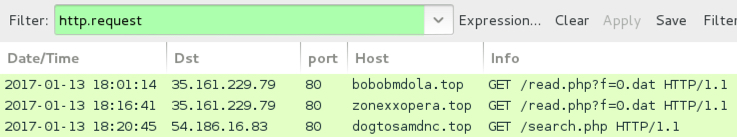
Shown above: URLs for all the Word documents filtered in Wireshark.
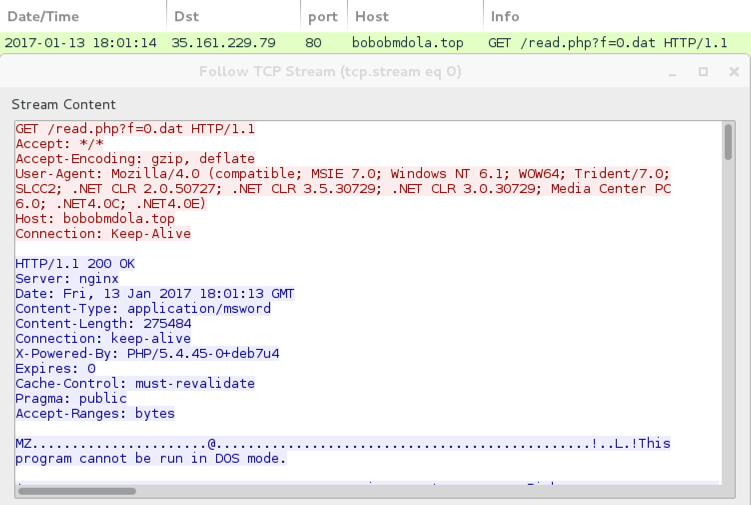
Shown above: One of the URLs hosted on AWS that served Cerber ransomware (1 of 3).
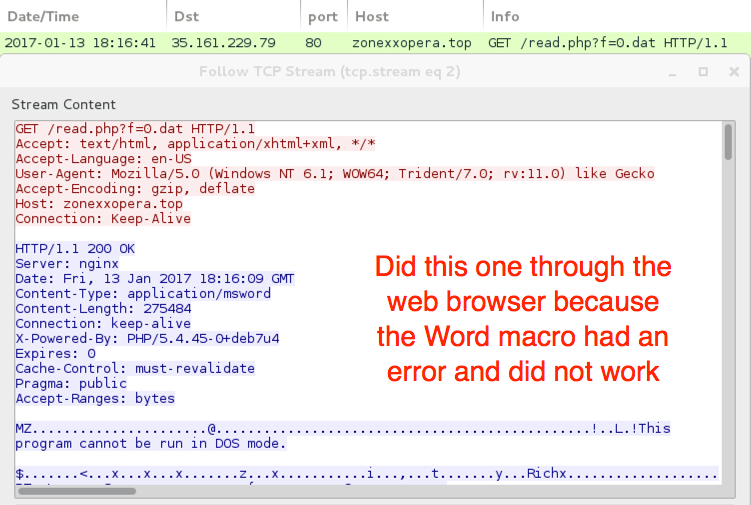
Shown above: One of the URLs hosted on AWS that served Cerber ransomware (2 of 3).
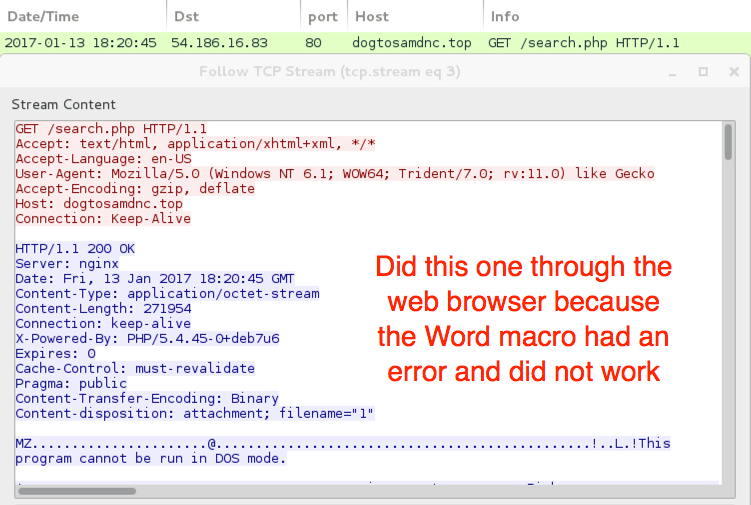
Shown above: One of the URLs hosted on AWS that served Cerber ransomware (3 of 3).
ASSOCIATED DOMAINS:
- 35.161.229[.]79 port 80 - bobobmdola[.]top - GET /read.php?f=0.dat [Cerber ransomware download from the Word macro]
- 35.161.229[.]79 port 80 - zonexxopera[.]top - GET /read.php?f=0.dat [Cerber ransomware download from the Word macro]
- 54.186.16[.]83 port 80 - dogtosamdnc[.]top - GET /search.php [Cerber ransomware download from the Word macro]
- 97.15.12[.]0 to 97.15.12[.]31 (97.15.12[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 97.2.48[.]0 to 97.2.48[.]31 (97.2.48[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 173.254.204[.]104 port 80 - p27dokhpz2n7nvgr.15rnwa[.]top - Cerber ransomware post-infection HTTP traffic
FILE HASHES
ATTACHED ZIP ARCHIVES:
- e788983d8f103c103bd581dbd6c6891328d70772f252e61c98c367cdcb4b5659 - 332101.zip
- e177b2a050c3a52247c87e9cce1d4fb3b02efc0a6a0c4d51bb818289a4fb8649 - 62274826.zip
- 0ea9690b79dd5c6ebe83b9539c619ce2057bf3715ff62e5e84599513a0970d78 - 793186269136.zip
- 8b9295f0960bd1d05c4da8330cba0cb9e73700a587a7aba91c1faf3c0bfbdb74 - 6225549306381.zip
- 1e5d324318dd3c9afca69db65871721b9350caed4f12102af259feffecebd193 - 09488786419-[recipient].zip
- a8c5459e332d2d61913b5d6498600e91a08c49692335ea4b716b3a726d192f53 - INFO_60191_[recipient].zip
- dce63003d79768b117b197b318f7650a744c1d94ce765795373c5e8a5889ec82 - $MONEY-86635301206-[recipient].zip
EXTRACTED MICROSOFT WORD DOCUMENTS:
- 7b3eed96748e306eb81ae4775965aec6aaf0b85bc220af5d47e2b117a3072fa7 - 2589.doc
- 2ec865098724f3a662dbf72b1723b3e0f4d26309723e3278614641a0dc248daa - 5274.doc
- c287e5df8f25d10d7f1e5f621877ced9e78771f6a6032d5672d61d3dfde3e0ed - 6254.doc
- 13f3a9a8fe4782b5d0b606893fce3c44b20e0e30d802783ff2b40a3b9f3782bf - 10803.doc
- e129eb25c397963f4d1eb2f4b1060d40554d54572431f14b28f6f3c57941a6a0 - 21457.doc
- da55f6b61d5740e91ba677e0afc075a671b9dc63f6bf6209bf2025c4725b75c0 - 23183.doc
- 0dd91d57db4753d0813f1587a0b41881a2175571dbc3e67d10ac6581b80441e5 - 29546.doc
DOWNLOADED CERBER RANSOMWARE SAMPLES:
- 8e1e7ea8aa4cc443f5b5231ecb2fd45acca4570c73d8963b8817ea692d951639 - Cerber ransomware 1st example/li>
- 81dcfc070e35ce217ba829cd400598da209e0953df0bc365c06ab21bceee98e0 - Cerber ransomware 2nd example/li>
- 8d5ecc4948096e3ff5570608f8b539c3f8249671f86a63b52791a5f83c71eeeb - Cerber ransomware 3rd example/li>
- 09e632cde8db7e70a37965b5faea2644d0a13b97a9526c12ae51a3cae11f2642 - Cerber ransomware 4th example/li>
Click here to return to the main page.
