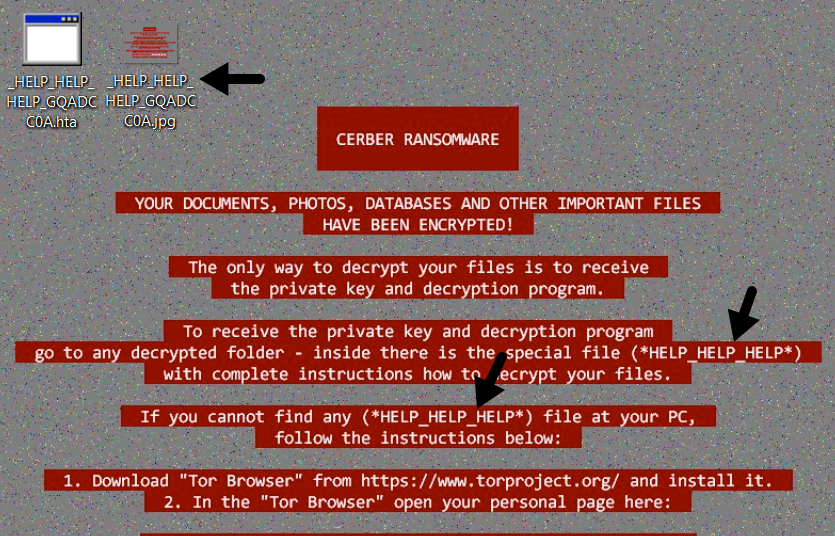
2017-01-17 - "BLANK SLATE" CAMPAIGN SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-17-Cerber-ransomware-infection-traffic.pcap.zip 242.6 kB (242,644 bytes)
- 2017-01-17-Blank-Slate-malspam-tracker.csv.zip 2.1 kB (2,111 bytes)
- 2017-01-17-Blank-Slate-emails-and-Cerber-ransomware.zip 6.2 MB (6,192,387 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- See below for information on where the Cerber ransomware binaries are hosted.
- Most all of these Word documents had an error in the macro that prevented them from working.
- File names for the Cerber decryption instructions today started with _HELP_HELP_HELP.
Shown above: New HELP_HELP_HELP message I haven't noticed before.
EMAILS
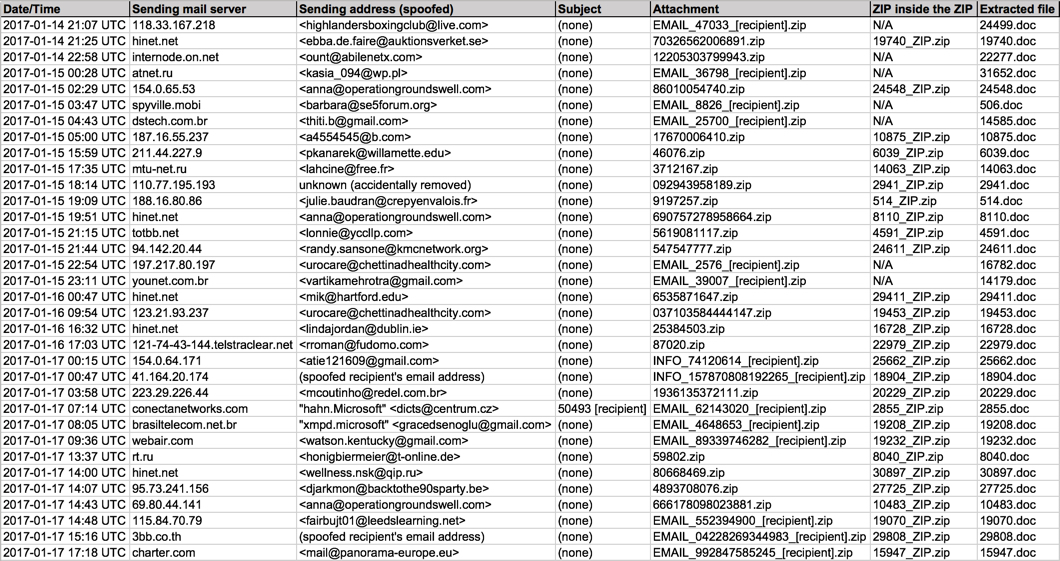
Shown above: Information from the spreadsheet tracker (part 1 of 2).
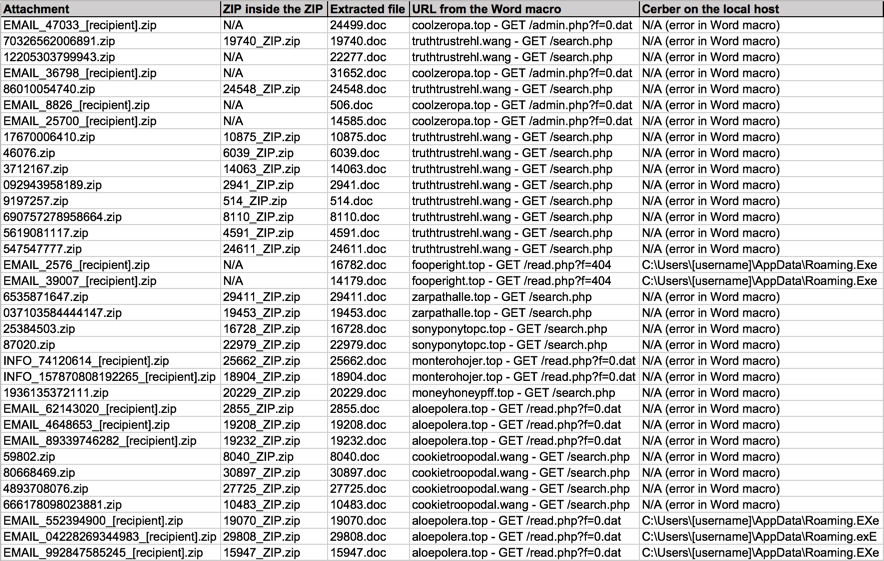
Shown above: Information from the spreadsheet tracker (part 2 of 2).
SOME OF THE EMAILS NOTED:
(Read: Date/Time -- Sending mail server -- Sending address (spoofed) -- Subject -- Attachment)
- 2017-01-14 21:07 UTC -- 118.33.167[.]218 -- highlandersboxingclub@live[.]com -- (none) -- EMAIL_47033_[recipient].zip
- 2017-01-14 21:25 UTC -- hinet[.]net -- ebba.de.faire@auktionsverket[.]se -- (none) -- 70326562006891.zip
- 2017-01-14 22:58 UTC -- internode.on[.]net -- ount@abilenetx[.]com -- (none) -- 12205303799943.zip
- 2017-01-15 00:28 UTC -- atnet[.]ru -- kasia_094@wp[.]pl -- (none) -- EMAIL_36798_[recipient].zip
- 2017-01-15 02:29 UTC -- 154.0.65[.]53 -- anna@operationgroundswell[.]com -- (none) -- 86010054740.zip
- 2017-01-15 03:47 UTC -- spyville[.]mobi -- barbara@se5forum[.]org -- (none) -- EMAIL_8826_[recipient].zip
- 2017-01-15 04:43 UTC -- dstech[.]com[.]br -- thiti.b@gmail[.]com -- (none) -- EMAIL_25700_[recipient].zip
- 2017-01-15 05:00 UTC -- 187.16.55.237 -- a4554545@b[.]com -- (none) -- 17670006410.zip
- 2017-01-15 15:59 UTC -- 211.44.227[.]9 -- pkanarek@willamette[.]edu -- (none) -- 46076.zip
- 2017-01-15 17:35 UTC -- mtu-net[.]ru -- lahcine@free[.]fr -- (none) -- 3712167.zip
- 2017-01-15 18:14 UTC -- 110.77.195[.]193 -- unknown (accidentally removed) -- (none) -- 092943958189.zip
- 2017-01-15 19:09 UTC -- 188.16.80[.]86 -- julie.baudran@crepyenvalois[.]fr -- (none) -- 9197257.zip
- 2017-01-15 19:51 UTC -- hinet[.]net -- anna@operationgroundswell[.]com -- (none) -- 690757278958664.zip
- 2017-01-15 21:15 UTC -- totbb[.]net -- lonnie@yccllp[.]com -- (none) -- 5619081117.zip
- 2017-01-15 21:44 UTC -- 94.142.20[.]44 -- randy.sansone@kmcnetwork[.]org -- (none) -- 547547777.zip
- 2017-01-15 22:54 UTC -- 197.217.80[.]197 -- urocare@chettinadhealthcity[.]com -- (none) -- EMAIL_2576_[recipient].zip
- 2017-01-15 23:11 UTC -- younet[.]com[.]br -- vartikamehrotra@gmail[.]com -- (none) -- EMAIL_39007_[recipient].zip
- 2017-01-16 00:47 UTC -- hinet[.]net -- mik@hartford[.]edu -- (none) -- 6535871647.zip
- 2017-01-16 09:54 UTC -- 123.21.93[.]237 -- urocare@chettinadhealthcity[.]com -- (none) -- 037103584444147.zip
- 2017-01-16 16:32 UTC -- hinet[.]net -- lindajordan@dublin[.]ie -- (none) -- 25384503.zip
- 2017-01-16 17:03 UTC -- 121-74-43-144.telstraclear[.]net -- rroman@fudomo[.]com -- (none) -- 87020.zip
- 2017-01-17 00:15 UTC -- 154.0.64[.]171 -- atie121609@gmail[.]com -- (none) -- INFO_74120614_[recipient].zip
- 2017-01-17 00:47 UTC -- 41.164.20[.]174 -- (spoofed recipient's email address) -- (none) -- INFO_157870808192265_[recipient].zip
- 2017-01-17 03:58 UTC -- 223.29.226[.]44 -- mcoutinho@redel[.]com[.]br -- (none) -- 1936135372111.zip
- 2017-01-17 07:14 UTC -- conectanetworks[.]com -- "hahn.Microsoft" <dicts@centrum[.]cz> -- 50493 [recipient] -- EMAIL_62143020_[recipient].zip
- 2017-01-17 08:05 UTC -- brasiltelecom[.]net[.]br -- "xmpd.microsoft" <gracedsenoglu@gmail[.]com> -- (none) -- EMAIL_4648653_[recipient].zip
- 2017-01-17 09:36 UTC -- webair[.]com -- watson.kentucky@gmail[.]com -- (none) -- EMAIL_89339746282_[recipient].zip
- 2017-01-17 13:37 UTC -- rt[.]ru -- honigbiermeier@t-online[.]de -- (none) -- 59802.zip
- 2017-01-17 14:00 UTC -- hinet[.]net -- wellness.nsk@qip[.]ru -- (none) -- 80668469.zip
- 2017-01-17 14:07 UTC -- 95.73.241[.]156 -- djarkmon@backtothe90sparty[.]be -- (none) -- 4893708076.zip
- 2017-01-17 14:43 UTC -- 69.80.44[.]141 -- anna@operationgroundswell[.]com -- (none) -- 666178098023881.zip
- 2017-01-17 14:48 UTC -- 115.84.70[.]79 -- fairbujt01@leedslearning[.]net -- (none) -- EMAIL_552394900_[recipient].zip
- 2017-01-17 15:16 UTC -- 3bb[.]co[.]th -- (spoofed recipient's email address) -- (none) -- EMAIL_04228269344983_[recipient].zip
- 2017-01-17 17:18 UTC -- charter[.]com -- mail@panorama-europe[.]eu -- (none) -- EMAIL_992847585245_[recipient].zip
ATTACHED ZIP ARCHIVES AND EXTRACTED WORD DOCUMENTS
SHA256 HASHES FOR THE EMAIL ATTACHMENTS:
- db0ee4e8fe9e5d75c2e96b4eec3d5d89cedf52b185982e1a7012e0b629b20af5 - 46076.zip
- 106b9770ff449af2192c53e37c9c382a777bb764b180be8b47e1ccc6b58f3356 - 59802.zip
- da782d7ce307afd0754a04fcdbff40d94f43b905aafd0770b8dd6ef984ec3f41 - 87020.zip
- 613fa4a85404acd51fbeefd3000c34a972e0c6200b0f3355a38525994b4d3ba8 - 3712167.zip
- b6852e7841a12da6cdc9718d8c11f7cfa9ea5759a3f33eda637740091dde105b - 9197257.zip
- bfa56daad47eb48fc29940369fcdbccc14639dbfd85a06940530750d7eed8c52 - 25384503.zip
- a81b8c841032c209a9a941a0b57ae6ec13087d69814acf238a943e5edda81af4 - 80668469.zip
- aea4590f6fa3899ad3845751fbeba279cfc5c1f6f912ac5a7f694974db962559 - 547547777.zip
- 27b636bb29857932520af93e6994497929c4811f1e52e92b8e453d9d8fad89d1 - 4893708076.zip
- 7f2601bd79b5bb3f357843275a54524a56627028b6562352a6dbcf6258c5df56 - 5619081117.zip
- 0d2c78f06e05f364d5e526c3e026ec5e4684a217a35e98de8841c92698b29e53 - 6535871647.zip
- b764e66de61fc73b03bfe67e33ef7b6519d99a116377d35a4bb932a66fb7d154 - 17670006410.zip
- 4b00174253029fce84af7a0f593bbd49ffca3b77a58c267e1302758fdd812d8f - 86010054740.zip
- 05d4e2ddb1d4c4d3bc192033600872378f4d323c930f36cb3b216903e3b61574 - 092943958189.zip
- b1d0b2db814dac737a153af33d7602a37be586325670325938fd33800c544a08 - 1936135372111.zip
- 80d39c46f72f1db679e0677bccb2ff00b5f989d4d226a9667dc1f3d2b098ec4f - 70326562006891.zip
- 5647a6f812091bf7804aa98c704e28e68d8f0f4f4fb13ee212ac41ed963c42bd - 12205303799943.zip
- 815859a4e3ebc478e8b5206c6bec94a67aef438a5eb9e266a41ece5aad4069a2 - 037103584444147.zip
- 70541937c65578e479c01d65957dac75e5dc97e1b4c84b840388a7e3c2f32ce7 - 666178098023881.zip
- 71662ac164614ca2e3817da8567ea1e493cbcdc04f823ff26e70afe8db12807b - 690757278958664.zip
- 97b585abda6f1fcfb465ba0bc441f34819822396321de563be15ee09cec75716 - EMAIL_2576_[recipient].zip
- f398643bccca15eb2d06ba8f52cad24117b95cc3c8e4be55b1ce6ab131c14999 - EMAIL_8826_[recipient].zip
- af595a9548a5185fcda6559fcde6cecd32581141ef8a63c4d1d9db11e770feff - EMAIL_25700_[recipient].zip
- 507dbad7530fa407537e029a973bcc45cdd22d904f8f6596ebae5d1ef1fd85dc - EMAIL_36798_[recipient].zip
- fcd50f2ba267e52f2a8e6c749b5005c8e58a211f4e54d8b6b3c0a68da3432775 - EMAIL_39007_[recipient].zip
- a2e7f449af4166f936b9c8533bd734f40cc016e087710f2dbbc39b5fd508ce2a - EMAIL_47033_[recipient].zip
- dbc0bdfd5439766e5a59e44afa5d6d5a2f163f3027780e9a22f5d083347f34f1 - EMAIL_4648653_[recipient].zip
- 4ea1662090e0bc8b6d54af3ae2842152a52b38a662c9b48b2801f9d3b6ba50c4 - EMAIL_62143020_[recipient].zip
- a45c70fdbdf979cef0850ff3e449d8662a200942abee46d322347df3ecb1c795 - EMAIL_552394900_[recipient].zip
- cd31e62ba35d40d90fcbe14ff2e29d50477df3f66b40017660ca522af96adb15 - EMAIL_89339746282_[recipient].zip
- 188d78d64c7a6a50905b65b874c48346afa3beec9a8a78245328ba7e77266228 - EMAIL_992847585245_[recipient].zip
- 4dc557815f632b14154a73935d742dff0ccf5359ea5ce96a8e16bc0f81ab6424 - EMAIL_04228269344983_[recipient].zip
- 4e9aba9e193e018d8c436a4533bf68629a0b571d3ef1950c039a72b7d5be86cc - INFO_74120614_[recipient].zip
- e5bf88d0a7cffdfd6a49c0b0d8ee73cbc4fd327a0be84f8e8f64d7e60f905dc9 - INFO_157870808192265_[recipient].zip
SHA256 HASHES FOR THE EXTRACTED WORD DOCUMENTS:
- de18e364c6f6f022a9b1d136eae86b274a91165d32273817050fcc8f19abfdba - 506.doc
- 203762e3d524e5ec7dd9b0ed7a06d5c54701087082e1a9d63a52bdff099bc445 - 514.doc
- 5040124544561dd61910438c17142c72f155f31a8b54ad8aba100179f4abc987 - 2855.doc
- 3da97dda684a78557a8639a3b3a46f703398b8aec7187382672dcd79f942da35 - 2941.doc
- c349866761e39d630aa26be2adf8bd9cc03257100008b9e3bfbc0429cf9f5a2f - 4591.doc
- 651263d15e15c884c8cd73373212d5d3bf538002b45a586226680b9c61317bf0 - 6039.doc
- 9124179c56e7b046b769666cace9949b67360af2b769fd730a41b6825559ff54 - 8040.doc
- 694010c2f5ae84a205c75ff926124e119ff92ddb8f54229a1c13a2126819e6d9 - 8110.doc
- 4f7b577f29b064792542aad6a40efc67dea15c98bdbb9c22bfd691356fe5ea0d - 29411.doc
- aadaa3fd3d8023f356db054d1d2b7998225769e2f4a493b7bee858b4d69a90bf - 29808.doc
- c8c633f6db0475234b86e994b8182ee13c7355e247b7cd8d352a548705185305 - 30897.doc
- e3e90c2ed75a3ae6b9ac64860402c67f4a0e992a0ddf35ba840c69f64443ce25 - 31652.doc
- 9124179c56e7b046b769666cace9949b67360af2b769fd730a41b6825559ff54 - 10483.doc
- 25873970bda2ea3964b34c5825dcb0dfa280452bc09d04a31a36bf843fc490c9 - 10875.doc
- af8b4ef565cba207c0eaf8541b3e9d88a9d1315ed87f492430c8f55e5028913c - 14063.doc
- d3a06bd901b6327e16fdb8c834c9af8e9e3bd14afcb3bbaaba00cc4fa39644a4 - 14179.doc
- b72bcded92eb190ef01d875c3cd00b4654598aa29644294670476c213a0dd6e2 - 14585.doc
- 4b8ccd76dd5bd6747a68394ec1259d0756b5b930af0f119f3e827ad2a7485fa1 - 15947.doc
- 2f54b6625745549b17749c550f04bd5e118d618cebe7bfc1fef52145f3acd7c7 - 16728.doc
- a4688cecc7ae6eb5005c905b56251e91ee81c458d23531d76a9fb535fc86add7 - 16782.doc
- b5d0b301ef3d21a468efbc7ca1c7bfa5f927c1195b8314c158e4fa9d862fcf11 - 18904.doc
- a854b0d09c7ca95d687a7875deee5d4ebd45f074998fce2d90b38aee251c134f - 19070.doc
- b06607449829a1c35084231e13442f7f43ec4fbe72f7975dec31c270d17caa67 - 19208.doc
- 5343cce259a3717b3aecda6b26ba9207a64e4f75f464e762551c23a6e3cf796f - 19232.doc
- 71e96fa9843e8a882a131bbe7ad01e0e44921e98cdc7136ccd995aaa8f176257 - 19453.doc
- 835c10545f572dcba44739cbda2dad6fe01cc9f98a2a75bbdfd3052d66dde7f3 - 19740.doc
- cd2b9e4f39d994d517eac99c9ee6f9ac04c5422b482041e5348eb3b799914466 - 20229.doc
- dbe0ea8ce224c55d0dc9f72dc54484d0ea0979f9e4b39a5eb814a6cea49e3057 - 22277.doc
- f46e53a892b14ec67525aa9919c40ef24f8573eeb0dbf1ca785030b16e16d89d - 22979.doc
- 3733874d52f74b6569efc31135490225159cc7e7d8c39c18ff97d5ceb39bbdd9 - 24499.doc
- b9005e1448c1558cbf208b24461886a3b64fdbe9a51b359a1990a198917a4594 - 24548.doc
- 795eeede35b8ecda1a537b6d8cba92d1eebfc6af72802846011828519318a30e - 24611.doc
- a0591c305a95b34c72bf986dd6644fa536ae5d0e229730e81cdb76cc2d1c422b - 25662.doc
- 9124179c56e7b046b769666cace9949b67360af2b769fd730a41b6825559ff54 - 27725.doc
TRAFFIC
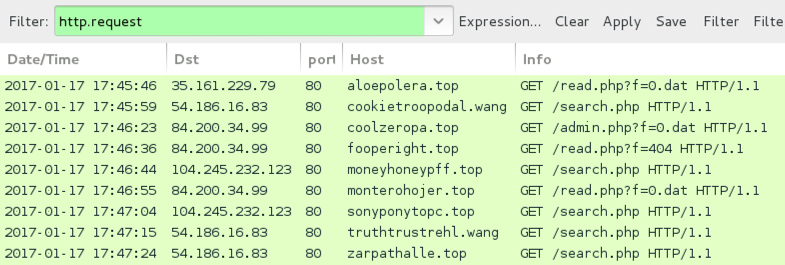
Shown above: URLs caused by the Word macros shown in Wireshark.
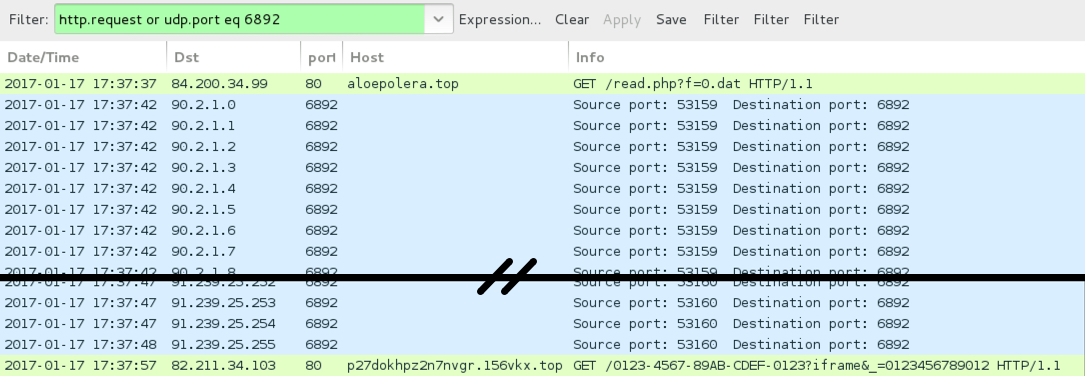
Shown above: Traffic from an infection example filtered in Wireshark.
URLS GENERATED BY THE WORD MACROS TO DOWNLOAD CERBER RANSOMWARE:
- 35.161.229[.]79 port 80 - aloepolera[.]top - GET /read.php?f=0.dat
- 54.186.16[.]83 port 80 - cookietroopodal[.]wang - GET /search.php
- 84.200.34[.]99 port 80 - coolzeropa[.]top - GET /admin.php?f=0.dat
- 84.200.34[.]99 port 80 - fooperight[.]top - GET /read.php?f=404
- 104.245.232[.]123 port 80 - moneyhoneypff[.]top - GET /search.php
- 84.200.34[.]99 port 80 - monterohojer[.]top - GET /read.php?f=0.dat
- 104.245.232[.]123 port 80 - sonyponytopc[.]top - GET /search.php
- 54.186.16[.]83 port 80 - truthtrustrehl[.]wang - GET /search.php
- 54.186.16[.]83 port 80 - zarpathalle[.]top - GET /search.php
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 90.2.1[.]0 to 90.2.1[.]31 (90.2.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 90.3.1[.]0 to 90.3.1[.]31 (90.3.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 82.211.34[.]103 port 80 - p27dokhpz2n7nvgr.156vkx[.]top - HTTP post-infection traffic caused by Cerber ransomware
DATA RELATED TO THE ACTOR(S) BEHIND THIS CAMPAIGN
IP ADDRESSES HOSTING THE CERBER RANSOMWARE:
- 35.161.229[.]79 - ec2-35-161-229-79.us-west-2.compute.amazonaws[.]com
- 54.186.16[.]83 - ec2-54-186-16-83.us-west-2.compute.amazonaws[.]com
- 84.200.34[.]99 - Germany: Pielayer (Accelerated IT)
- 104.245.232[.]123 - US: Haris Pajalic (Elctro Nebula LLC)
REGISTRATION INFO FOR THE MALICIOUS DOMAINS:
- aloepolera[.]top - created: 2017-01-16 (Eranet) - registrant email: jenniemarc@mail[.]com
- cookietroopodal[.]wang - created: 2017-01-16 (TodayNIC[.]com) - registrant email: lecborbobl@rothtec[.]com
- coolzeropa[.]top - created: 2017-01-13 (Eranet) - registrant email: lecborbobl@rothtec[.]com
- fooperight[.]top - created: 2017-01-13 (Eranet) - registrant email: jenniemarc@mail[.]com
- moneyhoneypff[.]top - created: 2017-01-16 (Eranet) - registrant email: lecborbobl@rothtec[.]com
- monterohojer[.]top - created: 2017-01-15 (Eranet) - registrant email: deanmcd@mail[.]com
- sonyponytopc[.]top - created: 2017-01-16 (Eranet) - registrant email: lecborbobl@rothtec[.]com
- truthtrustrehl[.]wang - created: 2017-01-13 (TodayNIC[.]com) - registrant email: deanmcd@mail[.]com
- zarpathalle[.]top - created: 2017-01-13 (Eranet) - registrant email: galicole@mail[.]com
NUMBER OF DOMAINS REGISTERED USING THESE EMAIL ADDRESSES:
- deanmcd@mail[.]com - 135 domains
- galicole@mail[.]com - 140 domains
- jenniemarc@mail[.]com - 118 domains
- lecborbobl@rothtec[.]com - 139 domains
MALWARE
CERBER RANSOMWARE SAMPLES DOWNLOADED FROM THE URLS:
- 585842497ce785b3336b8006662ab89ce8528eff06a53bd57c20c1d6d1a3a15d - Cerber ransomware downloaded by Word macro example 1 of 8
- aeaf5aee566e9abf087379625496be877ad0a3146eabe1d28d087d170053b0a1 - Cerber ransomware downloaded by Word macro example 2 of 8
- 75f5f3734e229fd5901757226a0639d55133604fc27e4b3e19a005a44fc368cc - Cerber ransomware downloaded by Word macro example 3 of 8
- 907eb3c310b5d86a4c58b3955c4802fe0c4e358c72b474ff0c8cedb81c5c0eae - Cerber ransomware downloaded by Word macro example 4 of 8
- b53490b8319b354b36b3e13b710f13a7da7fe1a3258fcc52c0b1f9c4e2fbc12b - Cerber ransomware downloaded by Word macro example 5 of 8
- d2cb1407cec8c5357557265ce0d3b59b9aeab1d754d9f5401e317504e7afbf67 - Cerber ransomware downloaded by Word macro example 6 of 8
- 51ce7e7bf3405854e1185a908e495ab113f7b57db369a3ff5e5fdfd9c05c7440 - Cerber ransomware downloaded by Word macro example 7 of 8
- 16d573cb8f9570e3bdfffa0dcaba76c4dfcec2620d426d1c08f10bdc26c63300 - Cerber ransomware downloaded by Word macro example 8 of 8
IMAGES
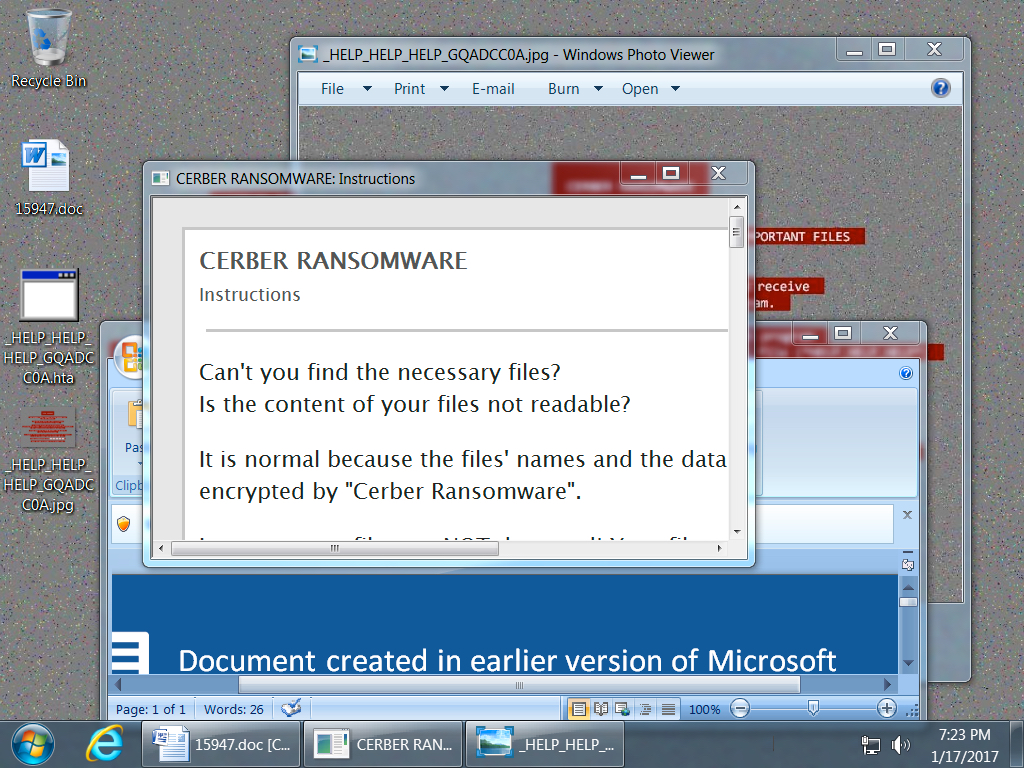
Shown above: Screenshot with an example of an infected desktop.
Click here to return to the main page.