2017-01-23 - "BLANK SLATE" CAMPAIGN SENDS CERBER OR SAGE 2.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-23-Cerber-or-Sage-ransomware-infection-traffic-6-pcaps.zip 871.5 kB (871,468 bytes)
- 2017-01-23-Blank-Slate-malspam-tracker.csv.zip 1.6 kB (1,636 bytes)
- 2017-01-23-Blank-Slate-emails-and-associated-ransomware.zip 4.0 MB (3,993,649 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
EMAILS
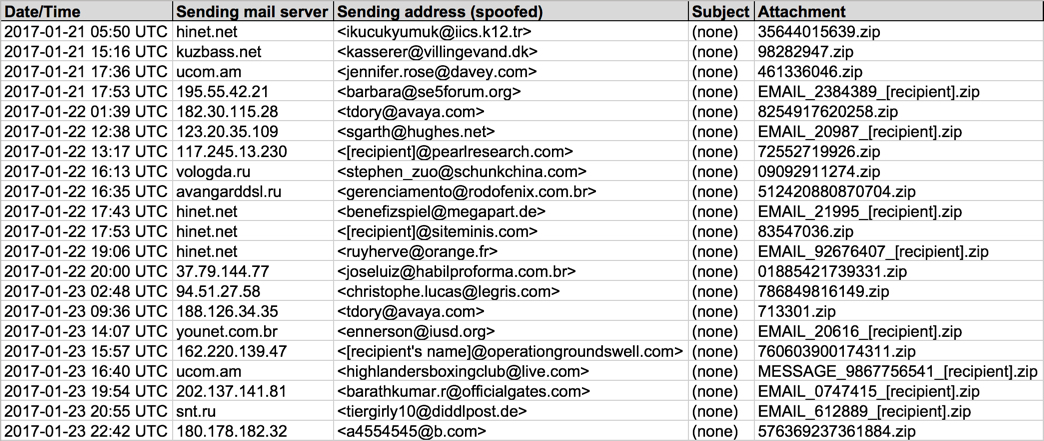
Shown above: Information from the spreadsheet tracker (part 1 of 3).
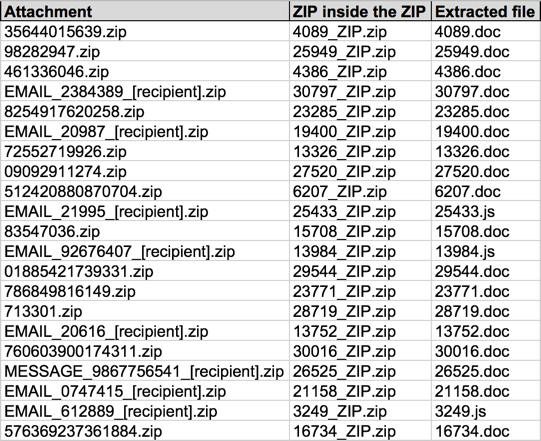
Shown above: Information from the spreadsheet tracker (part 2 of 3).
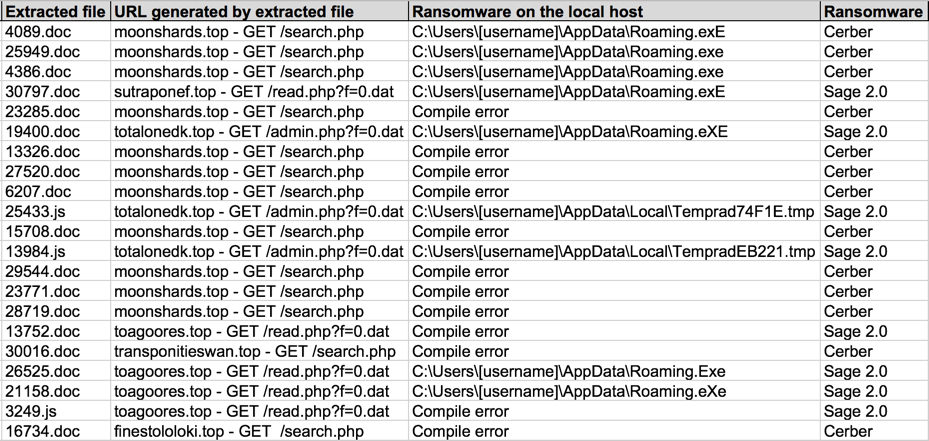
Shown above: Information from the spreadsheet tracker (part 3 of 3).
EMAILS GATHERED:
(Read: Date/Time -- Sending mail server -- Sending address (spoofed) -- Attachment)
- 2017-01-21 05:50 UTC -- hinet[.]net -- <ikucukyumuk@iics.k12[.]tr> -- 35644015639.zip
- 2017-01-21 15:16 UTC -- kuzbass[.]net -- <kasserer@villingevand[.]dk> -- 98282947.zip
- 2017-01-21 17:36 UTC -- ucom.am -- <jennifer.rose@davey[.]com> -- 461336046.zip
- 2017-01-21 17:53 UTC -- 195.55.42[.]21 -- <barbara@se5forum[.]org> -- EMAIL_2384389_[recipient].zip
- 2017-01-22 01:39 UTC -- 182.30.115[.]28 -- <tdory@avaya[.]com> -- 8254917620258.zip
- 2017-01-22 12:38 UTC -- 123.20.35[.]109 -- <sgarth@hughes[.]net> -- EMAIL_20987_[recipient].zip
- 2017-01-22 13:17 UTC -- 117.245.13[.]230 -- <[recipient]@pearlresearch[.]com> -- 72552719926.zip
- 2017-01-22 16:13 UTC -- vologda[.]ru -- <stephen_zuo@schunkchina[.]com> -- 09092911274.zip
- 2017-01-22 16:35 UTC -- avangarddsl[.]ru -- <gerenciamento@rodofenix[.]com[.]br> -- 512420880870704.zip
- 2017-01-22 17:43 UTC -- hinet[.]net -- <benefizspiel@megapart[.]de> -- EMAIL_21995_[recipient].zip
- 2017-01-22 17:53 UTC -- hinet[.]net -- <[recipient]@siteminis[.]com> -- 83547036.zip
- 2017-01-22 19:06 UTC -- hinet[.]net -- <ruyherve@orange[.]fr> -- EMAIL_92676407_[recipient].zip
- 2017-01-22 20:00 UTC -- 37.79.144[.]77 -- <joseluiz@habilproforma[.]com[.]br> -- 01885421739331.zip
- 2017-01-23 02:48 UTC -- 94.51.27[.]58 -- <christophe.lucas@legris[.]com> -- 786849816149.zip
- 2017-01-23 09:36 UTC -- 188.126.34[.]35 -- <tdory@avaya[.]com> -- 713301.zip
- 2017-01-23 14:07 UTC -- younet[.]com[.]br -- <ennerson@iusd[.]org> -- EMAIL_20616_[recipient].zip
- 2017-01-23 15:57 UTC -- 162.220.139[.]47 -- <[recipient's name]@operationgroundswell[.]com> -- 760603900174311.zip
- 2017-01-23 16:40 UTC -- ucom.am -- <highlandersboxingclub@live[.]com> -- MESSAGE_9867756541_[recipient].zip
- 2017-01-23 19:54 UTC -- 202.137.141[.]81 -- <barathkumar.r@officialgates[.]com> -- EMAIL_0747415_[recipient].zip
- 2017-01-23 20:55 UTC -- snt.ru -- <tiergirly10@diddlpost[.]de> -- EMAIL_612889_[recipient].zip
- 2017-01-23 22:42 UTC -- 180.178.182[.]32 -- <a4554545@b[.]com> -- 576369237361884.zip
ATTACHED ZIP ARCHIVES AND EXTRACTED FILES
SHA256 HASHES FOR THE EMAIL ATTACHMENTS:
- 2aaefb195f43f978deb49c3a55e64e52a6306790d34dfb6d125d8c2f669a9baa - 713301.zip (20,032 bytes)
- 833b8cb79383f9b82ed4152e732b92e1a1a855e414d1e298c945eba5e124006b - 83547036.zip (20,032 bytes)
- e594725fb46c4d19292addf994e56148b27d415e8b8b6da778e746867c0aff4b - 98282947.zip (37,133 bytes)
- 7ac2ce29425532f5c7828268591daa2c016447b4ffebb922749c602d1a95d24f - 461336046.zip (41,205 bytes)
- 7c71f19bc197bee3f26a7dcbbb2027e47d75b6f7781c26ce53bf514679df473b - 09092911274.zip (19,379 bytes)
- 247413652e789872152d0f0dfcf497d3f389d0f183f19bc02a6bceabd128ccde - 35644015639.zip (47,970 bytes)
- 4f9b74ba00840b9acab83354d68be6fd8e4d9cd91df3c2c95a51451d1a35f7f1 - 72552719926.zip (20,032 bytes)
- 96a59b8ee9a04f0fe7163f6124360cca019213f5ee45fde5db9acb5ee4ff35ca - 786849816149.zip (18,918 bytes)
- 219c5d46e19a2ff7b4c4615bf6aca143d28390ed1765fa3079ae24090d1917ea - 8254917620258.zip (19,881 bytes)
- f9e6240d624dacfd9c1ed721264ecdae2c59d73925eeb4090f5b6bb8f6346808 - 01885421739331.zip (17,391 bytes)
- a99d7eef10ae1f410bc3e8c56b384c3aee9685c0695b6a57344d5e9fc55cac5d - 512420880870704.zip (19,378 bytes)
- 81303213432927c4532771400171026da8e046f9eef5b4688a459757edb57848 - 576369237361884.zip (53,592 bytes)
- 7f757e5131c8429c8fb3bb373a5c7f8c231c994d3c28e842ee10f940a74c66db - 760603900174311.zip (49,065 bytes)
- 4a0b1db149b81400d07b84cfc03108fa2db9bfb0ee24b0be785d020d5d8b8ec7 - EMAIL_20616_[recipient].zip (55,357 bytes)
- 8ff7fe311c2fdfd3916b2b52825b49b62f97d5e2ad56909d72de54800d462802 - EMAIL_20987_[recipient].zip (51,290 bytes)
- 6e75f19ffb530a2208775501e63c297f6be6ea5d6643e38d074bdbc170f1838c - EMAIL_21995_[recipient].zip (17,396 bytes)
- 1d29df473a9bf0e3c855e7027053e3da8a5c69ac809149dd44195be61edee022 - EMAIL_612889_[recipient].zip (3,544 bytes)
- 21d431e93f692e51957828e09e10f393fa8e47090c817d12061ce2cc9d0c8df6 - EMAIL_0747415_[recipient].zip (61,593 bytes)
- 0cd52fb7ba227a46de123e243b074505abd0f41de664eb36a251a74b41728b2c - EMAIL_2384389_[recipient].zip (55,035 bytes)
- 3d09f69c545477c153937a29b79a578e69f9a9373039e2ab23ada11be5d30121 - EMAIL_92676407_[recipient].zip (15,867 bytes)
- a8dd66e0f5436f8a839f6601f77f95c70a6732ec4136dea08c53f4ae8b2ef11b - MESSAGE_9867756541_[recipient].zip (60,101 bytes)
SHA256 HASHES FOR THE EXTRACTED WORD DOCUMENTS AND .JS FILES:
- d48abd6e073057ea221c66eaf01b6930fd40f2bd0674a78ffbd7ed05c56a4b29 - 4089.doc (117,248 bytes)
- db1bb73c3baf2bac2d0450c63c574373e1ef3a3831a777da787fae5e2f853c8d - 4386.doc (101,888 bytes)
- 2c49401116158d1c5a58d10eee80d24a8f44c5bc1e1dbe5b7544394bb84aa6fe - 6207.doc (49,152 bytes)
- ccf3dfb7766c49b66a72079de69a38ee06303e01b12b6dedd2998420c5345cac - 13326.doc (50,688 bytes)
- 1f4a17a6453740ea4f29a731d4f2f507d43d78f664b5dfae5bffb8d317c1ff91 - 13752.doc (122,368 bytes)
- ccf3dfb7766c49b66a72079de69a38ee06303e01b12b6dedd2998420c5345cac - 15708.doc (50,688 bytes)
- bb27fce4489e2c56d3d30b9bb55a3fc8439dca55d857c5999ce0f3c18fee7103 - 16734.doc (143,360 bytes)
- 20d9edbd9b9ee821aa3fd6fcb7c5791b34ee63310244103417e0f34d6c3a5b35 - 19400.doc (111,104 bytes)
- 798ffcf1354a11cd1bd35444ce9ebe9b5d6632124388b7378409c26550e655cf - 21158.doc (128,512 bytes)
- fa46385734854947d2b559d954e8a89ecd768109d84f8526c0e0071b13c8f2ae - 23285.doc (50,688 bytes)
- 73c984947c250fcbeb06eeda39919dd0fa1549c240fb5ce396c0da989aeb9759 - 23771.doc (48,640 bytes)
- 6c5642178b33eff21ae7aa8454f13f14da0275655edb24d7f29f436f7727a24b - 25949.doc (91,648 bytes)
- c59ffb61e6e23048b3a6584178c40ddfd066c3d32f505cf1c25a8f7caf39fa32 - 26525.doc (121,856 bytes)
- 2c49401116158d1c5a58d10eee80d24a8f44c5bc1e1dbe5b7544394bb84aa6fe - 27520.doc (49,152 bytes)
- ccf3dfb7766c49b66a72079de69a38ee06303e01b12b6dedd2998420c5345cac - 28719.doc (50,688 bytes)
- 278db3b528d3ee095a426856c4edcf8297038a8f991a09958bf4a2bc39c15b98 - 29544.doc (44,544 bytes)
- 24eec180d056770461713e1895fd2a845bac87d2040de030ab9e964412572bfd - 30016.doc (114,688 bytes)
- 76ef256b35bc2eb742aa046a461e8552be043df90cad8047774d7313c0c024b0 - 30797.doc (121,344 bytes)
- 9ed278479e583c6a1aae293175f00d57db1fc17ac15749023261c0b3ac756c0d - 3249.js (10,465 bytes)
- ca8882ac9253d46d341e74028150888305ea54a4653cca6339ffc71cfe69fd01 - 13984.js (41,860 bytes)
- 7eb23c477a3f09200582eaa7b5c5a2a994388a6fc8c9b5f393480f601cd0a76c - 25433.js (44,665 bytes)
TRAFFIC
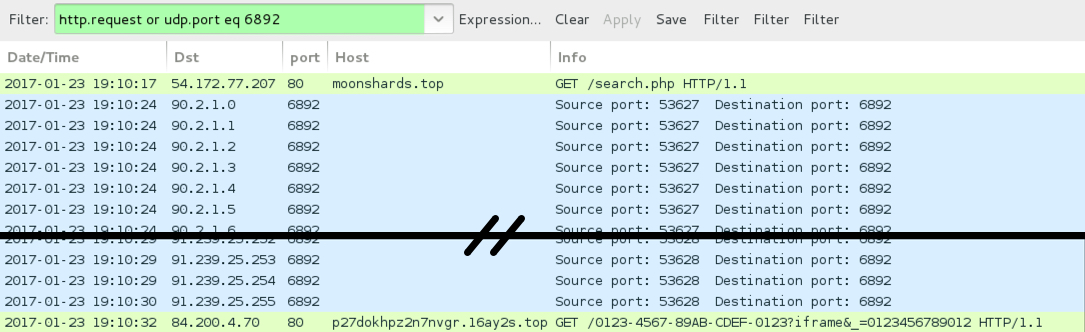
Shown above: Example of a Cerber ransomware infection from this campaign, filtered in Wireshark.
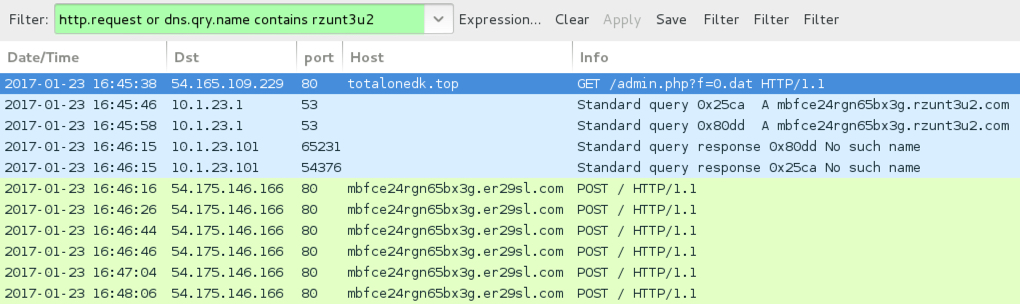
Shown above: Example of a Sage 2.0 ransomware infection from this campaign, filtered in Wireshark.
HTTP REQUESTS FOR THE CERBER RANSOMWARE:
- 54.213.200[.]232 port 80 - finestololoki[.]top - GET /search.php
- 54.172.77[.]207 port 80 - moonshards[.]top - GET /search.php
- 54.172.77[.]207 port 80 - transponitieswan[.]top - GET /search.php
HTTP REQUESTS FOR THE SAGE 2.0 RANSOMWARE:
- 54.165.109[.]229 port 80 - sutraponef[.]top - GET /read.php?f=0.dat
- 103.208.86[.]180 port 80 - toagoores[.]top - GET /read.php?f=0.dat
- 54.165.109[.]229 port 80 - totalonedk[.]top - GET /admin.php?f=0.dat
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 90.2.1[.]0 to 90.2.1[.]31 (90.2.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 90.3.1[.]0 to 90.3.1[.]31 (90.3.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 84.200.4[.]70 port 80 - p27dokhpz2n7nvgr.16ay2s[.]top - HTTP post-infection traffic caused by Cerber ransomware
SAGE 2.0 RANSOMWARE POST-INFECTION TRAFFIC:
- DNS request for mbfce24rgn65bx3g.rzunt3u2[.]com - DNS response: No such name
- 54.175.146[.]166 port 80 - mbfce24rgn65bx3g.er29sl[.]com - HTTP post-infection traffic caused by Sage 2.0 ransomware
DOMAINS FROM THE SAGE 2.0 RANSOMWARE DECRYPTION INSTRUCTIONS:
- 7gie6ffnkrjykggd.rzunt3u2[.]com
- 7gie6ffnkrjykggd.er29sl[.]in
- 7gie6ffnkrjykggd[.]onion
MALWARE
CERBER AND SAGE 2.0 RANSOMWARE SAMPLES:
- 7ac2a59c79d58e38a8e383ba3945406c7f4f649523be72ae7fc9c87a1022b60d - 2017-01-23 Cerber ransomware 1st sample (273,284 bytes)
- 908d810aa3b29046981d43b0f74f82a4b27d59ac620835d6c00e1d16e2b79d5e - 2017-01-23 Cerber ransomware 2nd sample (268,475 bytes)
- 2be1f50ed1b4d8720839f5dd6205ddeca7d2956b110eb4b9e1901fef9200eb04 - 2017-01-23 Cerber ransomware 3rd sample (268,475 bytes)
- 5e7cc796dfd2d47e6efb31412e1d614db6d96620ac118426dda04b6fbb943993 - 2017-01-23 Sage 2.0 ransomware 1st sample (245,833 bytes)
- 0f7f7e7429e3b6bbcbd17d34edb3ba7e3c1216aee2229dd5327a6d5a8659aa09 - 2017-01-23 Sage 2.0 ransomware 2nd sample (360,521 bytes)
- bead52bdfd2fbf477cd59acbfbf9174e518abebc952bcebf5a240b7dcdfe0ac1 - 2017-01-23 Sage 2.0 ransomware 3rd sample (360,521 bytes)
- 59483dad43e9016f8c2073fd20a214d00f2c750d9f96ee68aab67c96ac763a6b - 2017-01-23 Sage 2.0 ransomware 4th sample (278,661 bytes)
IMAGES
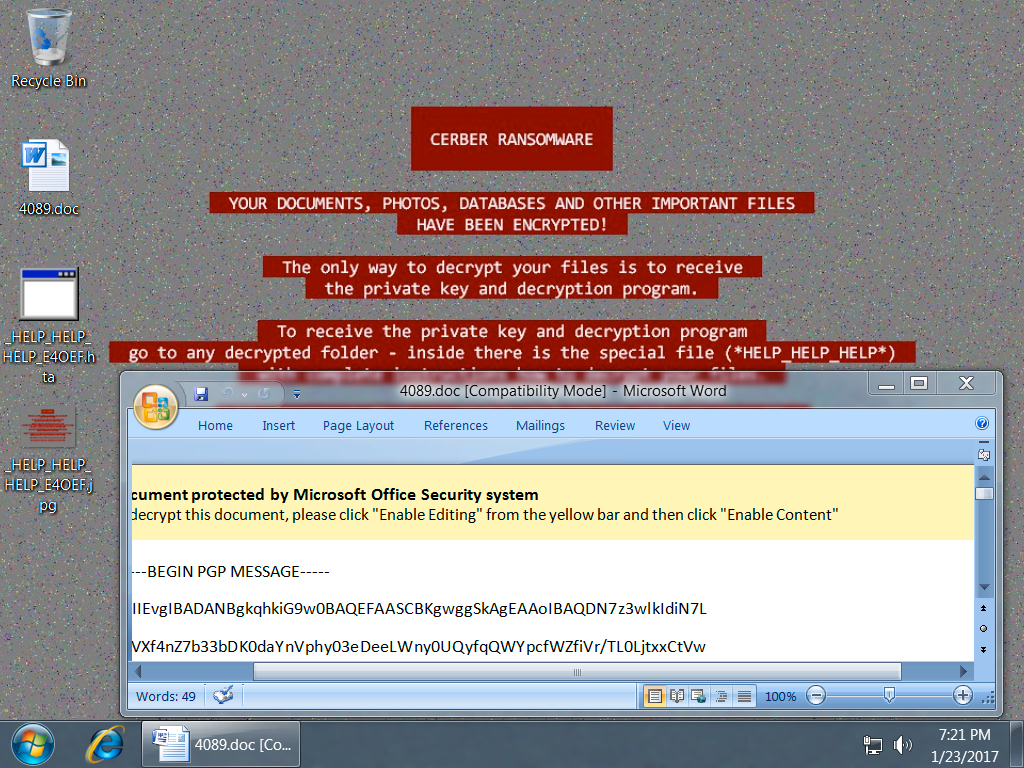
Shown above: Example of a desktop infected with Cerber ransomware from one of the email attachments.
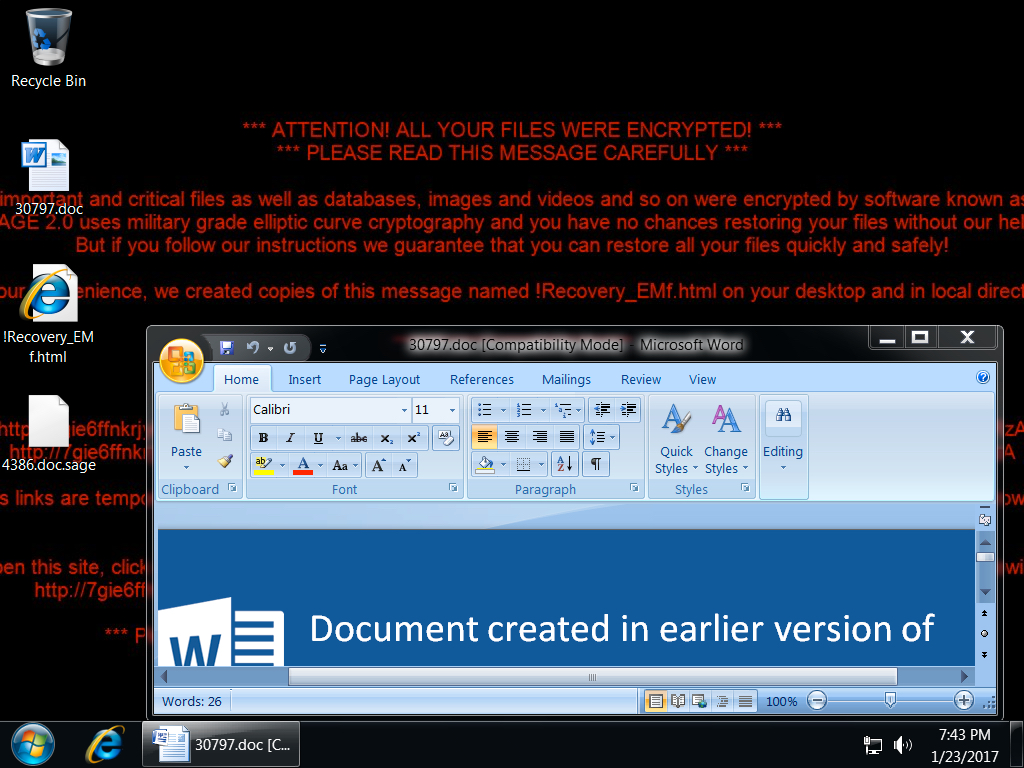
Shown above: Example of a desktop infected with Sage 2.0 ransomware from one of the email attachments.
Click here to return to the main page.
