2017-01-25 - HANCITOR INFECTION WITH SEND SAFE ENTERPRISE (SSE) SPAMBOT TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-25-Hancitor-infection-with-SendSafe-spambot-traffic.pcap.zip 9.8 MB (9,754,181 bytes)
- 2017-01-25-Hancitor-malspam-1521-UTC.eml.zip 1.6 kB (1,644 bytes)
- 2017-01-25-malware-from-Hancitor-infection.zip 1.7 MB (1,698,732 bytes)
NOTES:
- This is an email and traffic form the latest wave of apparent Hancitor/Pony/Vawtrak malspam.
- Traffic is similar to a recent ISC diary I wrote earlier this month at: https://isc.sans.edu/diary/HancitorPonyVawtrak+malspam/21919
- No Vawtrak this time, though.
- This one had malware downloaded of SendSafe Enterprise (SSE) based spambot malware designed to send out more Hancitor emails from the infected Windows host.
MALSPAM

Shown above: Screenshot of the email.
TRAFFIC
ASSOCIATED ACTIVITY:
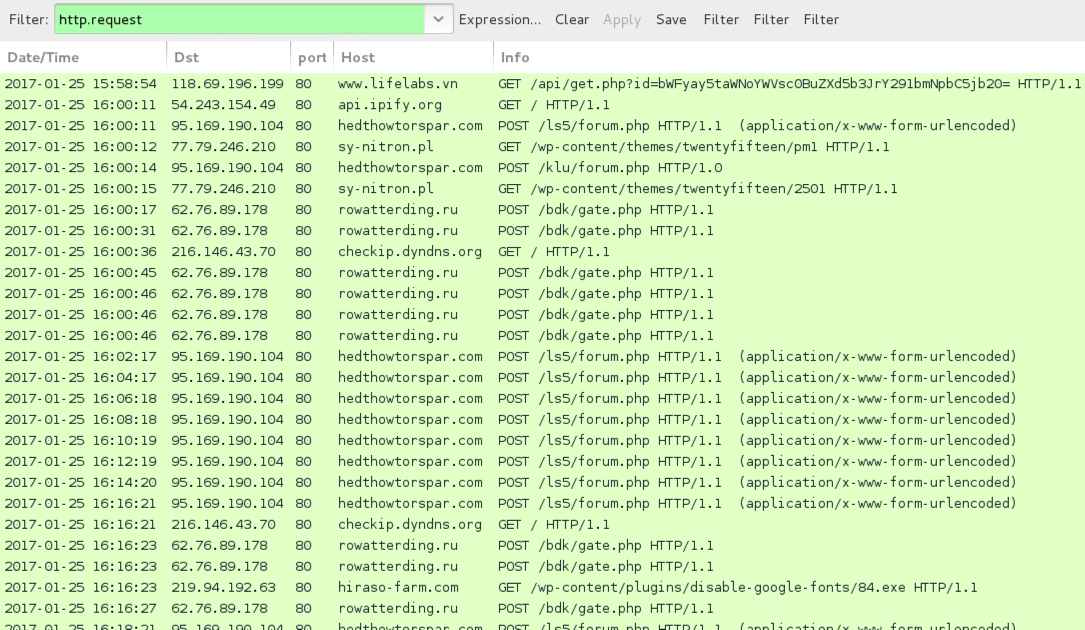
Shown above: Pcap of the infection traffic filtered in Wireshark.
- 118.69.196[.]199 port 80 - www.lifelabs[.]vn - GET /api/get.php?id=[base64 string representing recipient's email address]
- api.ipify[.]org - GET /
- 95.169.190[.]104 port 80 - hedthowtorspar[.]com - POST /ls5/forum.php
- 95.169.190[.]104 port 80 - hedthowtorspar[.]com - POST /klu/forum.php
- 77.79.246[.]210 port 80 - sy-nitron[.]pl - GET /wp-content/themes/twentyfifteen/pm1
- 77.79.246[.]210 port 80 - sy-nitron[.]pl - GET /wp-content/themes/twentyfifteen/2501
- 62.76.89[.]178 port 80 - rowatterding.ru - POST /bdk/gate.php
- checkip.dyndns[.]org - GET /
- 219.94.192[.]63 port 80 - hiraso-farm[.]com - GET /wp-content/plugins/disable-google-fonts/84.exe
- 91.220.131[.]84 port 50004 - UDP post-infection traffic
- 91.220.131[.]84 port 50003 - TCP post-infection traffic
- several different IP addresses - port 25 - attempted SMTP traffic
MALWARE
MALWARE RETRIEVED FROM THE INFECTED HOST:
- 9c1ad87660e13b35fc48961f0936e9724aa763a3130e194bf67402a118d32657 - eFax_mark.doc (201,728 bytes)
- 8e436941dc1a9892cb5ee170f16116ca0cf2e5c25abf84ed74b4a15eaee94f4e - C:\Users\[username]\AppData\Local\Temp\84.exe (1,930,752 bytes)
it, look at the "about" page of this website.
Click here to return to the main page.
